Google Meet might not have virtual backgrounds like Zoom, but it hits all of the other basics, from hosting many multiples of video participants to sharing your screen, that you'd expect from a robust video conferencing platform.

If you have devices that run different operating systems, you know how frustrating it is that Apple's Calendar app isn't available on other platforms. If you use Siri to quickly create an event on your iPhone or Mac, you're not going to see that event on your PC or Android tablet unless you sync your calendar to another service.

Your social security number, credit card information, and medical history can fall into the wrong hands if you're not careful about how and where you share your data online. If you really care about your data, there are tools and techniques you can utilize to protect yourself from cyberstalkers, advertisers, and hackers in a time when digital lives are a high commodity.
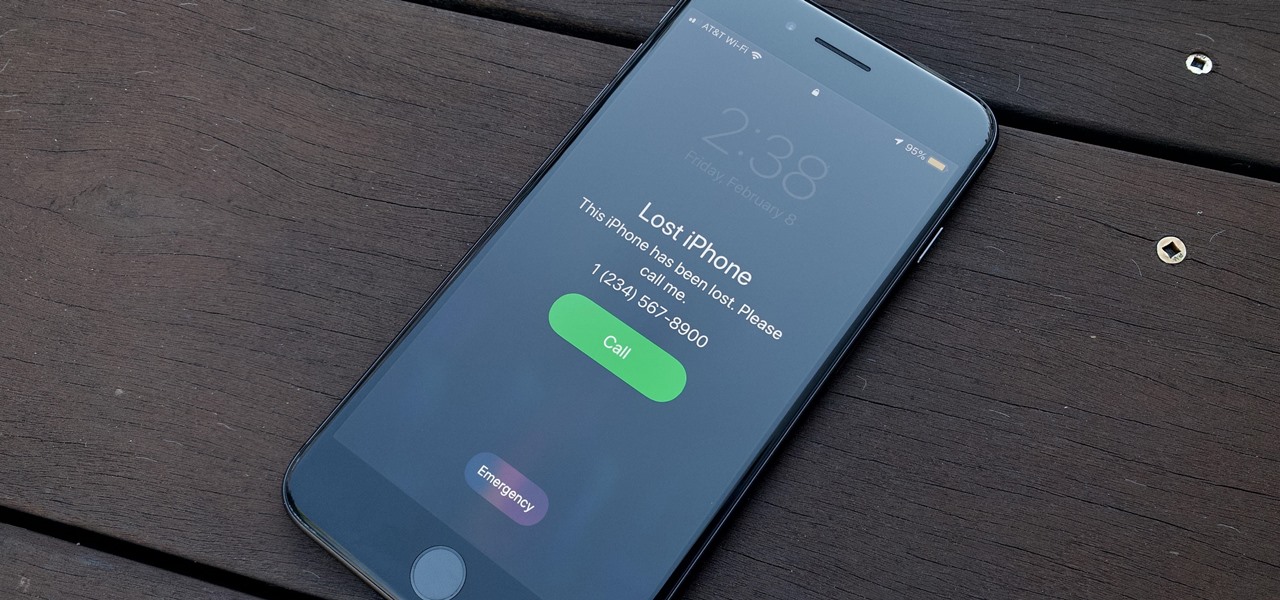
So, you're on the way back from a restaurant and realize you left your iPhone there, but you're late for a meeting and can't go back yet. You may as well kiss that iPhone goodbye, right? Not yet, as long as the right person gets their hands on it first. But that potential do-gooder won't know to contact you, and that's where Find My iPhone's "Lost Mode" comes in handy.

A simple security flaw can allow an attacker to gain a strong foothold with little effort on their part. When a web application permits remotely hosted files to be loaded without any validation, a whole can of worms is opened up, with consequences ranging from simple website defacement to full-on code execution. For this reason, RFI can be a promising path to obtaining a shell.

When it comes to your security, you want the best of the best. Why settle for mediocre service with something as valuable as your protection? Malware continues to make its way onto the Play Store, leaving millions of devices vulnerable. You need an app that will shield your devices from both the latest malware threats and threats nearby. And when it comes to antivirus apps, there is only one choice.

Many guides on Null Byte require using the Secure Shell (SSH) to connect to a remote server. Unfortunately for beginners, learning to use SSH can become a confusing mix of third-party programs and native OS support. For Chrome OS users, using SSH is even more difficult. We'll fix this by using the Chrome Secure Shell to establish an SSH connection from any device that can run a Chrome browser.

Koushik Dutta, the developer behind the Android app AllCast, has made the leap over to the realm of personal computers with his latest offering.

With Google's recent release of the Software Developers Kit for Chromecast, Android gurus now have a roadmap of sorts to guide them in adding Chromecast functionality to their apps. The results are beginning to pour in.

If you're marginally inclined towards computers, you've probably been approached at some point by a family member who wants you to "fix" their system during a visit home. With the holidays coming up, these opportunities (or ambushes) are even more likely.

Since the release of the Samsung Galaxy Note 2, many of its features have been replicated by Android developers for other devices. The most popular feature, aside from Smart Rotation, on the Note 2 has been the multitasking multi-screen/multi-window feature, which allows you to run several apps at the same time.

In this video tutorial, viewers learn how to quickly switch tabs with the keyboard. Users will need the Fire Mozilla browser to do this. Begin by going to the Firefox Mozilla add-on site and search for "crtl-tab". Then click Add to Firefox to install the add-on. To activate the add-on, simply press the ctrl and tab buttons on the keyboard. It will then open a thumbnail of your 7 most recently accessed tabs. There is also a search bar for users to use to find a specific site. This video will b...

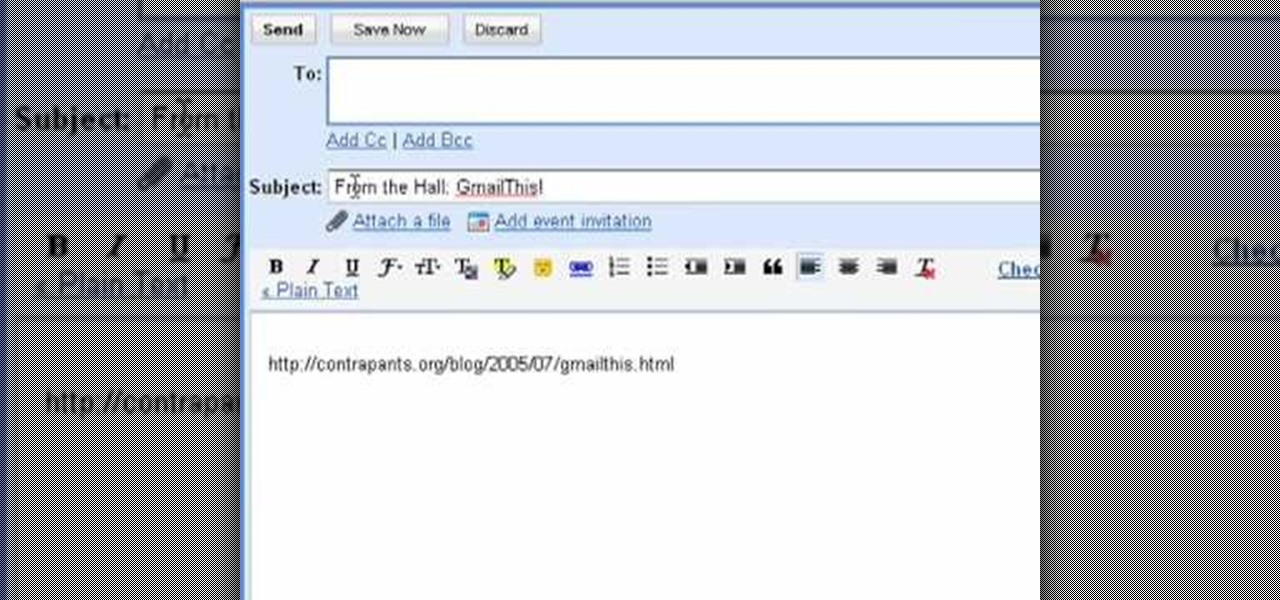
The bookmarklet tool lets you send Gmail messages with the click of a button so you don't have to visit your Gmail account. It's an application called GmailThis! From the developer's website, drag the GmailThis! link to the browser's toolbar. Then, if you are already logged into Gmail, just click on the bookmark and a Gmail applet will pop up with a link to the website you were visiting, along with any text you may have been highlighting. You may notice that the subject line is already filled...

Learn how to watch TV on your computer with Firefox add-on. * Note: You must have a version of Firefox that is older than 3.5.

This walkthrough will show you how to view your Google+ notifications using the bar at the top of your browser window when you are on any Google property. You can easily click through all of your notifications by using the newer and older buttons at the top of the notification window.

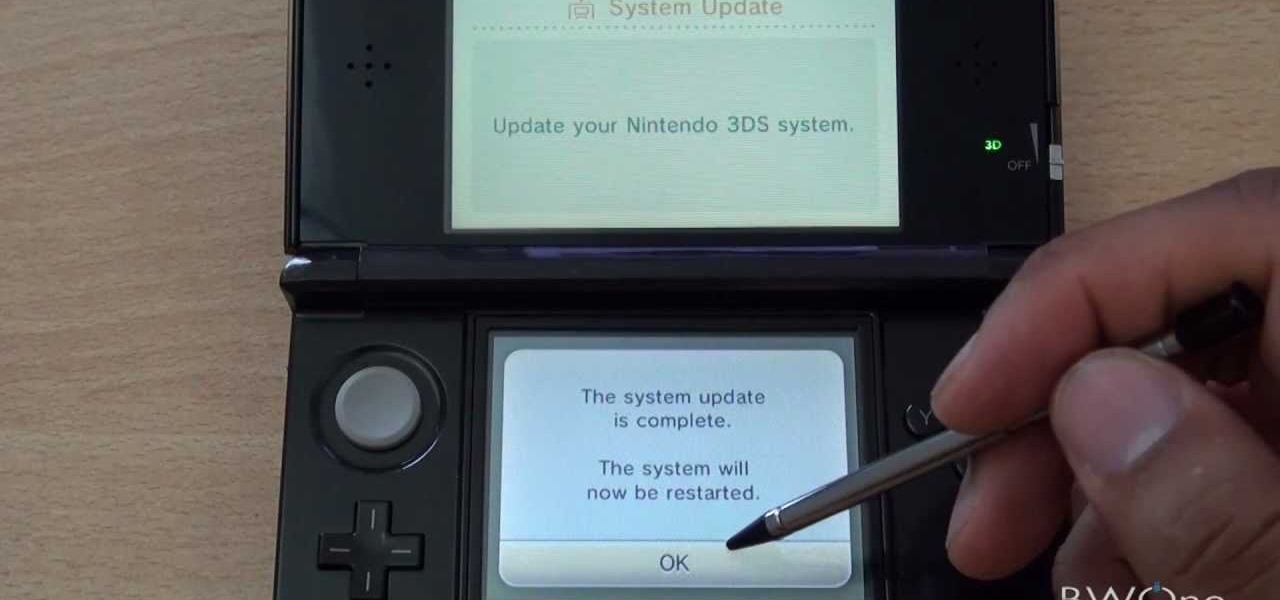
Similar to the Wii, Nintendo frequently updates the apps and software on the Nintendo 3DS. These upgrades are always available using System Update under the system settings on the gaming handheld. Take a look at this guide on how to access the System Update feature, download, and install the updated software. Now you can always access the latest version of the Nintendo 3DS software and apps, such as the eShop and internet browser.

Firesheep is a packet sniffing browser exploit that can access the exposed accounts of people on Facebook and Twitter while they use public Wi-Fi connections. This video shows what steps can be taken to protect yourself against someone accessing your Facebook account.

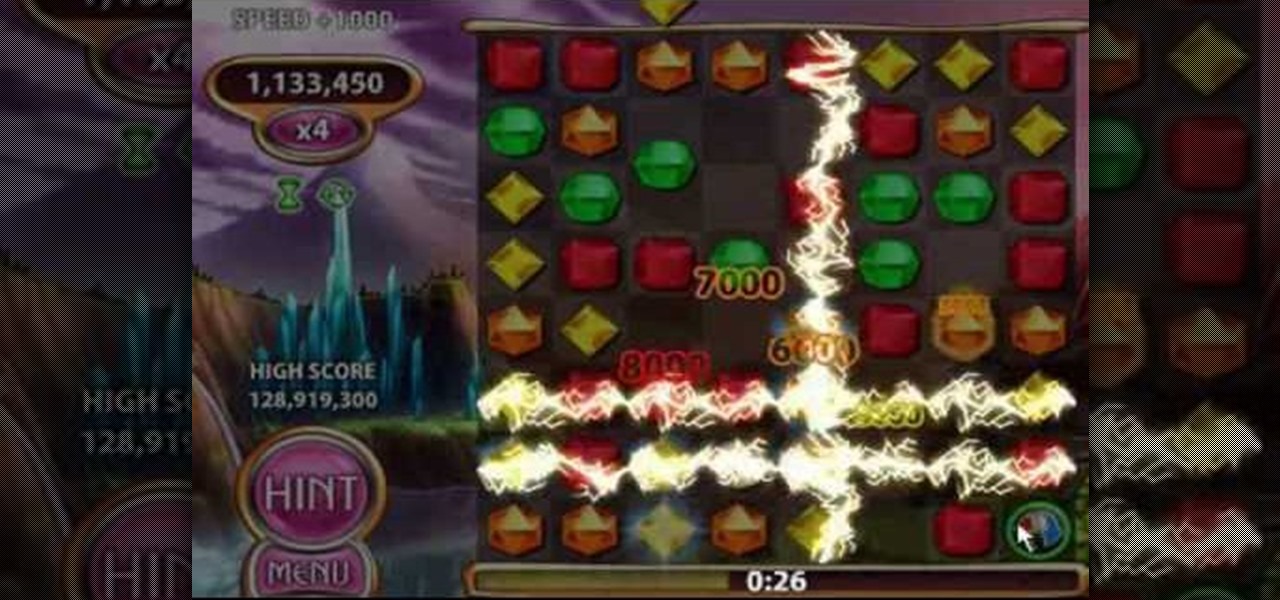
Hack the hex code in Bejeweled Blitz for a higher score! Everyone wants the top score in this popular web game, but it all comes down to how you get it. Do you have what it takes to come out on top? Check out this video tutorial to learn how to hack Bejeweled Blitz (07/24/10).

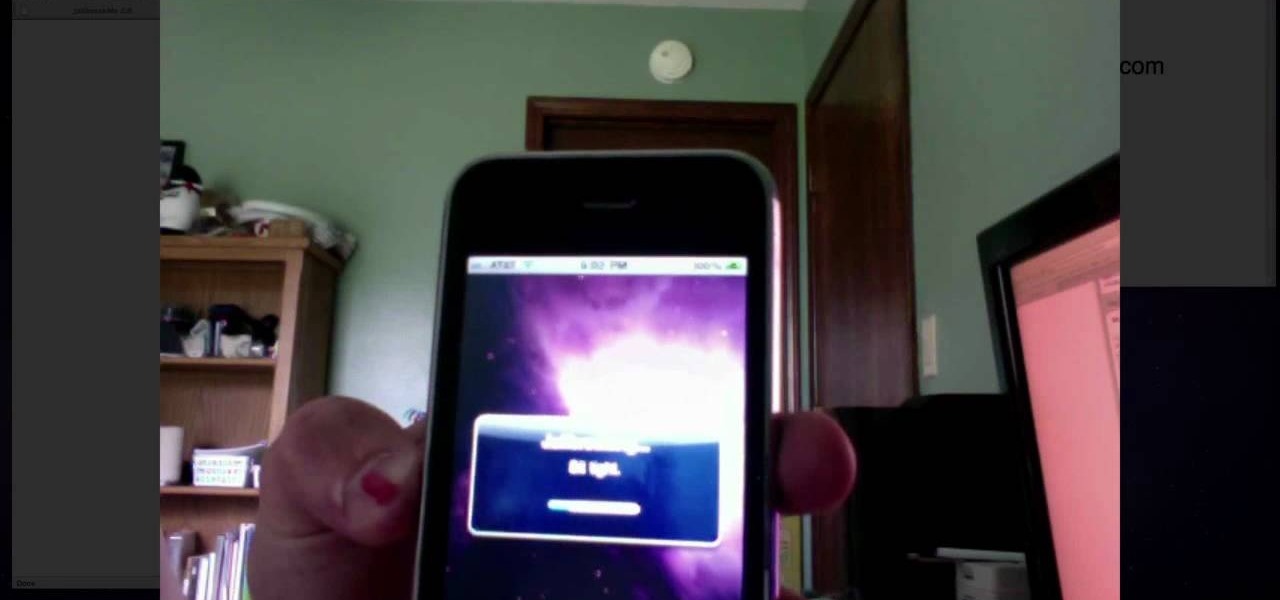
It's official! You are both able and allowed to jailbreak the iPhone 4. And oh boy is it easy! This video will show you how you can jailbreak your iPhone 4 quickly and easily using a program called Jailbreakme that you can acquire very quickly and for free right on your iPhone browser. How much easier could it be?

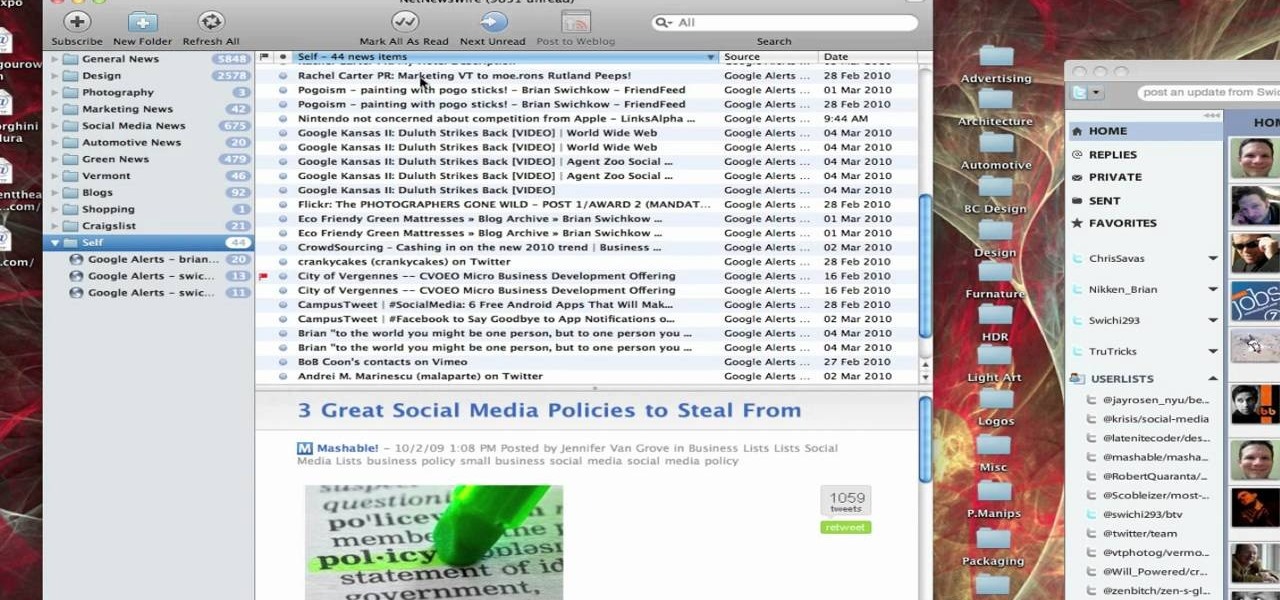
This video tutorial from TruTricks presents how to setup Google customized alerts.Open your internet browser and search for Google Alerts using Google search engine.Click first result that says Google Alerts.You will need to sign in to use this Google feature.Google or Google mail account will work. If you don't have it you should create one.After you signed in Google Alerts welcome screen will open.Here you can create new Google alerts using Create a Google Alert window.Enter Search Term you...

This video is about downloading videos in Firefox. Firefox is a web browser, but it will be used rather than Internet Explorer because Firefox allows you to install plug ins. Go to the tools menu and click "add-ons". Download helper is the add on we will select. Click "get extension". A web page opens. In the search box, choose "search for add-ons". Add to Foxfire. Install now. Restart to complete installation. On the toolbar you will see three rotating bars which will let you know the add on...

Aperture allows you to easily sort the images in the browser pane in several different way. By default, images are sorted by creation date.

You can easily integrate images from your Aperture library into your Keynote '08 presentations using the Keynote media browser.

Every single photo you take carries with it a considerable amount of seemingly "invisible" yet important information known as metadata. Although metadata is usually helpful to sort your photographs by location and date, that same information could potentially be used against you, especially if the pictures are taken during a precarious situation.

Over the past year, Magic Leap has teased its cross-platform vision of the AR cloud, which it dubs the Magicverse. While the company shared a timeline for its debut next year, it also served up new developer tools for the present.

When it comes to the athletic footwear retail game, it's just not enough to just sell shoes anymore.

Metadata contained in images and other files can give away a lot more information than the average user might think. By tricking a target into sending a photo containing GPS coordinates and additional information, a hacker can learn where a mark lives or works simply by extracting the Exif data hidden inside the image file.

If you've ever wanted to barge into Jerry Seinfeld's apartment like Cosmo Kramer, you can now do so without having to book a ride on the Peterman Reality Tour.

Unless you're completely new to Instagram, it's likely that you've linked your account with a third-party service at some point and forgotten about it. Those services still have access to data such as your media and profile information, so it's important that you not only know how to find these "authorized" apps, but that you know how to revoke their permissions.

Android is a highly customizable operating system, but that doesn't always apply to the apps you find on the Play Store. Most of the time, when you install an app, you're stuck with the default look and feel — but luckily, this isn't the case with Firefox. Unlike most other browsers, you can actually install themes to change the look of the top browser for Android.

The biggest corporation we know today is called Google, I bet you've heard of it yeah? How Google Tracks You:

Chrome's download bar has looked pretty much exactly the same for years now—a simple horizontal menu that spans the entire bottom of the browser and displays buttons for each of your recent downloads. It's not exactly pretty, and when it comes to functionality, the space it occupies could certainly be put to better use.

Unlike in the physical world, on the internet you're actually able to shut people up and block spoilers of newly-released movies, your favorite TV shows, or a sports event you've yet to watch on your DVR.

When we hack a web server, we usually want to be able to control it in order to download files or further exploit it. There are many websites that let you upload files such as avatar pictures that don't take the proper security measures. In this series, I will be showing you how to gain root access to such a web server.

Welcome back, my novice hackers! In this continuing series on Metasploit basics, let's next look at a module that many aspiring hackers find useful—autopwn.

Despite being one of the largest and most feature driven companies on the planet, Google can sometimes come up short. I have my Chromecast running 24/7, and while I use my phone to cast most of my content, I sometimes find a video while browsing Reddit or LiveLeak on my laptop and I'd rather just cast it from there.

Let's be real, browser histories are virtually useless. Trying to find something you passed up a week ago is like, pardon the cliché, finding a needle in a haystack.

I'm still amazed by all the things some people just don't know. Script-kiddies often refer to Metasploit if someone asks them how to hack a computer because they think there's simply no other way. Well here I am today trying to increase your set of tools and -of course- skills.

The first album I ever bought with my own money was Nirvana's MTV Unplugged in New York. It featured mainly lesser-known songs and covers, but was on constant repeat on my Walkman. While the whole album was fantastic, there was one song that stood out the most to me—"The Man Who Sold The World." The song (originally written by David Bowie) kept me under a spell, which had me replaying the song over and over and over and over. As I got older, I found myself sharing this relationship with a han...

If you want to know the most up-to-date news on a trending topic, Twitter can be a great place to look since people generally tweet about things as they happen. It used to be easy to find Twitter results in Google Search, but after their deal expired last year, tweets are no longer included in search results.