How To: Cheat in the flash game Pool Practice (01/01/10)
You want to know how to get extreme scores in the flash game Pool Practice? This is how. Watch this video tutorial to learn how to cheat in the flash game Pool Practice (01/01/10).


You want to know how to get extreme scores in the flash game Pool Practice? This is how. Watch this video tutorial to learn how to cheat in the flash game Pool Practice (01/01/10).
Settling a new planet will decrease your pride ratio, because your population will increase when you're settling a new planet. If you're not sure how to even settle planets...
In order to spy and gain intelligence on your Conrohl enemies, you need to make an intelligence agency. Then you recruit your spies to perform simple espionage.
Flash games are addicting, especially Bouncing Balls. But can you actually beat all of those high scores you see? Probably not, but you can if you use Cheat Engine.

If you're new to DreamCoder for PostgreSQL, one of the very first features with which you'll want to acquaint yourself is the data table browser, which will permit you to display entries in a given PostgreSQL database. For a detailed walkthrough of this feature, take a look at this video tutorial.

In the 21st century, we're all looking for ways to stay private, especially on our electronic devices. We have big tech corporations, enemy countries, malicious hackers, and other prying eyes watching our every move, so it's only natural to want to limit what they can see. Making your web browsing experience on iPhone and iPad more private is one way to do that.
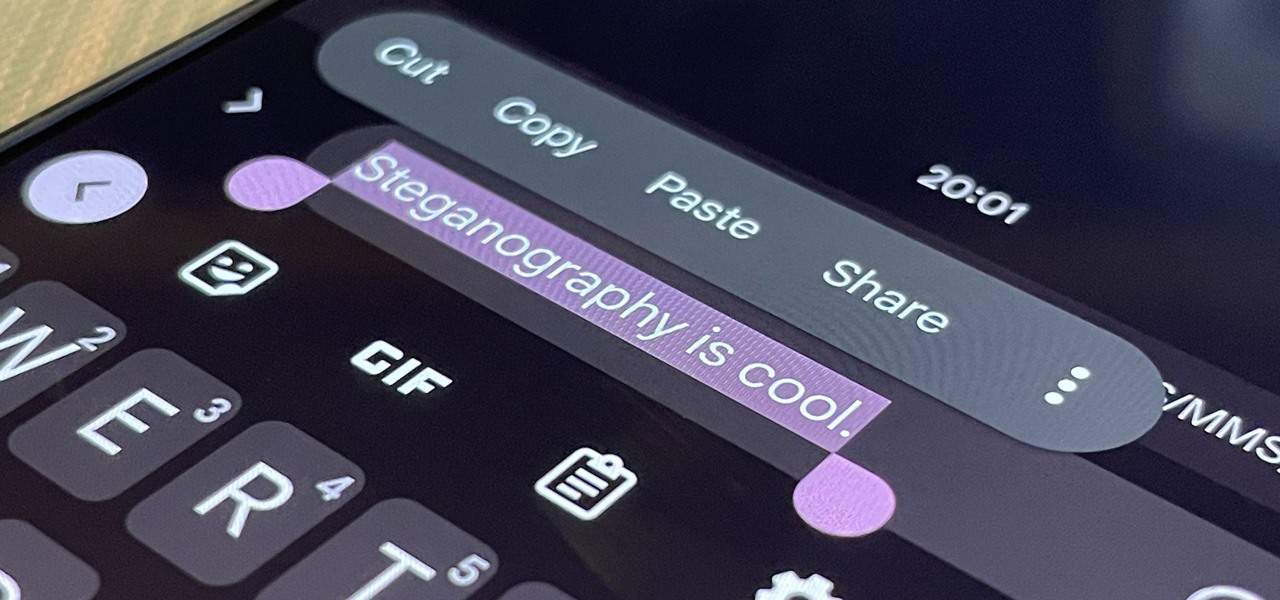
With a simple web-based tool, you can hide secret messages for family, friends, and fellow spies inside of plain text communications, and anyone that intercepts the messages will be none the wiser.

Since its launch two years ago, the HoloLens 2 has been the best AR headset available, and nothing has come close to touching it since.

Just as the NCAA men's basketball tournament is set to start later this month, USA Today has decided to trot out an augmented reality mini-basketball game to promote its bracket competition.

Whether you want to build your own website for your business, start your new lucrative career in web development, or gain a wealth of projects to add to your portfolio, this course will help you do it. And right now, "The Complete Web Developer Course" is on sale for just $14.99 — a staggering 92% discount off the regular price of $199.

Aside from home screen widgets, one of the most exciting updates to the iPhone with iOS 14 is Picture in Picture mode. With it, you can watch minimized versions of videos on top of other apps so you can multitask like a pro. However, not every service is on board with Apple's new features. YouTube is the primary culprit, but there is a workaround.

"What's your Wi-Fi password?" That's usually the first thing guests ask for when you have them over. You tell them the network name, then try to explain your complicated hacker-resistant password, which becomes a whole ordeal. But there's a better way to do it, which doesn't rely on using the same mobile OS as your guests.

The web development landscape has changed dramatically over the past ten years. Both aspiring and seasoned developers now need to know a wide range of programming languages and platforms to create truly pro-level sites from scratch, and continuing education is vital if you want to stay ahead of the curve and be competitive in this increasingly popular and lucrative field.

The only thing better than programming MicroPython is programming MicroPython over Wi-Fi. So once you set up MicroPython on a microcontroller and have it on its own power source, you won't need to use a data cable to connect to it whenever you need to interact with it, program it, upload files, or grab data.
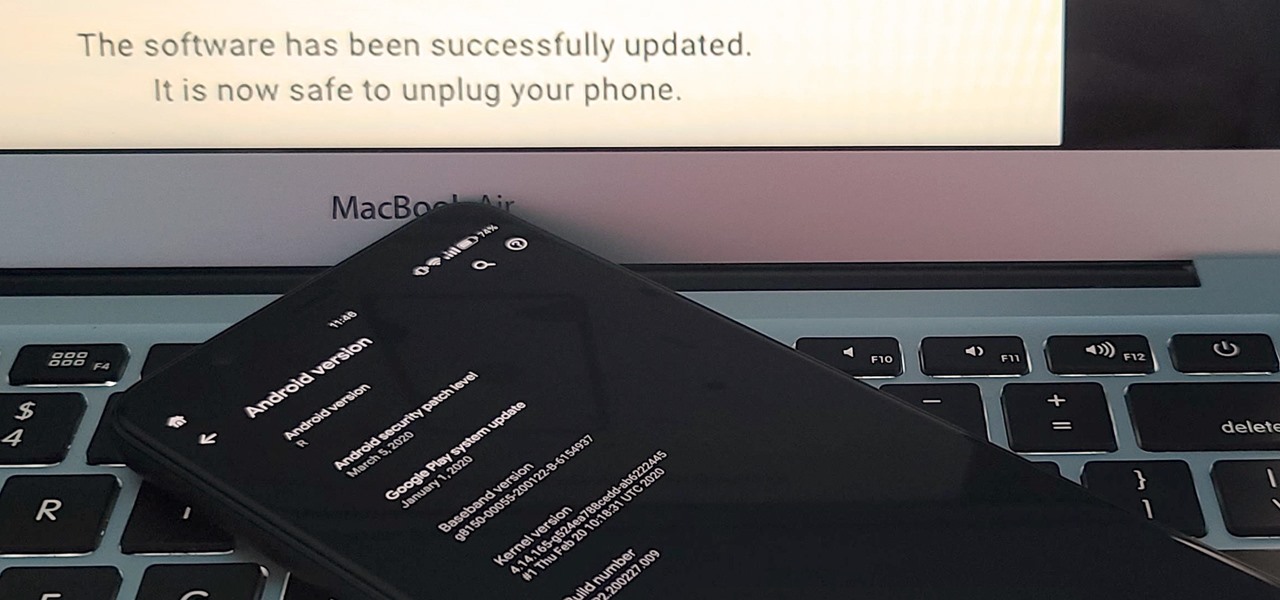
If you've ever tried to update your Android phone manually, you know the process can be unnecessarily hard. There are so many steps and parts, that if one thing goes wrong, the whole process doesn't work. Recognizing this, the Android team came up with an even easier way.
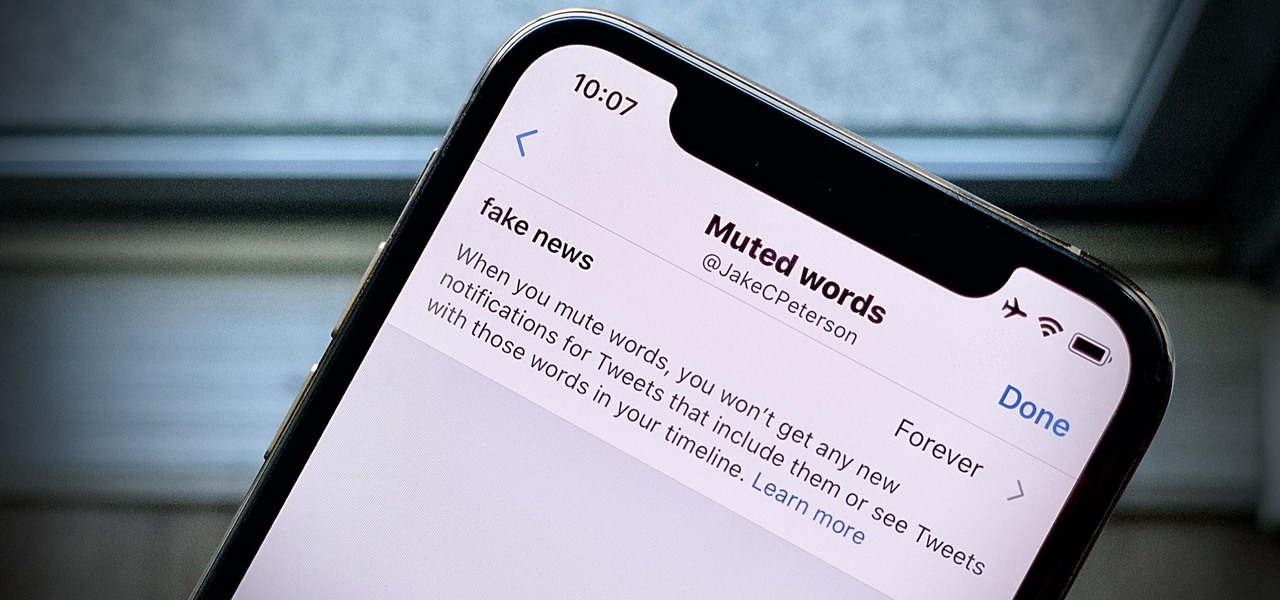
Twitter can be a wonderful place for people to express their emotions and chat with each other in brief. However, it can also be a breeding ground for hateful comments, foul language, and a whole lot of political talk.

Lego has shipped several apps and products that add an augmented reality dimension to their playsets. But it has taken a reality TV show from Fox to allow brick fans to build with virtual bricks in augmented reality.

In his famous 1996 "Content is King" essay, Bill Gates predicted that content is where tech companies will make money on the Internet. The adage clearly holds true in the current phase of augmented reality experience.
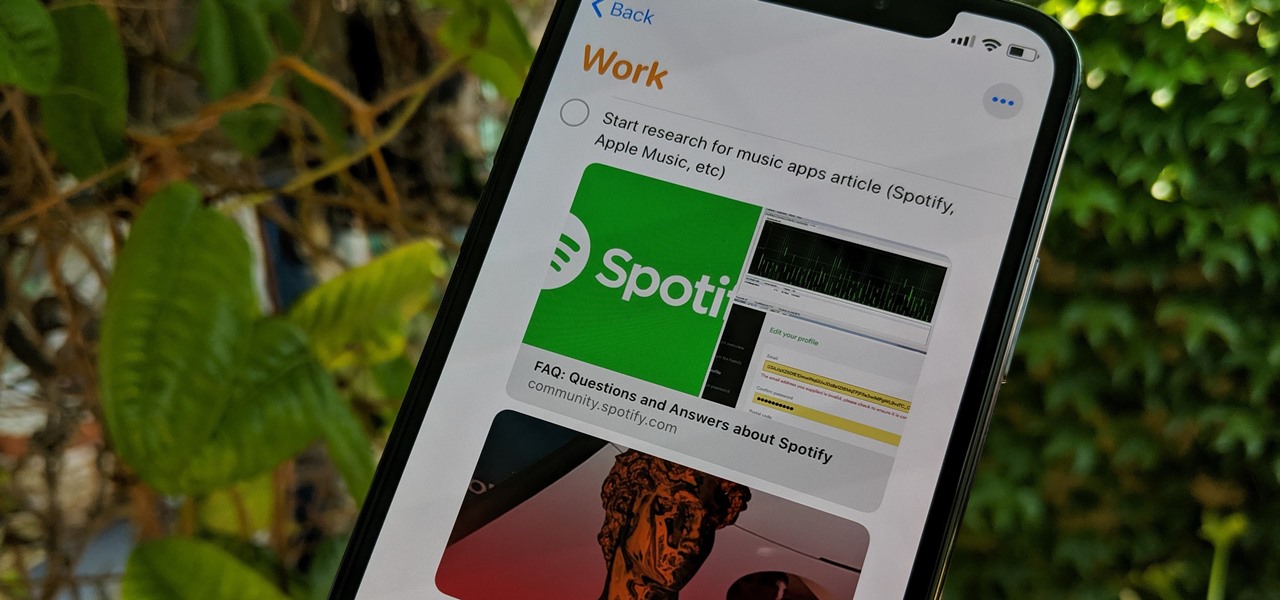
Apple's Reminders app has always been an underrated yet useful productivity tool for iPhone. It's not as powerful as many third-party to-do apps, but it makes it easy to keep track of a few basic tasks, and it's integrated deeply with iOS, macOS, and watchOS. In iOS 13, it's even better since you can now add attachments to your reminders, such as photos, documents, and webpages.
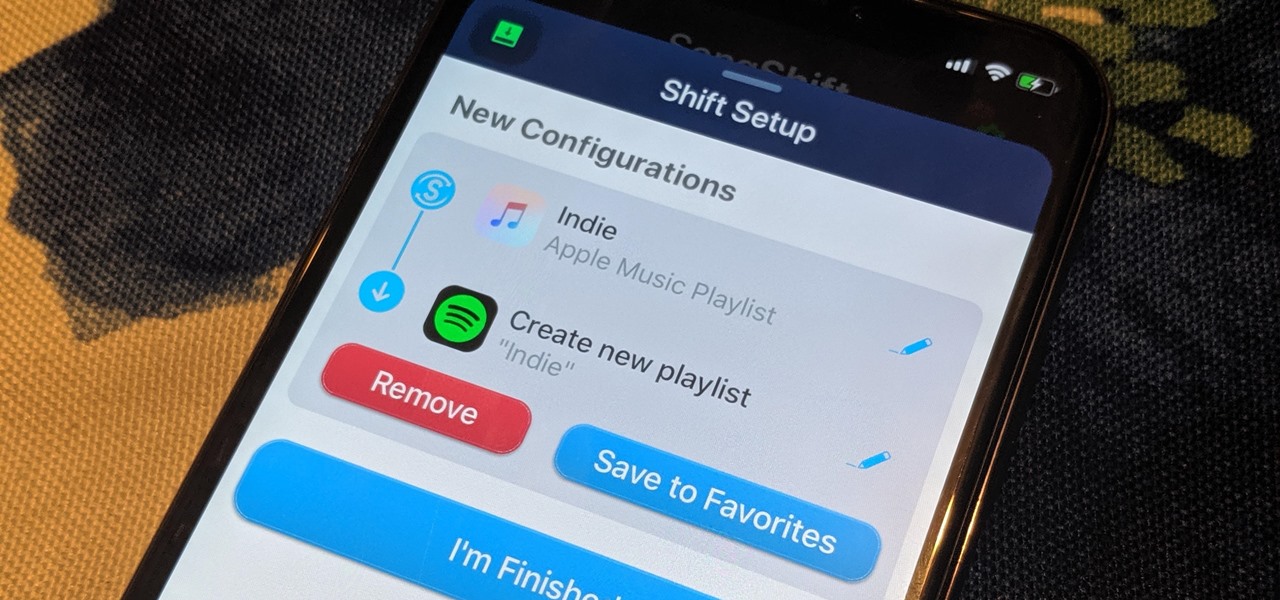
Switching from one popular music streaming service to another shouldn't have to be a hassle, but it is if you want to transfer all your favorite music over. No popular service offers a built-in feature to export or import playlists, so if you want to move your favorite Apple Music playlists over to Spotify, you'll have to use a third-party service.

Fans of the friendly neighborhood Spider-Man have yet another way to experience the web-slinger in augmented reality.

In the Tom Holland era, it appears to be impossible to promote a new Spider-Man movie without an augmented reality experience, a trend that continues with Spider-Man: Far From Home.

Months ago, we showed you some of the powers of Spatial, the HoloLens app that allows groups of workers to collaborate in augmented reality using 3D avatars.
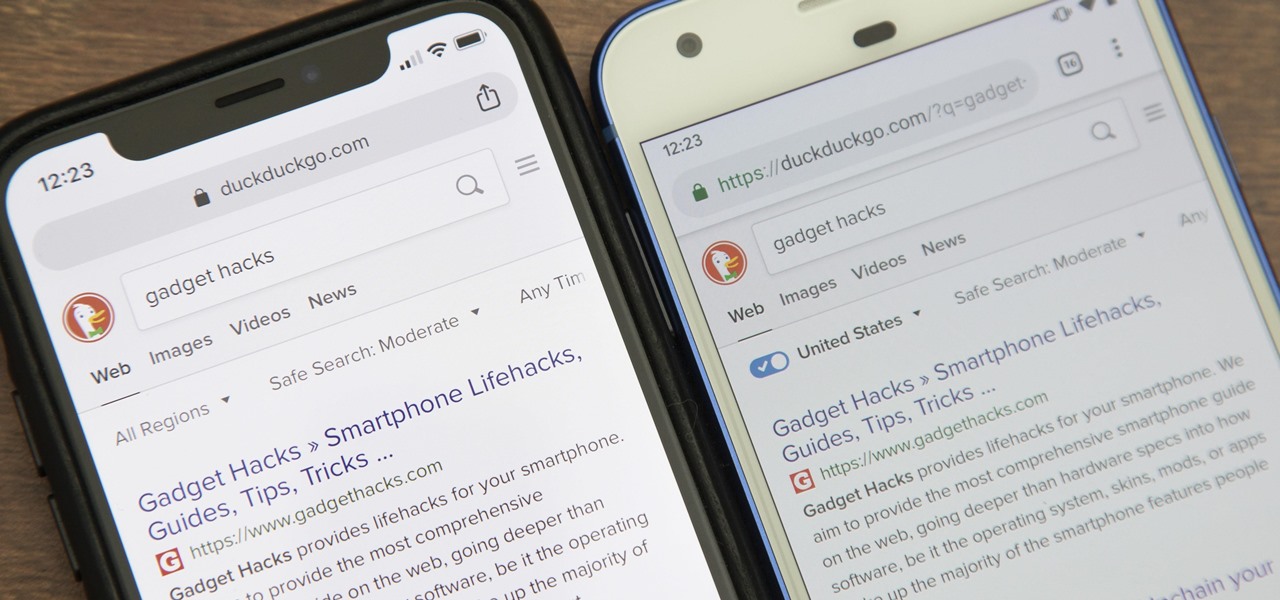
While Google would rather you use Google as the default search engine in Chrome, there's a way to switch to the more privacy-geared DuckDuckGo search engine for all your web browsing needs. With DuckDuckGo, the company does not track anything you search or allow anyone else to track it, so you can effectively search from your iPhone or Android phone anonymously.

It's easy to forget just how cool face filters are. Augmented reality has come a long way, and apps like Instagram now offer a suite of impressive effects to play with, but some of the best ones aren't easily found. There is a treasure trove of exclusive, custom face filters that are unavailable to the general public, but not at all inaccessible — you just need to know the trick to getting them.

It's common for IoT devices like Wi-Fi security cameras to host a website for controlling or configuring the camera that uses HTTP instead of the more secure HTTPS. This means anyone with the network password can see traffic to and from the camera, allowing a hacker to intercept security camera footage if anyone is watching the camera's HTTP viewing page.

UPDATE: The ported APK covered below is now obsolete because Fortnite beta is officially available for all Android devices!

There are a number of options and hidden menus within Android that provide users more control over their device. With this control, you can better manage how your phone operates. We came up with a list of tips and shortcuts that, when used, will slowly put you on a path to becoming an Android power user.

One of the best gifts that someone with an iPhone can receive is a paid app, hot new movie, bestselling album, gift card, or anything else in iTunes, Books, or the App Store that costs money. Even if it's a small $0.99 game that you heard a friend talking about, a gesture like this can go a long way. Gifting apps and media is now easier than ever, even if you don't have an iOS device yourself.

Shodan calls itself "the search engine for internet-connected devices." With so many devices connected to the internet featuring varying levels of security, the special capabilities of this search engine mean it can provide a list of devices to test and attack. In this tutorial, we'll use Python to target specific software vulnerabilities and extract vulnerable target IP addresses from Shodan.

Networking is built largely on trust. Most devices do not verify that another device is what it identifies itself to be, so long as it functions as expected. In the case of a man-in-the-middle attack, we can abuse this trust by impersonating a wireless access point, allowing us to intercept and modify network data. This can be dangerous for private data, but also be fun for pranking your friends.

Dutch filmmaker Anthony Van der Meer published his 2015 thesis short from Willem de Kooning Academy in South Holland online in December 2016. It's a brilliant piece of work that managed to be touching, alarming, and informative at the same time. His documentary, which already has over 6 million views on YouTube, covered the journey made by a stolen smartphone and how the theft and ensuing tracking affected all parties involved.

Backdoors are convenient to leave behind once you've already found a way into a server, and they can come in handy for a variety of reasons. They're good for developers who want a quick way into machines they're working on, or for systems administrators who want similar access. Of course, backdoors are also a hacker's best friend, and can be added in a variety of ways. One good tool for doing this is Weevely, which uses a snippet of PHP code.

Virtual reality holds the promise of electronically visiting distant places we'd otherwise struggle to reach, but that teleportation-esque ability isn't possible without the right content. YouVisit created a platform that makes it easy for almost anyone to create immersive 360-degree experiences so we can map our lives and see the world through the eyes of our fellow humans.

Hello NullByte, it's mkilic! This time I'm here with the C.H.I.P from NTC. Although it is not too popular, the C.H.I.P is a brand new micro computer. It is very similar to the Raspberry Pi or Beaglebone Black. The key difference with this particular board is its cost and size. The C.H.I.P only costs $9 and measures 2.5 x 1.5 inches. In addition to this, the C.H.I.P has built in 802.11 b/g/n Wifi and Bluetooth 4.0. Considering these great specs, what could a Hacker use this for? Step 1: The In...

Getting cool new features before everyone else is just plain fun. To be on the bleeding edge can require a lot of effort at times, since the fastest way to get an update is to find it as soon as it leaks, then get to work on sideloading the new version. Luckily, there's an easier way to get the latest features on your favorite apps, with WhatsApp being no exception.

Hello partners, first of all I would like to thank all those who have sent me positive feedback about my posts, to say that I'm always willing to learn and teach. I'm also open to answer the appropriate questions.

As one of the most powerful Android apps for connecting your phone or tablet to your other devices in various ways, Pushbullet had always been a fan—and Gadget Hacks—favorite.

Like the majestic mountain structure it's named after, Apple's latest version of OS X, El Capitan, goes a little deeper to expand on the foundation laid by Yosemite. While the update may not be as monumental as some have hoped, it is an improvement and includes tons of useful new features you don't want to miss.

If you are anything like me, you have a knack for taking silly selfies of yourself, i.e., taking scotch tape and wrapping it around your face to make yourself look like the blob, or perhaps you like taking selfies of yourself in weird or unusual situations doing weird and unusual things.