A new profile on Apple's exiting design chief Jony Ive, the man behind many of the company's most successful products, paints a fuller picture of what led to his departure.
Canary tokens are customizable tracking links useful for learning about who is clicking on a link and where it's being shared. Thanks to the way many apps fetch a URL preview for links shared in private chats, canary tokens can even phone home when someone checks a private chat without clicking the link. Canary tokens come in several useful types and can be used even through URL shorteners.

One of the ultimate goals in hacking is the ability to obtain shells in order to run system commands and own a target or network. SQL injection is typically only associated with databases and their data, but it can actually be used as a vector to gain a command shell. As a lesson, we'll be exploiting a simple SQL injection flaw to execute commands and ultimately get a reverse shell on the server.

One the leading game developers for the PlayStation 4 and Oculus Rift platforms, Insomniac Games, is finally releasing its first major augmented reality title: Seedling for the Magic Leap One.

When computers have vision but people don't, why not have the former help the latter? That's the gist behind the Cognitive Augmented Reality Assistant (CARA), a new HoloLens app developed by the California Institute of Technology.

It's always a good idea to know how an attack works at the very basic level. Manual techniques for exploitation often find holes that even the most sophisticated tool cannot. Sometimes, though, using one of these tools can make things so much easier, especially if one has a solid foundation of how it works. One such tool can help us perform a cross-site request forgery with minimal difficulty.

If there's one strength of Apple's that iOS and Android fans can agree on, it's the company's dedication to user privacy. With each new iteration of iOS, Apple builds upon these foundations, enhancing and increasing each iPhone's ability to protect its user's data. In iOS 12, Apple has added many new features to Safari, most of which have their own unique way of keeping you safe online.

One of the most critical bugs to come out in the last five years was Shellshock, a vulnerability which allows attackers to execute arbitrary code via the Unix Bash shell remotely. This vulnerability has been around for a while now, but due to the ubiquity of Unix machines connected to the web, Shellshock is still a very real threat, especially for unpatched systems.

Augmented reality is really picking up steam as a tool for marketing departments to pitch their products.

It's no secret that Android has a messaging problem. iPhone users can turn to iMessage as a one-stop shop for all their messaging needs — features like read receipts and the ability to text from a computer have been standard with Apple products for quite some time. Android has no such solution, but Google's looking to fix that with a huge update to the Android Messages app.

Bookmarks and favorites are handy options for saving interesting websites you come across while surfing the web on Android but are far from ideal when it comes to instant access. Thankfully, Google Chrome gives you the added ability to save webpages and progressive web apps directly to your home screen for added convenience.

Passwords stored in web browsers like Google Chrome and Mozilla Firefox are a gold mine for hackers. An attacker with backdoor access to a compromised computer can easily dump and decrypt data stored in web browsers. So, you'll want to think twice before hitting "Save" next time you enter a new password.

A funny thing happened on the way to the release of the virtual reality epic Ready Player One — augmented reality grabbed a major piece of the spotlight. Specifically, Microsoft's HoloLens.

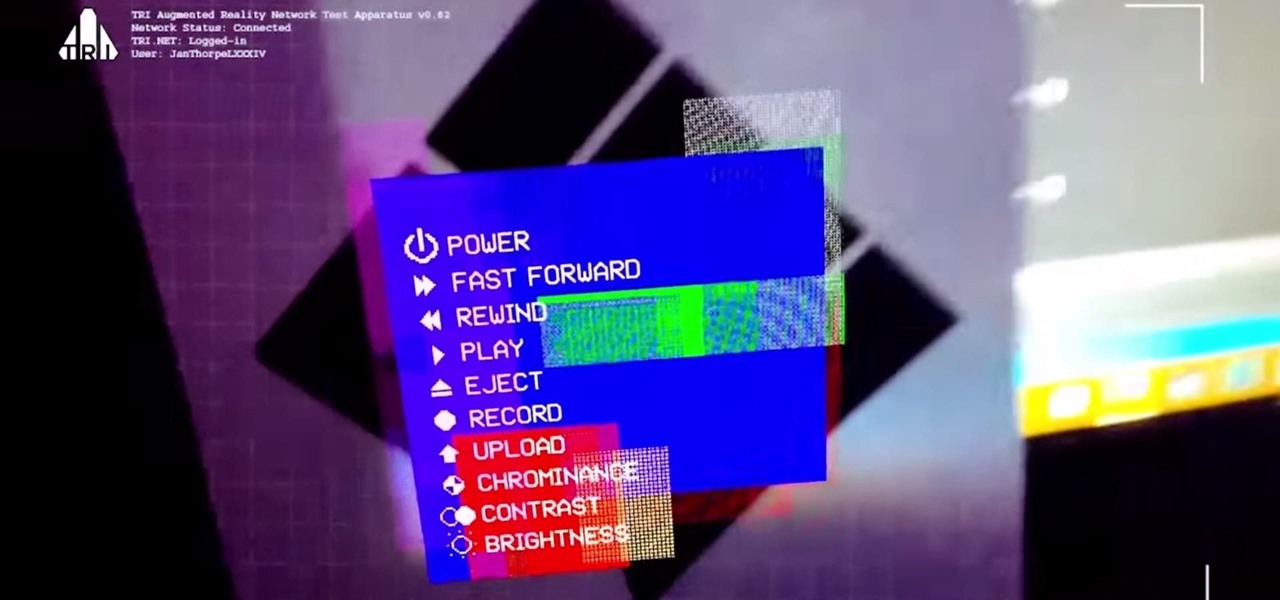
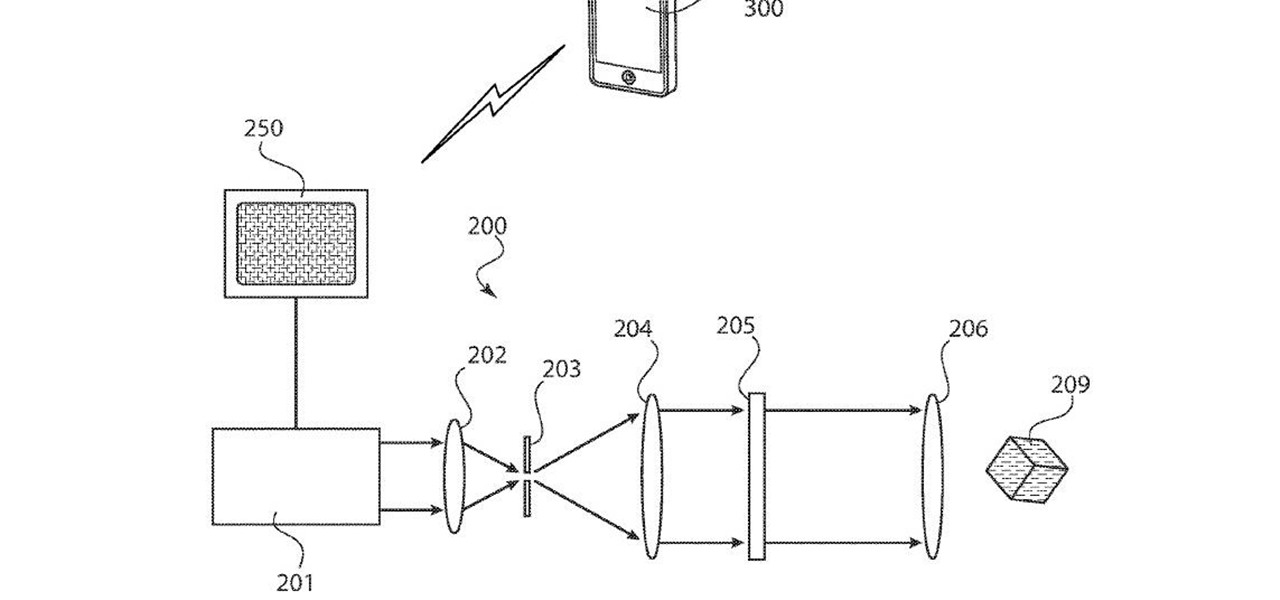
Noted poet T.S. Elliot once wrote that "April is the cruelest month." But Magic Leap might argue that March is the most miserable, as the Ides of March brought more legal woes to augmented reality startup. Elsewhere, its closely-held branding secrets have been spilled by way of the US Patent and Trademark Office (USPTO).

It would be difficult to discuss the business of augmented reality without acknowledging the annual tech meat market of CES.

Google, Facebook, and Huawei have made an investment in nurturing the future of augmented and virtual reality through $6 million in contributions to the opening of a new center at the University of Washington.

If CES 2018 is the starting gate for this year's race to release smartglasses, then Vuzix is already racing down the augmented reality track with its Blade smartglasses.

It took a few months, but several major phones are finally receiving updates to Android Oreo. At this point, we've spent significant time talking about Oreo on the Galaxy S8, Galaxy Note 8, and Essential Phone. While an update to the latest OS is always great, there is one big Android 8.0 feature that isn't coming to every phone.

The Watch Dogs video game series came out in 2014, enamoring audiences with the idea of a seemingly magical smartphone that could change traffic signals, hack web cameras, and even remotely control forklifts. This may sound like science fiction, but The Sonic uses a customized flavor of Kali Linux to allow you to unleash the power of Kali from any smartphone — all without the need to create a hotspot to control it.

A partnership between augmented reality company Zappar and IoT services provider EVRYTHNG will bring AR experiences to consumers while supplying market data to brands.

Anyone who knows me well is aware that I am a cyberpunk junkie. The conflict between lowlifes, corporations, and the government, flavored with dystopian future, high technology, transhumanism, artificial intelligence, and noir storytelling, just does something for me.

The launch of the latest line of iPhones came and went without major revelations for advanced AR hardware other than the next iteration of processors and cameras.

CEO (and NR50 member) Tim Cook and Apple unveiled the long-awaited lineup of next-generation iPhones today on stage of the Steve Jobs Theater, packed with hardware improvements to facilitate AR experiences from ARKit, which will arrive with the iOS 11 on Sept. 19.

When Disney teased an augmented reality game called Star Wars: Jedi Challenges running on a headset from Lenovo, fans had more questions than Disney had answers. When? How much? Can I be a real Jedi?

This morning Google announced ARCore, an SDK for Android devices that will allow augmented reality developers to add new functionality to Android 7.0 and up, all without any special hardware other than the camera of a phone.

More prescriptions for antibiotics are written for ear infections than any other type of infection. A new study comparing the incidence and causes of ear infections in children between the ages of six months and three years found that the incidence of ear infections over the last decade has dropped significantly since the 1980s.

Gonorrhea infections reached a peak in 1975, then decreased until 2009, when infection rate started rising and has increased each year since. With the rise of antibiotic resistance, those numbers are only going to get worse — unless we find new treatments against the bacteria.

A new study shows the Zika virus is present in saliva — but it may not be enough to make you sick. The Centers for Disease Control and Prevention notes there is "no evidence that Zika can be transmitted through saliva during deep kissing." Given the results of research published in the journal, Nature Communications," the agency may need to revise its guidance.

The number of households in the US that go hungry because they lack money for food hit a high of almost 15% in 2011. While that number continues to decline, nearly 13% of American households still go hungry.

All eyes will be on Tesla CEO and founder Elon Musk tonight to see if he is reveals details about the status of Tesla's challenged Autopilot at tonight's official Model 3 launch party.

If you are an NYC commuter like me, then I'm sure you know how bad the city's transportation has gotten.

Results of an early-stage clinical trial of an HIV vaccine could mean a hoped-for breakthrough in the battle against AIDS.

A recent case of Powassan virus has been reported in Saratoga County and may have been the cause of the infected patient's death. It's the 24th case in New York State since 2000, and will be reported to the CDC tomorrow, the NY Department of Health told Invisiverse. The tick-borne illness has no vaccine or specific treatments and can damage the nervous system.

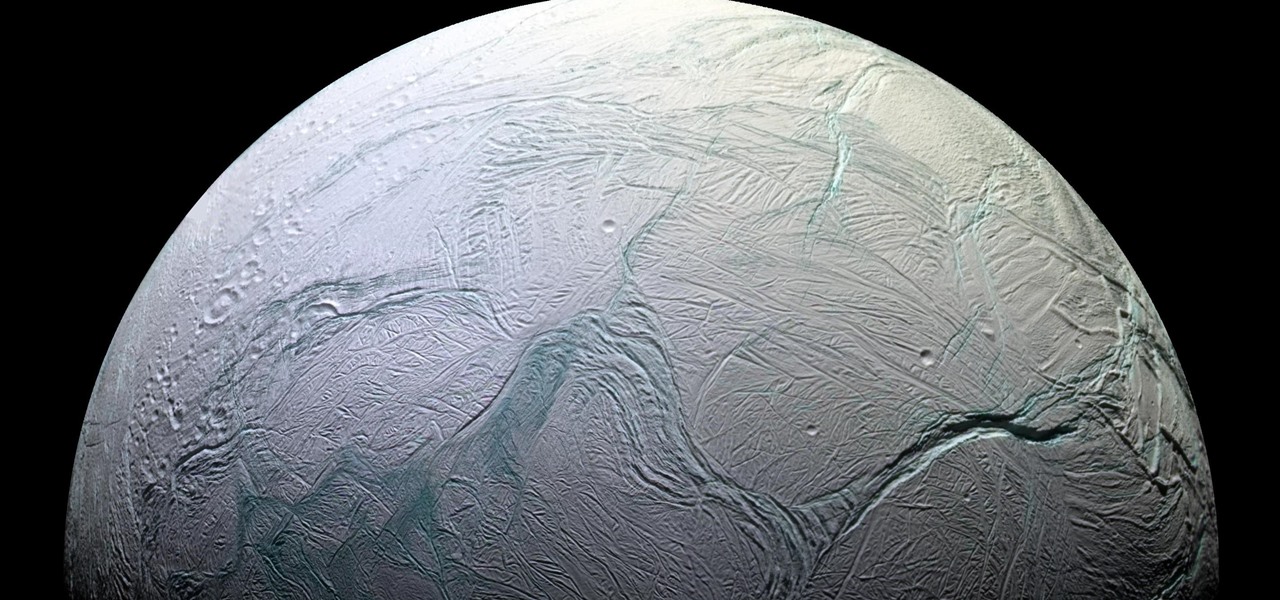
Earlier this year, NASA reported on findings that might point to water, and microbial life, on moons orbiting Jupiter and Saturn. Named Europa and Enceladus, those moons contain large oceans under their icy surfaces, which many speculate could hold microbial life.

One inventor wants to bring augmented reality to internet radio and home audio speakers. Meanwhile, a leading consumer electronics company has opened up access its deep learning tools for building augmented reality apps. In addition, analysts examine how augmented reality will impact the design and construction and profile the top developers in augmented and virtual reality.

New research reveals how E. coli bacteria construct elaborate and effective tunnels to pump unwanted molecules like antibiotics and other toxins out of cells. The discovery could help us better understand how antibiotic resistance occurs and give us a leg-up to beat them at their own game.

Uber's struggles are expected help Lyft get ahead in driverless development as it confirms its third partnership with autonomous tech company nuTonomy today.

Instagram Direct is fast becoming the end-all-be-all messaging app, and it just added some incredibly convenient features that should make it a bit more practical. These new additions have a clear purpose: To help Instagram Direct grow its base and take on more feature-rich messengers like Snapchat or WhatsApp.

From Farmville to selling a company to Google, Amitt Mahajan has been through the startup ringer. Now, as managing partner with Presence Capital, he's funding the future of augmented and mixed reality.

Things aren't looking good for Uber after its driverless experiment in Pittsburgh soured relations with local authorities. Surprised? Me neither.