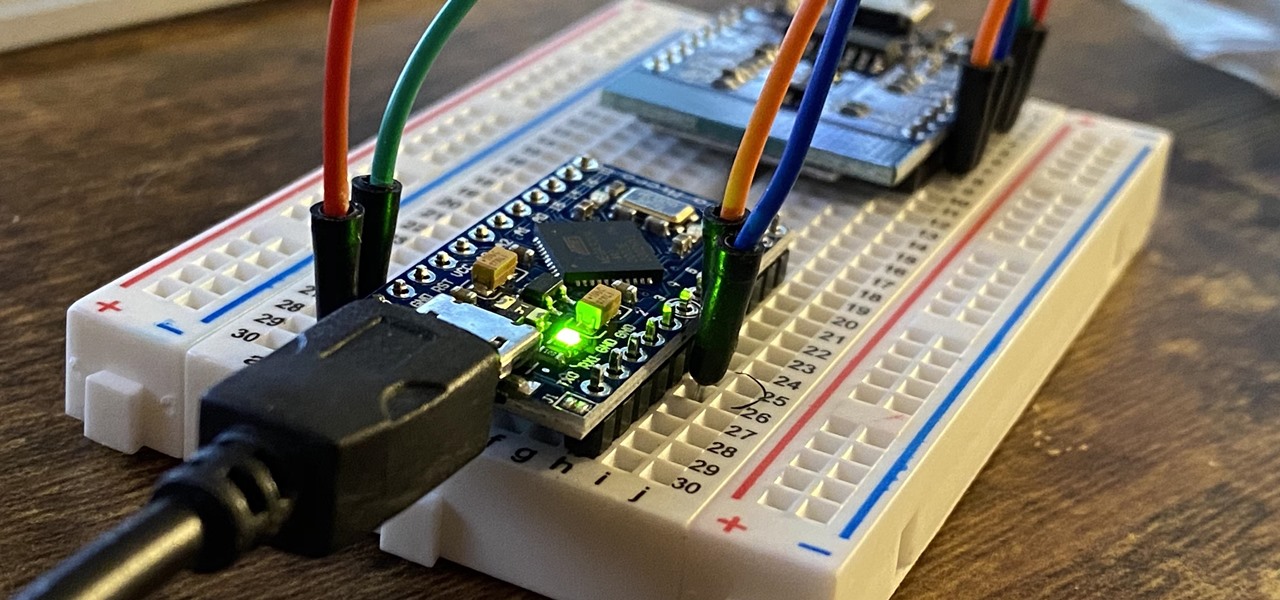
When you don't have a steady cellular signal or immediate Wi-Fi access but need to communicate with others around you, you can set up an off-the-grid voice communications network using a Raspberry Pi and an Android app.

By using almost any packet-crafting tool, a hacker can perform denial-of-service (DoS) attacks. With the power to create just about any packet with any characteristics, a hacker can easily find one that will take down a host or network. Nmap and Hping are effective packet manipulation tools, but there's also Scapy, which is almost infinitely customizable.

Over the last few years, the only thing teased by Magic Leap more than the Magic Leap One itself has been the company's flagship gaming title Dr. Grordbort's Invaders. The game, developed by New Zealand studio Weta Workshop, finally got its debut last week during the L.E.A.P. conference in Los Angeles.

If you're looking for your gaming fix and nothing on the App Store is piquing your interest, you should give soft-launched games a try. These are games that haven't been released in the US yet because they're getting tested in smaller markets first. Using a simple workaround, you can install them on your iPhone in any country.

Because augmented reality is still so new to so many people, there are a number of would-be experts opining online, often repeating basic facts anyone with a spare 15 minutes can find on their own. That's why it's important to point out when someone delivers what could be considered the ultimate cheat sheet for ramping up your AR IQ if you're unfamiliar with the finer points of the space.

Thanks to ever more powerful smartphones — the iPhone X with its advanced A11 processor and the Galaxy Note 8 powered by Snapdragon's 835 come to mind — the mobile industry is fast closing in on consoles and PCs with regards to gaming. Game developers have been aware of this fact, and have ported many games once dedicated to computers onto our handheld devices.

Social engineering makes headlines because human behavior is often the weakest link of even well-defended targets. Automated social engineering tools can help reclusive hackers touch these techniques, but the study of how to hack human interactions in person is often ignored. Today, we will examine how to use subtle, hard to detect persuasion techniques to compromise a human target.

Whether you're riding the subway on your way home from work, or stuck in the backseat of the car on a long road trip, there are times when you need to entertain yourself without a mobile data connection. A good mobile game would pass the time perfectly, but not every game works without an internet connection.

Will the predicted apocalyptic date—December 21st, 2012—really be the end of the world? In this ongoing five-part series, we examine what would happen if zombies, nuclear weapons, cyber wars, earthquakes, or aliens actually destroyed our planet—and how you might survive.

Open-source intelligence researchers and hackers alike love social media for reconnaissance. Websites like Twitter offer vast, searchable databases updated in real time by millions of users, but it can be incredibly time-consuming to sift through manually. Thankfully, tools like Twint can crawl through years of Twitter data to dig up any information with a single terminal command.

The price of hacking Wi-Fi has fallen dramatically, and low-cost microcontrollers are increasingly being turned into cheap yet powerful hacking tools. One of the most popular is the ESP8266, an Arduino-programmable chip on which the Wi-Fi Deauther project is based. On this inexpensive board, a hacker can create fake networks, clone real ones, or disable all Wi-Fi in an area from a slick web interface.

Hackers rely on good data to be able to pull off an attack, and reconnaissance is the stage of the hack in which they must learn as much as they can to devise a plan of action. Technical details are a critical component of this picture, and with OSINT tools like Maltego, a single domain name is everything you need to fingerprint the tech details of an organization from IP address to AS number.

There has been significant debate over law enforcement's right to access our digital devices in recent years. New tools from Grayshift and Cellebrite are popping up faster than ever to help government agencies, as well as traditional hackers, break into iPhones. If you're concerned, you can take steps right now to beef up your passcode and prevent outsiders from gaining access to your device.

Puzzle games are great at giving your brain a workout while keeping things fun and killing time. They stimulate your noggin as you strategize and plan your next move, whether it's to keep your character from getting killed, or to get that special item to finally complete your collection and unlock a new feature within the game.

A new technological movement without the technology itself is just an idea sitting and waiting. Once the technology is present in the equation, movement forward can begin. This is how many of us see the head-mounted displays (HMDs) and smartglasses that have recently entered the augmented and mixed reality market — or are coming out in the next few months. This is a movement that will sweep over the world, changing everything in its path, and these are some of the people behind it.

In five short years, three generations of ultra-low-cost Raspberry Pi devices have challenged the boundaries of what a person can do with a $35 computer — especially with Kali Linux.

Notch loves Halloween. He must, because he keeps putting scarier and scarier things into Minecraft around Halloween time!

Thrift stores! As a Steampunk, they can be your best friend, but it's easy to make a tragic mistake. This hands-on guide will help you navigate the murky waters of successful thrifting in order to find the hidden gems that will make your Steampunk outfit complete!

When it comes to platform games on mobile, endless runners are some of the hardest to play since they can go on seemingly forever. There's always room for improvement since your goal is to beat your previous score (or someone else's high score). But which endless running games are worth your time?

It always looks different when it's not about you. The Internet is our world's Alterego. Those many bits don't really make sense unless we want them to be valuable, to mean something.

One of the best things about Christopher Nolan's Batman trilogy is how realistic he makes the caped crusader feel. Unlike the Joel Schumacher or even the Tim Burton versions, Nolan's world seems grounded in some level of scientific fact. But just how close is science to actually being able to replicate some of the Dark Knight's gadgetry?

ESP8266-based microcontrollers can be used to create exciting and legal Wi-Fi hacking games to test your or your friends' Wi-Fi hacking skills.

The USB Rubber Ducky is a well-known hacking device in the cybersecurity industry, but it needs to be preprogrammed before it can be used. That means it's not easy to issue commands to a target computer since you can't interact with it from afar after plugging it in. And if you don't know what the target computer is, you might come up empty. That's where the WiFi Duck comes in handy.

3D printers allow hackers and makers alike to create something from nothing. They're an incredible technology that lets you build protective cases and covers for gear such as a wardriving phone and Raspberry Pi-Hole. 3D printers can even help you out in a bind when something breaks, and it's impossible to get the part, since you can just print one out yourself.

The latest film addition in the American-produced Millennium series, The Girl in the Spider's Web, was just released on Blu-ray a few days ago. As you could expect, the movie has many hacking scenes throughout, just like the previous English and Swedish language movies centered around hacker Lisbeth Salander. Of course, with the quick pace of some scenes, the hacks can be hard to follow.

As a hacker, the final stage of exploitation is covering their tracks, which involves wiping all activity and logs so that they can avoid being detected. It's especially crucial for persistence if the target will be accessed again in the future by the attacker.

To name just a few companies, VK, µTorrent, and ClixSense all suffered significant data breaches at some point in the past. The leaked password databases from those and other online sites can be used to understand better how human-passwords are created and increase a hacker's success when performing brute-force attacks.

This video demonstrates how to select your weapon in Gears. The video walks you through switching weapons and performing melee attacks with different weapons.

Are you apart a LARP association? No, well maybe you just like boffer fighting just for fun then, hmm?

Learn how to shoot a bow and arrow with expert tips and techniques, in this free weapons training video series on archery tips and techniques.

There are different types of swords used in fencing including and Epee, a Foil, and a Saber. In this series of video clips, you’ll learn more about these different weapons.

In this series of video clips, you’ll learn more about these different weapons. An important component of fencing is the footwork and balance. Get informative tips on the choreography of a sword fight from our expert. Learn more about the modern scoring apparatus and other fencing equipment. If you are a novice fencer, you can get more advanced tips and ideas for fencing foil techniques and vaulting and linear footwork.

Wish things were free? Well, with this hack, you can make sure all the gold is zero and everything costs nothing. How? With Cheat Engine!

So You're New to Counter Strike Source? So you're new to Counter Strike Source and you want to improve your gameplay? Great. You've come to the right place.

Introduction Halo: Reach is Bungie's latest and final addition to the franchise. Microsoft has claimed the title and from now on 343 Industries will be working on the Halo franchise. In my opinion, Bungie's last game is the best out of all of them. These are some tactics and bits of advice that I've picked up.

It's currently 2011, but when you fire up your game console, put your hands on the controller and play the new Dead Space 2 video game, you're warped into the future— into the year 2511— just 3 years after the events that took place in the first Dead Space. And it's sure to be a beautiful, frightening, futuristic experience.

The last few months of WikiLeaks controversy has surely peaked your interest, but when viewing the WikiLeaks site, finding what you want is quite a hard task.

All you LARPers out there, watch and see how you can make a blue boffer sword for LARPing. This weapon passes all weapons specs as of Ragnarok XXI War Council for Eryndor.

Mass Effect 2 may have been around for a whole year... but not on the PlayStation 3. And last Tuesday, January 18th, PS3 gamers finally got their hands on a copy of the critically acclaimed RPG. Actually, this is the first time any Mass Effect game has been available on the PS3, making this a historical event for BioWare.

The resume is an essential tool for getting freelance work assignments. A well written article is not enough when trying to secure a freelance or staff position as a writer. Publishers want to see a resume. It gives the writer an outstanding opportunity to introduce themselves and it gives the editor a general idea of who you are, where you've been, and the work you've completed.