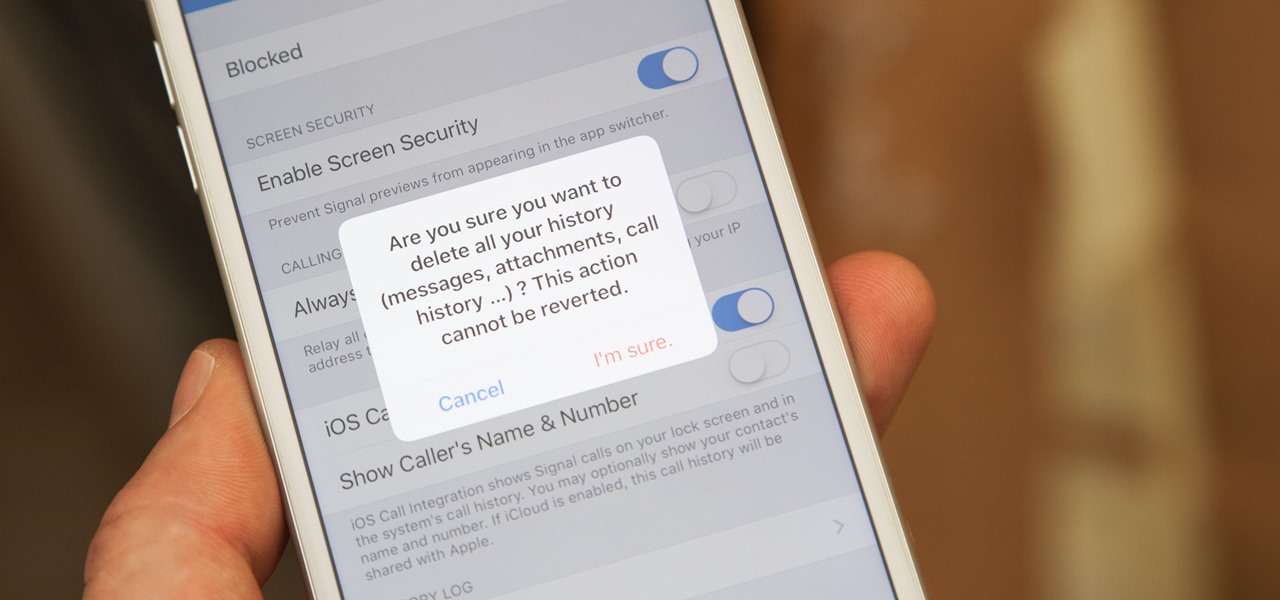
If thieves, hackers, law enforcement, or other would-be enemies should ever gain entry to your smartphone, they could also access conversations you've had in Signal Private Messenger. To better secure your encrypted communications, you can password-protect the whole app and its contents — but only on Android. Even then, it's necessary to perform data deletion on a periodic basis, if not immediately.

It's time for another Achievement Hunter video from the guys who know how to do it best. The game they're playing this time is the first DLC for the psychological hit thriller, Alan Wake. The Signal takes players deeper into the story of Alan Wake and find out what's actually going on with his life.

Step 1: Score! Watch for the referee signaling a touchdown, field goal, extra point, or successful try by raising their arms straight up over their head. Raising their hands above their head with palms together signals a safety.

If you own a Pixel or Nexus device, Project Fi is a great alternative for cellular service outside of the four major US carriers. Project Fi is a Google-managed MVNO, providing service primarily through the T-Mobile and Sprint networks. One of the biggest mysteries on Fi is which network you're connected to at any given time, but there's a simple solution.

If you've received a spam message in Signal Private Messenger, you know that anyone can contact you as long as they have your linked phone number. But when it comes to the people you're actually trying to have a private conversation with, how do you know it's really them?

This experiment is intended to introduce students to hydrated compounds. These compounds have water molecules coordinated in their chemical structures. Examples CuSO4*5H2O, BaCl2*2H2O, and NaC2H3O2*3H2O.

Brute-forcing is an easy way of discovering weak login credentials and is often one of the first steps when a hacker finds network services running on a network they gain access to. For beginners and experienced hackers alike, it's useful to have access to the right tools to discover, classify, and then launch customized brute-force attacks against a target. BruteDum does it all from a single framework.

Want the next level security? Well then take a read here because this is some next level stuff. Heard of It?

Horseriderchamp productions presents this video on how to do join-up with a horse. Here, in this video, the lady demonstrates this with her one year old horse 'majestic. She says that join-up is basically creating bond or relationship with your horse and there are three signals to join-up. The first signal she says is to have horse's one ear locked on you when they start to look on you and start to make small circles, and she says that once you get the signals, when you turn to speak to them ...

Whether your plane made a crash landing or your ship got lost on a three-hour tour, now you're stranded on a remote island. Here's how to get help.

Want to boost your WiFi reception? Have an extra wok or parabolic collander? This video tutorial demonstrates a simple hack that will allow you to build an effective radio antenna that will significantly increase the gain of your WiFi signal. To replicate this hack at home, you'll need the following items: (a) a piece of parabolic cookware, (b) heavy tape, (c) a USB WiFi stick, (d) tin snips, and (5) a USB extension cable. For detailed instructions on building your own wireless signal extende...

Researchers have developed a new method that harnesses the power of augmented reality to detect a patient's heart rate using a Microsoft HoloLens and computer vision.

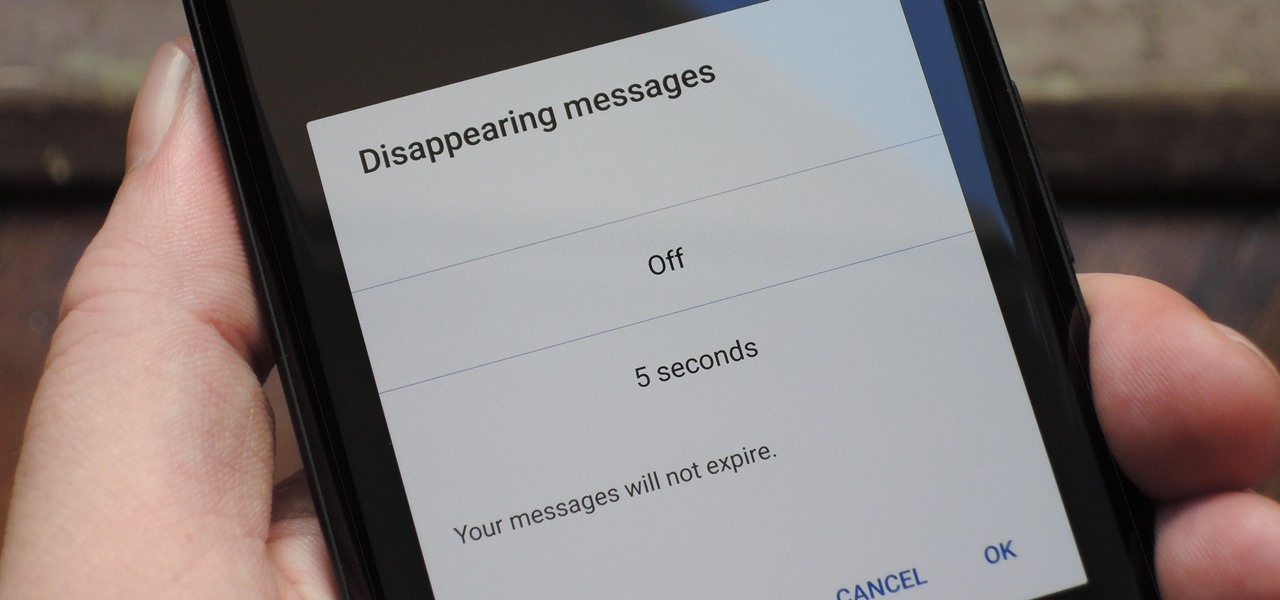
With Signal's class-leading end-to-end encryption, you can be sure your messages will remain secure as they travel to the recipient. However, once the message arrives, its privacy is completely dependent on the receiver, who could share it anywhere if they wanted. To patch this vulnerability, Signal added disappearing messaging.

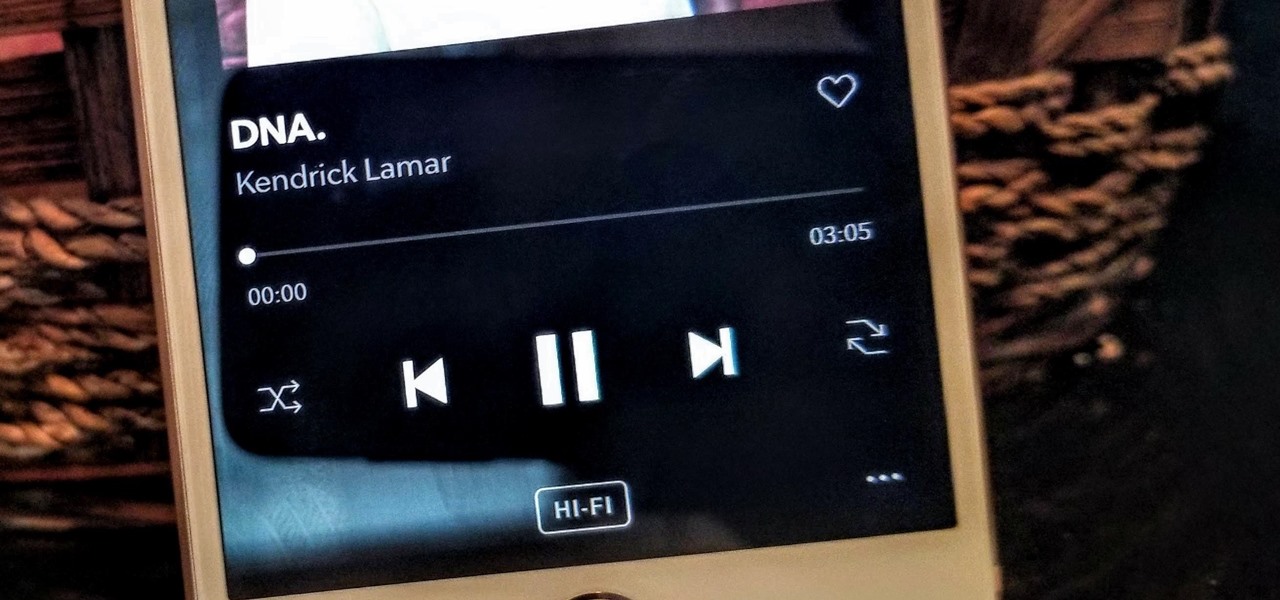
Thanks to their partnership with Tidal, over 30 million Sprint customers can access Hi-Fi audio on the go. And the Jay-Z-owned music service isn't limited to just Sprint customers — for $19.99/month, anyone can listen to lossless audio from their favorite artists. But streaming uncompressed audio files uses a lot more data than standard quality, so how do you use Tidal without hitting your data cap?

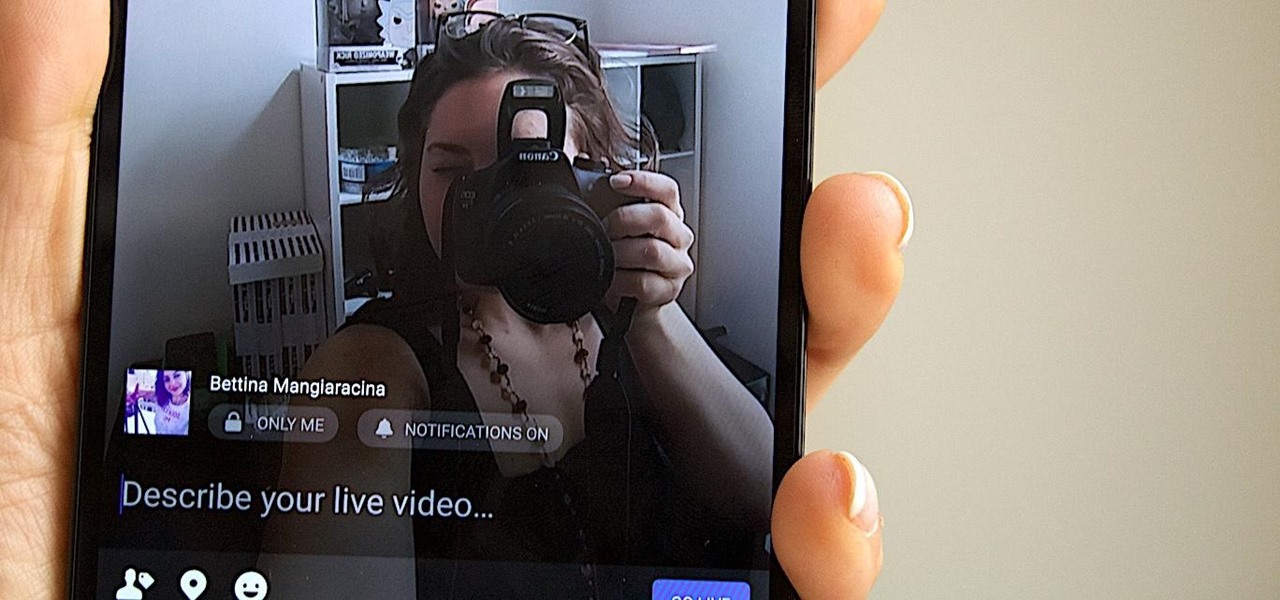
It looks like "going live" is another thing we all have to figure out how to do to remain relevant in this very Facebook-driven world. But why would you ever want to go live? That's really up to you.

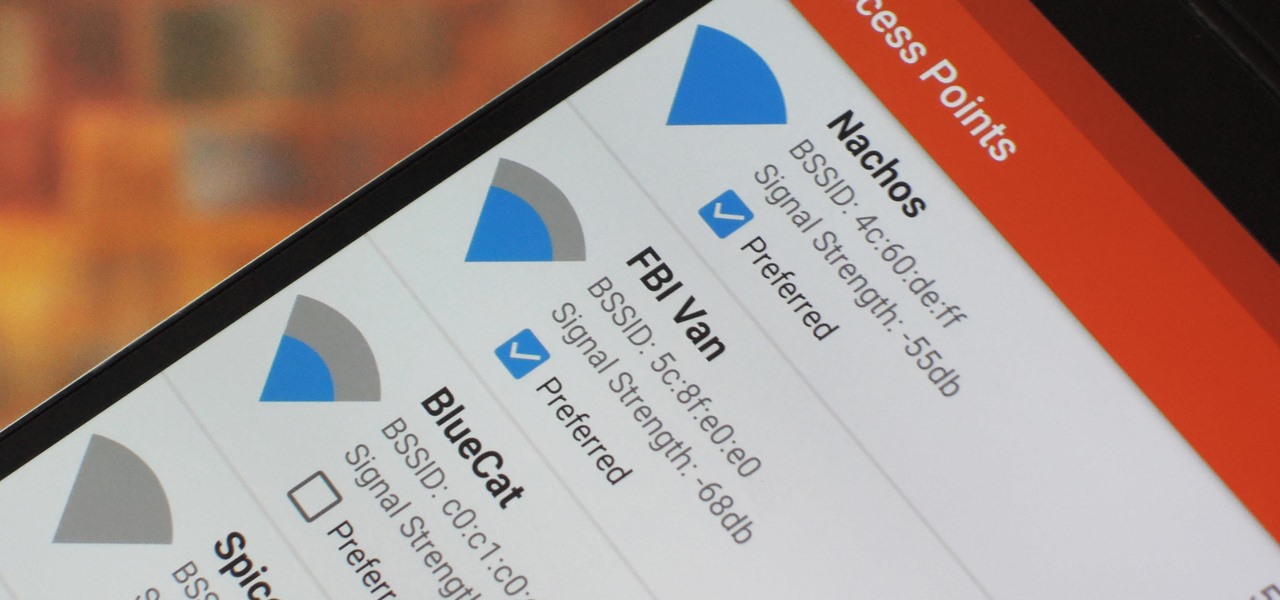
Wi-Fi signals have limited range, so if you live in a two-story house or work in a larger office, you may have set up multiple routers or repeaters to ensure full wireless coverage. Sadly, Android handles the transition between networks pretty poorly.

With over a billion videos uploaded to YouTube, passing your time browsing through the immense library can be an emotional roller coaster ride. One second you're bawling your eyes out over this devastatingly sad clip of Oden the dog's last minutes with his owner, and the next you're laughing hysterically at Spider-Man falling on his face.

In this video we will show you how to replace the turn signal on your 93-98 Volkswagen Jetta.

If you ride your bike or motorcycle a lot, especially in a large city, you've probably had a few close calls. No matter how safely you're driving, you never know what other people are going to do, and being on a smaller vehicle makes you difficult to see.

Jake von Slatt of The Steampunk Workshop kept breaking the rear glass panel on his iPhone. So, he ended up making his own gorgeous replacement out of brass to replace the standard Apple logo ones who kept getting. The only problem was that it made his signal strength super weak, so he figured out how to transfer the etching onto a glass back. Here's the basic rundown of how he accomplished this feat...

In this four part video demonstration, learn how to build your own HID projector headlights. The four parts cover the following:

A function or signal generator is an electronic device that can create different types of waves and send them through a circuit without building oscillators. This video will teach you how they work and how to build a basic LED dimmer that uses one as an example.

Many MicroKorg enthusiasts focus on it's synthesizer functions, but it's also a vocoder, and nowhere is that more apparent than in this video. It will teach you how to connect an electric guitar and a mic to your MicroKorg and use them together so that you can hear your voice on your guitar. It's very worth it.

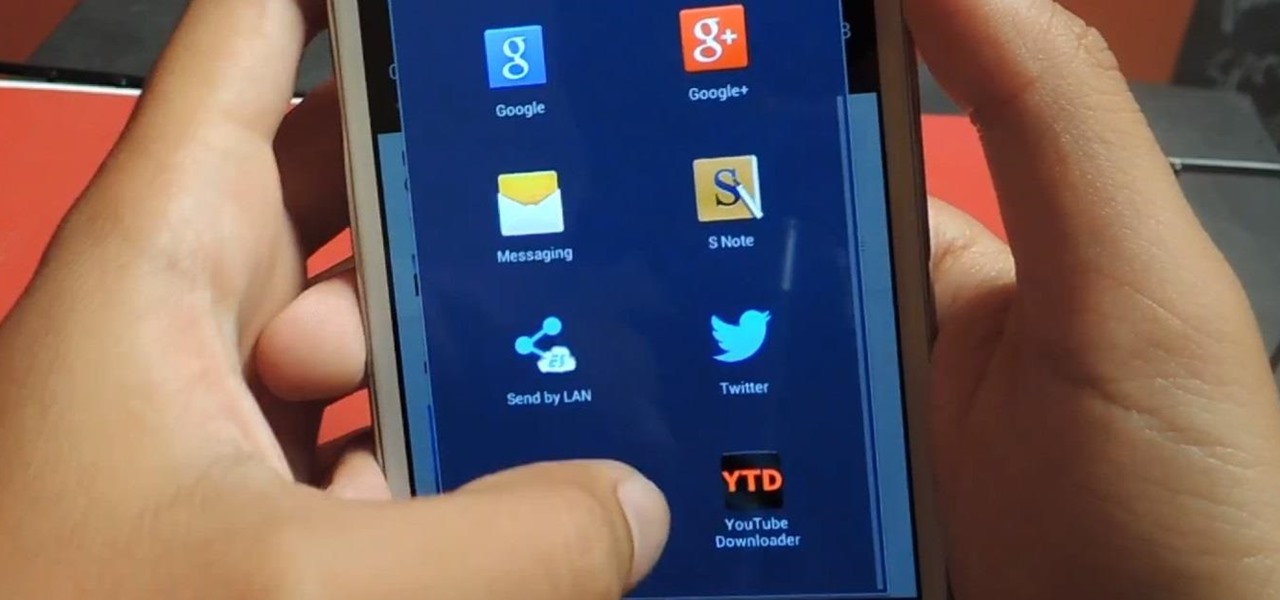
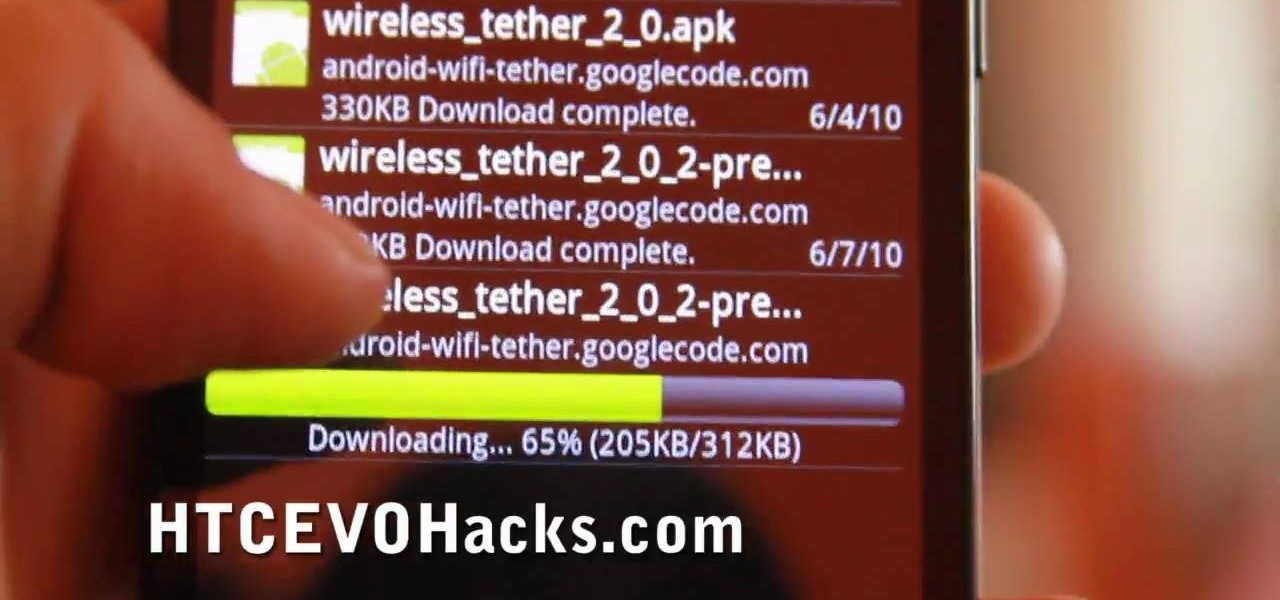
In this tutorial, learn how to access your phone's data network to enable free tethering on your new HTC EVO 4G. By tethering with your EVO you can connect up to eight other devices to your phone and use it as a wireless modem. This hack works with any EVO and will allow you to connect regardless of whether your city offers 3G or 4G signals.

Have you been trying to figure out a way to record your Xbox 360 and broadcast it into Final Cut Pro? Using the DV Passthrough method, you can take an analog signal, pass it through your camcorder, and send it to Final Cut Pro.

There are many ways to attack a Wi-Fi network. The type of encryption, manufacturer settings, and the number of clients connected all dictate how easy a target is to attack and what method would work best. Wifite2 is a powerful tool that automates Wi-Fi hacking, allowing you to select targets in range and let the script choose the best strategy for each network.

Having a dropped call can be incredibly frustrating, especially when you look down and see that your iPhone has full reception. While there's any number of issues that can cause this, one common and often overlooked issue is your iPhone failing to switch cell towers as appropriately needed.

Developed by Open Whisper Systems, Signal is a free, open-source encrypted communications app for both mobile and desktop devices that allows users to make voice calls, send instant messages, and even make video calls securely. However, a vulnerability was recently discovered for the desktop version that can be turned into a USB Rubber Ducky payload to steal signal messages with a single click.

A weak password is one that is short, common, or easy to guess. Equally bad are secure but reused passwords that have been lost by negligent third-party companies like Equifax and Yahoo. Today, we will use Airgeddon, a wireless auditing framework, to show how anyone can crack bad passwords for WPA and WPA2 wireless networks in minutes or seconds with only a computer and network adapter.

Signal Private Messenger is famous for its end-to-end encryption, but you can't even use the messaging app without having a real phone number attached to it. Luckily, there is a way around this limitation, so you can use Signal even if you don't have a valid SIM card in your smartphone.

If you work at a large office or have a multi-story home, you're probably familiar with Wi-Fi range extenders. Since one hotspot isn't always enough to cover an entire area, Wi-Fi repeaters are generally set up in larger areas to capture and rebroadcast the original signal.

Males fight for dominance in order to gain access to the limited supply of female eggs. This is why male birds expend energy on brightly colored plumage, but female birds do not.

In this video, Chad tells us how to know if a guy really likes a girl. If a guy uses physical contact with you, he most likely likes you and wants to contact you. The hard thing about knowing a guy likes you, is if they guy sends you the right signals. A guy could feel more like a friend with you, so feel him out before you approach him. The best way to know if a guy likes you, is to set up boundaries to see if he respects you. A guy should also be able to tell you that he likes you, and tell...

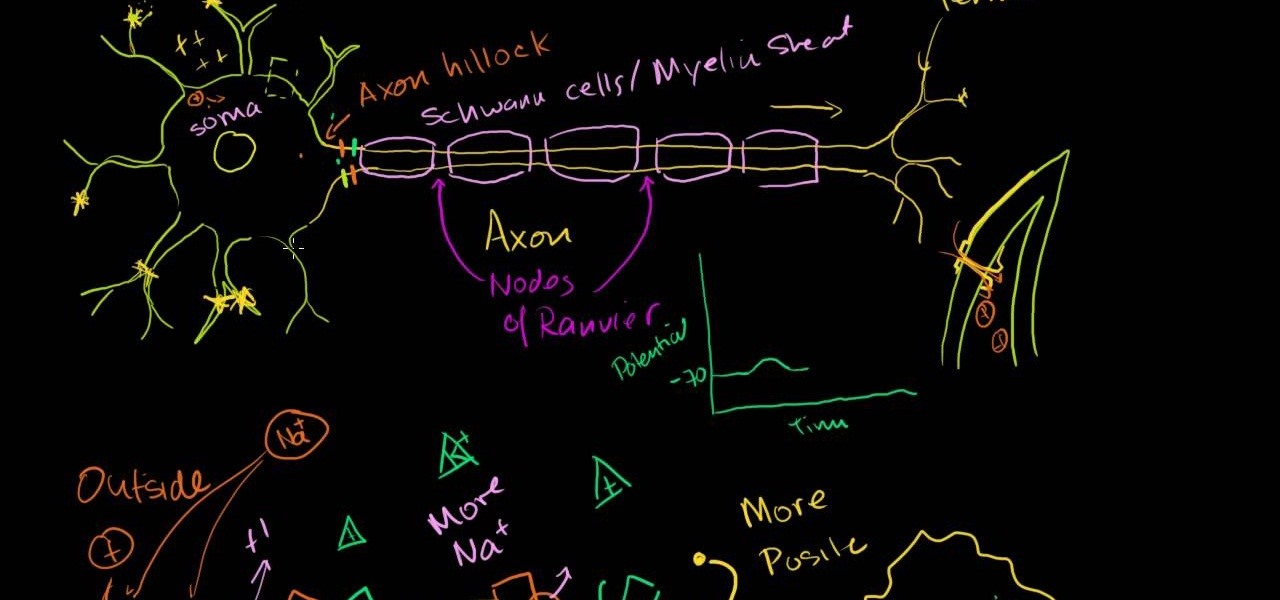
This video is a discourse about saltatory conduction in the neurons. According to the author, it begins with the opening of a gate on the membrane of one of the dendrites of a neuron, and positive charge enters through this gate. The positive charge spreads throughout the cell, and gets dissipated as it spreads, so that, by the time it reaches the Axon hillock of the neuron, it is left with very little potential. However, the potential which results from the simultaneous excitement of many de...

This makeup style is perfect for an Indian wedding or for a Bollywood style costume party. Watch this instructional cosemtics video to apply flashy Indian eye makeup.

We are now in the age of 5G. Carriers worldwide are upgrading their networks to the newest standard for mobile, which will dramatically improve your phone experience. How? By giving it download speeds and latency that surpass Wi-Fi. But before you upgrade, there are few things you should know first.

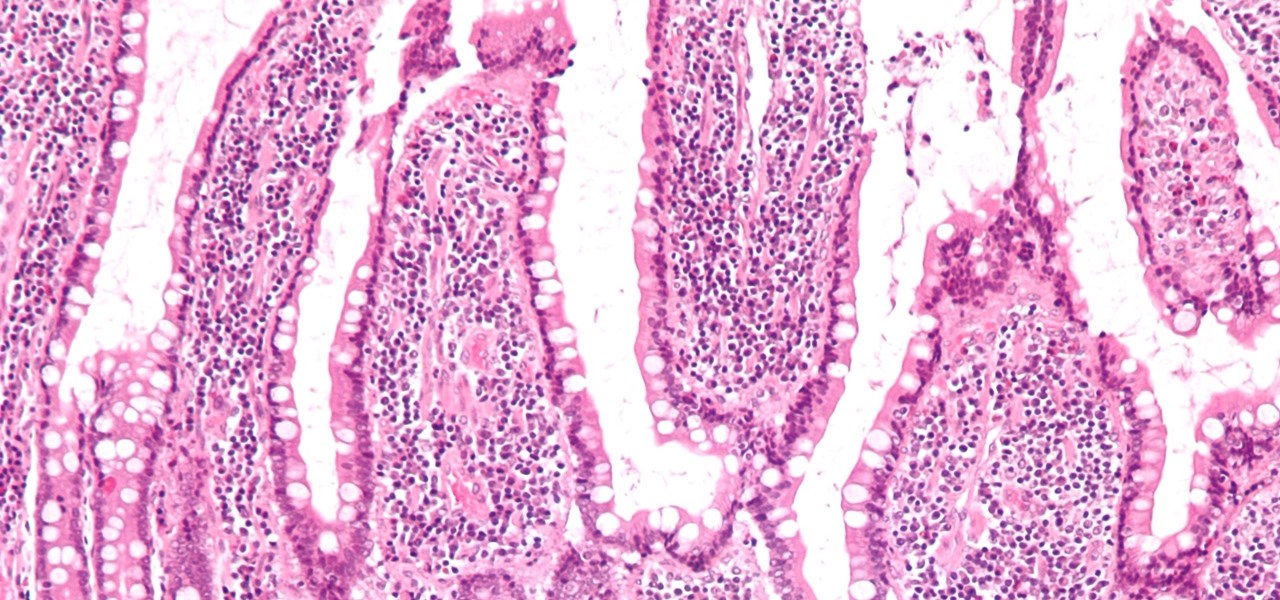
If the all the fingerlike projections in our gut were flattened out, its surface area would be 100 times bigger than our skin's. It's so large that the actions of just a small part of it can impact our health. A new research study has found that enterochromaffin cells in the intestinal lining alert the nervous system to signs of trouble in the gut — trouble that ranges from bacterial products to inflammatory food molecules.

In our first part on software-defined radio and signals intelligence, we learned how to set up a radio listening station to find and decode hidden radio signals — just like the hackers who triggered the emergency siren system in Dallas, Texas, probably did. Now that we can hear in the radio spectrum, it's time to explore the possibilities of broadcasting in a radio-connected world.

On April 7, 2017, residents in Dallas, Texas, woke to the sound of emergency sirens blaring all over the city. No one could shut them off, and after repeated efforts to contain the situation, the city had to shut down the entire system. While the media reported a sophisticated computer hack was responsible, the truth was much less high-tech.

Google's new Project Fi cellular carrier has been making waves across the mobile industry, so we decided to put it to the test against T-Mobile, one of the more established networks. For the actual testing, we slapped a SIM card from each carrier into two identical Pixel XL phones, which offer full compatibility with both networks.