The purpose of this video is to show an e-mail security flaw using telnet that allows hackers to send e-mails using anyone's e-mail address. Thankfully, many major e-mail providers have software that blocks this. My intention is to make people aware of this flaw so that other e-mail providers can protect themselves as well.

When joining a new network, computers use the Address Resolution Protocol to discover the MAC address of other devices on the same network. A hacker can take advantage of ARP messages to silently discover the MAC and IP address of network devices or actively scan the network with spoofed ARP requests.

One of the best ways to improve your skills as a hacker is to learn to combine different avenues of attack to achieve success. What if it were possible to get a victim to connect to our machine and execute a chosen payload on our behalf? This is indeed possible with the almighty Metasploit and the aid of a technique known as command injection.

This video tutorial from iTouchMaster2 shows how to SSH to iPod or iPod Touch using FileZilla application.
1. Type in WWW.sendthisfile.com in the web toolbar and press enter 2. Click on Register found on the top right side
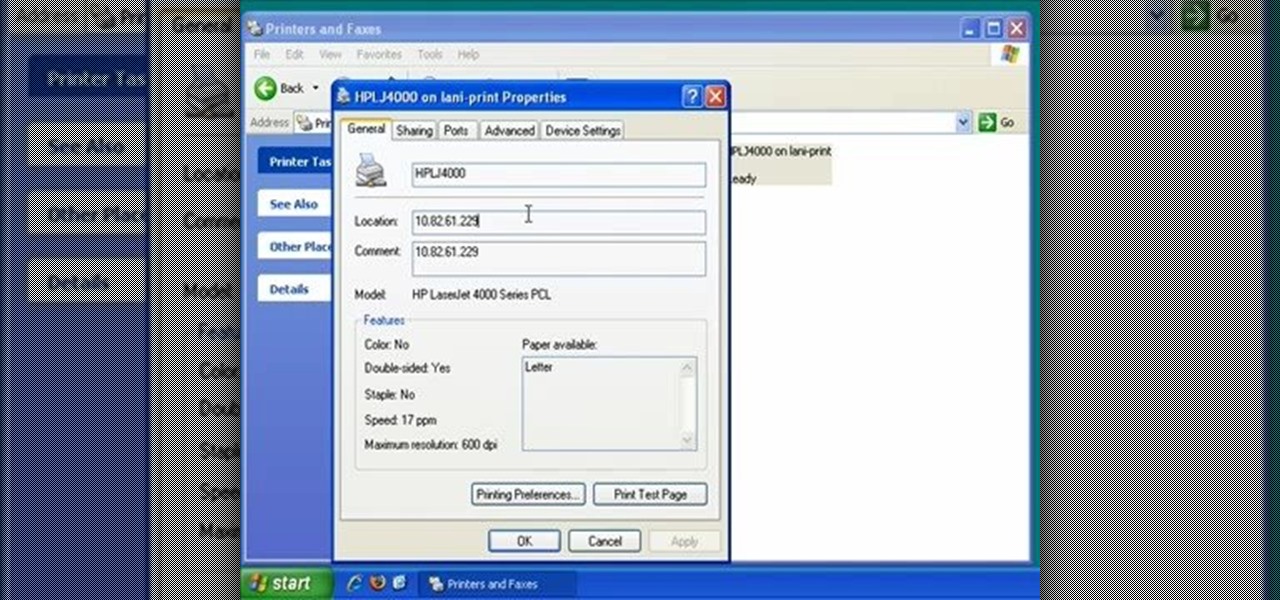
In this video, we learn how to find the IP address of a printer on your computer. Before you begin, make sure you start on your main desktop. First, click on the "start" menu, then click on "control panel" and last click on "printers and faxes". Once you're in there, right click on the printer you want to see the IP address for and then click on "properties". After this, you will find the IP address under the "location" section. You can look up the IP address for all the printers in your netw...

Whether you are protecting your children or hiding personal information, there are ways to block unwanted websites from your computer. Follow this tutorial and learn how to accomplish this on a Windows PC easily.

If you're with AT&T and need to change wireless-user information, you can do it easily through the business mobility online customer portal, AT&T Premier. Whether you're needing to change email addresses, phone numbers or physical addresses, this is the place and way to do it.

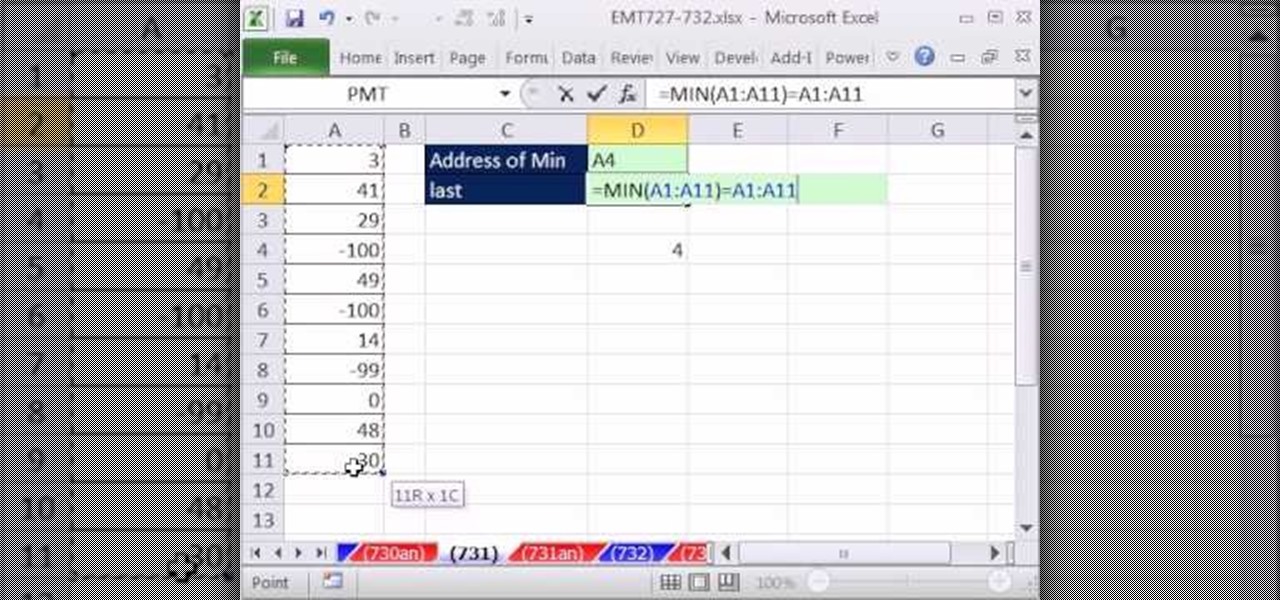
New to Microsoft Excel? Looking for a tip? How about a tip so mind-blowingly useful as to qualify as a magic trick? You're in luck. In this MS Excel tutorial from ExcelIsFun, the 730th installment in their series of digital spreadsheet magic tricks, you'll learn how to create a formula that will retrieve the cell address of the minimum value in column. To accomplish this, you'll use the ADDRESS, MATCH, INDEX, MIN, ROW and LOOKUP functions.

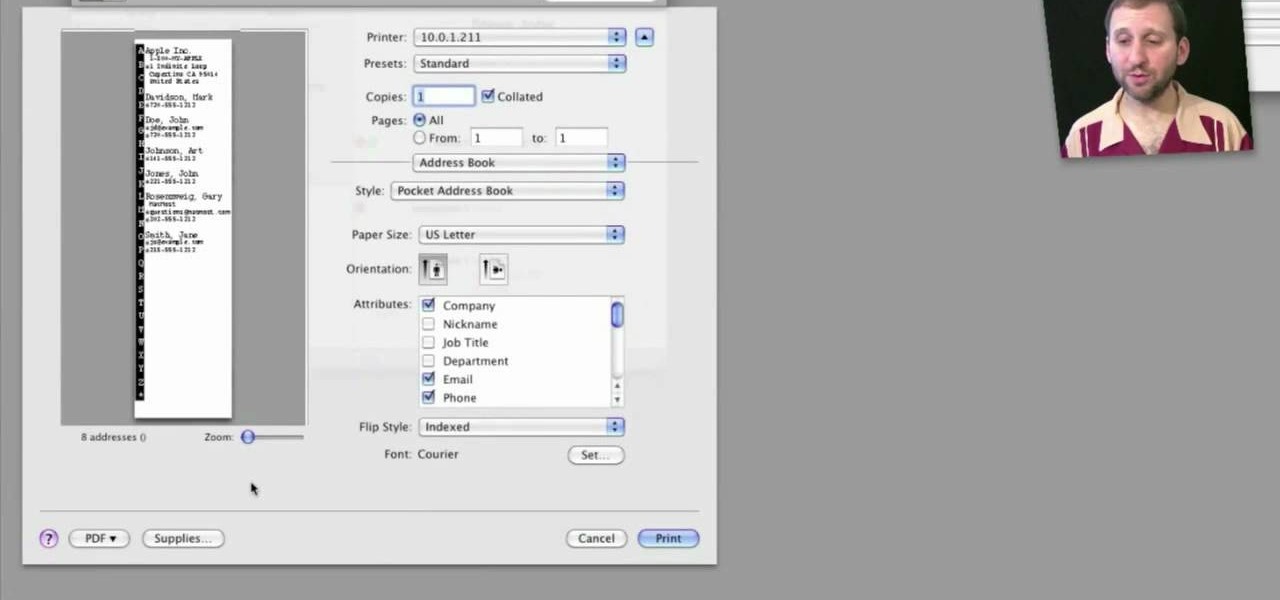
Looking for a quick primer on how to print from Address Book on a Mac OS X computer? It's easy! So easy, in fact, that this home-computing how-to from the folks at MacMost can present a complete overview of the process in just over three. For more information, including step-by-step instructions, take a look.

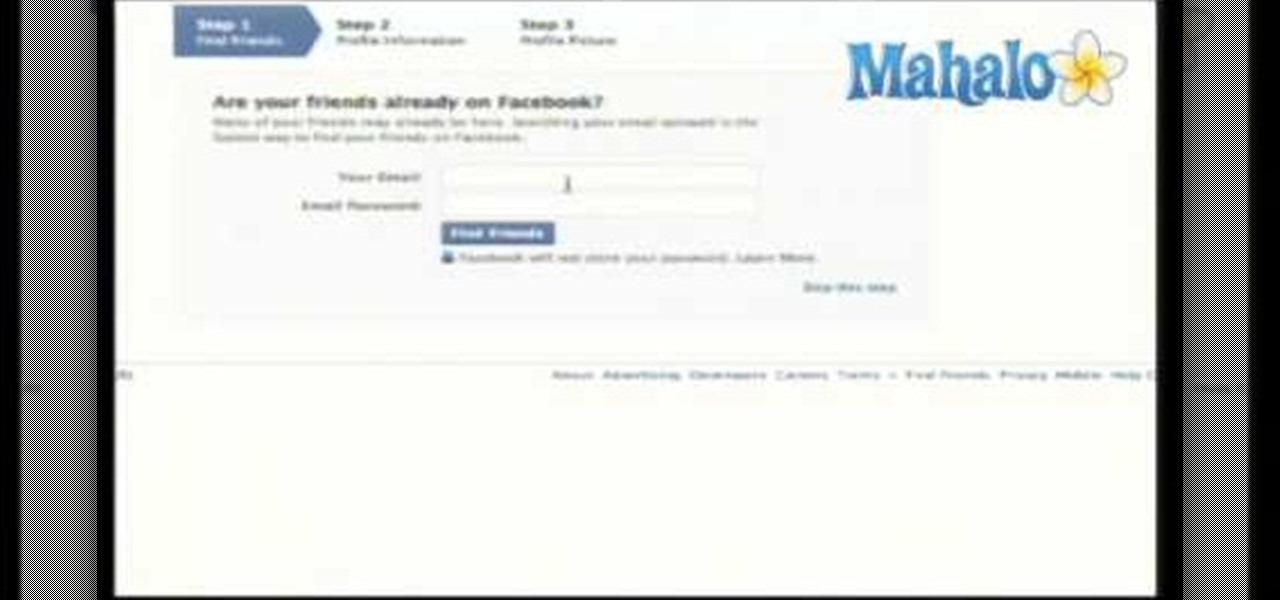
Want to find a friend on Facebook? Have their email address? Whether you're completely new to the Facebook's popular social networking site or simply require a small amount of clarification on how to perform a particular task on Facebook, you're sure to benefit from this helpful video guide. For more information, including detailed, step-by-step instructions on how to use Facebook's handy email search feature, take a look.

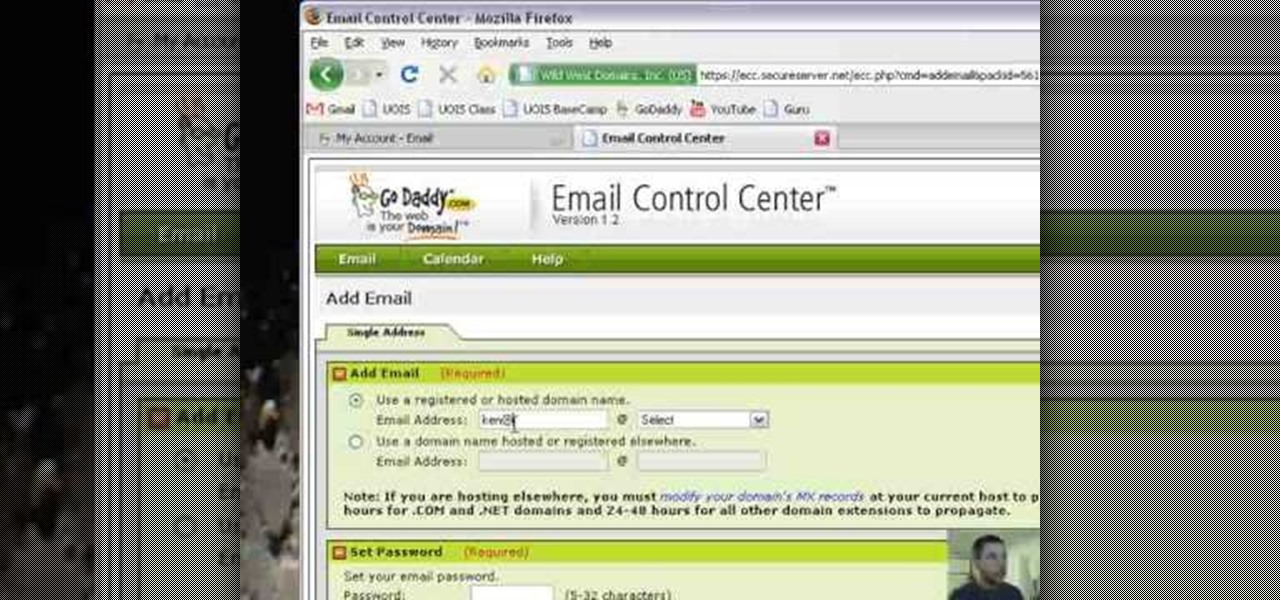
Want to set up a custom email account for a domain hosted by GoDaddy? It's simple. So simple, in fact, that this free video guide can present a complete overview of the email address creation process in just over three and a half minutes' time. For complete instructions, and to start using your own custom email addresses, watch this helpful how-to.

New to Microsoft Excel? Looking for a tip? How about a tip so mind-blowingly useful as to qualify as a magic trick? You're in luck. In this MS Excel tutorial from ExcelIsFun, the 363rd installment in their series of digital spreadsheet magic tricks, you'll learn how to create an array formula using the ADDRESS, MIN, IF, COLUMN & ROW functions that will return the address of the first non-blank cell in your Excel spreadsheet.

Here you will see how to add a contact to the address book of a Nokia N97. Follow these steps to add a contact to your Nokia M97's address book: From the home screen, tap the "Contacts" icon and then tap "Add New Contact". Enter in the contact information and tap "Done". Tap "Exit" to return to the home screen. To set a contact as one of your favorite contacts, tap "Add to Favorites", and select the contact you wish to add as a favorite. Tap "OK" You can also do things such as add a called ID...

It's now standard for websites to have a mobile version. Conveniently, we can browse the web with a mostly mobile-optimized experience. But what if you want the desktop experience on mobile? If you want, you can browse the mobile web and see only the desktop version of websites on Android devices.

The easiest way around a security policy is to find users who don't follow it. The Have I Been Pwned database identifies accounts with information breached by major third parties like Yahoo and LinkedIn. With Maltego, hackers can locate breached accounts created using company email addresses, potentially giving attackers access to a company account if the employee reuses a compromised password.

The desktop browser market has some stiff competition going on, but Opera has always been able to maintain its market share by offering innovative features such as a data saver option. With over 350 million users, it's safe to say folks are appreciative of the efforts being made by the web browser's development team.

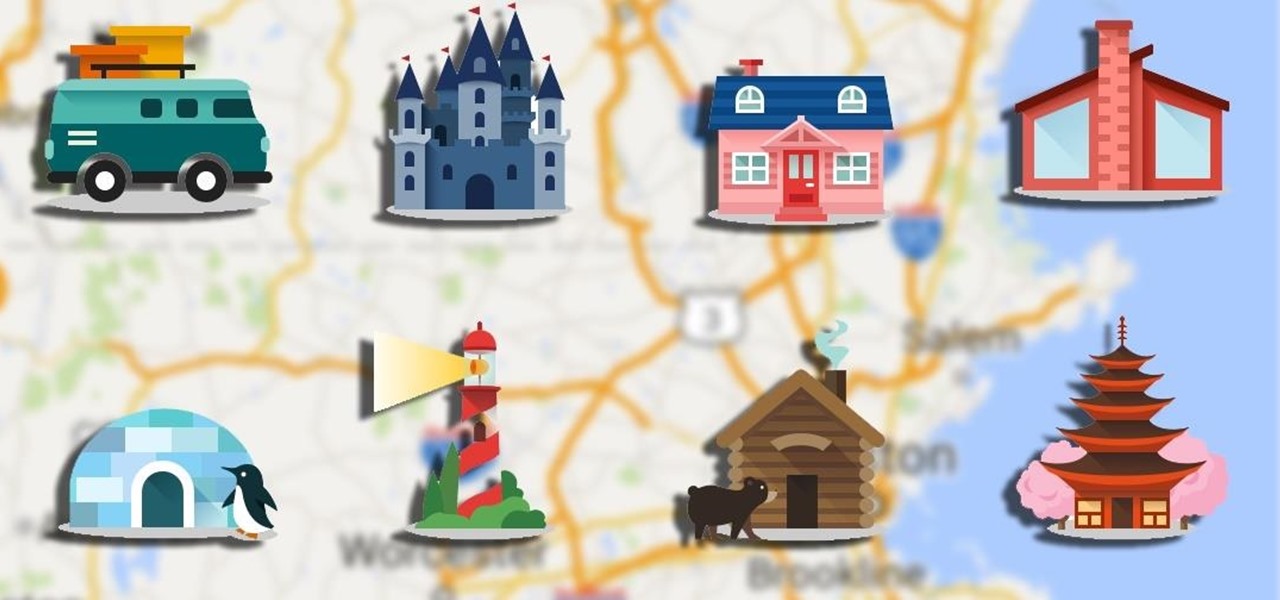
If you're using an up-to-date version of Google Maps on your Android device, there's a little-known feature you can use to apply stickers to saved places, making them visually easier to find while you're looking at the map.

In previous tutorials we have encountered these things called pointers and addresses but we still don't know what they really are. Let's learn a bit more to clear things up.

In most cases, when the free trial of software is over, that's it—you're left to either pay for it or find an alternative. But what happens if the trial wasn't long enough to sell you on the product? It'd be nice if there was a way to test it out again without having to whip out your credit card.

Welcome back, my hacker novitiates! In an earlier tutorial, I had introduced you to two essential tools for cracking online passwords—Tamper Data and THC-Hydra. In that guide, I promised to follow up with another tutorial on how to use THC-Hydra against web forms, so here we go. Although you can use Tamper Data for this purpose, I want to introduce you to another tool that is built into Kali, Burp Suite.

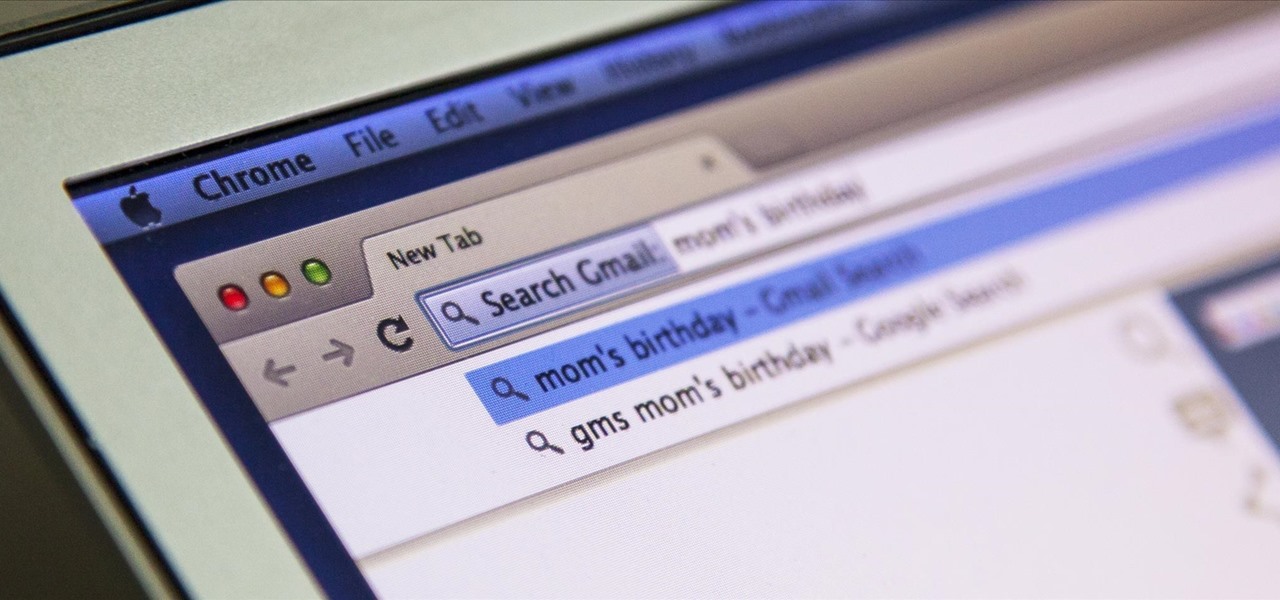
I'm all about saving time. If there's a quicker way to do something, I'm going to find it. For this reason, whenever I need to search through old emails or compose new ones in Gmail, I do it directly from Chrome's address bar, or as Google likes to call it, the omnibox—and you can, too.

Do you take your notes on a word processor while browsing the web? Well, stop. There's an easier, less RAM hungry way to take notes by turning the tab of your web browser into a notepad. Whether it's an email address, a line of code, a new how-to, or an idea you don't want to lose, you can easily jot it down without slowing down.

Welcome back, my tenderfoot hackers! Not too long ago, I showed how to find various online devices using Shodan. As you remember, Shodan is a different type of search engine. Instead of indexing the content of websites, it pulls the banner of web servers on all types of online devices and then indexes the content of those banners.

Welcome back, my hacker apprentices! My recent posts here in Null Byte have been very technical in nature, so I thought that I'd have a little fun with this one.

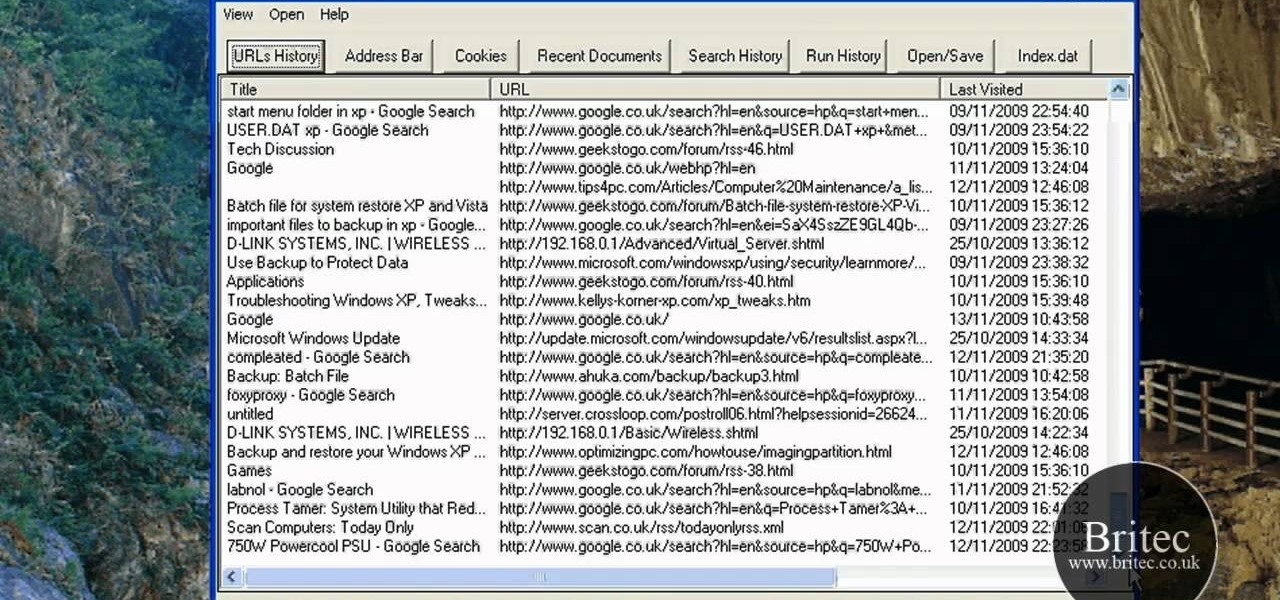
Interested in reading the list of web addresses in an index.dat file on a Microsoft Windows computer? This clip will teach you everything you'll need to know. With WinSpy, it's easy! So easy, in fact, that this home-computing how-to from the folks at Britec can present a complete overview of the process in just over two minutes. For more information, including detailed, step-by-step instructions, take a look.

Learn how to delete your old Yahoo account from this video in simple steps. First open your web browser on your computer and go to the Yahoo home page. Now sign into your account using your username and password. Now copy and paste this link "http://edit.yahoo.com/config/ delete_user" in your address bar. Enter your password to confirm the deletion of your account. Finally enter the code to confirm and delete your account.

At midnight on February 17, 2009, all full-power television stations in the United States will stop broadcasting in analog and switch to 100% digital broadcasting. Digital broadcasting promises to provide a clearer picture and more programming options and will free up airwaves for use by emergency responders.

New to the Ubuntu Linux distribution and interested in setting up an address book for to keep track of your contacts? In this how-to, you'll learn how to make maximum use of the address book built into the Evolution email client. Take a look!

If you're putting your email address online on your own website, or sites like facebook or myspace, you may want to be a bit clever about it. Check out this tutorial and see how to protect your email address from spam.

Check out this video to learn how to search more effectively in the Google Chrome browser. This video will explain how to manually enter keyword searches in Google Chrome and Chromium, which will allow you to search using any engine from the address bar.

Your manuscript is complete, and you have a list of your favorite agents and a strong query letter... but how do you properly address letters to agents? You neither want to be too formal nor too casual - strike the perfect balance.

The days of Skype 2.8 for Mac are over! Mac users can now rejoice and make calls with ease using the new beta version: Skype 5.0 for Mac OS X (available here). It was well worth the wait, with a revamped look and feel that simplifies navigation and provides a more Mac-like experience.

In this clip, you'll learn how to reinstall an accidentally-deleted system application like TextEdit, Preview, iCal, Address Book or QuickTime without reinstalling OS X. With a little know-how, it's easy. So easy, in fact, that this video guide can offer a complete overview of the process in a matter of a few minutes. For more information, including a complete demonstration and detailed, step-by-step instructions, watch this home-computing how-to from MacMost.

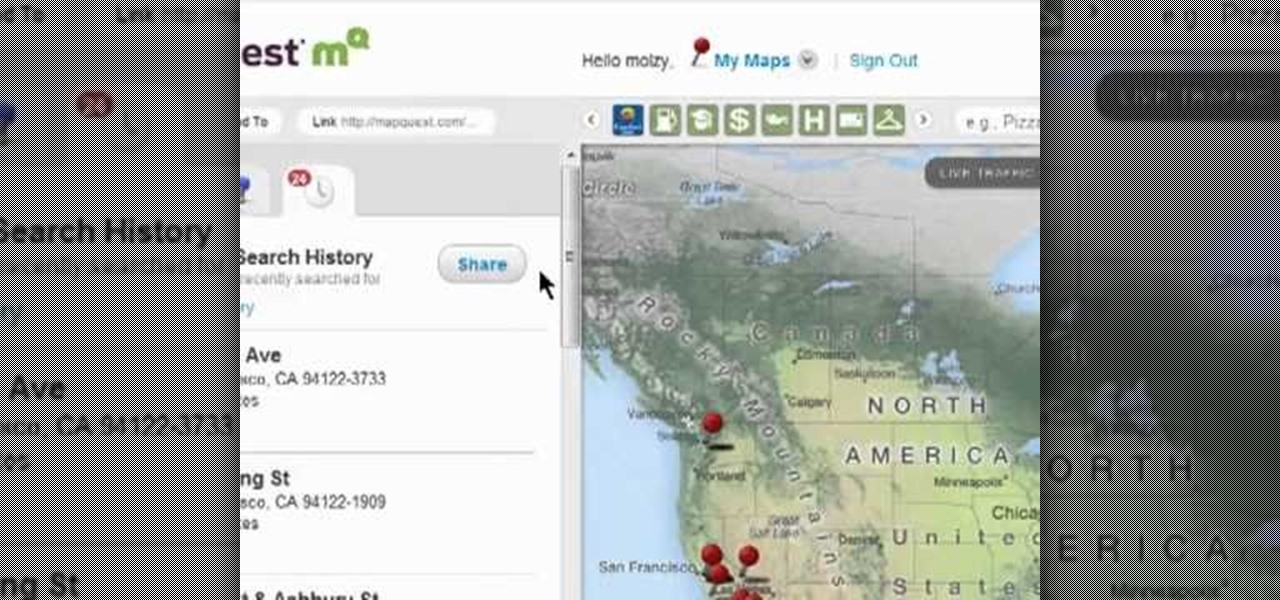
In this clip, you'll learn how to view the list of your previously searched addresses on MapQuest Maps. It's easy. So easy, in fact, that this home-computing how-to can present a complete, step-by-step overview of the process in about two minutes. For more information, including detailed, step-by-step instructions, take a look.

Need some help figuring out what your IP address is? It's easy. And this brief video tutorial from the folks at Butterscotch will teach you everything you need to know. For more information, including detailed, step-by-step instructions, and to discover your own IP address, take a look.

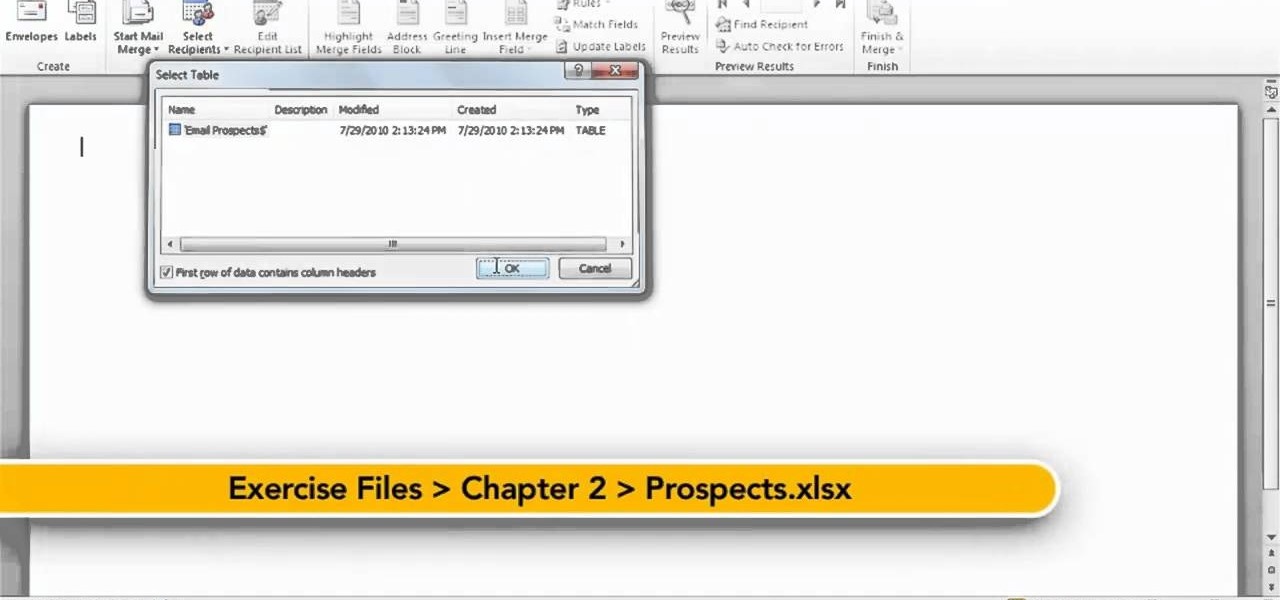
In this quick clip, you'll learn how to insert address blocks and merge fields when using Mail Merge within Microsoft Office Word 2010. Whether you're new to Microsoft's popular word processing application or a seasoned professional merely looking to pick up a few new tips and tricks, you're sure to benefit from this video tutorial. For complete instructions, take a look.

Trying to find your friend's Yahoo! mail address so you can send them a letter or tell them about a cool new website you found? Yahoo! directory makes it easy to find someone you're looking for. All you need is is their name.

Want to get involved with the information superhighway? E-mail is the best technology to stay connected with friends and family. Use these tips to create your own email account in Gmail, MSN or Yahoo! mail. Keep track of addresses, improve your networking and learn the basics of instant messaging.

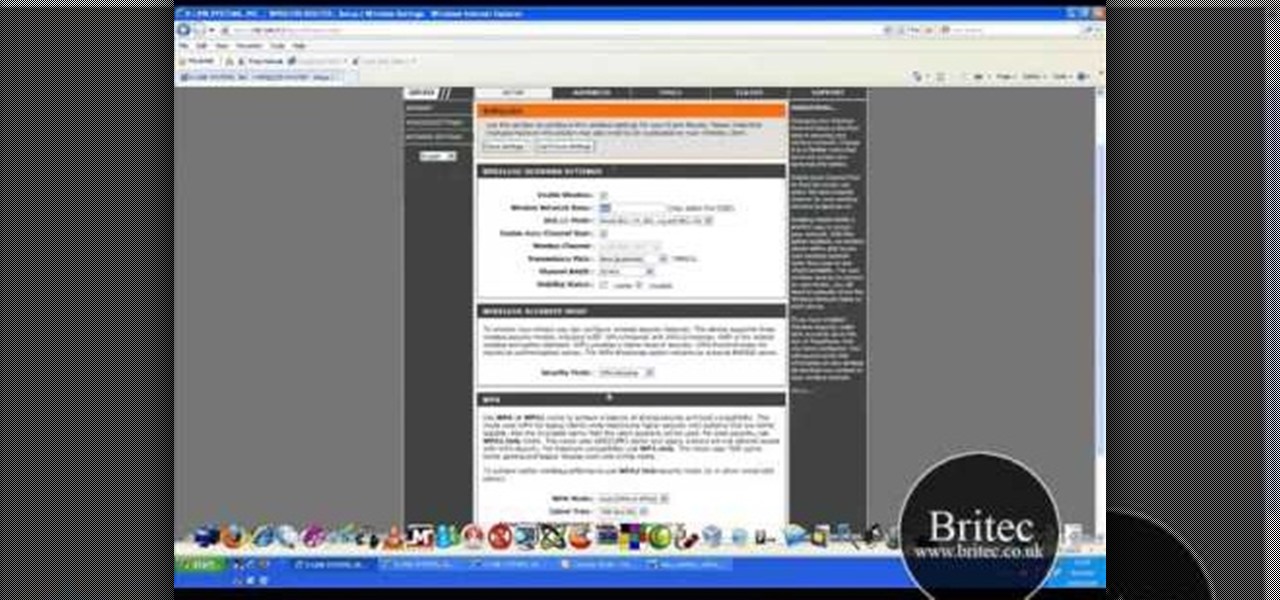
In this tutorial, Brian teaches us how to make your wireless network secure. First, go to the start menu, then go to run and type in "cmd", then type in "iconfig /all". Now a new window will pop up and you will look for the default gateway. Find the IP address to log onto the routers you have. Now, type in your IP address into your address bar on your internet browser. You will be asked to log into your account with your password and user name, which you can find at the manufacturers website....