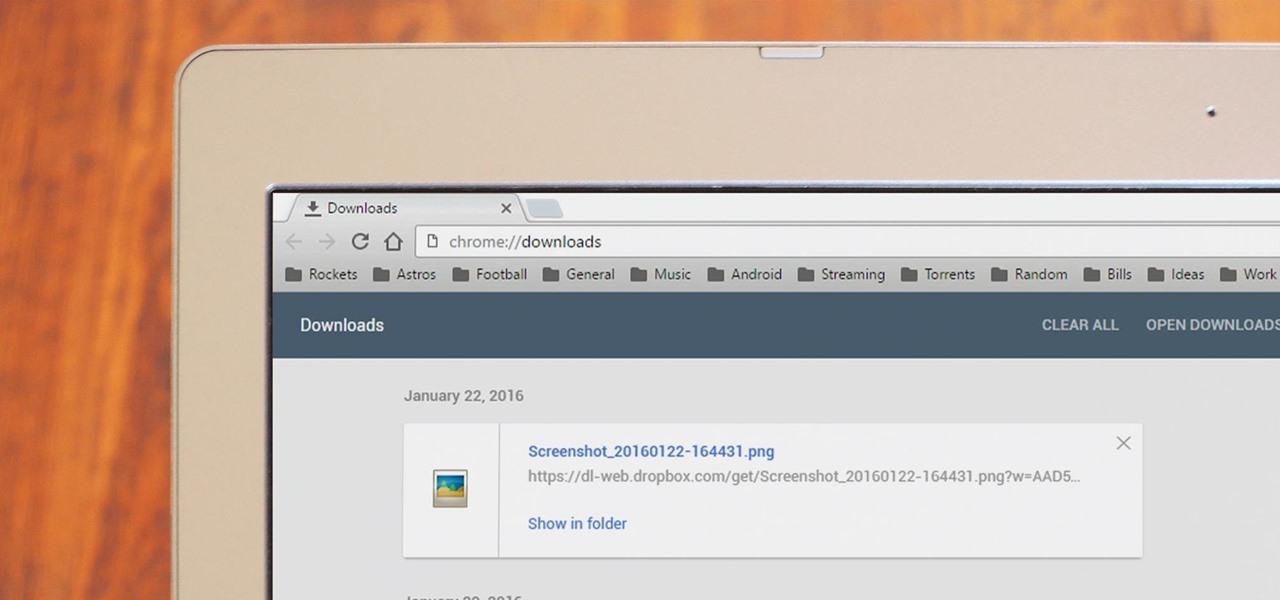
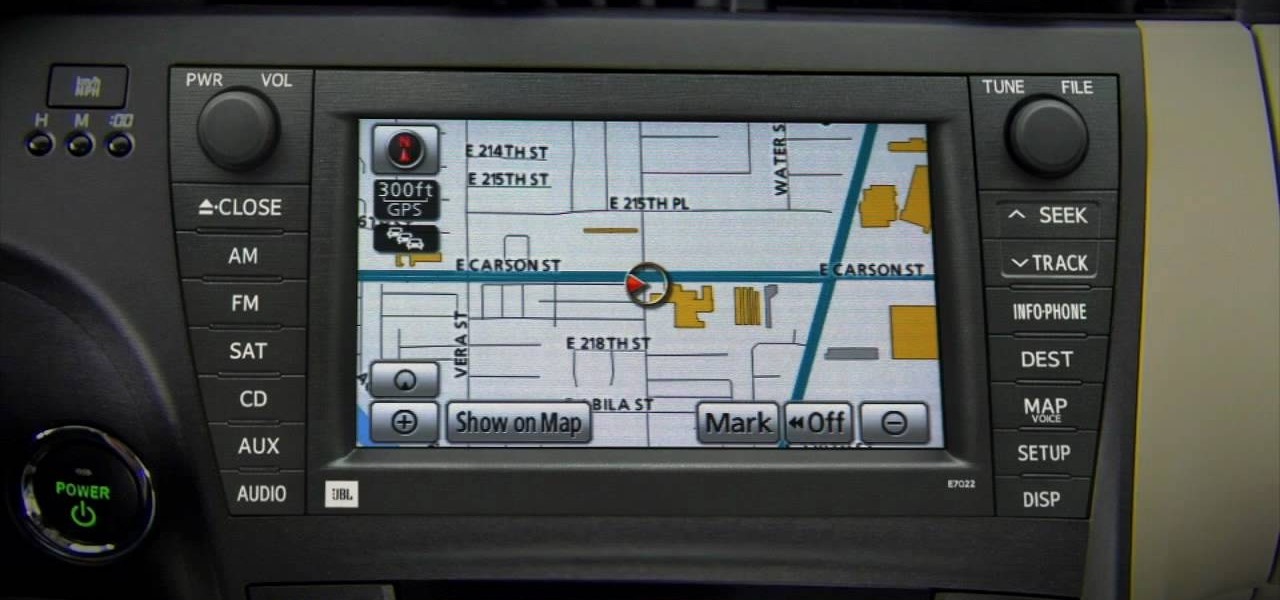
Screenshots taken from a compromised computer can provide hackers with access to private emails, photographs, and information found in sensitive documents. This data can be used by the attackers to build profiles of a target for social engineering attacks and blackmail or even just to release the information out in the wild.

Business cards are a great way to keep tabs on the contacts we network with. So why shouldn't our smartphones make them even more useful? Enter Google Lens, which will help you save, search, and expand on the contact information found on all of the business cards you've collected.
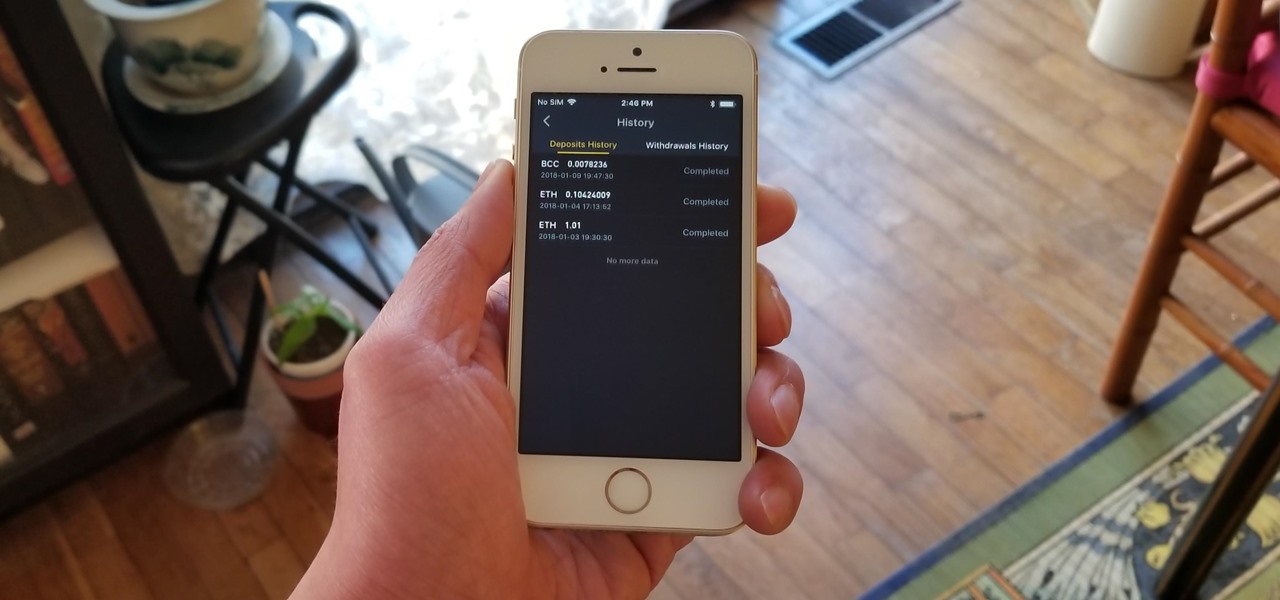
As cryptocurrencies gain mainstream acceptance, it's not far-fetched to think that we'll one day be able to buy alt coins like Ripple (XRP) and Stellar (XLM) using debit cards and bank accounts. Until then, we'll have to rely on using bitcoins and ethereum to buy digital coins. Thankfully, depositing and withdrawing cryptocurrencies with Binance is relatively hassle-free.

With all the hype surrounding meteoric rise of Bitcoin (BTC), Litecoin (LTC), Ethereum (ETH), and Bitcoin Cash (BCH), it's easy to overlook the fact that you can send and receive cryptocurrencies as a form of payment. And thanks to Coinbase, sending and receiving digital coins couldn't be any easier.

The Operative Framework is a powerful Python-based open-source intelligence (OSINT) tool that can be used to find domains registered by the same email address, as well as many other investigative functions. This reconnaissance tool provides insight about your target through examining relationships in the domains they own.
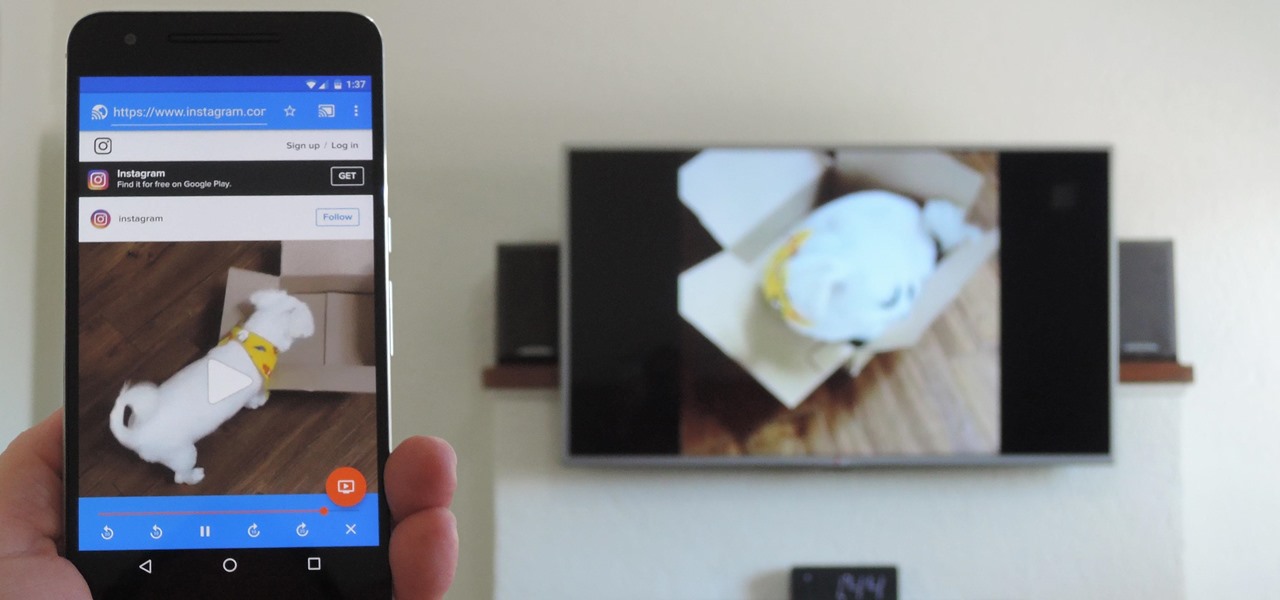
The Google Chrome browser for Android allows you to cast quite a few different videos from the web to your TV, but some sites actively disable this functionality, and others have outdated video players that won't allow for it. For example, Instagram's mobile website won't let you cast any videos, and the official app doesn't support Google Cast.

Google's design chief Matias Duarte has gained fame and acclaim for his recent visual revamp of the Android operating system, and now, Google's starting to incorporate this Material Design styling into more of its products.

Many websites are crowded with ads, pictures, and other irrelevant content that make it harder than necessary to read a simple article on your iPhone. In many cases, you have to zoom in just to get a better view of the text you're attempting to read—unless the webpage blocks zooming.

There's no denying it was a hectic 2014 here in the United States. We saw the rise of ISIS, dealt with an Ebola scare, and witnessed the turmoil in Ferguson (and its aftermath). Plus, let's not forget about all of the hype revolving around The Interview, in which Sony was hacked.

Welcome back, my tenderfoot hackers! As you know, DNS, or Domain Name System, is critical to the operation of the Internet. It provides us with the ability to type in domain names such as www.wonderhowto.com rather than the IP address. This simple service saves us from having to memorize thousands of our favorite website IP addresses. Instead, we simply type in a domain name to retrieve the website.

Google Now is a quick and intuitive way to tailor your device to work for you and, unlike other personal assistants, provide you with up-to-date information based on search habits, emails, and the general all-knowingness of Google.

Welcome back, my greenhorn hackers! Sometimes, we don't have a specific target in mind, but rather we are simply looking for vulnerable and easy-to-hack targets anywhere on the planet. Wouldn't be great if we had a search engine like Google that could help us find these targets? Well, we do, and it's called Shodan!

For the most part, transferring files from your computer to your Nexus 7 (and vice versa) is a simple process. Just hook up your tablet to your computer with the USB cable and transfer. However, most of the time you'll need additional software on your computer to do this, and then, of course, you need the USB cable.

There are a number of reasons why you might want to trick a web server into thinking you're on a different operating system (OS) or web browser. One might be that you want to test the mobile version of your website from your computer. Or perhaps for some reason a website is restricted to a certain OS or browser and you wish to circumnavigate that barrier. Today's guide shows you how to do just that!

Free trials are a great way to test out products before a purchase, or simply for the exploitation of free stuff for that limited amount of time. Some trials last a few days and some last even a month or two, but no matter what—these trials will always expire. But like most things in life, there is a way to get around such limitations.

Dropbox announced Tuesday that a recent security breach compromised a list that included the email addresses of certain Dropbox users. To avoid future complications, the service announced that it would be implementing two-factor authentication, and even more useful, a security page that lets you monitor all activity on your account. In light of this and other recent web security threats, you might also want to know that services like Gmail, Facebook, and Yahoo! Mail have similar pages where y...

WPA-secured wireless networks, or WiFI Protected Access, is a form of internet security that secures your wireless LAN from being accessed by unauthorized users. Safer than WEP, or wireless equivalent privacy, WPA still has weaknesses that are prone to cracking - IF, that is, you know what you're doing.

Learn how to use the navigation system in a new 2010 Toyota Prius in simple steps. It has DVD based navigation system with easy to use touch screen display. All the navigation routes of USA, Hawaii and parts of Canada are available in it supporting English, French and Spanish languages. When you start the car it opens the map and you can input the destination using voice command or entering text. You can also input your home address and five other special location address.

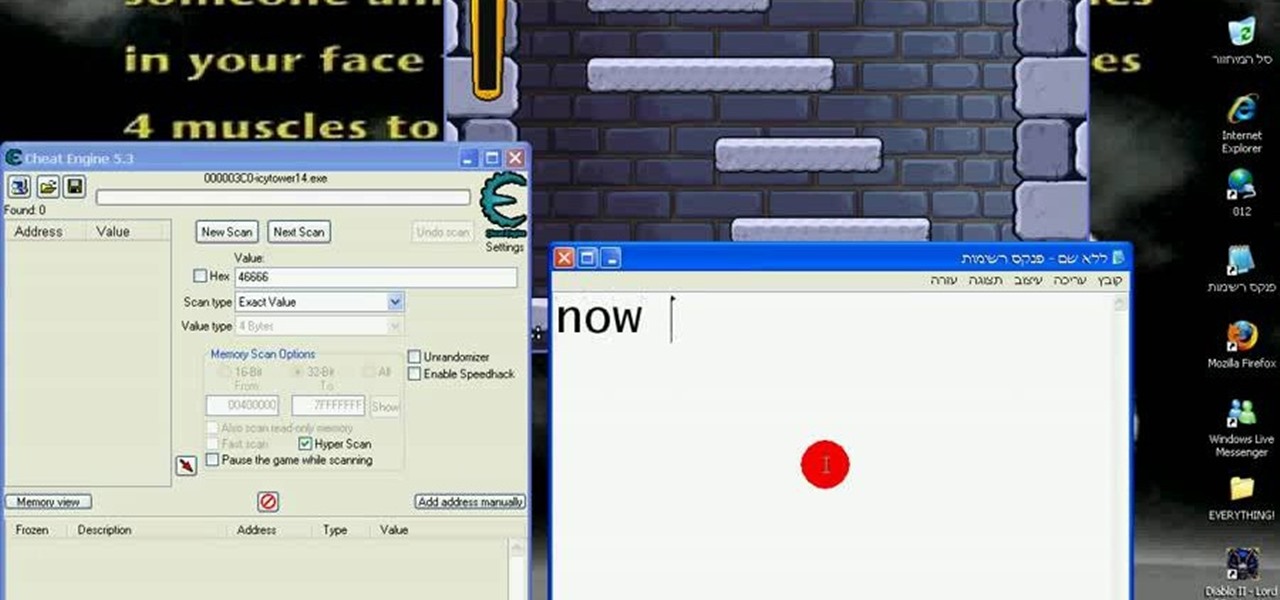
The cold time of Christmas is upon us, and Icy Town is a winter-ific game you can play… and hack. With Cheat Engine and a little patience, you can hack and unlock floors in the game easily.

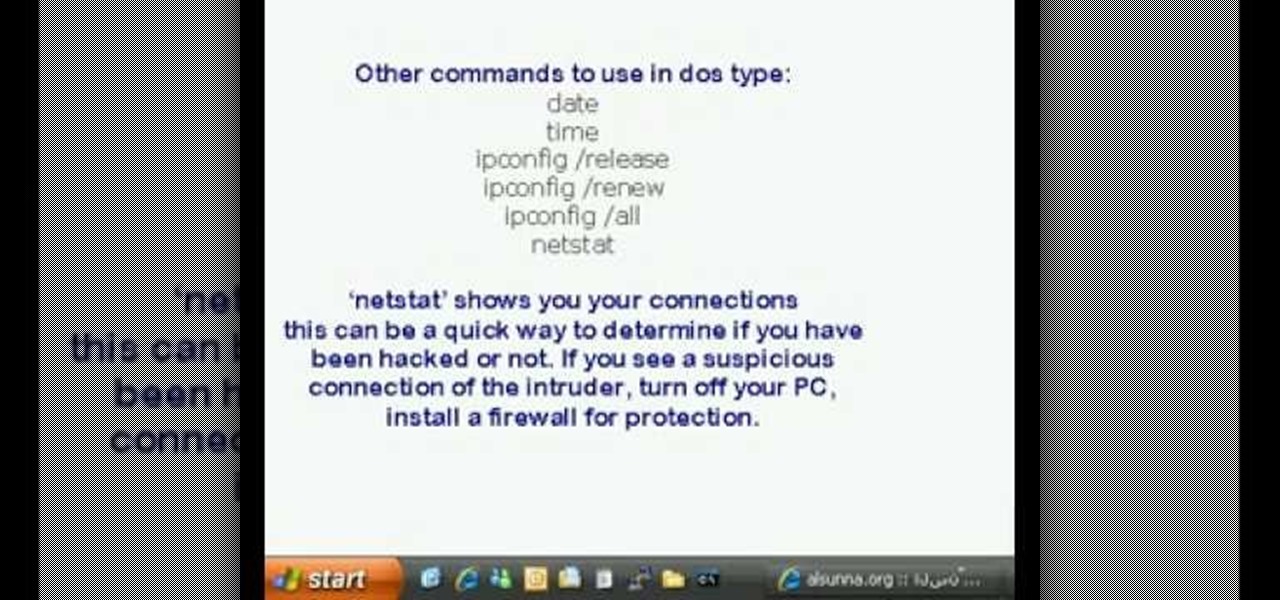
This is a video tutorial in the Computers & Programming category where you are going to learn how to find and ping your IP address. Go to start > run and type in "cmd" to get the DOS window. Here type in "ipconfig" and hit enter. If you are online, your IP address will be displayed. If you are offline, go online and try again. Then in DOS type in "ping yahoo.com". This is to see if you can connect to Yahoo. If you are online, the site will reply 4 times. If you type in "netstat", it shows yo...

In this clip, you'll learn how to reset the IP (or Internet protocol) address on a desktop or laptop computer running the MS Windows Vista operating system. For more information, including a complete demonstration of the process and detailed, step-by-step instructions, watch this home-computing how-to.

This video will show you how to find your own IP address in Windows Vista, which is more difficult and confusing to use than Windows XP was. First, you should go down to the bottom right hand corner and find an icon of two computers, which is your network connection button. Click on the Networks and Sharing selection and find the section which says "View status". After clicking on this, you will find a section which will be labeled "IPv4". The numbers which are indicated after this are the nu...

This walk-through video tutorial shows you how to find out your IP address for XBox live. First press the start button and search for run as shown, click the result, bring up the dialog and type in the given command to open the command prompt window. Type the command in the given window and hit enter. The number that appears is your IP address, use it as the key for XBox Live. In the case of XBox 360, it automatically detects it.

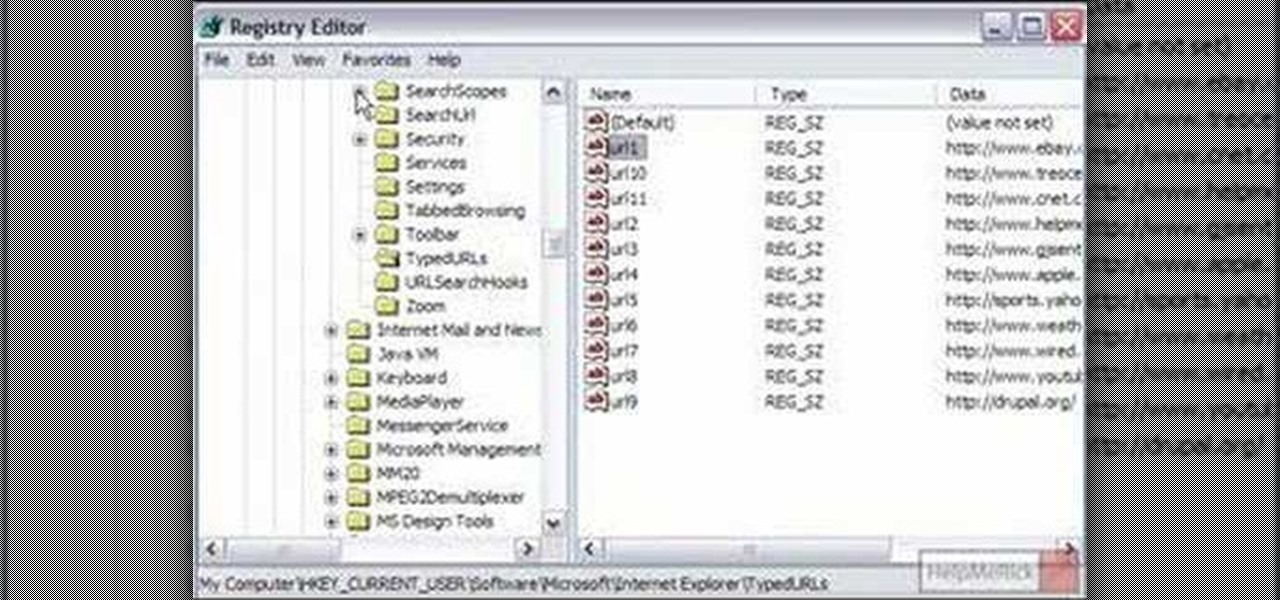
Ever wondered how to go about deleting individual entries from the Internet Explorer address bar? While it's possible, it's not particularly easy. You can do it all at once by purging your entire history through Internet Options or you can hack your Windows registry. For more information, or to try this hack for yourself, take a look!

Don't lose your friends' numbers; save them to the address book. Watch this iPhone tutorial video to learn how to save numbers in your iPhone's address book. This how-to video is intended for new iPhone owners.

Male instructor explains how to create new contacts in the BlackBerry 8700 mobile device. Going to the BlackBerry's address book, it is a matter of entering in all the information for a new contact to be created. Step-by-step process makes it very easy to understand and complete the contact.

For spreadsheets that require contact information, you can grab that information from your address book when you are working in Numbers '08. This tutorial shows you how it's done.

Pages '08 allows you to access the information in your address book and add it to your documents. This is helpful if you are printing envelopes or writing letters.

Take better advantage of your Gmail tools -use aliases to organize your mail and forwarding to manage multiple email addresses and locations.

If you have friends who aren't privacy-conscious, you've surely heard the old "What do I have to hide?" excuse. Despite the fact that billions of people are using the internet each day, many of them don't know the dangers that can find them. And many don't know the tools to combat them.

When it comes to attacking devices on a network, you can't hit what you can't see. Nmap gives you the ability to explore any devices connected to a network, finding information like the operating system a device is running and which applications are listening on open ports. This information lets a hacker design an attack that perfectly suits the target environment.

Command injection is a technique used by hackers to execute system commands on a server, usually via a web application or some kind of GUI. This can happen when an application provides some sort of functionality to the user involving the use of system commands. When the input is not properly sanitized, commands not originally intended to be run are allowed to be executed.

Identifying vulnerable devices and services on a target router can be difficult without leaving logs and other traces of an active attacker on the network. However, there is a way to covertly decrypt and view Wi-Fi activity without ever connecting to the wireless network.

While TouchWiz as an Android skin isn't a favorite among many, Samsung Internet is a fantastic web browser that S9 owners should be happy to have preinstalled out of the box. But you don't need to buy Samsung's latest flagship to try their browser — Samsung Internet is available to all compatible Android phones.

Proxies can be quicker to use than a VPN for specific applications, like web browsers or torrent clients. Both services will hide your true IP address, but a VPN is slowed down because it encrypts all data through a VPN network, while a proxy just acts as a middleman for fetching and returning requests from a server on your behalf. When speed is needed, go proxy.

Using either iMessages or FaceTime on the iPhone is a great alternative for coworkers to stay in touch in the event that messaging services like Slack go down. They're also a handy means of communicating between buyers and sellers, as it provides a more intimate way of either checking out or showcasing a product. But you're not always going to want to give out your real number to everyone.

Good day people, today we will examine some basic, for some people well-known attacks, also we will take a look at some advanced attacks.

Hello ladies and gentlemen, PySec here coming at you with another informative(hopefully) article for you all. In the last tutorial, we finally finished our discussion about IP Addressing and I intentionally didn't mention a really important concept with which IP Addressing wouldn't be feasible without it. What I'm talking about is how our network device gets the IP Address in order to communicate with other devices on the network/Internet. There are many different ways for that to be accompli...
Greetings null-bytians. Say you have been able to penetrate your neighbour's AP, and of course you had spoofed your MAC address. Now you go on and test to see with excitement if the password really works and the MAC is still spoofed. You login successfully and you browse the web forgetting to check what your current MAC is. Well, if you may do an ifconfig command, you will see that your permanent MAC is being used. Oh!! and guess what, ... your real MAC has been logged. Even though there is t...