When you look up the word free in the dictionary, you'll find a lot of definitions, but in the days of digital dependency and a falling economy, free only means one thing—expensive stuff for nothing. And if you own a Windows computer, one of the best sites to get free software from is Giveaway of the Day.

Have you ever heard symmetrical is sexier? Yep, according to scientists, symmetry is inherently more attractive to the Homo Sapien eye. Back in the days of Helen of Troy, Phidias, Plato and other great philosophers all observed the golden ratio, "a sum where the quantities to the larger quantity is equal to the ratio of the larger quantity to the smaller one". Confusing? Let's apply it to the human face only: the features of the human head were measured in calculated, precise proportions to d...

If you tried visiting the Apple Store online this morning, you were probably prompted with the same notice as the one below, which lasted a good portion of the a.m. What could Apple have been doing to shut down their online store for so long?

Body hacks. So simple, so ingenious. They're the shortcuts in life. We love them, the internet loves them. Back in 2008, somebody named Alicia Goh wrote a friendster blog post that has been passed along far and wide. Her tricks of the body include quick solutions for an itchy throat, a stuffy nose, a dire need to pee, and more. My favorites:

I'm not going to lie. I was Catholic. But one of my reasons for my faithful departure was having to tell my innermost secrets— my sins— to a silhouetted figure behind a latticed screen. With the creepy enclosed booth structure and separation of sinner and confessor, its anonymity was clear, yet deceiving. You always knew the priest and he always knew you. If I wanted total privacy, was there really a need for this intermediary to God?

Any time a feature is introduced in an MTG set and not replicated in subsequent sets, balancing issues are surely forthcoming. You wind up with one set that can do things the others can't, forcing players to counter that set with other cards from it, and generally limiting the creativity with which one can effectively play the game. Playing these types of cards is like playing trap defense in hockey or boxing like Floyd Mayweather: you might win, but neither you, your opponents, nor the peopl...

We have no control on the weather yet it is a part of our lives which influence what we do, what we eat, what we wear and many times where we live. How did people predict the weather before there was the Internet, television, radio or the weatherperson with all of their gadgets?

Every day of the week, WonderHowTo curators are hard at work, scouring the web for the greatest and most inspiring how-to videos. Every Friday, we'll highlight our favorite finds.

Alice Waters and The Green Kitchen So what, yes I admit it I am drawn to all things Alice Waters. So sautee me. A new discovery was made today while walking through my local bookstore. I found a sweet looking cookbook with Alice on the cover. Naturally I stopped. The item of my interest was a sort of "how to" cookbook called In The Green Kitchen

You may have already heard of Zazzle, an online service that allows you to print on a variety of goods (tees, mugs, posters, etc.). You can design-it-yourself, or choose from Zazzle's library of available designs.

JUAREZ. PH33R. SUX0R. If you know what these mean, then you probably spend way too much time on the internet. If you're as bewildered as I was, these words actually mean something in leetspeak.

Word of mouth is that Zynga is preparing to harvest the world. Is this a horror movie? No, but FarmVille has already invaded millions of homes, and now it wishes to conquer our pockets. They're gearing up for a mobile platform, one that will reach millions more via the iPhone, iPod Touch, iPad, and Android.

How much do the producers of Lonely Girl make? How much do the producers of American Idol make? How much does COPS cost to make? I decided to share what I have learned for the CES audience in Vegas.

Introduction In the competitive world of today's video game scene, PC gamers are known to squeeze out the best possible visuals in their games. Every few months a new video card rolls out, and RAM is ever increasing; constant upgrading is the norm of staying ahead the curve. One of the most important things a PC gamer looks at is how many FPS (frames per second) he gets. It defines his gaming experience.

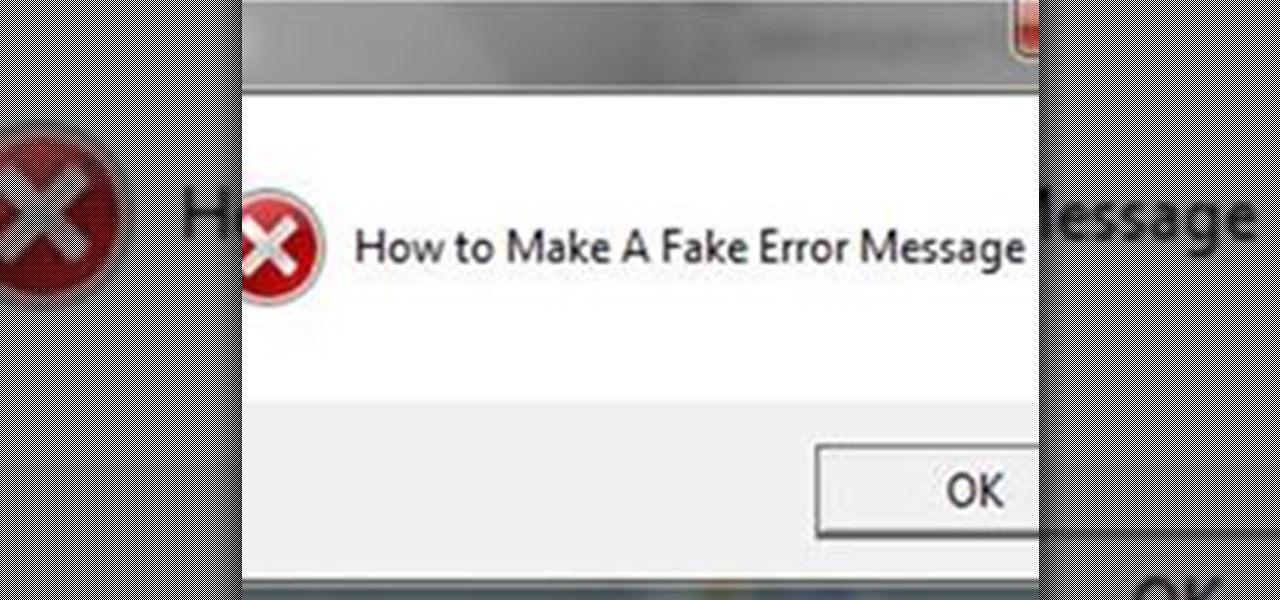
This article will show how to make a simple, fake computer error message. These message boxes are 100% harmless, and make for funny pranks. They will display any text you want them to.

In this video tutorial, viewers learn how to change the URL of their MySpace profile. Begin by opening your web browser and go to the MySpace website. Then sign into your account. Now click on Mail and select Inbox. In the sidebar, click on Settings. Now users are able to change their profile URL and email address. When finished, click on "Create my Email!" and click on Confirm when the confirmation window appears. This video will benefit those viewers who use MySpace, and would like to learn...

Slow-loading pages could easily turn off your website visitors. Therefore, if you have a large image on your web page you might want to slice it into different parts to help the page load faster. In this Photoshop CS2 video tutorial you will learn how to use the Slice tool to do that. Make sure to hit "play tutorial" in the top left corner of the video to start the video. There is no sound, so you'll need to watch the pop-up directions. Use the Slice tool in Photoshop CS2.

In this Illustrator CS2 video tutorial you will learn to slice and export an Illustrator file for the web. You'll see it's the same procedure in Photoshop. Remember to select PNG or GIF file formats if you want to reserve transparency layers when exporting images. Make sure to hit "play tutorial" in the top left corner of the video to start the video. There is no sound, so you'll need to watch the pop-up directions. Slice and export an Illustrator file in Illustrator.

Business owners and marketeers are diverting from traditional marketing techniques, including billboards, radio and TV advertising, brochures, and any other outdoor promotions, to cheaper but effective Internet marketing strategies. Under the new arrangement, business owners reach out to the final consumers through advertising on the World Wide Web.

Advances in technology continue to make our lives easier and more convenient. If you want to send fax, for instance, you no longer need to own a fax machine. You can easily and quickly send fax directly from your computer in one of several methods, including via an Internet fax service provider or using Windows built-in Fax and Scan tools. Read on how to use an Internet fax service, one of the faster faxing methods, to send fax messages from your PC.

Poetry to me is an expression of the sudden noteworthy inner thought, that arrives unexpectedly in an ephemeral, fleeting form. When you are attracted to the idea of creating some verses, do not sit there with the pen in your hand trying to force yourself to create poetry. If anything, you will produce something boring, you will pull words by the ear, and use too many of them absolutely unnecessarily. It is because you do not have direction, and if you think you do, than it is something too t...

After years of being a PC technician and Windows System administrator, I had the blind hatred for Apple that I thought I was suppose to have. I swore that I'd never even touch an iPod, let alone buy an Apple product. But I found a new career that drug me out of the Windows server/PC tech room dungeon, and into the bright modern office of a web development firm. Then it happened. After a couple weeks with all this Apple stuff around me, my love for gadgets and (closet) Apple curiosity got the ...

Adobe Fireworks is a bitmap and vector graphics editor aimed at web designers. In this Fireworks 8 video tutorial you will learn how to combine path objects, create a vector path, and join paths from multiple layers. Make sure to hit "play tutorial" in the top left corner of the video to start the video. There is no sound, so you'll need to watch the pop-up directions. Combine path objects in Fireworks 8.

Sometimes a simple change in your web page could make it look more livelier. In this Illustrator video tutorial you will learn to create glossy buttons. Learn how to use the Blend and Gradient tools in this example. Make sure to hit "play tutorial" in the top left corner of the video to start the video. There is no sound, so you'll need to watch the pop-up directions. Create glossy buttons in Illustrator CS2.

If there ever was a time for Null Byte to need people to contribute, it's now. Let's make Null Byte a place where anyone, from novice to master computer user, come and learn. It has been sometime since the last "Call to Arms" for Null Byte, and even longer since the last "Weekend Homework". We all know that this time of year is busy for everyone, but that didn't stop occupytheweb otw from creating a great article in his continuing "Hack Like a Pro" series.

The community here on Null Byte has always been great and helpful in sharing their know-how, even before I took up admin duties in this World. I jumped at the chance of leading Null Byte because I enjoy teaching and informing people on all of the important need-to-know things out there, but more so than that—there is a deeper reason.

Big brother is watching when you're playing around on another system—and big brother is that system. Everything from operating systems to intrusion detection systems to database services are maintaining logs. Sometimes, these are error logs that can show attackers trying various SQL injection vectors over and over. This is especially so if they are using an automated framework like sqlmap that can spam a ton of requests in a short time. More often than not, the access logs are what most amate...

No doubt you've seen some of the hack logs being released. One part that stands out over and over again is the heavy database usage. It used to be early on that virus and hackers would destroy data, usually just for lulz. However, with the explosive commercial growth of the Internet, the real target is turning into data theft. You should learn how this happens so you can protect yourself accordingly. Let's take a look at what makes this possible and dare I say, easy.

If you follow the Anonymous, Occupy, and IT security scenes, you have no doubt heard about a dox release. What is it? How can it hurt you? And most importantly, how can you protect yourself from it? Some of these steps might seem common sense, while others will be an ah-ha! moment. Your private info is both your biggest weakness and your biggest weapon in your battle to remain anonymous. You must learn how to use it as both.

WonderHowTo is made up of niche communities called Worlds. If you've yet to join one (or create your own), get a taste below of what's going on in the community. Check in every Wednesday for a roundup of new activities and projects.

Last week, we had a great contribution from Christopher Voute, who introduced us all on some of the basic moves in Python. Now, who else will share their knowledge and tackle some of the topics below?

In my recent Darknet series, I attempted to connect the dots on the Deep Web. I covered the two largest anonymity networks on the Internet today, Tor and I2P. While my initial four articles were meant as an introduction, I ended up receiving a lot of interesting comments and messages asking the technical differences between the two. I'd like to thank all of you for letting me know what was on your minds, as you should always!

¬¬Just about every business has a website these days but very few businesses know how to effectively use their websites to get more customers. There are two different things that a business owner needs to do to increase their website traffic: optimize their site so that search engines can find them easier and promote their site on the internet so that they have greater visibility. This article will discuss how to optimize a website.

I recently posted a link to what seemed to be a very useful guide on Lifehacker for creating a TOR button in Chrome. However, when I tried it myself, it did not work. Also, it lacked a warning on the limits of Tor, which I think are important. Therefore, I decided to create an updated and more comprehensive tutorial.

Accounting and Finance Degree

When it comes to webcams these days, most people are using their laptops over desktops. The cameras are centered, integrated, and require no configuring. They're a cinch and usually have great resolution. So, then what do we do with all of those old wired desktop webcams that we've accrued over the years? Even if you still use an external USB one, chances are you're not using it daily, so why not come up with a better use for it?

Three Days without You Poem Description: