Link shorteners like TinyURL and Bitly are great for Twitter (or anytime you're limited on space), but they're also great for hackers. It's easy to hide a malicious link in an innocent-looking shortened URL, which increases the chances that people will click on it.

Even though we all know it's a bad idea, a lot of people still use their browser's store password function to keep up with all their accounts. While convenient, this shortcut also makes their passwords very easy to find if you have access to the computer they're stored on.
Want to get an absurdly high score on the Mindjolt game, Cube Crash? Of course you do, and that's precisely what this video tutorial is going to show you. You will first need the free game hacking program Cheat Engine, as well as a Cheat Engine compatible browser (such as Internet Explorer or Mozilla Firefox - this won't work if you're using Google Chrome). If you have both programs, open up Cube Crash in your browser, then open up Cheat Engine and just follow the outlined instructions to hac...

In this tutorial, we learn how to save music from MySpace as an MP3. First, download and install the Firefox plug-in from: https://addons.mozilla.org/en-US/firefox/addon/1843. After this, go to MySpace and search for the artist whose music you want. Then, click on the top of the browser on the "view" button, then click "page source". After this, search "mp3" at the bottom of the page, then scroll through until you see "<PARAN NAME="src"value=themp3linkwearelookingfor" and copy this. Paste thi...

In order to find out if an email is a scam, you should avoid clicking on any links in that are in any emails. The links that are attached to emails, in this manner, usually have cloned the website of the institution where you do your banking. The link will look similar to your banking institutions site. Do not enter any of your personal information in emails in this fashion. Your bank will not contact you in this way.
In order to get add-ons and plug-ins for Google Chrome, you to go to Chrome Plugins. Type the address into your browser. Then, press Enter. Scroll down the list. Choose and add-on that you want: for example, Click & Clean. Click on the one that you would like to choose. Find "Download Latest Version" and click on it. Wait for it to download and click on it. There are lots of options. Click & Clean allows you to clean your browser with only one click. Session Save allows you to save the sessio...

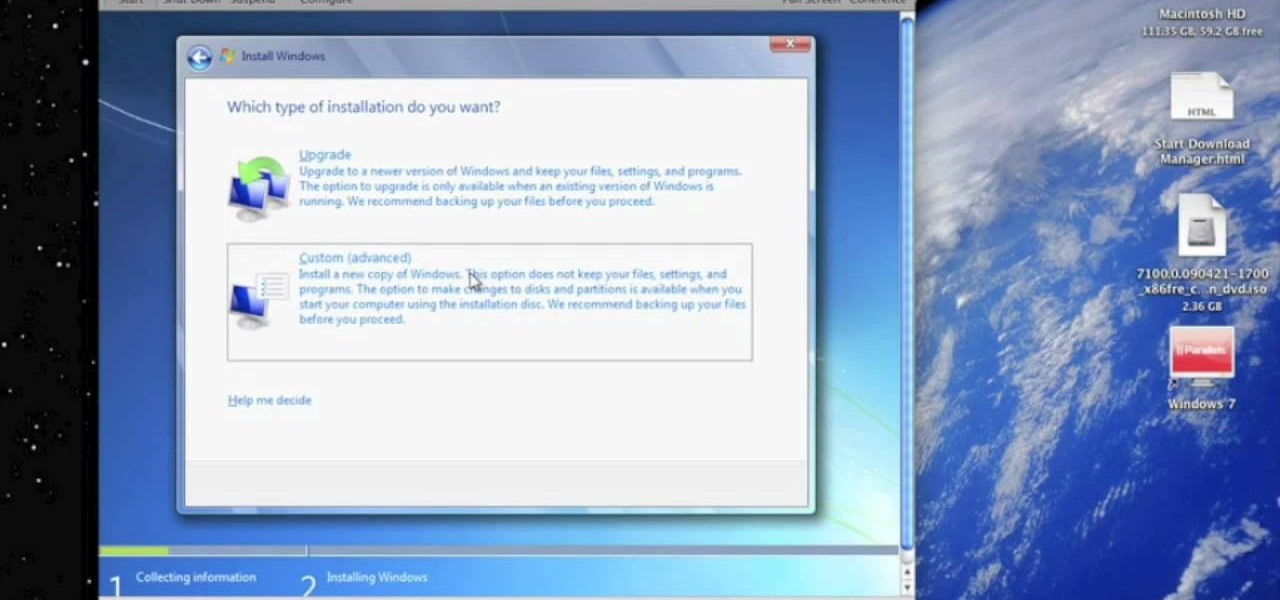
In this Computers & Programming video tutorial you will learn how to run Windows 7 on a Mac using Parallels. First you got to download Windows 7. For this you will need Firefox browser. Open the browser and go to www.microsoft.com/windows/windows-7/download.aspx. Scroll down and under the 32 bit download link, select English and click GO. If you have a windows account, type in your email and password and sign in. You will get the download link in the email. Go to the link, it will have the pr...

In this tutorial, we learn how to save drive space using Firefox. If you want to change the cache folder location, whether it's for security or just because, it's very simple. First, type in "about:config" into your internet browser. A new page will appear, right click your mouse and select "new" and then "string". When the page asks for the preference name, type in "browser.case.disk.parent_directory". Then, type in the name of the folder where you want the cache to go. Next, Firefox will cr...

Deleting your Internet history once in a while is important. Not only will doing so protect your privacy, but it will also clear up much needed space on your harddrive and help your PC run quicker.

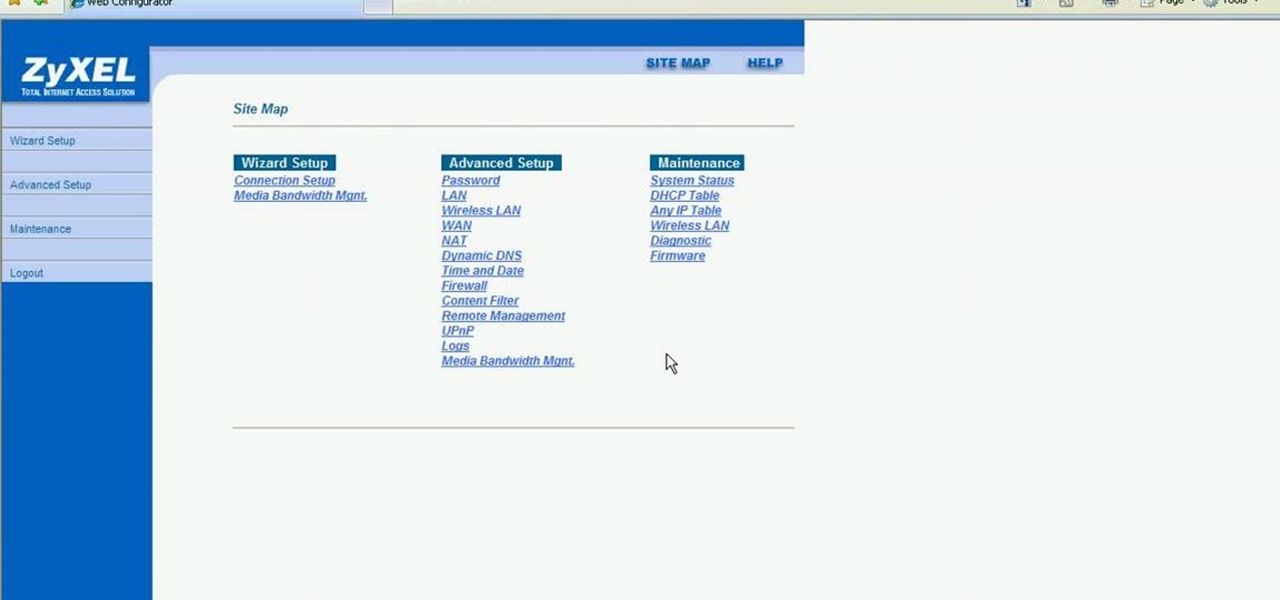
This video shows how to secure a wirelees internet connection on your Zyxel P-660hw-t1. For this, first click on Start button and open Internet Explorer(or any other browser). On the address bar of the browser, type in the IP address of your router. On the next page, enter your password and on the next page, either change the password or ignore. On the next webpage, under Advance setup, click on Wireless LAN. On the next page, click on 8021xWPA. Select authentication required and then click a...

You should use the file Winrar to unzip your file, it's the easiest. You're going to open up an internet browser and go to: Zybomen. Click on download, then click on Winrar. Click on the one that says 32bit, unless you've got a 64bit system which is the second one. Click run, then wait for it to download. Close your internet browser. Click install, go through the process. Right click on the file you would like to unzip, and then click on extract to and then the file name. Double click on the ...

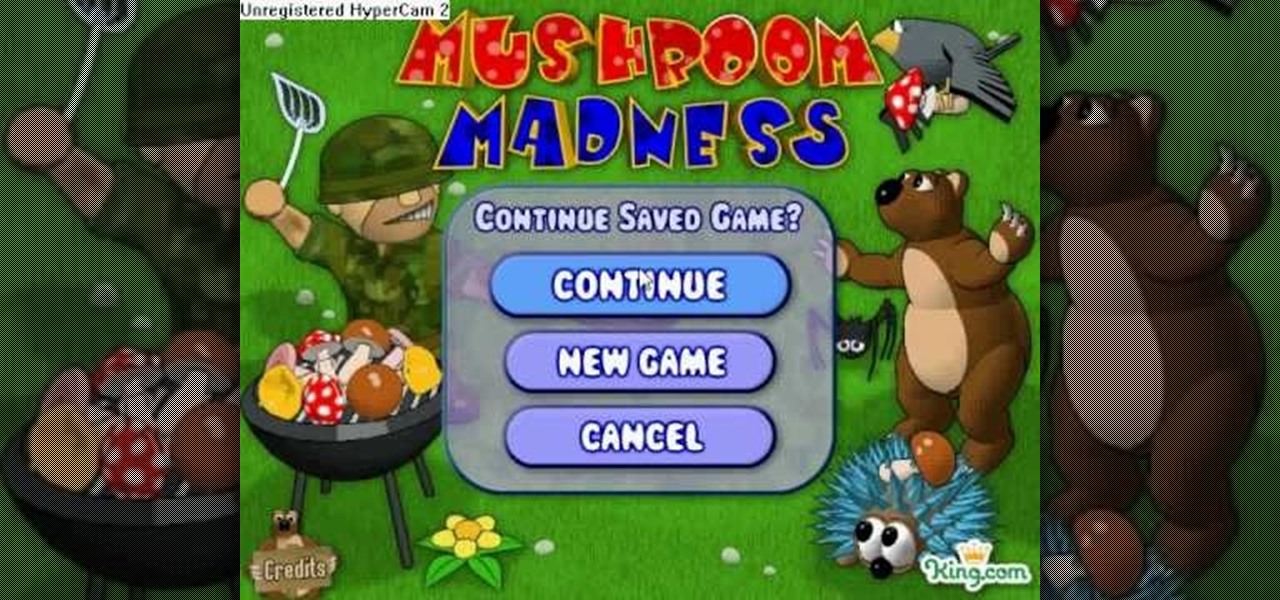
YouTube user Hacker of None teaches you how to hack Mushroom Madness using Cheat Engine. Start the game from Kongregate website and then run Cheat Engine. Search for your browser, which may be Firefox, Chrome or Internet Explorer, in the Process List and then click Open. Change the Value Type to Array of bytes and make sure the Hex box is checked. Then simply enter the values provided in the video to access the hacks. These give you one hit kills, unlimited ammo or no money will be needed. En...

The video provides you two easy ways to get onto MySpace at school. There is no need to install anything at all. If you have a Windows operation system, open a command prompt window and just ping MySpace. Then copy and paste the IP addresses you found directly into your browser's address bar. In case you have a Mac computer, try search 'ip address finder' on Google and tool sites such as ip-address.com can help you find the same information. Now getting onto your favorite MySpace will never b...

This video tutorial shows you how to block any website on a Windows xp operating system by simply using notepad. First the URL to the site that needs to be blocked should be located by visiting the website form your browser and copying the URL from the address bar. Next close the browser and locate the "hosts" file and open it with notepad as indicated. Make the necessary changes to the "hosts" file and save it. Now the selected website is blocked on your computer.

This video shows you how to easily install the Adobe Flash Player in Internet Explorer. The first thing you have to do is open the Internet Explorer and surf to http://get.adobe.com/flash/player/ . Scroll down the page, uncheck the Download Free Google Toolbar box and then click the "Agree and Install Now" button. Then, click the pop-up bar in the upper side of the browser that just appeared, and click the Install ActiveX Control. A pop-up window will appear. Click install and then wait until...

Did you know you can set your homepage on your Motorola Droid just like you can set up a homepage on Firefox or Safari? This video tutorial will show you step by step how to change your browser homepage on the Droid. The Droid is a very cool smartphone with the ability to run multiple apps, so why not take advantage of all of its features? If you want to personalize your homepage on Droid, check out this tutorial and you will be on your way. Your new phone will feel like home in an instant.

Deleting cookies in your Internet browser allows you the freedom to surf privately. Cookies are little chips that store your information for different websites. For example, when you visit your e-mail, a cookie is attached to your browser that remembers your sign in information so you don't have to reenter it every time you navigate away from that page and back. Deleting cookies is a good idea if you are giving or selling your computer to someone else, or if you are on a shared machine. This ...

Removing the cookies from Firefox and Internet Explorer is explained in this how-to video. First let's see how to delete cookies from Firefox browser, just follow the following steps:

Google is one of the most powerful forces on the Internet, and their technology can be the key to helping you find success in whatever your online endeavor might be, from web design to filmmaking. This video is a part of their Google Webmaster Series, offering help to webmasters the world over on how to best utilize Google in their work. This video will show you how to optimize your deep web content, like databases and forms, to be crawled by Google using a few simple tricks.

Create a text box for the web using Adobe Photoshop! Whether you're new to Adobe's popular image editing software or simply looking to pick up a few new tips and tricks, you're sure to benefit from this free video tutorial from TutVids. For more information, including step-by-step instructions on how to create and slice up your own custom text boxes in Photoshop from scratch, watch this web designer's guide.

This tutorial covers the ABC's of getting started in Web Development. Mike Lively shows you how to get a server, a free HTML editor, and free FTP Software.

This video provides an introduction to building 15mm scale buildings for Warhammer or miniature dioramas. Simulate roofing shingles and with small pieces of cardboard. Create a haunted scene with real spider webs. Preserve tiny spider webs with a protective spray or make miniature spider webs out of milkweed. Build small scale grapevines with toothpicks, wire, and painted leggy moss.

The spider web stitch and the ribbed spider web stitch are both "woven" embroidery stitches, either used as isolated accents or used in clusters. They aren't a line stitch or a filling stitch, and they aren't really a "small" detached stitch that can speckle a background lightly, either. Watch this video from Needle 'n Thread to see how it's done.

No website will be inaccessible and no web filter will deny you content once you learn the skills presented in this internet hacking video.

In this video tutorial, viewers learn how to clear their cache in Internet Explorer. Begin by opening the web browser. Then click on Tools from the top menu and select Internet Options. In the General tab under Browsing History, click on Delete. When the Delete Browsing History window opens, click on Delete Cookies and click OK. To automatically clear cookies, click on Settings under Browsing History and check Every time I visit the web page. Then finish by clicking OK. This video will benefi...

There's a million web games spread throughout the internet now, and if you like to play them, you probably want to play them all the time. And if you play one flash game, you probably play another, maybe 10 or 20. But what if you don't have an internet connection one day? What if you can't play those web games anymore? Well, you can, and all you have to do is download them to your computer. Watch to see how to download and play web-based flash games on your computer without web access.

Google Images, TinEye, and other reverse image search engines can help you find where images appear on the internet. You can discover what TV show or movie an image comes from, who took a photo, and if the profile picture of someone you're talking to online is really them, among many other uses. And there's a shortcut for iOS that makes running a reverse image search easy.

Recently, Android Police highlighted one of the downfalls of Android 10's new privacy protection: the fact that it broke the ability for apps like Pushbullet to sync your clipboard across devices. While third-party apps can potentially find a way around this, there's no guarantee. But have no fear, Google is here to the rescue.

Phishing is the easiest way to get your password stolen, as it only takes one mistake to log in to the wrong website. A convincing phishing site is key to a successful attempt, and tools to create them have become intuitive and more sophisticated. SocialFish allows a hacker to create a persuasive phishing page for nearly any website, offering a web interface with an Android app for remote control.

While Toyota ranks as the leading automotive brand in the world, the company is a follower when it comes to augmented reality.

With Tasty dominating Facebook videos and online cooking flourishing, it can be cumbersome to keep track of all your recipes. Someone might send you something, and storing it in an app like Pocket is like jamming all your school papers in one folder — it just isn't practical. Fortunately, there's a better way to catalog your recipes so you can always have them on hand.

Every dollar that comes your way is a blessing, especially when it comes to trading in the volatile world of bitcoins. Thankfully, Coinbase rewards you for sending much valued customers their way, giving you more money to feed your cryptocurrency trading needs.

Tony Parisi, the global head of VR/AR at Unity Technologies, has been passionately working with virtual and immersive spaces for a long time. And while the internet world we live in now is very different than when Parisi was co-authoring VRML (Virtual Reality Modeling Language) — an early attempt at creating 3D environments that would work in a web browser — some of the questions that were assumed answered are being asked again.

The Google Chrome browser for Android is packed with many great features, but it definitely has a bad rep for being slow and laggy on low-end or midrange devices. Without a top-notch processor, you'll likely notice some stutter with choppy scrolling, and pages can take too long to load in general.

Hello friends! This tutorial will teach you how to build a local pentesting lab on your Linux machine which will enable you to easily install common web applications so you can practice locating and exploiting their known vulnerabilities (or discover new ones!). In particular, this is an excellent way to learn how to hack Wordpress, Joomla, and Dupral plus many more!

Welcome back, my greenhorn hackers! Over the years, I have written many articles here on Null Byte chronicling the many the hacks of the NSA, including the recent hack of the Juniper Networks VPN. (By the way, my speculation in that article has proven to be correct. The NSA did embed a backdoor on those devices.)

There's a feature in Google's Photos app for Android, iOS, and the web that lets you create shared albums with your friends and family. It's really a useful feature that makes it fun and easy to collaborate on an album with a person or persons of your choosing.

Welcome back, my greenhorn hackers! Many new hackers come from a Windows background, but seldom, if ever, use its built-in command-line tools. As a hacker, you will often be forced to control the target system using just Windows commands and no GUI.

Like most people who spend a good deal of time in front of their computer—whether for work, school, or play—I jump back and forth from window to window, working and playing with different things at the same time to get my work done faster or procrastinate harder.

Hello you sexy, savage, surreptitiously tech-savvy penetrators (Pun intended)!