Whenever I go to Jamba Juice, I usually gravitate towards either the Matcha Green Tea or Caribbean Passion smoothies. But when I learned about their secret menu a few years ago, I felt like a little kid all over again—especially with flavors like Pink Gummy Bear and Orange Dream Machine.

Recently I've been looking around our wonderful community and I've seen some absolutely hands-down fantastic python scripting articles. But, in the end, these series weren't very extensive. I've been wanting to do a series on teaching python for a while now, and I don't mean just the basics, I mean to make an extensive series that takes it all the way from "Hello, World!" to popular third party modules, and everything in between!

Most of you already know that a zero-day exploit is an exploit that has not yet been revealed to the software vendor or the public. As a result, the vulnerability that enables the exploit hasn't been patched. This means that someone with a zero-day exploit can hack into any system that has that particular configuration or software, giving them free reign to steal information, identities, credit card info, and spy on victims.

We never have a wealth of cheese leftovers in my house since we love the stuff so much, but I'm always happy after a cocktail party if we do, because I know I can turn it quickly and easily into fromage fort. To create this incredible French spread, all you need to add to your cheese scraps is a clove of garlic and some white wine.

If you've ever used IFTTT, you know how well it can automate your online world. The premise is simple—If This, Then That—but the results are powerful. From automatically printing images based on hashtags to getting around Twitter bans, the service is quite useful with a wealth of possibilities.

If you're a dedicated Instagrammer, you're probably well aware of the humblebrag hashtag #NoFilter, which expresses to other users that your photo is just so damn awesome that it looks like you added filters to it, even though you really didn't.

One of the best features on the new Moto X is Touchless Control, which lets you verbally ask the device questions or perform tasks without ever touching or turning on the display, a feature that would do quite nicely on the Nexus 7, if it could handle it.

Always downing a glass of red wine in the evening? Don't be ashamed. Red wine has some great health benefits when consumed in moderation, including improved memory, lower risk of heart disease, and even bone strengthening. Photo by Joe Shlabotnik

It's summer, which means vacations, barbeques, and, most importantly, no school. But that doesn't mean you can't learn something while you lounge by the pool. Schools and organizations all over the country are offering online courses taught by real professors—for free.

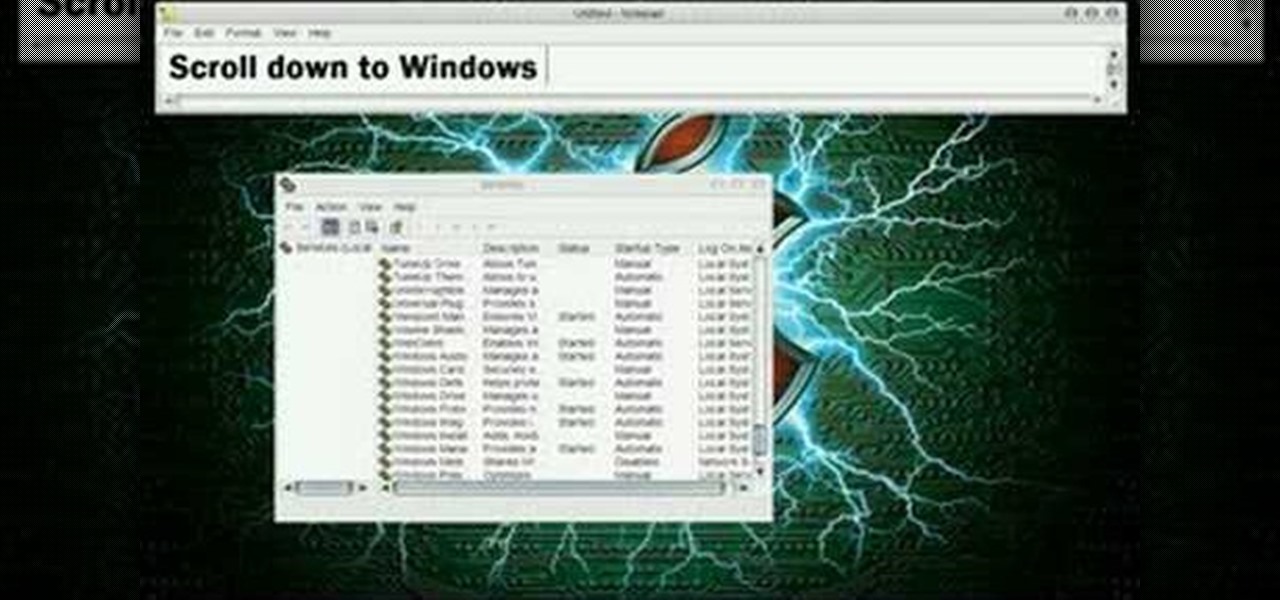
In this video tutorial, viewers learn how to turn off the system firewall without admin privileges. Begin by clicking on the Start menu and open he Run program. Type in "system.msc" and click OK. Scroll down the Services list and look for Windows Firewall. Double-click on it and under the General tab, click on Stop. Then click Apply and OK. This video will benefit those viewers who use a Windows computer and would like to turn off the firewall, even if they are not running the administrator a...

It has often been said that the only constant is change. IT's ability to manage change is an important business success criteria in today's competitive markets. Change can either be planned or unplanned. This presentation will help you understand the effects of change, and how to manage change properly. It will help Oracle database administrators better prepare to implement changes and measure the positive (or negative) affects those changes produce on the system.

Compromised uTorrent clients can be abused to download a malicious torrent file. The malicious file is designed to embed a persistent backdoor and execute when Windows 10 reboots, granting the attacker remote access to the operating system at will.

Passwords on Windows are stored as hashes, and sometimes they can be tough to crack. In certain situations, though, we can get around that by using the hash as is, with no need to know the plaintext password. It's especially interesting if we can manage to get the hash of an administrative user since we can then authenticate with higher privileges by performing an attack known as pass the hash.

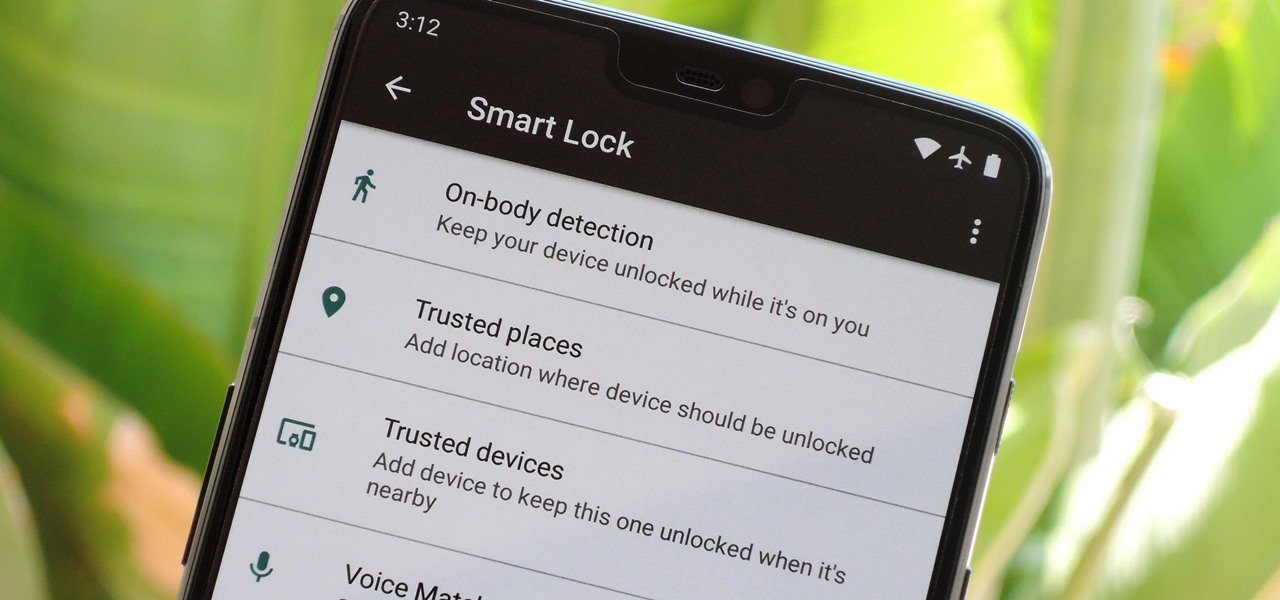
When it works, Android's Smart Lock feature is incredible. There's no need to enter your PIN when your phone "knows" it's in your hands — just unlock and go. But Smart Lock, particularly its Trusted Places feature, can be finicky sometimes.

Configuring onion services for the first time can be tricky. A surprising number of system administrators make seemingly trivial mistakes that ultimately lead to catastrophic cases of de-anonymizing supposedly anonymous sites on the dark web. OnionScan is a tool designed to identify common misconfigurations in onion services and aid us in understanding how to fix them.

A remote administration tool, or RAT, is a piece of software used for remotely controlling machines. They are commonly used by tech support to gain remote access for troubleshooting purposes, but RATs are also an important part of a hacker's advanced persistent threat (APT) toolkit. Unlike standard administration RATs, these tools are designed to be delivered stealthily and operate undetected.

Windows 10 has so many new features that we couldn't even cover them all with one article. From keyboard shortcuts to revamped search functions and all-new window gestures, Microsoft definitely piled on the fresh functionality in the latest version of their operating system.

Welcome back, my budding hackers! People often ask me, "Why are you training hackers? Isn't that illegal?" Although I usually give them a short version of this post, there are MANY reasons why YOU should be studying hacking.

Apple may have made Mavericks more accessible to Mac users everywhere at the fair price of zero dollars, but unfortunately, they made it trickier to create a bootable install drive of the Mac OS X 10.9 operating system.

Welcome back, my hacker novitiates! Many of you have probably heard of a man-in-the-middle attack and wondered how difficult an attack like that would be. For those of you who've never heard of one, it's simply where we, the hacker, place ourselves between the victim and the server and send and receive all the communication between the two.

Want a cool 3-in-1 hack for Restaurant City? Go no further. You don't even need Cheat Engine for this one! Just Piaps Restaurant City Hack.

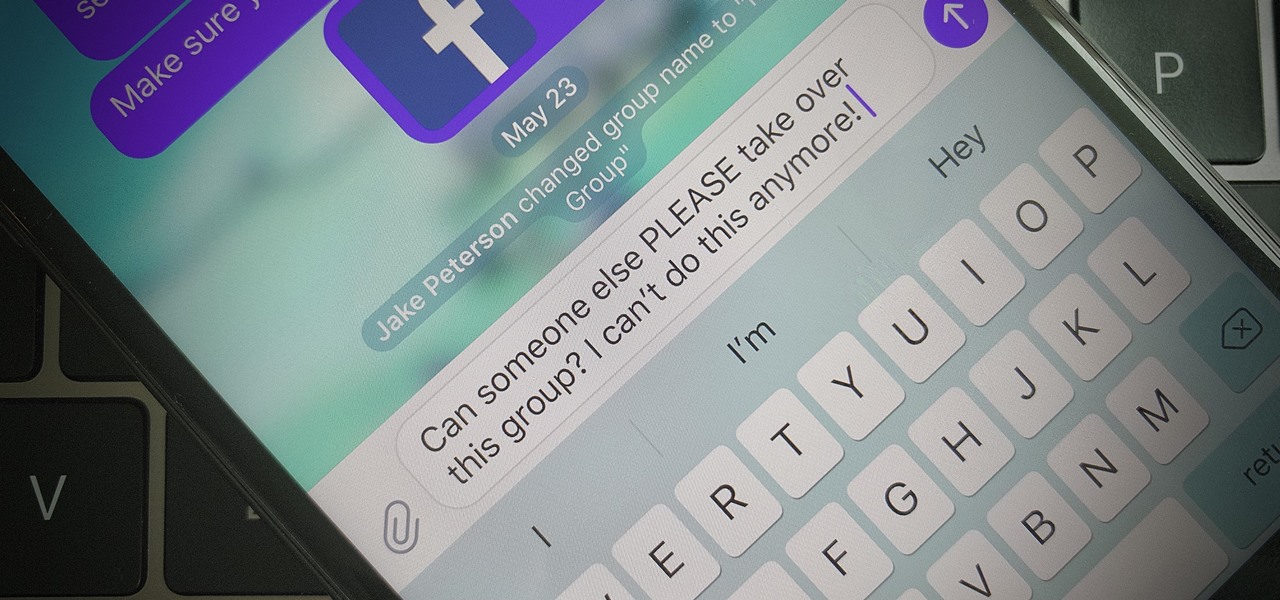
Group chats are fun, effective ways of staying in touch with the many people in our lives. Whether it's the local friend chat or the group from work, we rely on these groups to keep connected. Running one of these group chats, however, can be a monster task. If you're feeling overwhelmed with administrative responsibilities, why not pass on that burden to another member of the Telegram group?

The HoloLens has made enough of an impact on the healthcare industry for Microsoft technology partner Medivis to convince investors to pledge $2.3 million in funding for its surgical platform.

Despite funding difficulties that forced Meta to place employees on temporary leave in September, the augmented reality headset maker is reminding enterprise companies that it remains a viable option for visualizing and working with 3D design models.

Amid the opulent and historic confines of Paris, Microsoft is now hosting an exhibit at a local museum that brings a historic map of a Normandy tourist destination to life in augmented reality.

There's a new macOS vulnerability that hackers within physical reach of your computer can use to gain root access to your system and accounts. Just by using "root" as the username and a blank password on a privilege escalation prompt, someone can install malware on your computer, access hidden files, reset your passwords, and more. Root access gives them the ability to do anything they want.

It looks like there is a fatal flaw in the current macOS High Sierra 10.13.1, even straight from the login menu when you first start up the computer. This severe vulnerability lets hackers — or anyone with malicious intentions — do anything they want as root users as long as they have physical access to the computer.

A pair of organizations recognized companies working in augmented reality for their innovative technologies over the past week. Meanwhile, another company used augmented reality for a sector that is overdue for a technology makeover, while another company has developed new camera modules that could usher in the next evolution of mobile AR.

It's fair to say that Google's messaging services are in a bit of a heap at the moment, and to make matters worse, Hangouts is removing its SMS capacities. Hangouts version 18 is now being rolled out, but doesn't appear to incorporate any functional changes.

Google's Pixel phones have a feature that lets you swipe down on the fingerprint scanner to open your notification shade and Quick Settings panel. It's one of those features that make you wonder why it wasn't there in the first place, since it gives you another way to interact with your device, and your fingerprint scanner isn't being used while you're screen is on anyway.

When Google released the Nexus 5X and Nexus 6P, they added official support for fingerprint scanning to Android's main code base. On the surface, this was done to ensure that the fingerprint scanner in their own devices could be used to its full extent, but because it was added to AOSP, this meant that the new Fingerprint API could be used by any Android manufacturer.

NMAP is an essential tool in any hacker's arsenal. Originally written by Gordon Lyon aka Fydor, it's used to locate hosts and services and create a map of the network. NMAP has always been an incredibly powerful tool, but with it's newest release, which dropped mid-November of last year, they've really out done themselves.

Welcome to my very first tutorial ever. Today I will be teaching you how you can use Arachni to scan vulnerabilities of web applications. I welcome all criticism good or bad as a teaching method for myself.

Samsung's Galaxy series of devices have one common design theme that ties them all together—the physical home button at the bottom of the phone. This button can wake the phone, take you to your home screen, and even scan your fingerprint to securely unlock your device.

Slowly but surely, Microsoft seems to be steering Windows in the direction of Google's Android. First, they released Windows 10 as a free upgrade, mainly because they wanted to cash in on the revenue that they hoped would come when more users had access to the Windows Store. Then, they included tons of tracking "features" to help populate Bing with targeted ads, which has always been Google's primary method for monetizing Android.

There are several reasons that you might want to restore the factory firmware on your device—maybe you need to send your phone back for warranty purposes, or perhaps you're getting ready to accept an over-the-air update and need to unroot first. In some cases, reverting to the stock firmware can even resurrect a soft-bricked phone.

Hi Elite Hackers! Welcome! to my 4th post. This tutorial will explain, how to extend a (hacked) AP's range with a wireless adapter. I made this guide because after hacking an AP it was difficult to connect to it (poor connection) and further exploit it. You can also use this:

Using a combination of my phone, laptop, and an arsenal of apps and plugins, I can send pretty much anything to my Chromecast. However, nothing is ever perfect, and the file type that was still giving me headaches were torrent and magnet files.

Whenever a new Android device is realized, the first thing I figure out how to do is to get it root access. Generally speaking, rooting has never been easier, with many one-touch methods like Stump and Towelroot available. But as manufacturers and carriers increase security with each new product, there is one tried-and-true root method that continues to work on most Samsung devices—Chainfire's CF Auto Root.

There are many different reasons that you might want to revert your Samsung Galaxy S5 back to stock. The main one would probably be that you need to return your device to the manufacturer for warranty purposes. And if you've used root to modify system-level files and components, you'll need to undo those changes before you send the phone back.