If you're a U.S. expat living, traveling, or studying abroad, or just someone who typically uses virtual private networks (VPNs) in order to access the North American video libraries of services like Hulu or Netflix, you were probably surprised to see that these video streaming services don't work on your Chromecast or Chromecast 2.

When it comes to news, updates, and arbitrary nonsense, it's hard to find a better source than Twitter. And for some of us, the best way to consume Twitter is through the web (versus a mobile app). But as much as I prefer the standard browser version, it's easy to make it better, faster, and more convenient using a few Chrome extensions—and here are my favorites.

Recently, I've been experimenting with BeEF (Browser Exploitation Framework), and to say the least, I'm hooked. When using BeEF, you must "hook" the victims browser. This means that you must run the script provided by BeEF, which is titled "hook.js", in the victims browser. Once you've done that, you can run commands against the victims browser and cause all kinds of mayhem. Among these commands, there is an option to use the victims webcam. This is what we'll be doing here today, so, let's g...

Welcome back, my tenderfoot hackers! In this series, we are exploring the myriad of ways to hack web applications. As you know, web applications are those apps that run the websites of everything from your next door neighbor, to the all-powerful financial institutions that run the world. Each of these applications is vulnerable to attack, but not all in the same way.
Google continues to be the most commonly-used search engine for a reason. While continuing to stay ahead of the pack with advanced semantic search functions, Google even introduced Knowledge Graph results that offer key information without ever having to click a search result.

Anytime you surf the web on your iPad or iPhone, Safari saves which webpages you visit, the information you enter into them, and other types of data. This not only make your internet experience quicker, but it'll also keep track of everything you're doing.

When browsing the web, you may not be quite as anonymous as you think, especially if you are using public WiFi. The easiest way to stay as anonymous and safe as you are going to get, is to use a VPN (there are a number of great free ones). In this tutorial, we will show you how to set up a VPN on Android, and how this protects you.

This video will provide an idea how to block an email address in Yahoo and Gmail. This video will show in two steps. Watch the video and follow all the steps to block email ids in Yahoo and Gmail account.

Welcome back, my greenhorn hackers! In a previous tutorial on hacking databases, I showed you how to find online databases and then how to enumerate the databases, tables, and columns. In this guide, we'll now exfiltrate, extract, remove—whatever term you prefer—the data from an online database.

There are hundreds of keyboard shortcuts out there, but these 7 are the ones you'll definitely want to remember. I use them every day, and you should too. Step 1: Tab Domination

Welcome back, my novice hackers! Most of my tutorials up until this point have addressed how to exploit a target assuming that we already know some basic information about their system. These include their IP address, operating system, open ports, services running, and so on.

For the most part, keyboard shortcuts are great. They save you some time and make it easier to do everything right from the push of a button. But like most things in life, there is always a caveat, and in this case, for me—it's a huge one.

Security researcher and iPhone hacker pod2g has brought attention to a flaw in Apple's iOS that allows the user to change the reply address of an SMS message. This bug has been a part of the iPhone's SMS since the first iPhone in 2007, but Apple has yet to address it. Basically, there's a section in the text payload called User Data Heading (UDH) that controls some advanced features, one of which is the reply address. By changing the reply address of a text message, you can make someone send ...

This video tutorial shows how to open a port for torrent downloading on your computer. Click Start menu, type cmd command in Search area. In cmd window type ipconfig and press Enter. Remember or write down your IP adress. Type exit and press Enter to close cmd window.

This video shows you how to control your computer from your iPod touch. 1. Go to UVNC. Click on Installation. This will take you to download options. Download the latest stable version. 2. Install Hamachi, which helps you find your computer's IP address. Click on Download Here link, fill in the registration information, and click submit. 3. Install a VNC listener on your iPod so it can connect to your desktop. Jailbreak your iPod, and open the installer. Click All Programs; scroll down until ...

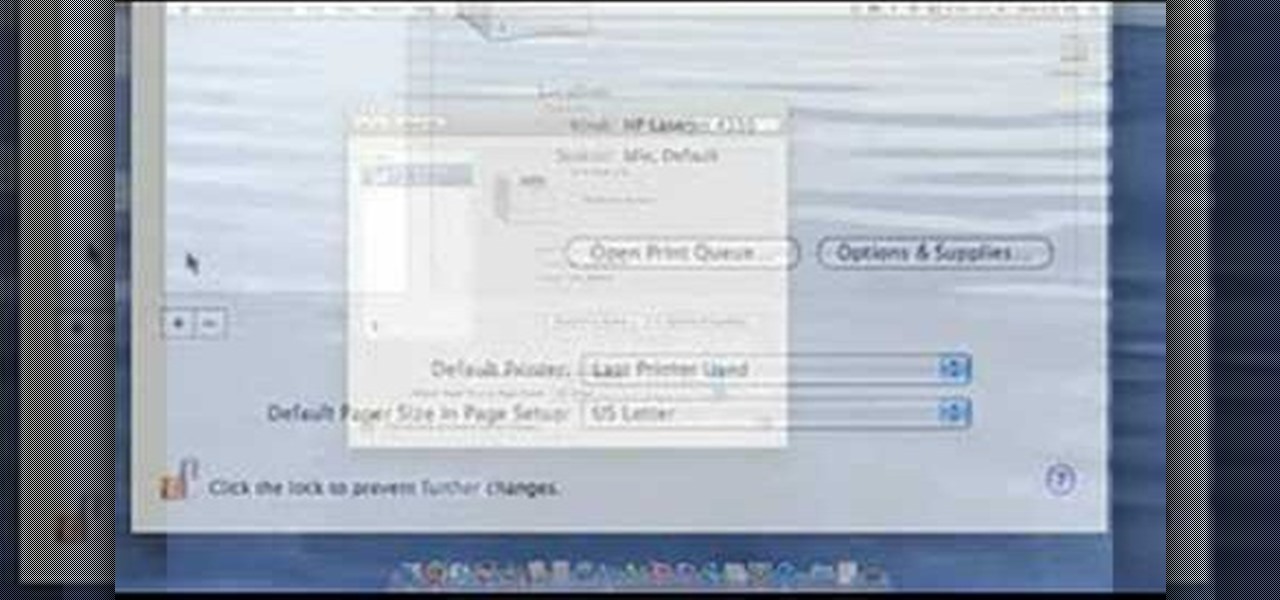
This video demonstrates how to setup a printer on a Macbook Pro.Open the document you wish to open. Go the File menu on the top bar menu and select Print. On the Print dialogue box, you will notice that no printer is selected. Click on the drop down menu to select Add A Printer. Click on the IP found on top of the window. Change the protocol to IPP or Internet Printing Protocol. On the address bar, type in the address of your printer then click on Add. Once done, you can now print your docume...

In this tutorial, we learn how to use GPS and maps on the Nokia N97. From the home screen press the menu key. Then, scroll down and tap the maps icon. After this, tap yes to go online. You can now navigate around the map by using your finger and you can zoom in and out by using the zoom icon. This icon is on the left hand side of the screen. To search for an address, tap the search icon and then tap address or places to choose where you want to go. You will then be shows the GPS and have dire...

A leaky washing machine is a problem that should be addressed quickly. Any access water leaking out of your machine can cause your floor to be slick and possibly create a mess, especially if you have carpet.

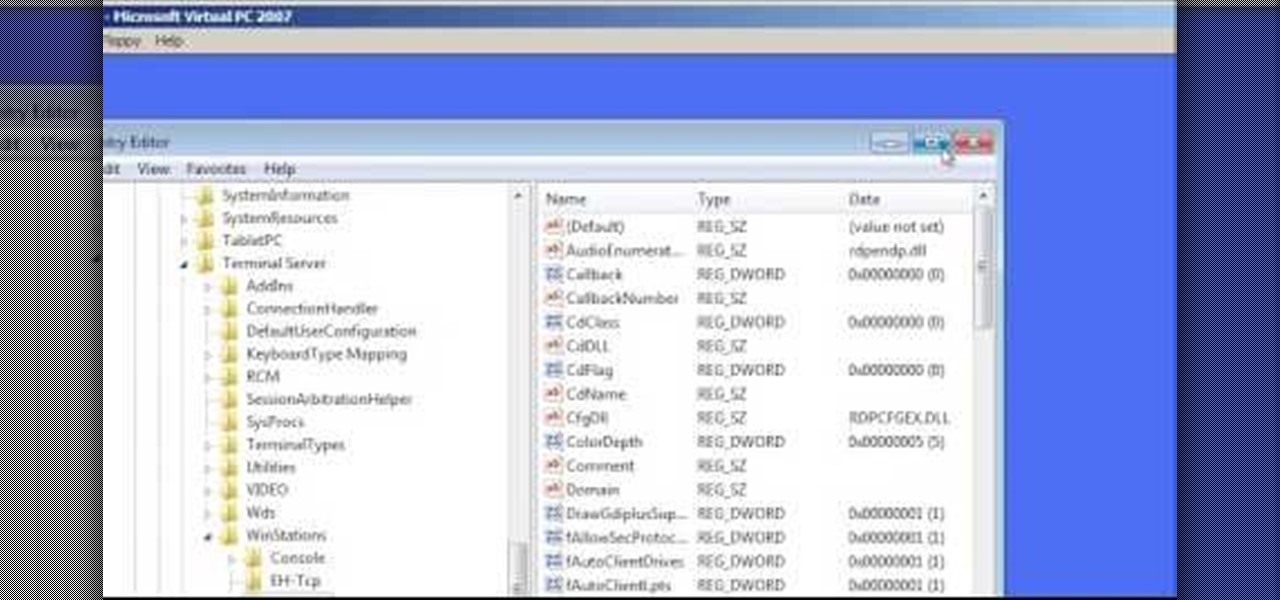
In this Computers & Programming video tutorial you will learn how to change the default Windows Remote Desktop port. It is actually a registry hack. You can check the IP address of our machine by typing ipconfig into the cmd prompt. For hacking into a machine, you should have created a user for the machine and allowed remote desktop to that user. Open up the remote desktop and type in the IP address and it will ask for a login. To hack the registry, click start and type in ‘regedit’ . now go ...

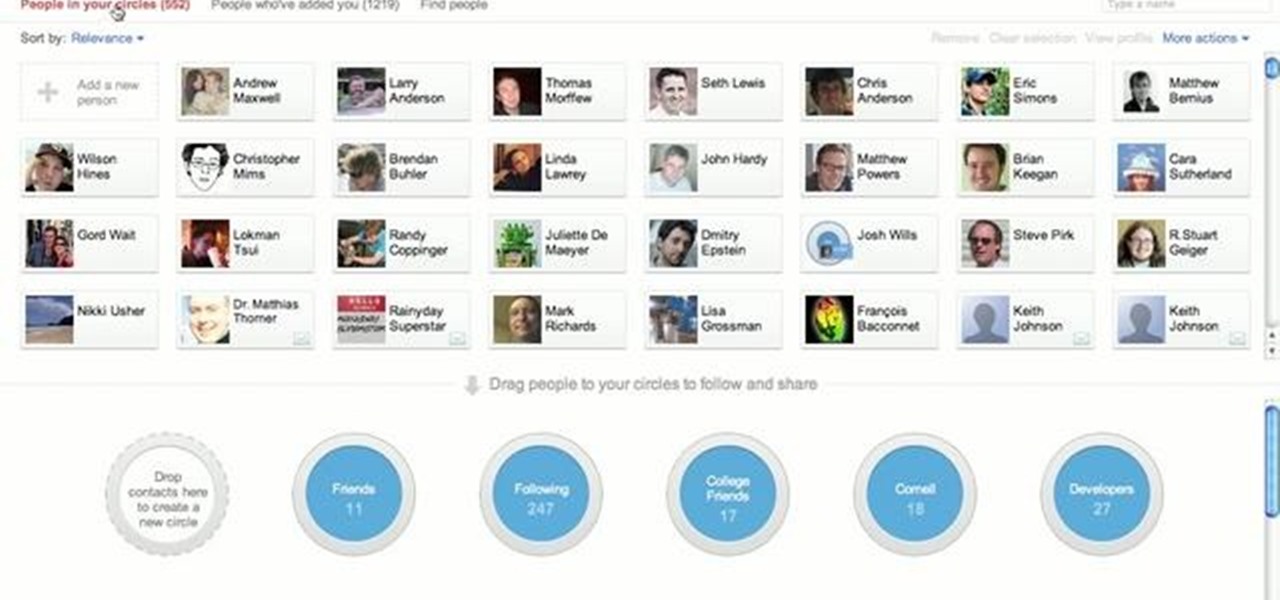
In addition to being a great way to share content and information that are also using Google+, additional sharing features in Google+ allow you to send content and information to other individuals who do not use the service. You can even import your address book to make sharing even easier.

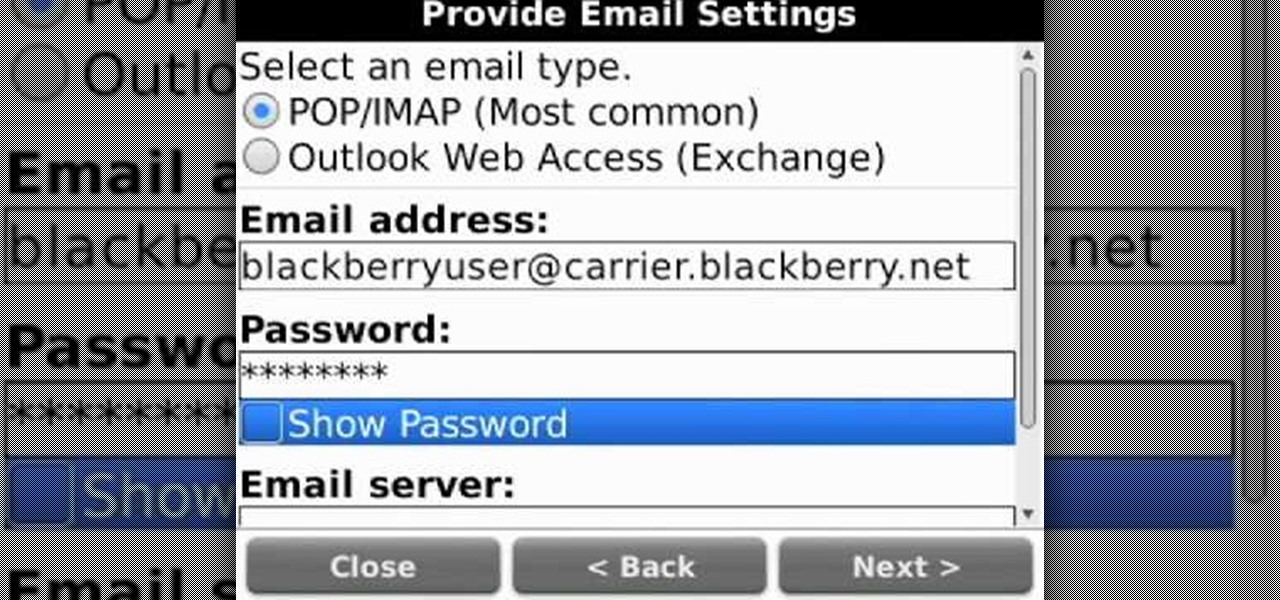
Well, you've got your friends & family email account, your email account for buying junk and that little secret email you keep for all other reasons. If you've been looking for a way to get them all onto your AT&T BlackBerry, here's a clear & concise tutorial teaching you how to do just that.

Want to Google Earth-style bird's eye view of a given address? This clip will show you how it's done. It's easy! So easy, in fact, that this handy home-computing how-to from the folks at Tekzilla can present a complete overview of the process in about two minutes' time. For more information, including detailed, step-by-step instructions, take a look.

While Google Maps is useful for finding addresses and calculating directions, it's not, strictly speaking, very fun. Unless, of course, you know how to hack it. This hacker's how-to from Tekzilla will show you how to access a number of Easter eggs and hidden features like a geography quiz game.

Learn how to manage multiple email addresses at once on your BlackBerry phone. This clip will show you how it's done. Whether you're the proud owner of a BlackBerry smartphone or are merely considering picking one up, you're sure to be well served by this video guide. For detailed information, including step-by-step instructions, take a look.

Google is one of the most powerful forces on the Internet, and their technology can be the key to helping you find success in whatever your online endeavor might be, from web design to filmmaking. This video is a part of their Google Webmaster Series, offering help to webmasters the world over on how to best utilize Google in their work. This video will show you how to optimize your deep web content, like databases and forms, to be crawled by Google using a few simple tricks.

The Contacts application on Android-powered cell phones provides a powerful way to manage your address books and keep in touch with friends and family. You can even add and manage multiple accounts from various sources. Watch these tips from Google to learn who to get the most of the Contacts Android app.

The browser on your Android-powered cell phone offers numerous features that enhance your overall web experience. Some of the great features include double-tapping to zoom in, searching for text on webpages, sharing websites with friends, and copying and pasting. There's a lot more, so watch this video tip from Google to see how to fully enjoy your web browser.

Create a text box for the web using Adobe Photoshop! Whether you're new to Adobe's popular image editing software or simply looking to pick up a few new tips and tricks, you're sure to benefit from this free video tutorial from TutVids. For more information, including step-by-step instructions on how to create and slice up your own custom text boxes in Photoshop from scratch, watch this web designer's guide.

Right out of the box, iPhone is incredibly easy to use. If you want to get the most out of every feature, you’ve come to the right place. This video tutorial straight from Apple will teach you how to browse the web with Safari on the Apple iPhone 3G. The iPhone redefines what a mobile phone can do.

This video tutorial talks about browser exploitation. Particularly, it talks about tools, like BeEF, that can be used to hack known vulnerabilities within browsers and some cool frameworks that you can use to check the security of your own browser. To get started hacking your own browser, watch this how-to.

This video provides an introduction to building 15mm scale buildings for Warhammer or miniature dioramas. Simulate roofing shingles and with small pieces of cardboard. Create a haunted scene with real spider webs. Preserve tiny spider webs with a protective spray or make miniature spider webs out of milkweed. Build small scale grapevines with toothpicks, wire, and painted leggy moss.

The spider web stitch and the ribbed spider web stitch are both "woven" embroidery stitches, either used as isolated accents or used in clusters. They aren't a line stitch or a filling stitch, and they aren't really a "small" detached stitch that can speckle a background lightly, either. Watch this video from Needle 'n Thread to see how it's done.

Screen mirroring software has been around for ages, allowing you to mirror your iPhone to a projector, laptop, TV, or another device. It's useful to have during lectures, presentations, and meetings, so it's no wonder why Apple created its AirPlay technology. However, AirPlay doesn't work in all situations.

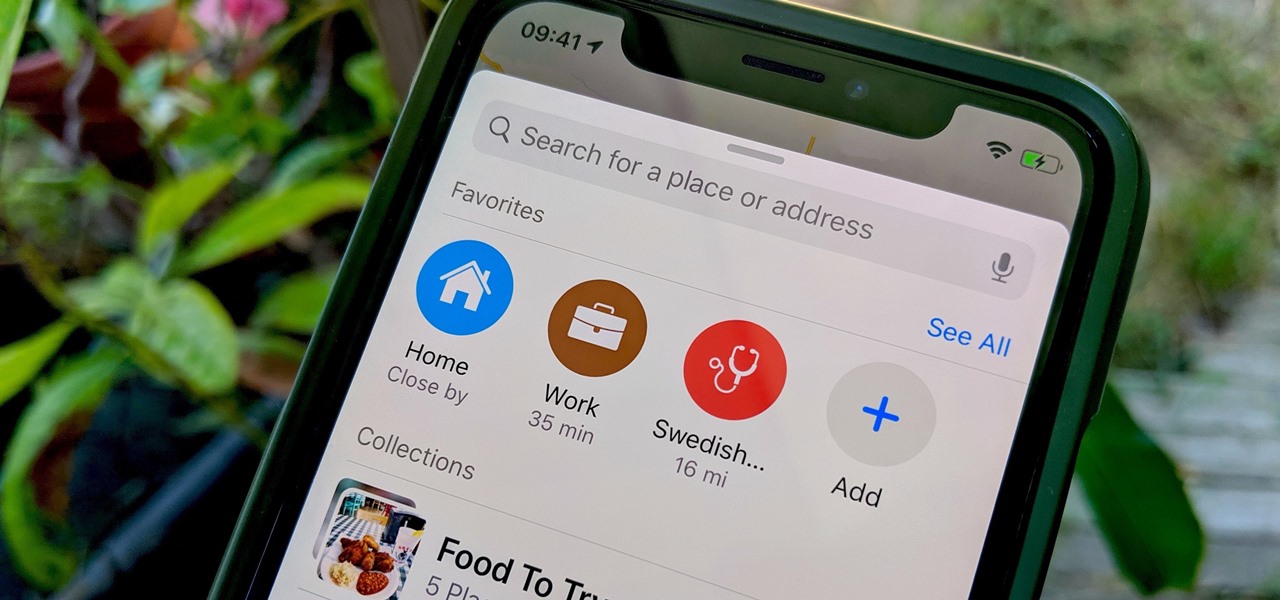
In iOS 13, Apple Maps makes it easier for you to organize essential places on your iPhone, allowing you to save locations as favorites that you can access at a glance.

Business hours and addresses change, but they're not always updated on Yelp by business owners for the rest of us to see. Showing up when a business is closed or going to the incorrect address is a major annoyance, which is why the company allows us, the customers, to help update business information through the Yelp mobile app on iOS and Android. If owners won't do it, somebody has to.

Reconnaissance is the phase of an attack where a red team or hacker designs a strategy based on the information they can learn about the target, as well as what the available attack surface looks like. These scans can take time to discover relationships, but Raccoon OSINT scanner coordinates multiple automated scans to produce invasively detailed reports on a target with a single command.

A simple security flaw can allow an attacker to gain a strong foothold with little effort on their part. When a web application permits remotely hosted files to be loaded without any validation, a whole can of worms is opened up, with consequences ranging from simple website defacement to full-on code execution. For this reason, RFI can be a promising path to obtaining a shell.

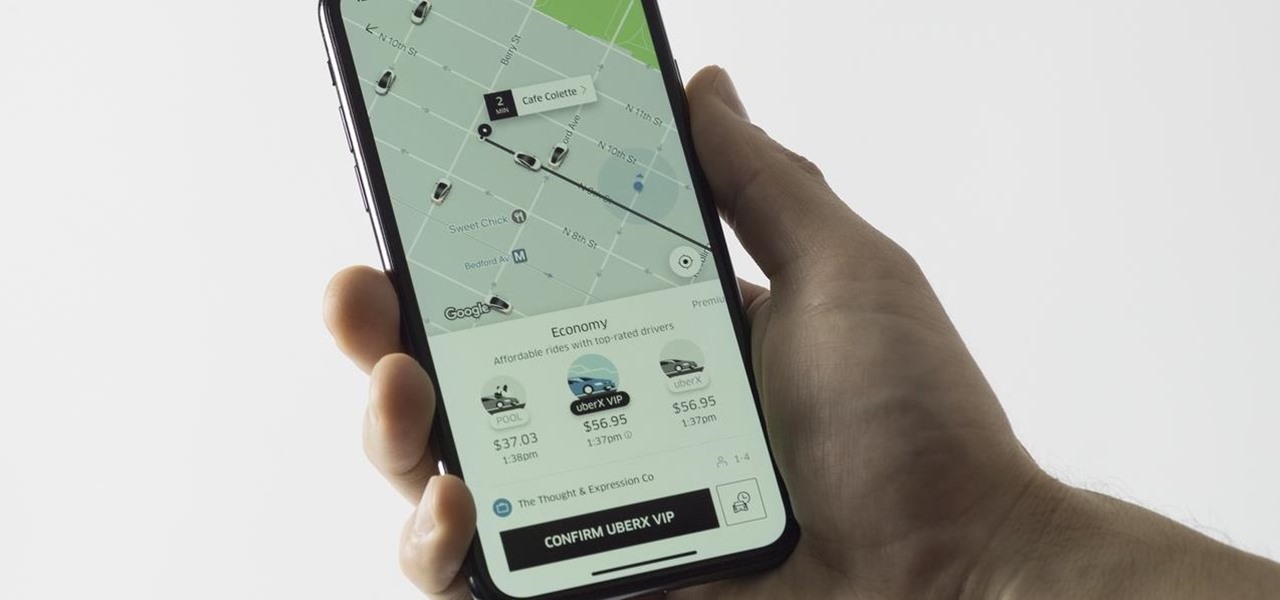
Uber is one of the best ride sharing services out there, allowing you to travel without needing to be tethered to a car of your own. Still, if you're a frequent flyer, you may get tired of entering the same few locations into your app every time you use it. Fortunately, Uber lets you streamline this process.

In the previous article in this short series, we learned how to find our neighbor's name using publicly accessible information and how to monitor device activity on their home network. With this information at our disposal, it's time to get into installing and configuring the necessary tools to begin our attack on John Smith's computer.