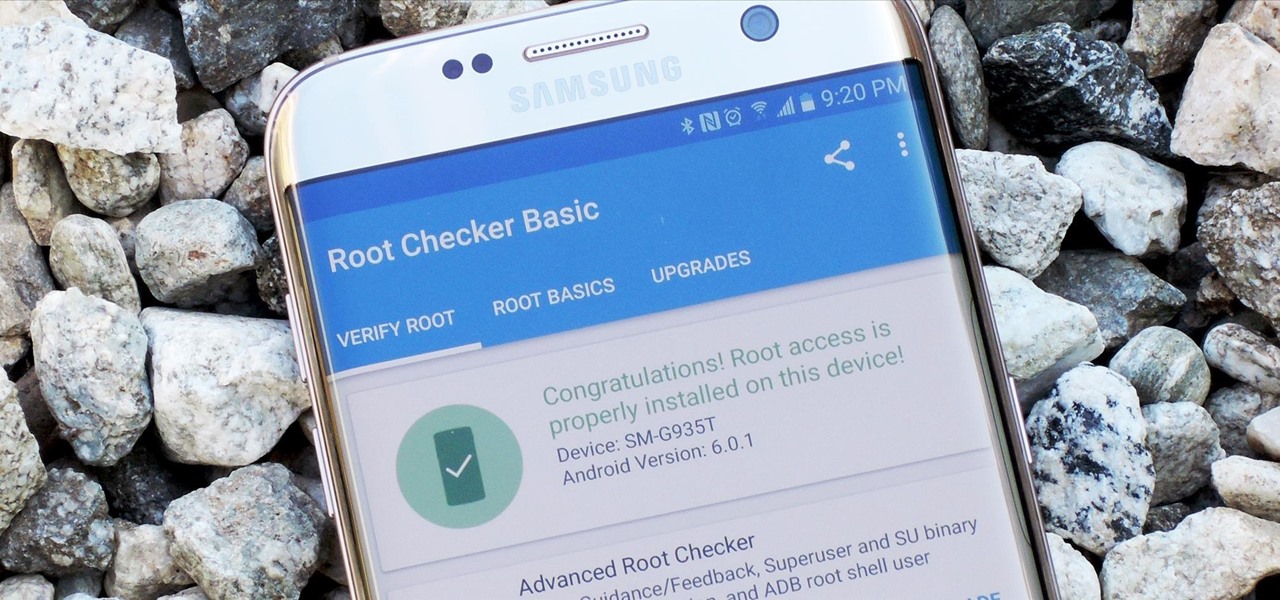
Samsung's 2016 flagship devices are some of the most beautiful, powerful smartphones ever made. And amazingly enough, thanks to legendary root developer Chainfire, the Samsung Galaxy S7 and Galaxy S7 edge are about to get even more powerful.

Welcome back, my fledgling hackers! It's been awhile since we did a Metasploit tutorial, and several of you have pleaded with me for more. I couldn't be happier to oblige, as it's my favorite tool. For the next several weeks, I'll intersperse some new guides that'll help expand your Metasploit skills and keep you abreast of new developments in Metasploit, so look for them in the near future.

I hope you haven't updated past here if you want to jailbreak your iPhone. Jailbreaking gives you access to many open ended applications and games. This video will demonstrate exactly how to jailbreak and unlock your iPhone 3G/3GS firmware 3.1.2 and 5.11.07 baseband.
This video describes how to create a new account on Windows 7. In this video it is shown the whole procedure and all you need to know to crate new user account.
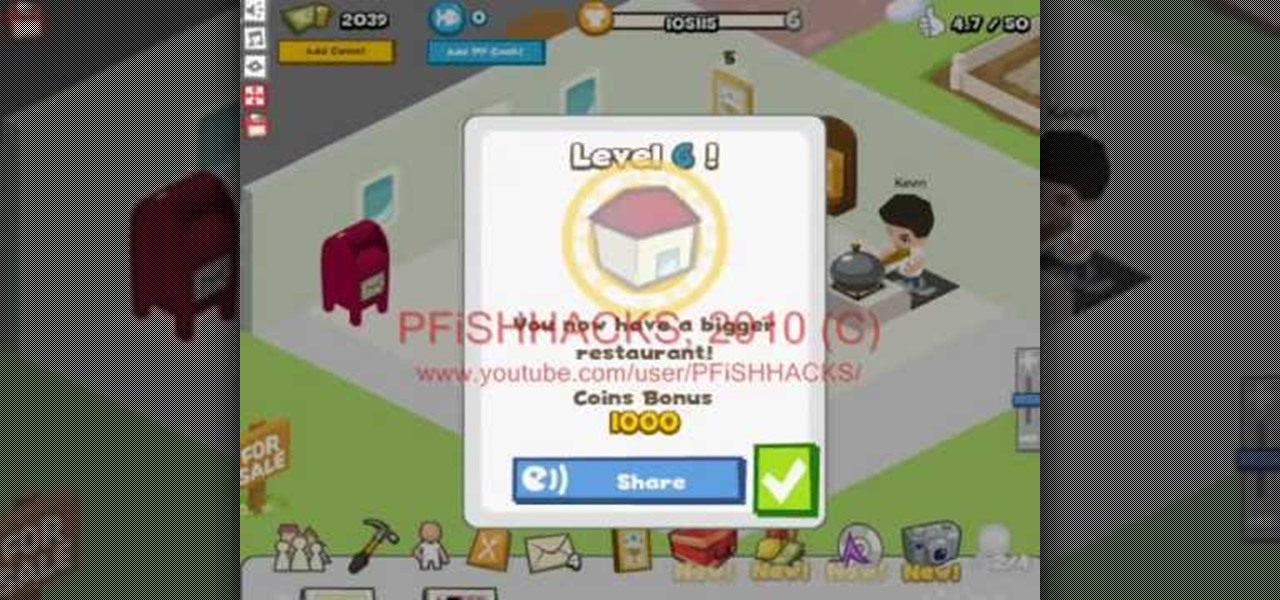
Want to be the John (or Jane) D. Rockefeller of Restaurant City? Watch this video tutorial to learn how to hack Restaurant City with Cheat Engine 5.5 (02/04/10).
Want to play your video collection on any media extender, console or AppleTV? Step one is to get your movies off of the DVDs and onto your hard drive! If you're like most people you probably have a huge library of DVDs that you've bought and collected over the years. Unfortunately, it's an inconvenient format if you want to playback all that content anywhere around the house. So, learn how to rip and encode that stack of DVDs into a format that you can play on your Windows Media Extender, set...

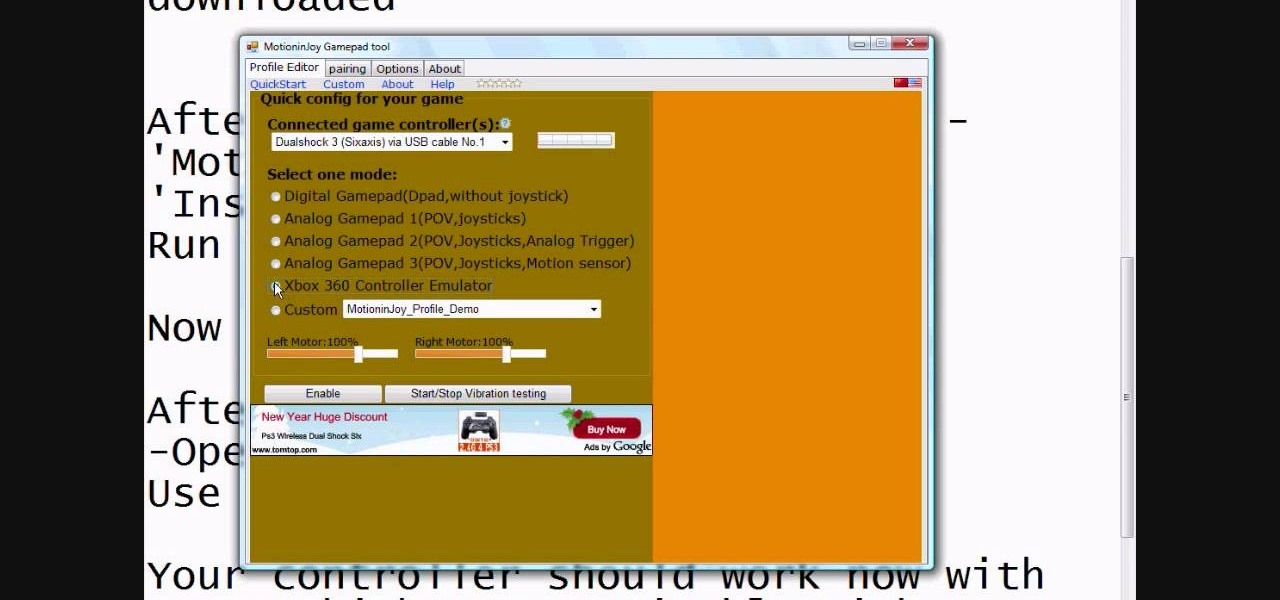
This video tutorial from radeon4350 shows how to connect dualshock PS3 console controller to PC. First, download driver software from here: http://www.motionjoy.com/download

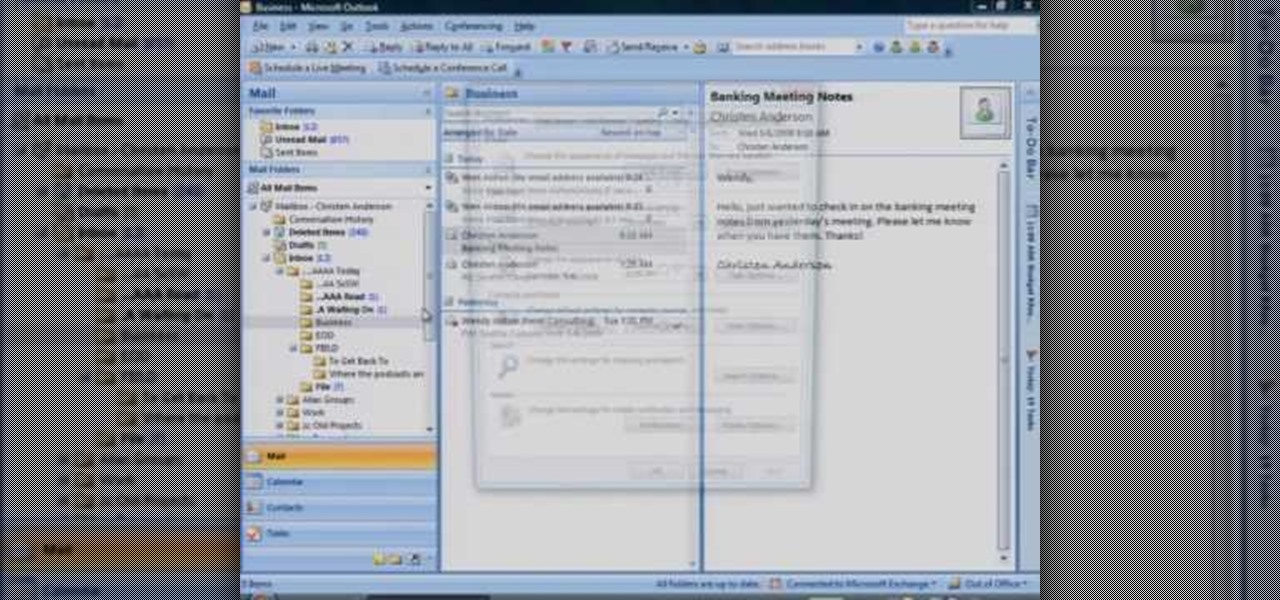
In this how to video, you will learn how to check your voice mail in Microsoft Office Outlook. Your exchange administrator must enable unified messaging for these messages to appear. First, open the program to set up your voice mail options. Go to options and click the voice mail tab. Your phone number should appear in the correct form. Click call to check your voice mail. Enter your number and click x and okay. Now you are ready to listen to your voice mail messages on your computer. From Ou...

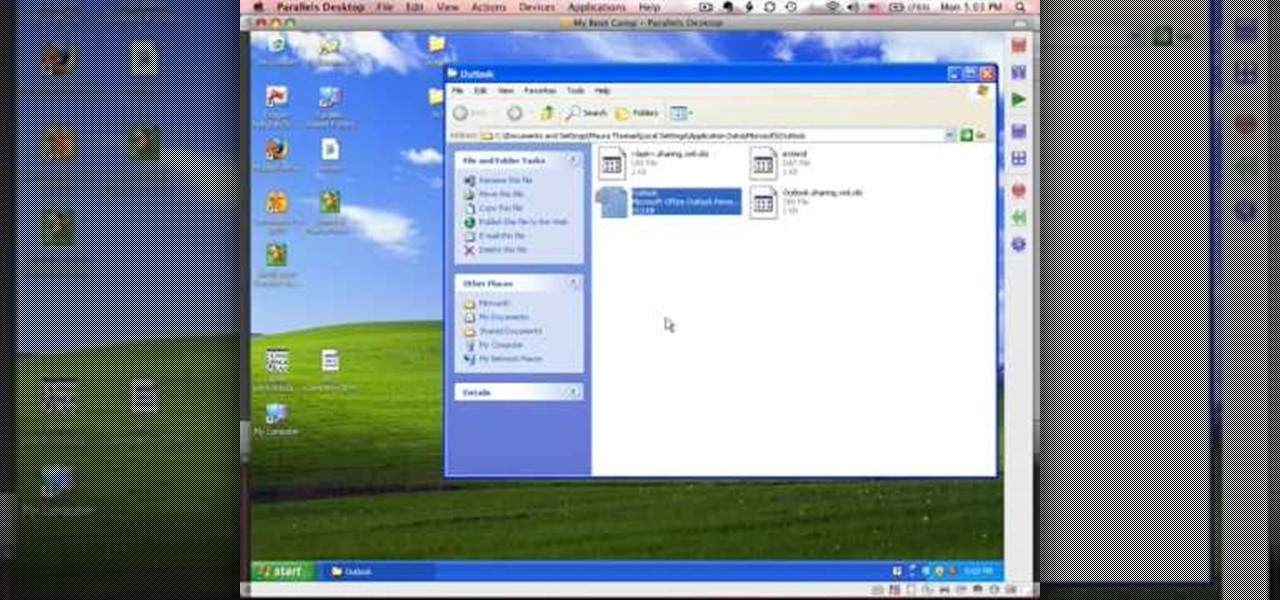
This tutorial describes how to backup the PST file of Outlook.

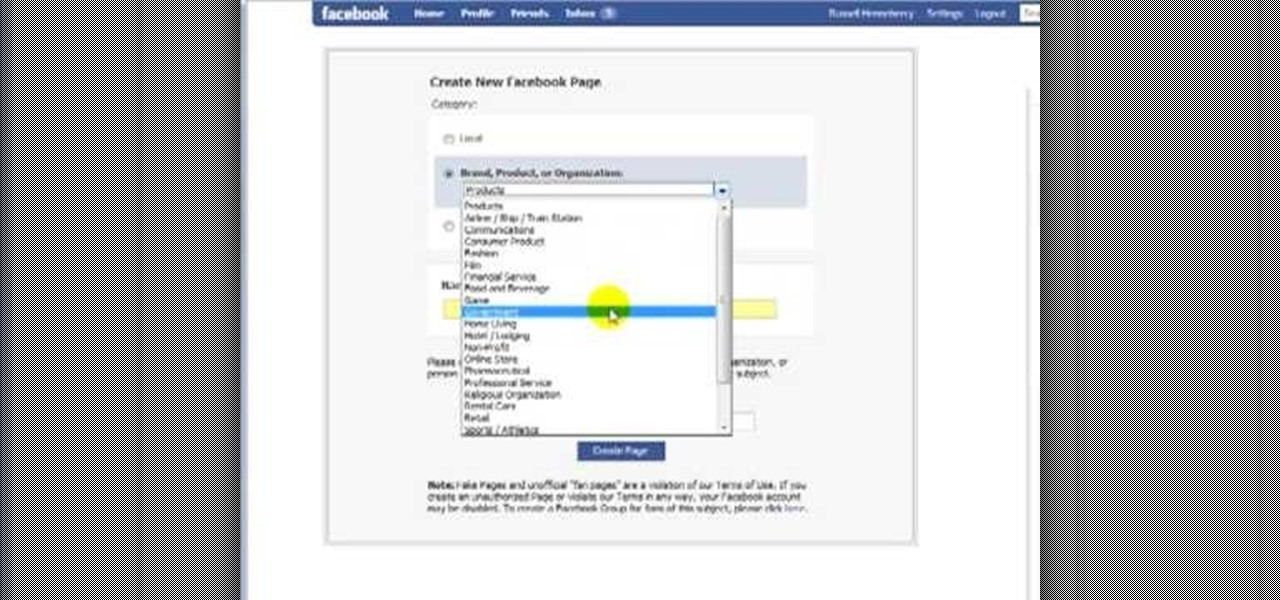
First, you must log on to your personal face book page or create one if you do not already have, but don't log in yet. Then at the bottom of the face book home page click the click here sign within the words to create a page for a celebrity, band, or business click here. Now that you are on this page log in. You will be able to select what you are. Enter name of your website, now select that you are authorize to create this page. You must then enter your electronic signature, which is the exa...

Nmap ("Network Mapper") is a free and open source (license) utility for network exploration or security auditing. Many systems and network administrators also find it useful for tasks such as network inventory, managing service upgrade schedules, and monitoring host or service uptime. Nmap uses raw IP packets in novel ways to determine what hosts are available on the network, what services (application name and version) those hosts are offering, what operating systems (and OS versions) they a...

It looks as though the novel coronavirus and social distancing guidelines are here to stay for a while. So companies of all sizes and industries are scrambling to adapt to a new reality in which everything from morning meetings to large-scale presentations are done entirely online. It looks like this is going to be the new normal for the foreseeable future.

UAC is something we've all dealt with on Windows, either as a user, administrator, or attacker. It's a core feature of the Windows security model, and for the most part, it does what it's supposed to. But it can be frustrating as a hacker when attempting privilege escalation, but it's easy enough to bypass UAC and obtain System access with Metasploit.

Augmented reality and computer vision company Blippar has a new lease on life, as previous investor Candy Ventures has completed a successful bid to acquire the assets of the beleaguered company.

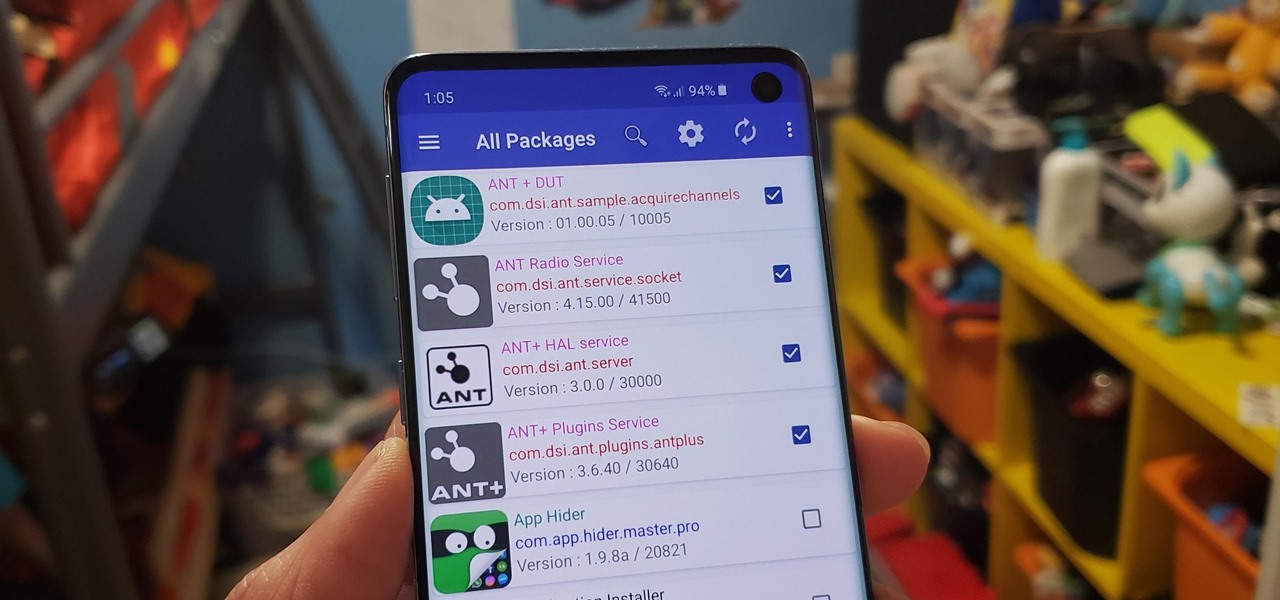
Bloatware remains one of the biggest problems with Android, especially when tied to a carrier. Removing bloatware usually requires you to take extreme measures like rooting. Unfortunately, the Galaxy S10 falls under this annoying umbrella, but there's an easy workaround.

This is a how to to change any user password on a windows 7 computer. If you forgot your password you can change any account password even if you are locked out of your account.

Let's say you got a little careless while installing apps from unknown sources, and now your Android device has been infected by malware. Or perhaps your friend has come to you for help after they had haphazardly installed random apps until their phone was filled with popups and garbage like that.

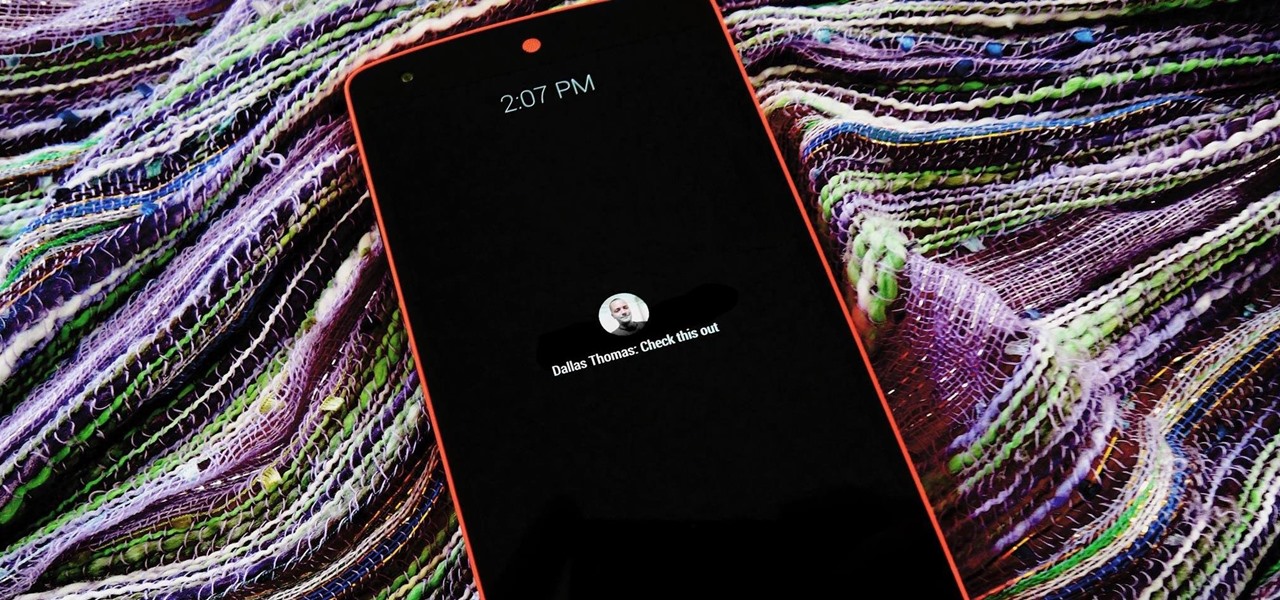
The act of viewing a new notification on your Nexus 5 can feel a bit clunky and cumbersome at times. When a new message comes in, you hear the notification sound, you see the LED blinking, but you can't see what the actual notification says without waking the device and opening the notification tray.

A few days ago I finally finished my 2 week journey into trying to get OpenVas to work properly. You all may have noticed that you can't just click the setup openvas in kali and have it working properly.

Welcome back, my greenhorn hackers! Earlier in this series, I showed a you a couple of different ways of fingerprinting webservers. Probably the easiest way, is to use netcat and connect to port 80 and pull the webserver banner.

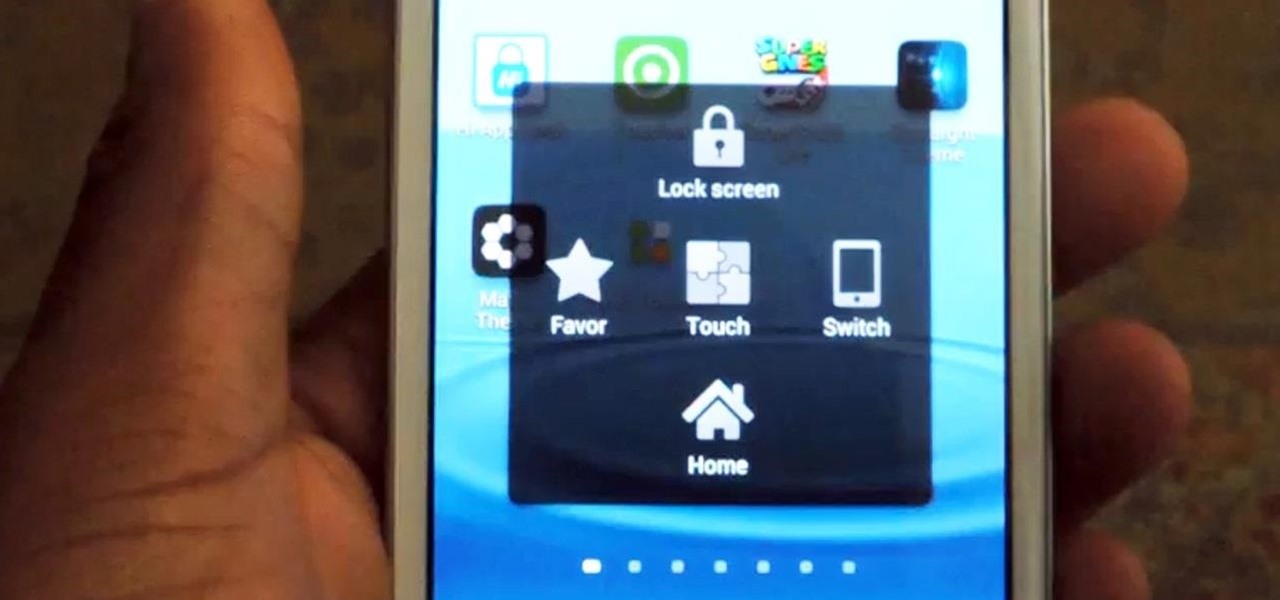
Dorothy had it right: "There's no place like home." This is especially true when it comes to using your Samsung Galaxy S3, or pretty much any other smartphone, whose most vital button is the Home key.

Welcome back, my tenderfoot hackers! In some of my past articles, I've shown numerous ways of embedding a listener/rootkit on a remote system, including buffer overflows of the operating system, getting the victim to click on a link to our malicious website, and sending a malicious Microsoft Office and Adobe Acrobat file.

There is so much information in the world that trying to make sense of it all can be daunting. That's where data analytics comes in. By learning how to inspect and model data, you can take large data sets and transform them into highly valuable information that can take any business further.

You never want to stop learning. Whether you're facing a career pivot or want to better understand the vocation you've chosen, there's always room for growth. The most successful workers are those who make education a lifelong pursuit.

With the addition of the OpenSSH client and server in the Windows 10 Fall Creators Update, you no longer have to rely on third-party programs to open an SSH server and connect to a Windows machine. While still a beta feature, this represents a long-overdue update fulfilling a promise made back in 2015.

I.M. Healthy Original Creamy SoyNut Butter was recalled on March 4 after being linked to 16 Escherichia coli cases in nine states. Montessori of Alameda preschool in Portland is the latest victim in a multi-state E. coli outbreak caused by the nut-free butter.

The headsets of tomorrow offer some amazing possibilities in both gaming and work, but what we've seen so far only begins to scratch the surface. The US Navy saw the potential to use augmented reality in a helmet to provide divers with an incredible amount of information we have so far only seen in Hollywood movies.

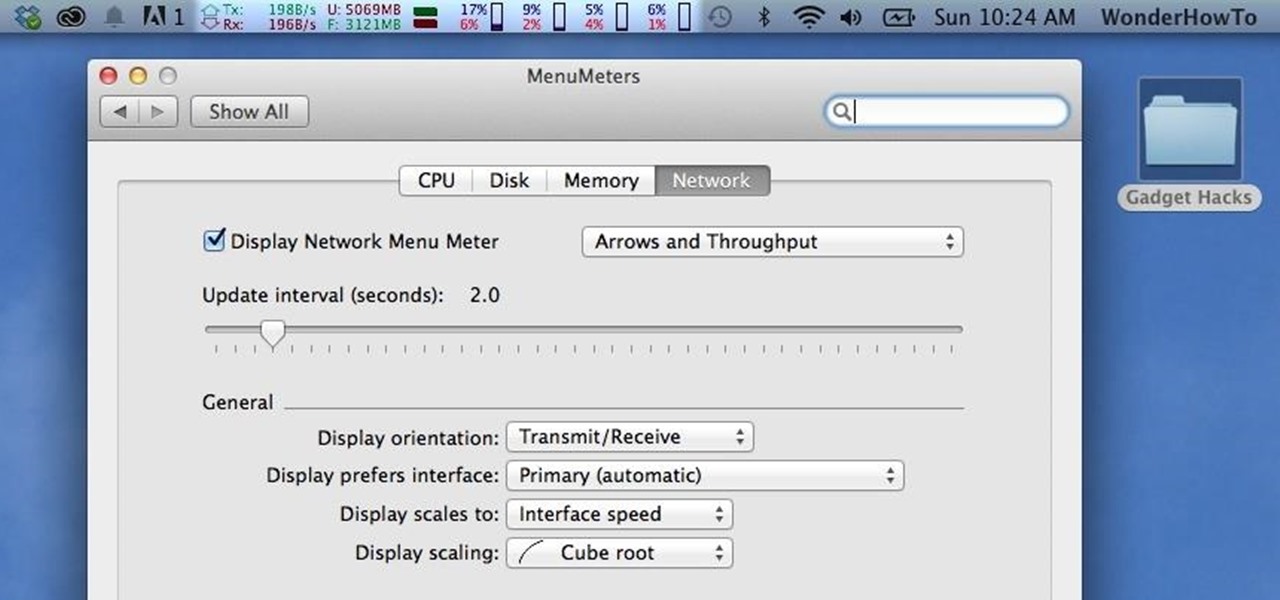
Like a car, your Mac needs to be monitored and cared for to keep it running as smoothly as possible. While your vehicle comes with a ton of gauges to keep track of your oil, temperature, and in some cases, even tire pressure, your Mac has no easy way to watch for low memory or high disk usage. Normally you would have to open up Activity Monitor to take a look at your usage stats, but now there is something better.

While the Play Store has a plethora of apps available for finding lost Android phones, Google came out with its own web-based application, Google Device Manager, earlier this year to help you keep track of all your Android devices and remote lock, erase, ring, and track if need be.

While websites may run smoothly without any noticeable vulnerabilities, there's always the looming threat that any background weakness in the site can be exploited by hackers. Once a site is compromised, it can be difficult to get it fixed without the proper help. Google has recently launched a new series entitled "Webmasters help for hacked sites”, which teaches web developers and site owners how to avoid getting hacked and how to recover their website if it gets compromised in any way.

In the Windows 8 Enterprise edition, you can use the Windows to Go feature to travel with Windows 8 OS, personal files, documents, settings and many more. All you need is an external hard drive or USB drive of 32 GB space or more and USB 3.0 support or more for fast Windows 8 booting. We need the storage media of above specification to create bootable USB to access the data anytime by plugging the media into different PC running latest version of Windows 8 PRO or Windows 7.

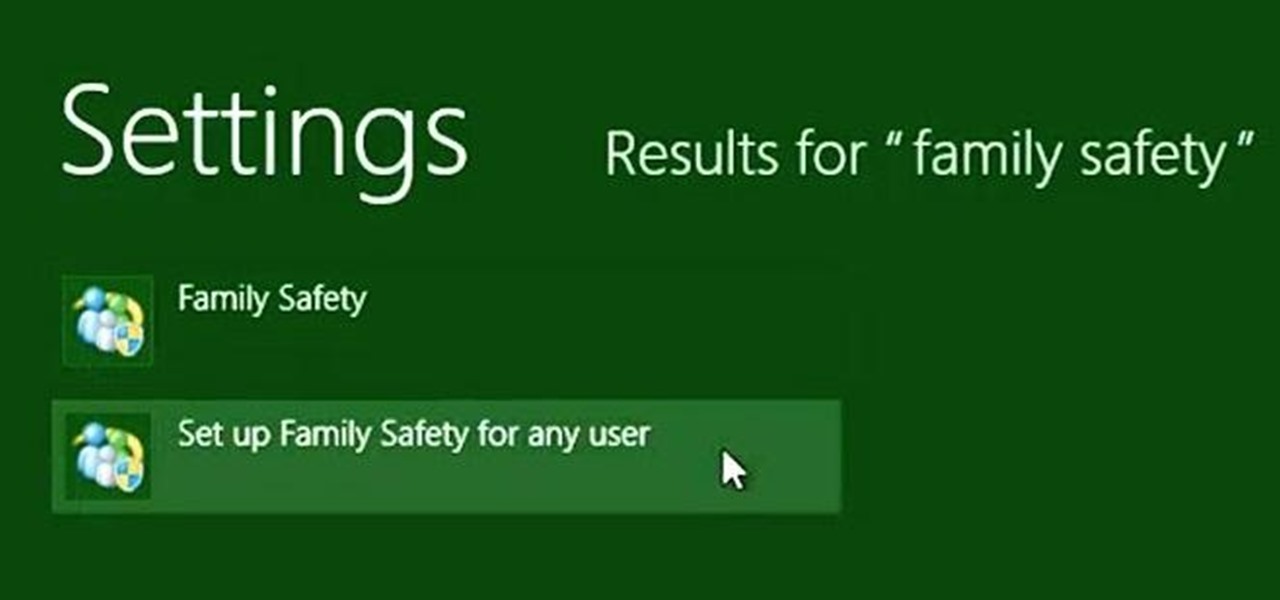
The internet is full of information and entertainment, but if you have children, you might want to put a cap on what sites they have access to. While it may be a free world out there, it doesn't mean that little Mickey should be free to roam the web during his downtime (or uptime, if you know what I mean).

Configuring user accounts is extremely important for those with a family shared computer or anyone using a work computer. Assigning different accounts with their own distinctive accessibility, customizations, and applications is the best way to manage a computer with multiple users.

It always sounds like a good idea to throw a party... until the party gets there. Next thing you know, you're running around hiding anything breakable, and once everyone leaves, you're stuck cleaning up the mess. But the worst part is footing the bill for everything, and if you don't charge at the door, your chances of getting anyone to chip in are slim to none once the party starts.

Confused by TikTok? Trying to grow your Instagram fanbase? Aiming to create the perfect Facebook ad? Growing an audience might be challenging, but with the right strategies, it is possible — and fun.

As we settle into our new normal, this extra time provides a perfect opportunity to learn new skills. Speaking a foreign language is a great way to expand your cultural boundaries while also training your brain. Not only will you pass the time more effectively, but you'll also be doing something positive for your health.

The iPhone X is Apple at its most classic — they take away a key feature that seems odd at first, but usually, the change pans out in the end. So is the case for the long-lived Home button, whose last appearance may be on the iPhone 8 and 8 Plus. That begs the question — how do you use an iPhone without a Home button?

The good news keeps on coming for Samsung! According to the market research firm Strategy Analytics, the Korean giant sold a whopping 7.2 million Galaxy S7 and S7 Edge smartphones in the first quarter of this year. That totals 55 million of the company's flagship smartphones sold since their launch in March 2016.

Soy sauce is a sushi essential for most Americans and we don't often consider its exact origins whilst chowing down on that tuna roll.

Today, at Abundance 360, an exclusive event for tech entrepreneurs in Beverly Hills, California, Boston Dynamics unveiled a video of "Handle," a humanoid-like robot with wheels instead of feet.