This video shows how to get more value on your GoDaddy account. You have to have a deluxe account to share domains. You have to pay an extra $2 a month to get this account. Once you sign in go to "hosting" then my "hosting account". To add another domain you move it over to a new folder then put the site files in there. To do this, click add domain then go to bulk. Then create a folder and name it what you desire. Sometimes the file folder doesn't always appear immediately, but it is there, i...

In this Photoshop tutorial video from Tasktutorial, the host leads you through the process of creating a speech bubble in Photoshop. As you watch this video and follow along with the host, you will learn how to create a speech bubble, like they use in the comics. You will also learn how to add color and blur effects to it, to give it a more three dimensional feel, as well as how to use the stroke effect to give it that comic book outline when you're done.
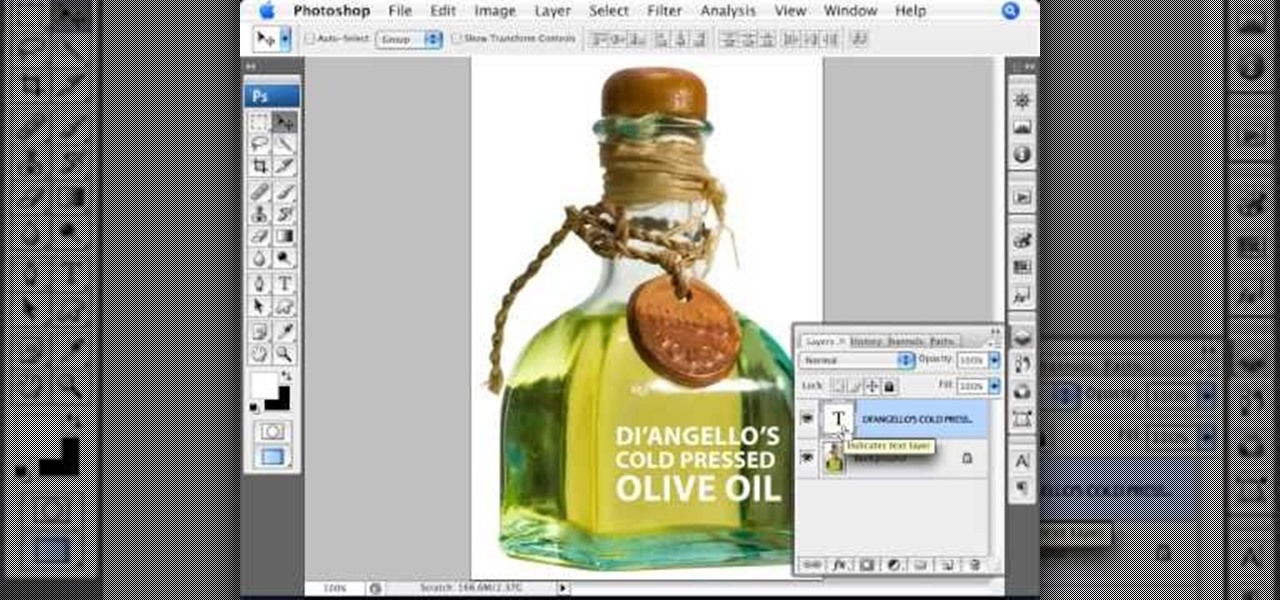
In this Photoshop video tutorial, hosted by photoshopuniverse, from Free Photoshop Video Tutorials, you will learn how to create an effect that makes it appear as though text you input into your image has been embossed on a glass surface. As you follow along with the host in this video, you will learn how to insert text, and align it to a plane, so that it will appear to be aligned to the surface you want to place the text on, as well as how to achieve the embossed look when you're finished.
Here's a fast lesson in hosting video on your own Drupal website using the FileField and jQuery Media modules. The Filefield and jQuery Media modules are a one-two knock out combination for allowing users to upload media files to fields in your custom content types and then playing back the media files in their matching player or handler. It represents a positive direction for treating fields containing files and is a great starting point for researching your own implementation of this recipe.
Are you willing to do whatever it takes to gain host privileges in COD: Black Ops Annihilation Shangri-La Zombies? If you answered yes to that question, this is the video for you. Watch and learn how to use a lag switch to become host.

Google is one of the most powerful forces on the Internet, and their technology can be the key to helping you find success in whatever your online endeavor might be, from web design to filmmaking. This video is a part of their Google Webmaster Series, offering help to webmasters the world over on how to best utilize Google in their work. This video will show you how to optimize your deep web content, like databases and forms, to be crawled by Google using a few simple tricks.

The browser on your Android-powered cell phone offers numerous features that enhance your overall web experience. Some of the great features include double-tapping to zoom in, searching for text on webpages, sharing websites with friends, and copying and pasting. There's a lot more, so watch this video tip from Google to see how to fully enjoy your web browser.

Create a text box for the web using Adobe Photoshop! Whether you're new to Adobe's popular image editing software or simply looking to pick up a few new tips and tricks, you're sure to benefit from this free video tutorial from TutVids. For more information, including step-by-step instructions on how to create and slice up your own custom text boxes in Photoshop from scratch, watch this web designer's guide.

Right out of the box, iPhone is incredibly easy to use. If you want to get the most out of every feature, you’ve come to the right place. This video tutorial straight from Apple will teach you how to browse the web with Safari on the Apple iPhone 3G. The iPhone redefines what a mobile phone can do.

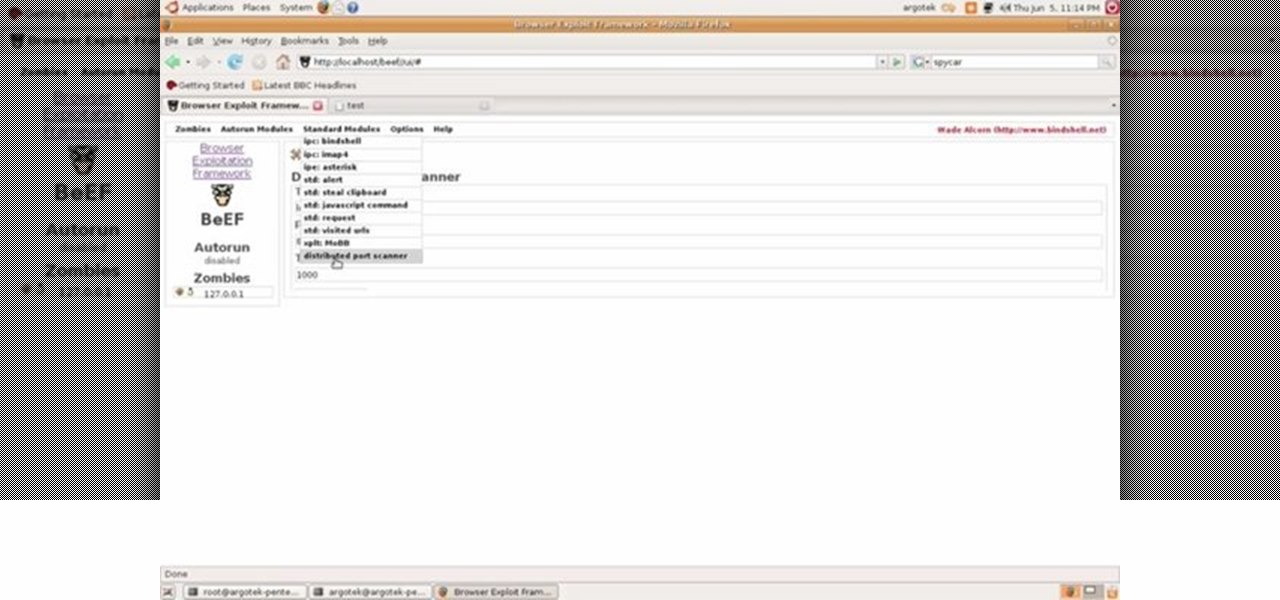
This video tutorial talks about browser exploitation. Particularly, it talks about tools, like BeEF, that can be used to hack known vulnerabilities within browsers and some cool frameworks that you can use to check the security of your own browser. To get started hacking your own browser, watch this how-to.

This tutorial covers the ABC's of getting started in Web Development. Mike Lively shows you how to get a server, a free HTML editor, and free FTP Software.

This video provides an introduction to building 15mm scale buildings for Warhammer or miniature dioramas. Simulate roofing shingles and with small pieces of cardboard. Create a haunted scene with real spider webs. Preserve tiny spider webs with a protective spray or make miniature spider webs out of milkweed. Build small scale grapevines with toothpicks, wire, and painted leggy moss.

The spider web stitch and the ribbed spider web stitch are both "woven" embroidery stitches, either used as isolated accents or used in clusters. They aren't a line stitch or a filling stitch, and they aren't really a "small" detached stitch that can speckle a background lightly, either. Watch this video from Needle 'n Thread to see how it's done.

Augmented reality already seemed like the ideal technology to advertise for a movie based on the premise of being sucked into a video game world the first time around. For the sequel, how about two times the immersion?

Nmap is more powerful than you know. With a few scripts, we can extend its functionality beyond a simple port scanner and start to identify details about target servers sysadmins don't want us to know.

Hackers rely on good data to be able to pull off an attack, and reconnaissance is the stage of the hack in which they must learn as much as they can to devise a plan of action. Technical details are a critical component of this picture, and with OSINT tools like Maltego, a single domain name is everything you need to fingerprint the tech details of an organization from IP address to AS number.

Hello everyone! I hope you are having a great day so far. Today, instead of caring about networks we are going to talk about subnetting based on host requirements as promised in my first article about subnetting. Just like in the previous articles we will jump right into the examples because that's the best way to learn.

Welcome back, my tenderfoot hackers! In continuing my series on digital forensics using Kali, I want to introduce you to two complementary tools, both built right into Kali Linux. These are Brian Carrier's tools Autopsy and Sleuth Kit.

With a few hosting tips, you will perfect your Thanksgiving season! This craft shows you how to make some elegant place cards, some easy and beautiful napkin rings, and custom-made deocrative candles. Be the perfect host or hostess this Thanksgiving season!

This clip presents a number of tips on hosting an open house at your Pilates club or studio. Whether you're considering the possibility of starting your own Pilates studio or already have one and just need a little help tackling a particular pedagogical problem, you're sure to be well served by this free video lesson from the folks at Balanced Body Pilates. For more information, including a comprehensive overview, watch this video guide.

There are several types of barrier breaker glitches in Gears of War 2. The one described in this video might be the easiest one of all. It will allow you to escape from many multiplayer maps. The only caveat is that this won't work if you are hosting the game. Simple, get one of your friends to host and glitch on!

Get ready to dance "The Ellen!" In this tutorial, you will learn all of the steps to the dance that is sweeping the..morning talk show circuit.. The Ellen! This video, hosted by Forest Thomer, will show you step by step how to follow along to this dance and bop around with TV's favorite host.

Cityslipper shows you how he uses the cleft grafting method to make a less appealing green apple tree produce better tasting red apples. 10-12 inches long scion wood is collected from the good apple tree while it is dormant. Care is taken not to let the twigs dry out. Selected scions should not have spurs rather they should have leaf buds that lay flat against the twig. A good host twig on a healthy-looking branch should be selected. A clean cut should be made with the fine teeth of a grafing...

AMICLUBWEAR created a tutorial on how to host a tea party based on "Alice in Wonderland". The video begins with a step by step instructional on how to make tissue paper "flowers" as decorations for your tea party. The tissue papers are layered in opposite colors, after which the tissue paper is accordion folded and tied together using a pipe cleaner. Afterwards, the tissue paper is carefully extended layer bay layer and shaped into a flower. Next, there was a tutorial for making the "EAT ME" ...

Everyone loves a party—until the host’s pooch starts giving your leg a little bit of his doggie style. Show that canine he’s not humping any old bitch.

If you have your own domain, odds are you do things from FTP from time to time. In this tutorial, you'll learn a technique for making FTP shortcuts with the Windows HOSTS file, which will allow you to simplify the process. The time you save will be your own.

How to solve some of SC's common hosting problem, this clip is using LINKSYS but it can work with all routers in about the same way.

Ever wonder who's host in Halo 3? Well now there is a way to find out with this Halo tricks video.

DNS spoofing - how to use the hosts file in Windows XP to block unwanted spyware/popups/etc, block programs from reporting to a site, filter/block/redirect websites, and locally create forward lookups (IP to name resolution in network)

In this three-part tutorial, learn how to create a web page layout in Dreamweaver CS4 with DIVs. In Dreamweaver CS4, this Dreamweaver expert uses DIV containers with margins and floats to create web page layouts. A demonstration of a basic CSS reset rule is also included.

You should encrypt everything. These are what you need: BackTrack 4,0, modify IP tables, Python and ARPspoofing. Program the PC to flip to forwarding mode. Adjust the programming in the IP tables. You are convincing the host and the client that the man (PC) in the middle is the host and capture passwords, user names and other information from unsuspecting clients. This program strips the "S" from "https" which make your computer vulnerable to hackers. You need to observe the address bar and m...

The fine folks at ITS Tactical made this detailed tutorial on how to make a two-piece lock pick set out of only a few paper clips and using only a multi-tool in the construction. The host begins by demonstrating how to construct the pick, then how to use it on a real lock. It is not as easy as using a real lock pick, but will still work. As the host emphasizes at the beginning of the video, these picks are only to be used in emergency situations, and NOT to break into other people's homes wil...

To make quick and easy cornbread in a truck, the host only needs jiffy corn muffin mix, egg beaters instead of whole eggs, and a little bit of milk. The ingredients are combined in a bowl, then poured into a disposable baking tin. A Crockpot is used in place of a traditional oven for baking by removing the glass interior. Place the tin with the mix directly inside, and cover until baked fully. The host usually uses a small tin that will fit easily inside the Crockpot, but if only a larger one...

No website will be inaccessible and no web filter will deny you content once you learn the skills presented in this internet hacking video.

There's a million web games spread throughout the internet now, and if you like to play them, you probably want to play them all the time. And if you play one flash game, you probably play another, maybe 10 or 20. But what if you don't have an internet connection one day? What if you can't play those web games anymore? Well, you can, and all you have to do is download them to your computer. Watch to see how to download and play web-based flash games on your computer without web access.

Remember concerts? Those were fun. While gathering in large groups to listen to live music might not be allowed at the moment, the live music part still is. Thanks to the internet, more and more musicians are taking the stage each day to perform for those of us stuck in social isolation due to the new coronavirus. The best part? Many of these concerts are 100% free.

Web applications are a prime target for hackers, but sometimes it's not just the web apps themselves that are vulnerable. Web management interfaces should be scrutinized just as hard as the apps they manage, especially when they contain some sort of upload functionality. By exploiting a vulnerability in Apache Tomcat, a hacker can upload a backdoor and get a shell.

NOTICE: Ciuffy will be answering questions related to my articles on my behalf as I am very busy. Hope You Have Fun !!!

Welcome back, my hacker apprentices! In recent weeks, the revelation that the NSA has been spying on all of us has many people up in arms. I guess I take it all in stride as I just assume that the NSA is spying on all of us—all of the time. Don't get me wrong, I don't condone it, but I know the NSA.