How To: Hack Restaurant City with Cheat Engine 5.6 (04/23/10)
Want to be the Donald Trump of Restaurant City? Watch this video tutorial to learn how to hack Restaurant City (02/21/10) with Cheat Engine 5.6.


Want to be the Donald Trump of Restaurant City? Watch this video tutorial to learn how to hack Restaurant City (02/21/10) with Cheat Engine 5.6.
Want a pile of coins, Scrooge McDuck style? Watch this video tutorial to learn how to hack Restaurant City (01/08/10) with Cheat Engine 5.5 for unlimited free money.
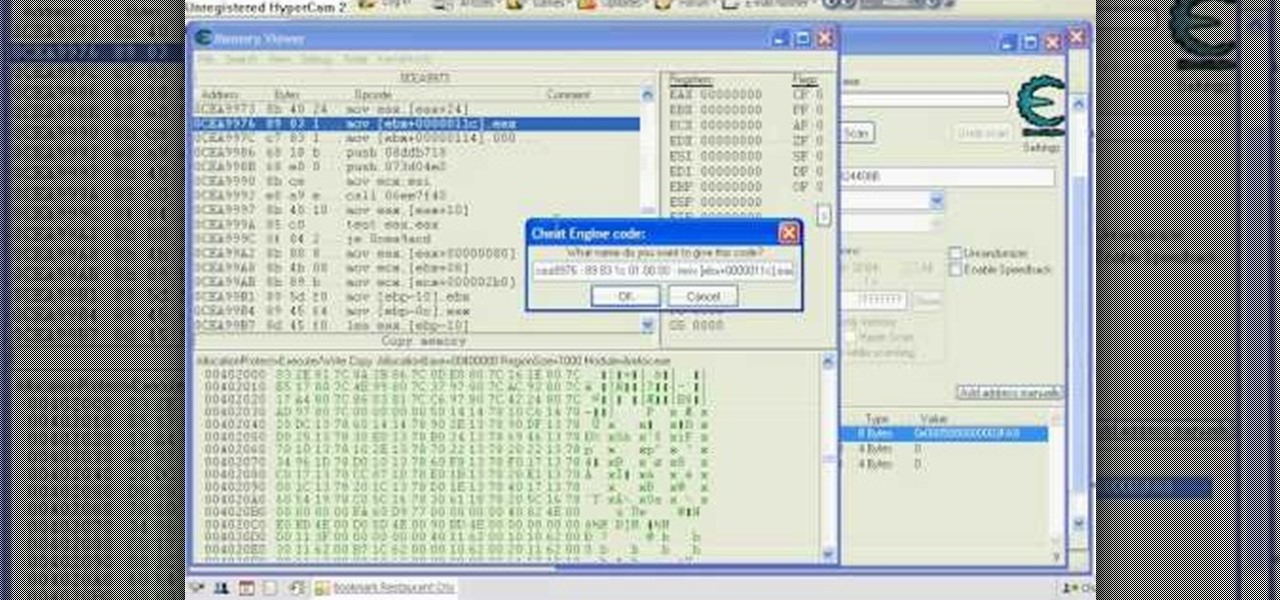
This is the Double Pointer Coin Hack for RC. The tools you need for this hack are Cheat Engine 5.5, Adobe Flash Player 9 or 10, Mozilla Firefox or Flock, and Mouse Recorder.
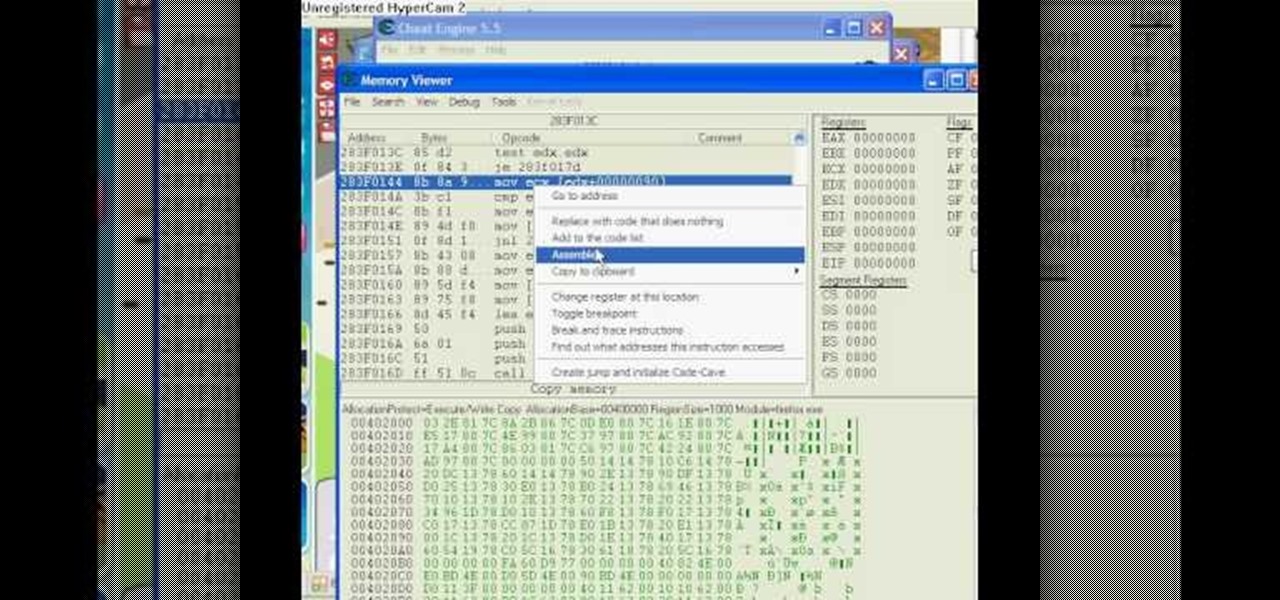
This is a Piaip's and Cheat Engine hack for RC. Restaurant City is a Facebook game that allows you to create and manage your own virtual restaurant. Watch this video tutorial to learn how to hack Restaurant City: Garbage Guru trophy (11/15/09).
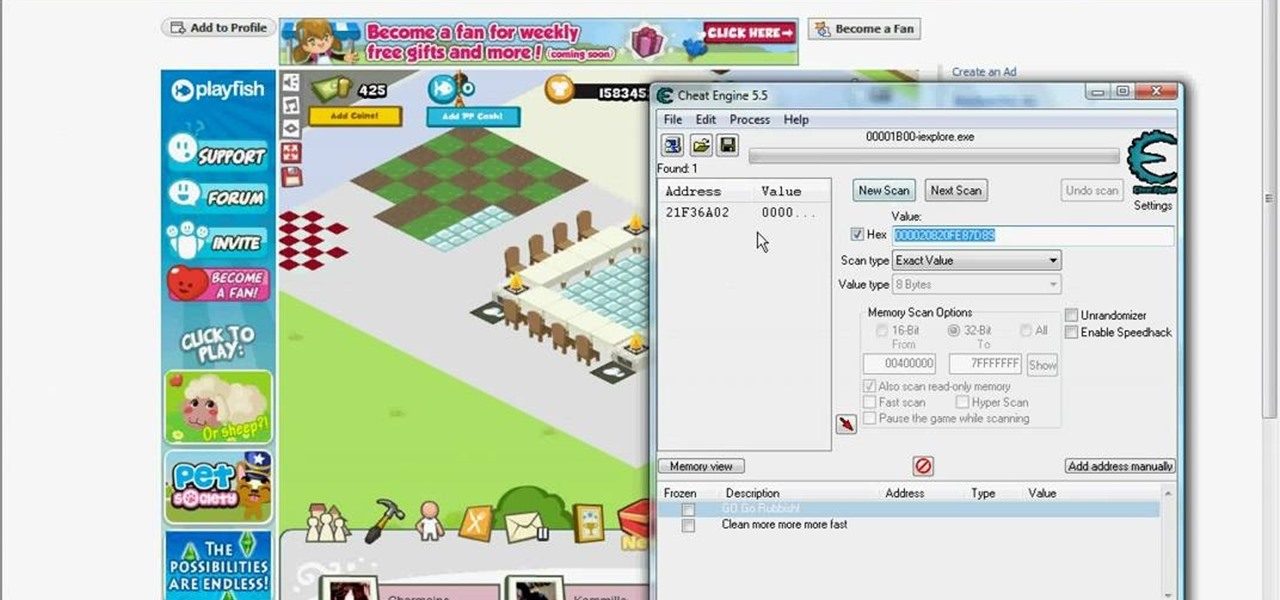
Restaurant City is a Facebook game that allows you to create and manage your own virtual restaurant. Watch this video tutorial to learn how to hack Restaurant City coins (11/12/09). You need Cheat Engine 5.5, RC Tools 5.1, and RC Tools Online.
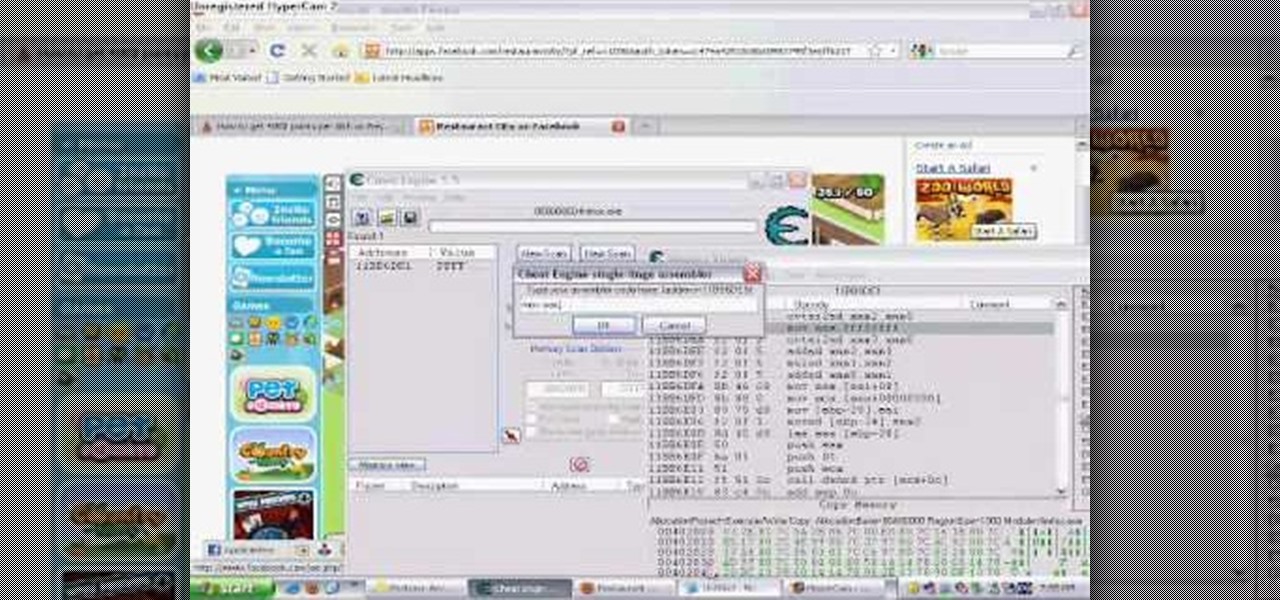
Want to know how to get 4000 gourmet points per dish in Restaurant City? Cheat Engine, that's how. With Cheat Engine, it's super easy to hack RC for gourmet points, so see for yourself.

First download Cheat Engine 5.5. Once you have CE 5.5, you're ready to hack Restaurant City experience. EXP is hard to earn, but not with Cheat Engine… hack it.
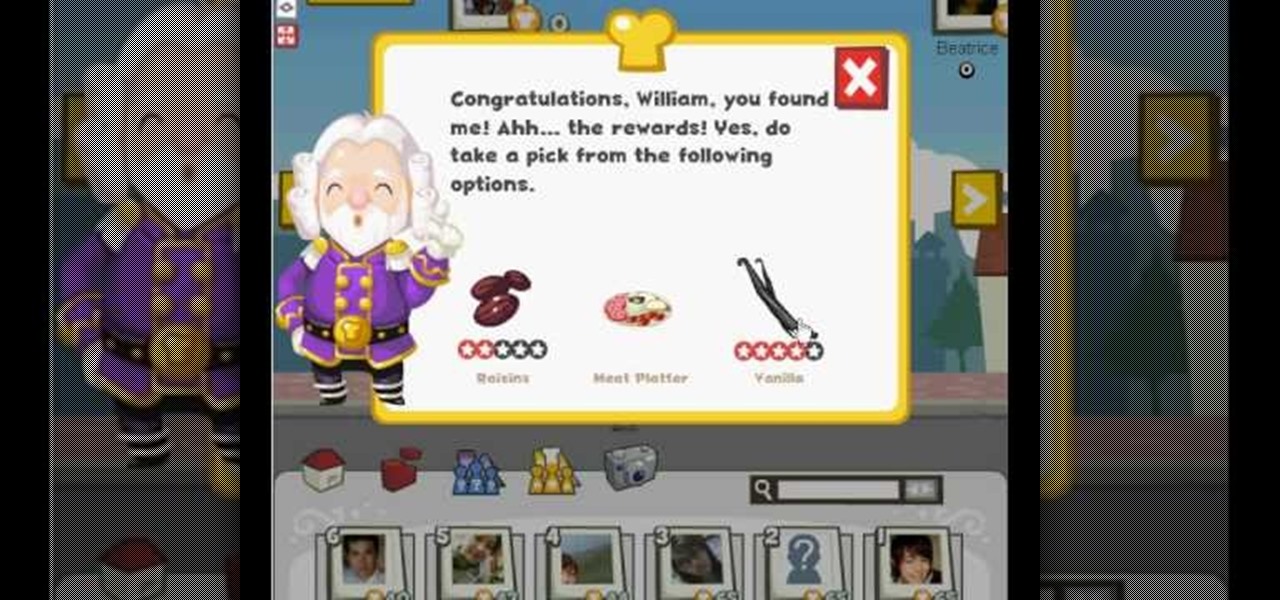
With this Restaurant City hack, you'll find the Gourmet King and get a choice between the following rewards; raisins, met platter, or vanilla. It's pretty simple to do, as long as you have Piaip's RC Hack v2.22.
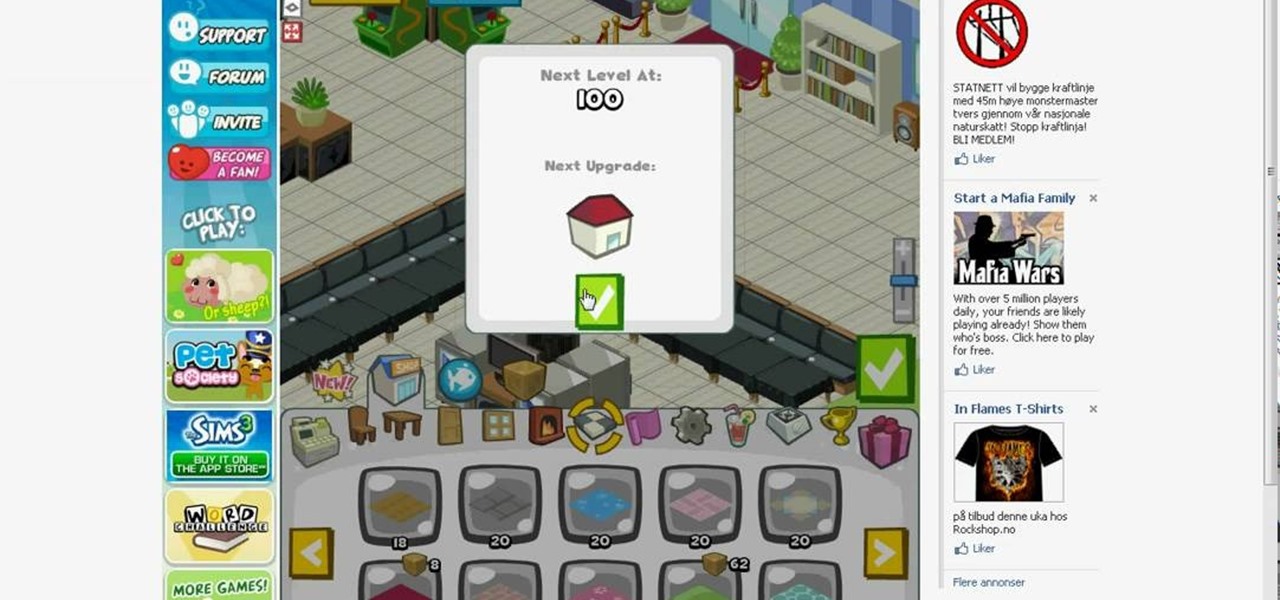
Restaurant City is a Facebook game that allows you to create and manage your own virtual restaurant. Watch this video tutorial to learn how to hack Restaurant City money (11/12/09). You need Cheat Engine 5.5 and the hex is: 00000039840FD285.

Lure luck your way at your workplace by arranging things according to the ancient Chinese design philosophy known as feng shui. De-clutter your desk and workspace, which is the most important thing you can do to balance the _chi_—or energy—in your office. Repair or get rid of anything that’s broken—like a pen that’s out of ink or a flickering desk lamp. They block your chi. The placement of your desk and chair should allow you to see who’s coming into the room. Business and opportunity symbol...

Sometimes you need a password to gain access to an older running Windows system. Maybe it's a machine in your basement you forgot about or a locked machine that belonged to a disgruntled employee. Maybe you just want to try out your pentesting skills.

Every Windows system includes command prompt; and while a lot of people on Null Byte and WonderHowTo in general know how to use it, some people don't know anything about it, even how to access it.
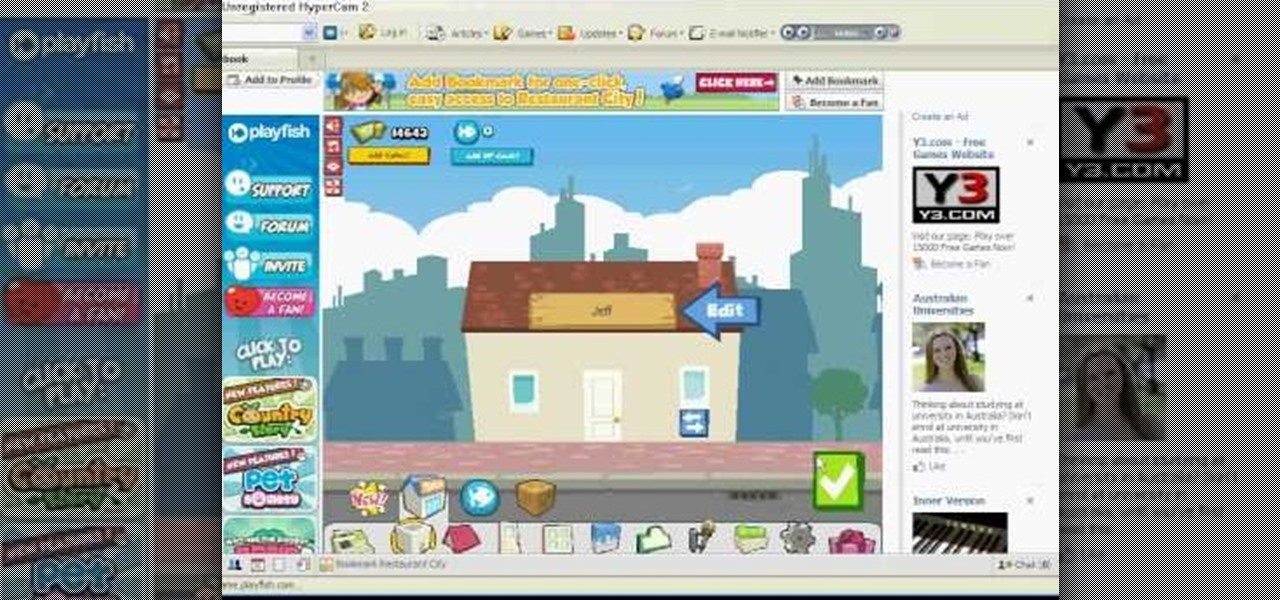
This is the RC Pointer Coin Hack for Restaurant City. You can keep getting coins and coins and coins… it just depends on how long and how far you are willing to go.

Restaurant City is a Facebook game that allows you to create and manage your own virtual restaurant. Watch this video tutorial to learn how to hack millions on Restaurant City (11/15/09).
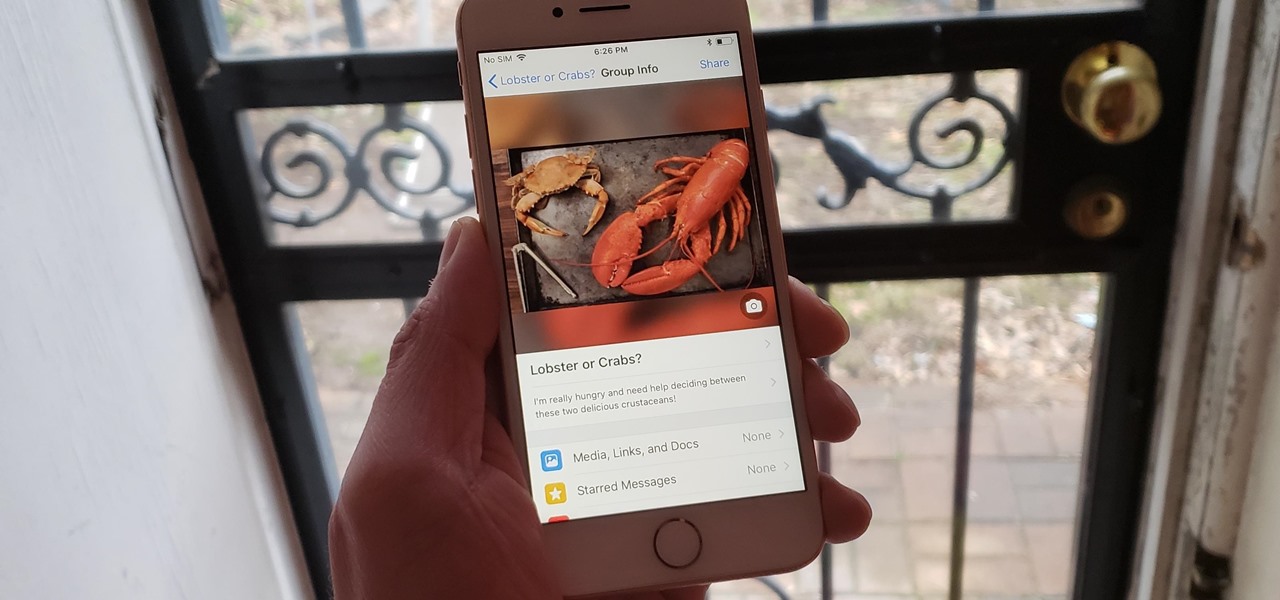
There's a fine line between order and chaos in group chats. With all the cross-talk, threads can easily devolve into a random mess that has nothing to do with the original discussion topic. WhatsApp group chats certainly aren't immune to this problem, but they've recently taken a step in the right direction.

Onshore, or on a boat, have you ever wondered what swims below in the dark water? Using standard equipment and a new process, marine scientists can now get a good look at what is swimming by—just by analyzing the water.
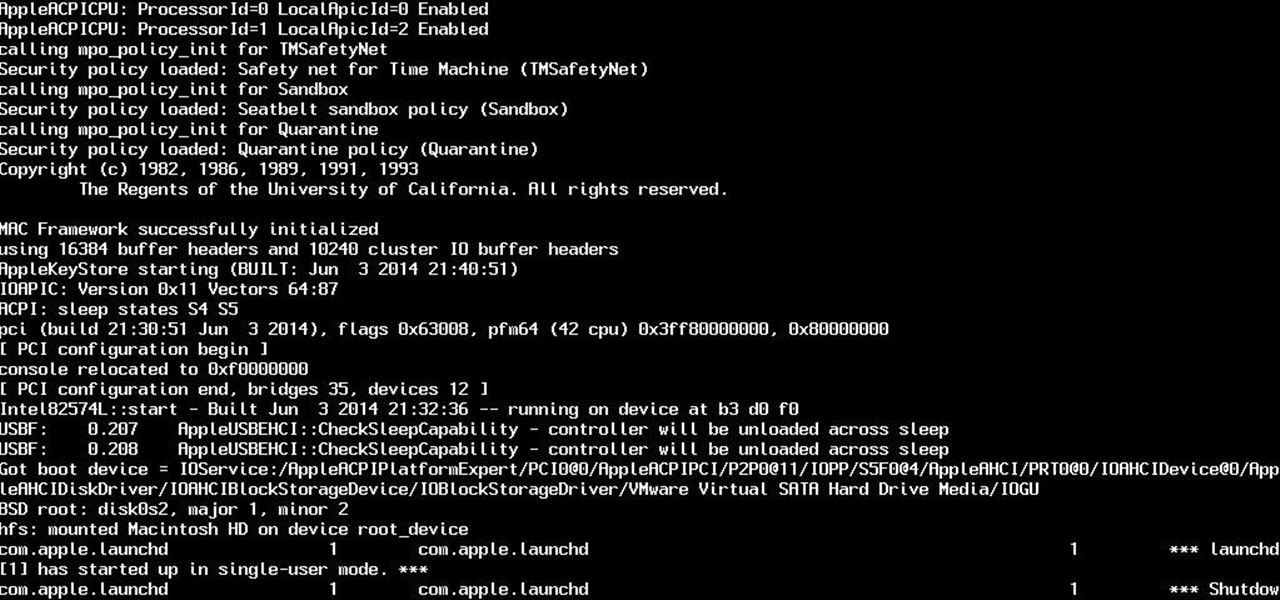
So yeah. Its AugustFackYou and I felt like posting today and being an active member of the community. After reading this please tell me if you have any comments on what I can do better or if this method is bad. Anyway today I will be showing you how to get root on a mac. I managed to become an administrator at my school with this and one other method.

With as much creativity and freedom that we have on Android, it feels a little underwhelming that the only gesture we can perform on the status bar is a downward swipe to expose the notification tray or quick settings. Maybe this is a field for Android to expand on in the future, but until that day, third-party developers are exploring this now.

Ideas can be a fleeting thought, just like a shooting star that appears and disappears within a brief moment. So when you're inspired and have an awesome idea, it's important to jot it down as soon as possible, otherwise it may vanish from your memory for good.

Whether it's because you have nosy family and friends or you're just cautious about losing your device, having a passcode on your Android smartphone is essential for protection. However, you don't always need or want a passcode, especially when you're home alone or in your car on the way to work.

Welcome back, my fledgling hackers! There's an evil dictator hellbent on destroying the world, and in one of our last hacks, we successfully compromised his computer and saved the world from nuclear annihilation. Then, we covered our tracks so no one would know what we did, and developed a hack to capture screenshots of his computer periodically so we could track of what he was up to next.
If you've ever seen something called ThinkPoint Antivirus on your computer, you have gotten one ofhte most widespread and infectious fake antivirus malware programs out there. To get it off your PC, follow the instructions below, or watch this video for an alternate method if this one doesn't work.
This is, by far, the easiest way to root your Android phone, and it's even got its own name— the "SuperOneClick" method. This is a universal technique that applies to most Android-based smartphones (minus the HTC Evo and T-Mobile G2/Vision). TheUnlockr shows you the secret behind rooting your Droid, so watch and learn. Anyone with an Android-enabled phone can do this.
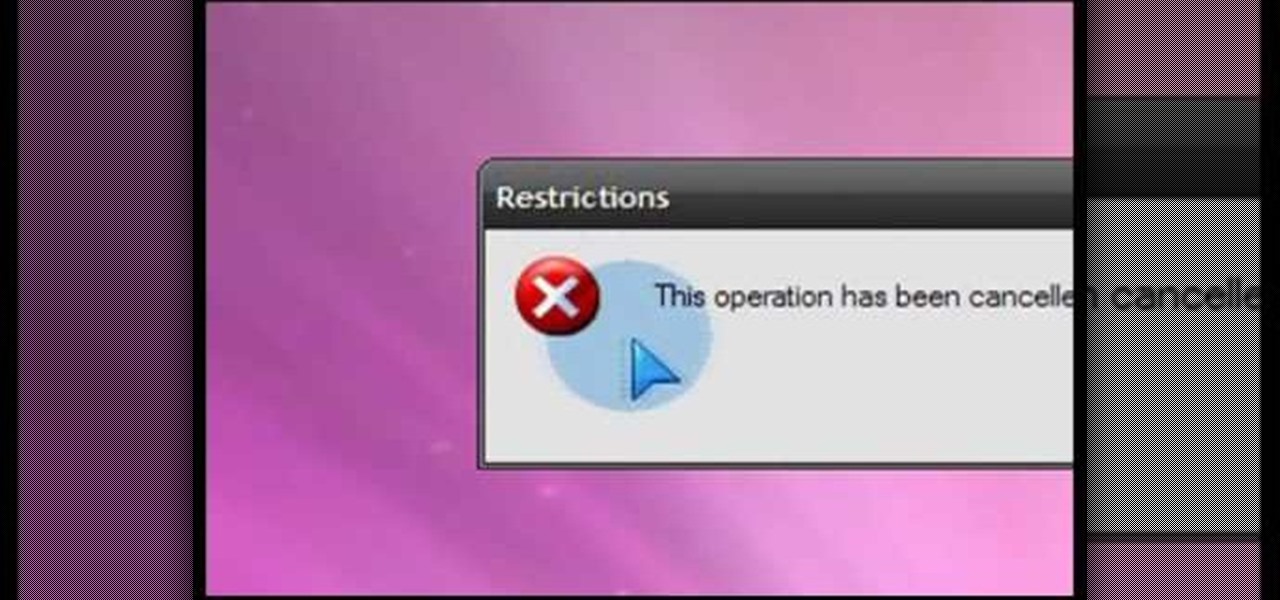
If you love computer pranks, this is one of the easiest ones to pull. This video will show you how to remove the Shut Down button from the start menu in Windows XP. Actually, it does't remove the shutdown button, it just disables it, giving the user a restriction message, stating "This operation has been cancelled due to restrictions in effect on this computer. Please contact your system administrator."
Now that you're officially allowed to do it, jailbreaking your iPhone, iPod Touch, or iPad is a better idea than ever before! This video will show you everything you need to jailbreak a wide variety of Apple devices, including the iPhone 3G and 3GS, the iPod Touch 2G and 3G, and the iPad wifi or 3G model. All you need is a program called Spirit, iTunes version 9.2, and you device and you're good to go! This particular method is great because the jailbreak is untethered, meaning that you can t...
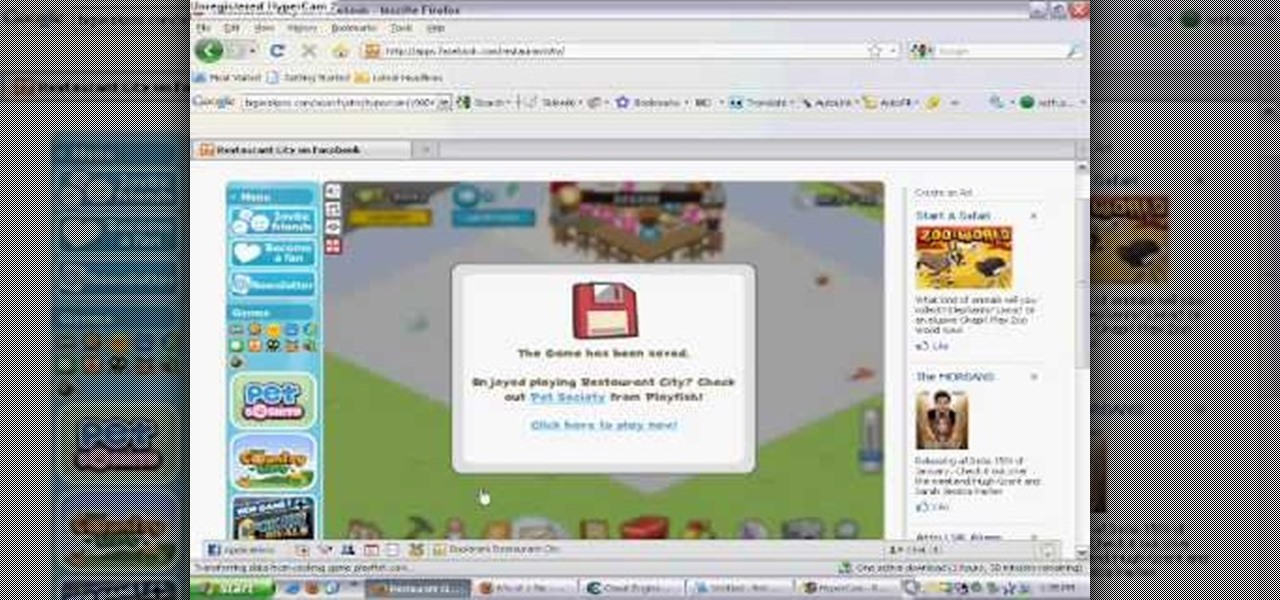
This is one of the easiest Restaurant City hacks out there… the rubbish hack. All you need is Cheat Engine and very little time. Very easy to complete.
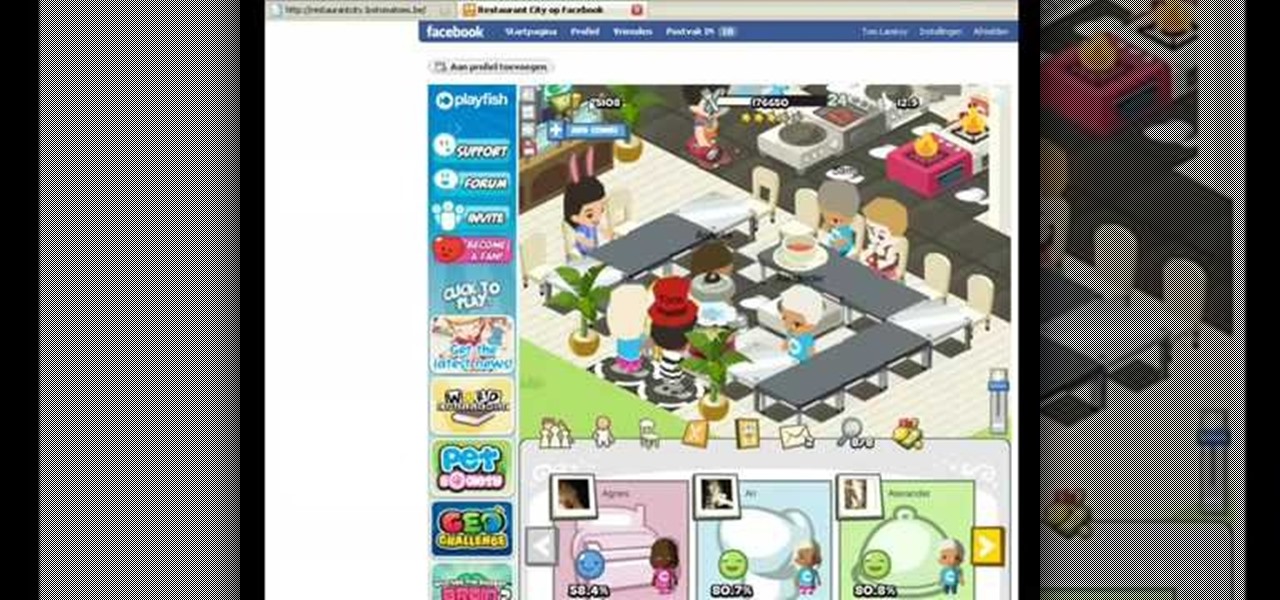
Need a little more cash on Restaurant City? That's easy. Hack money to get your desired amount. Just get Cheat Engine.
The COVID-19 pandemic has hit everyone hard. With over 36 million American workers filing unemployment claims, finances are at the front of everyone's mind. Understanding your accounts has never been as important.

The race for the future of the automative world has never been tighter, with reports earlier this week that Tesla is now almost as valuable as Ford. The neck-in-neck companies are focused on the same next big step for automobiles: the driverless car.

TrueCaller is sharing your phone activity by revealing the last time your phone was used to contacts. The application used to identify unknown callers launched in 2009 and has faced a wealth of privacy concerns before.
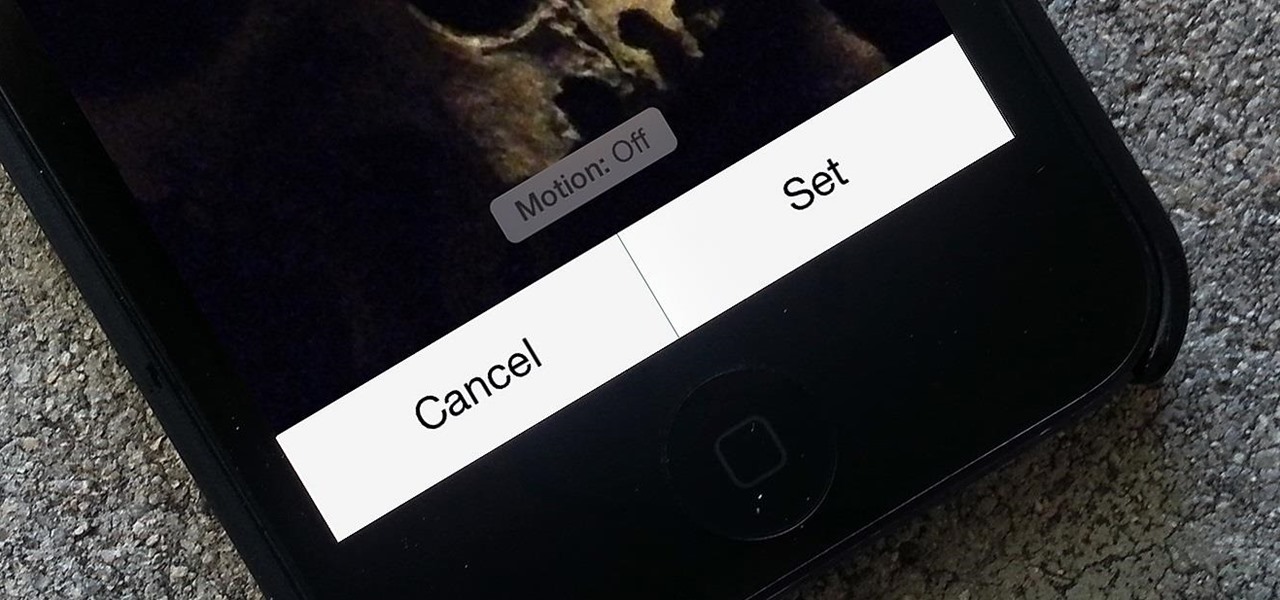
When the first version of iOS 7 was released, there was a wealth of awesome new features, but there was also a lot to complain about. The biggest issue by far was, and still is, how custom home and lock screen wallpapers work on iPads and iPhones.

If an athlete gets athlete's foot, what does an astronaut get? Mistletoe. Yup, that's about the only time I've ever really needed mistletoe for anything, but cheesy one-liners aside, mistletoe can be the greatest wingman (or wingwoman) ever, but only during the holiday season.
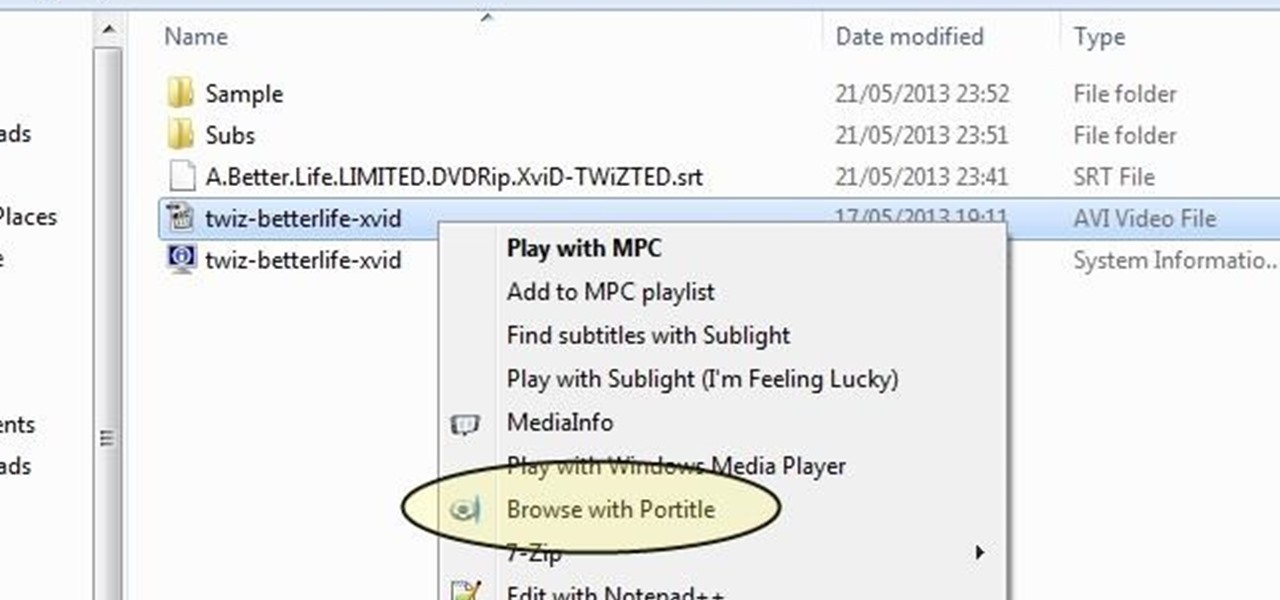
Understand the Problem of Couch Potatoes I have a lot of movies stored on my PC and when I have to finally have the time to watch something, I do not always remember which movie is which. So now I have to google for each movie with the keyboard or search in IMDB.

The internet is a great place to find information for pretty much anything you can think of. So why shouldn't it be a place for official higher learning? I'm not talking about a course in Wikipedia or SparkNotes, but real colleges offering real college courses completely online. And guess what—it's FREE.

In yesterday's tidbit, we learned that across the planet women seek material wealth in their mates. This stems from our hunter-gather past in which females depended on male hunters to provide them and their children the meat necessary to support their large brains.
Open up Cheat Engine and be prepared to hack Restaurant City! This is a new level hack that will help you gain levels fast.

Automating port scanners, directory crawlers, and reconnaissance tools can be complicated for beginners just getting started with Kali Linux. Sparta solves this problem with an easy-to-use graphical interface designed to simplify a penetration tester's tasks.

After exploiting a vulnerable target, scooping up a victim's credentials is a high priority for hackers, since most people reuse passwords. Those credentials can get hackers deeper into a network or other accounts, but digging through the system by hand to find them is difficult. A missed stored password could mean missing a big opportunity. But the process can largely be automated with LaZagne.

Locking individual apps on your Android device gives you an added layer of security by safeguarding app data from unwanted attention. I personally prefer using an app locker over a standard lock screen because my kids play with my phone, and they've completely disabled it after inputting the wrong PIN. So app lockers give me the right balance between giving my children access to my device, and the security of locking down my data from would-be intruders.

In this tutorial I am going to show you how to create an undetectable Meterpreter Trojan using a Domain name. I have taken a few guides/tutorials and built it into one. The first part is creating the DNS Payload. The second part is creating the Executable file. Part 3 is using both in Shellter to create your undetectable Trojan. Part 4 is setting up your listener using Armitage.