How To: Clear Your History, Cookies, Passwords, and Cache
With this useful video, you will learn some tips and tricks about how to delete your web browser history, passwords, cookies, also cache form data and temporary internet files.


With this useful video, you will learn some tips and tricks about how to delete your web browser history, passwords, cookies, also cache form data and temporary internet files.

If you're working in the page layout mode of Pages '08 then you are probably going to want to work with the text layout and control the text flow. This tutorial shows you the basics of how to do it.

It's pretty standard when creating a document that requires some basic page layout formatting, that you're going to want to wrap or flow text around images. In this Apple tutorial, you'll see how easy it is to accomplish in Pages '08.

In this video we'll see how to create one business card on the page and then using the Transform Effects we'll replicate the card multiple times up. This is a really slick way to make something once and have it repeated on the page as often as you like. The beauty of it is that you can still make changes to the original and have those changes replicate throughout the page.

Knowing just one or two programming languages is no longer sufficient if you want to make serious money in the lucrative world of web design and development. But the good news is that you don't need to spend an excessive amount of time or money on a traditional coding education to get the skills you need to thrive.

Those of us who've taken the time to learn how to code are relatively well-suited for shakeups in the economy. Despite the recent and notable disruptions caused by the COVID-19 outbreak, demand for talented and trained programmers and developers is still high, and it will likely keep rising as companies in every industry adapt their business models to a more remote world.

People use browsers for all types of things, and in general, we trust a lot of personal information to them. That's why browsers are a perfect attack surface for a hacker, because the target may not even know they are infected and feed you all of the information you could want.

No website, service, or platform is immune to being abused or exploited by hackers, and Google Analytics is no exception. To better understand how Google Analytics can help deliver payloads and bypass security protocols, one might want to learn how to use Google Analytics from a user's perspective first.
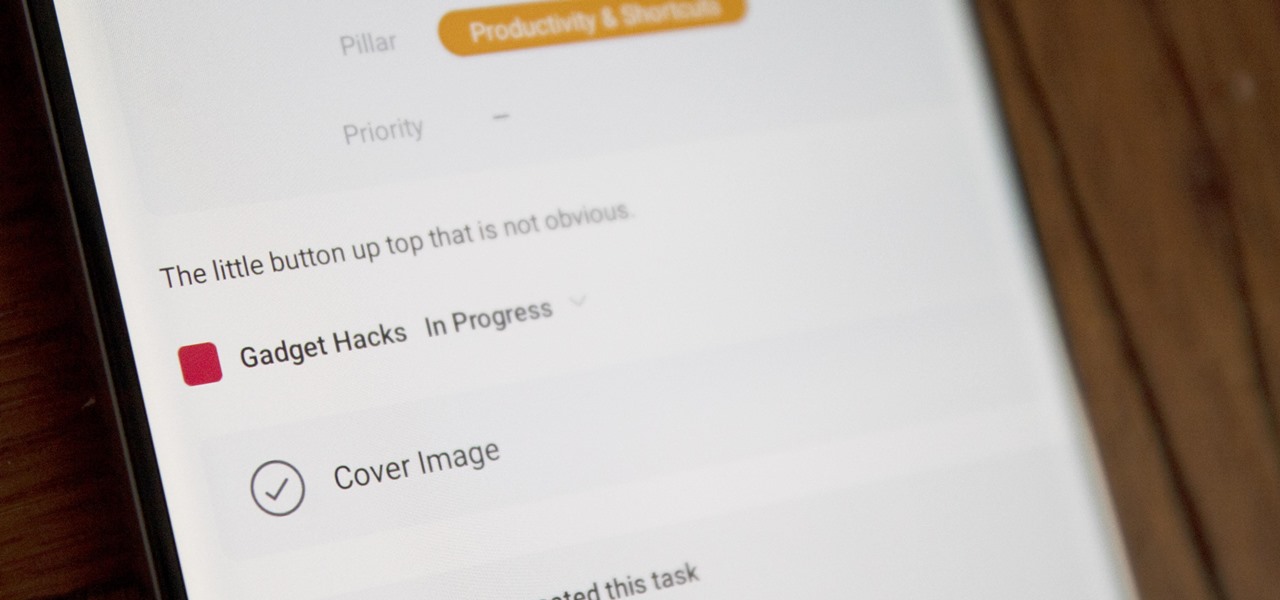
The Asana mobile app lets you manage your projects with the same functionality as the website. Most features are pretty straightforward, thanks to Asana keeping the same design cues from the web app. However, one element is very easy to miss: adding subtasks.

While much of the world is currently in some form of quarantine due to the COVID-19 pandemic, augmented reality (AR) gives us all the opportunity to see virtual content while stuck in our homes.

One of the best ways to dig into a website and look for vulnerabilities is by using a proxy. By routing traffic through a proxy like Burp Suite, you can discover hidden flaws quickly, but sometimes it's a pain to turn it on and off manually. Luckily, there is a browser add-on called FoxyProxy that automates this process with a single click of a button.

After one of Britain's "Brothers Bling" bought Blippar out of bankruptcy, the mobile augmented reality company is getting back to business with the addition of web-based AR capabilities to its platform.
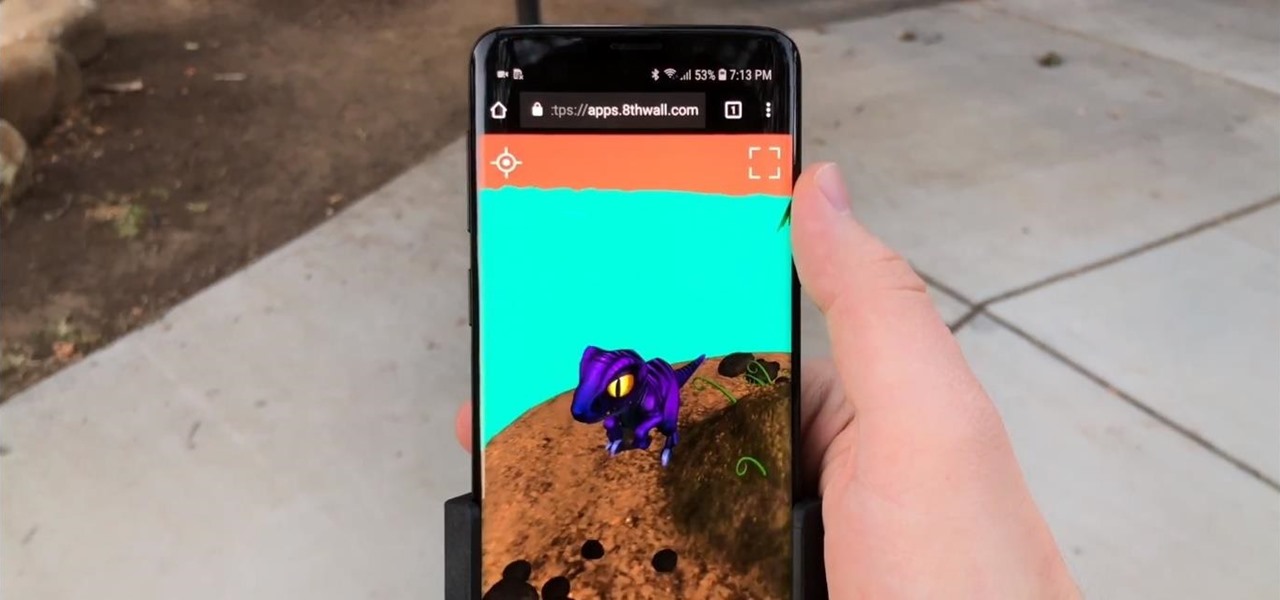
In the past few years, augmented reality software maker 8th Wall has worked to build its platform into a cross-platform augmented reality toolkit for mobile apps, as well as web-based AR experiences.

One of the ultimate goals in hacking is the ability to obtain shells in order to run system commands and own a target or network. SQL injection is typically only associated with databases and their data, but it can actually be used as a vector to gain a command shell. As a lesson, we'll be exploiting a simple SQL injection flaw to execute commands and ultimately get a reverse shell on the server.
If you ever looked at Apple's Peek and Pop feature on Safari and said "I want that," Google has kinda-sorta delivered. A new hidden Chrome feature brings similar functionality to Android despite the lack of 3D Touch, and while it's a bit redundant and nowhere near as polished, it does make navigating the web easier.

Mozilla has created yet another browser for Android. Similar to Firefox Focus, Firefox Rocket was designed to address specific problems: limited internal storage and low data caps. However, in the process of solving these problems, they created one of the fastest browsers on the market.

Thanks to recent reports, we now know third-party apps have a lot more access to our Gmail than we may have initially thought. In fact, these third-party apps have the ability to read our emails, not because these companies are necessarily shady, but because we agreed to it. Luckily, there's a way to view which apps have this access, as well as a way to boot those apps from your Gmail entirely.

Before the release of the Galaxy S8, Samsung quietly uploaded one of their core TouchWiz apps to the Google Play Store as a beta. Samsung Internet, as it's called, has been a staple on all Galaxy devices for years now, but you can now try the browser on any Android phone.

With the release of the Mirai source code, botnets are back in a big way. In the early days of botnets, zombies (infected hosts) would report to IRC (Internet Relay Chat) channels for CNC (command and control) instructions. Modern botnets have evolved, but they continue to use the same concepts as their predecessors.

This scrapbooking page was so easy to create using great products and the fabulous new collection from Anna griffin of the Seafarer Designer Paper/Card Collection.

In this project I make a full 12x12inch scrapbooking page with my Bridal photo. I explain the layers and show you how I arrange the details and the flowers to create a glorious page fit for any album. Step 1: Now Watch the Tutorial

In this demonstration I show you how I have created a really pretty scrapbooking page using papers from the Madison Collection from Anna Griffin and a great photo of me from my Hen Night.

Welcome back, my hacker novitiates! In the previous part of this series, we looked at how to use Metasploit's web delivery exploit to create a script to connect to a UNIX, Linux, or OS X machine using Python. Many members of the Null Byte community have asked me, "Can we do the same for a Windows systems?" The answer is YES!

Welcome back, my tenderfoot hackers! Web apps are often the best vector to an organization's server/database, an entry point to their entire internal network. By definition, the web app is designed to take an input from the user and send that input back to the server or database. In this way, the attacker can send their malicious input back to the servers and network if the web app is not properly secured.

Welcome learners, lets us proceed further with the information we already have. In this post we will explore more about finding hacked accounts online. We will look into how to find juicy info in pastes which are deleted on Pastebin.

Being an Google fanboy means that I pretty much use anything with the company puts out, so it's no surprise that out of all the cloud services out there, I stick with Google Drive. But, this is way more than just some blind allegiance.

Welcome back, my novice hackers! In this third installment of my Hacking Web Apps series, we will look at the authentication of web applications. Remember, there are many ways to hack web applications (as I pointed out in my first article), and cracking authentication is just one method.

As it stands, Firefox OS isn't a very popular third-party operating system for Android devices, especially when compared to others like CyanogenMod, but Mozilla developer Fabrice Desré is attempting to change that.
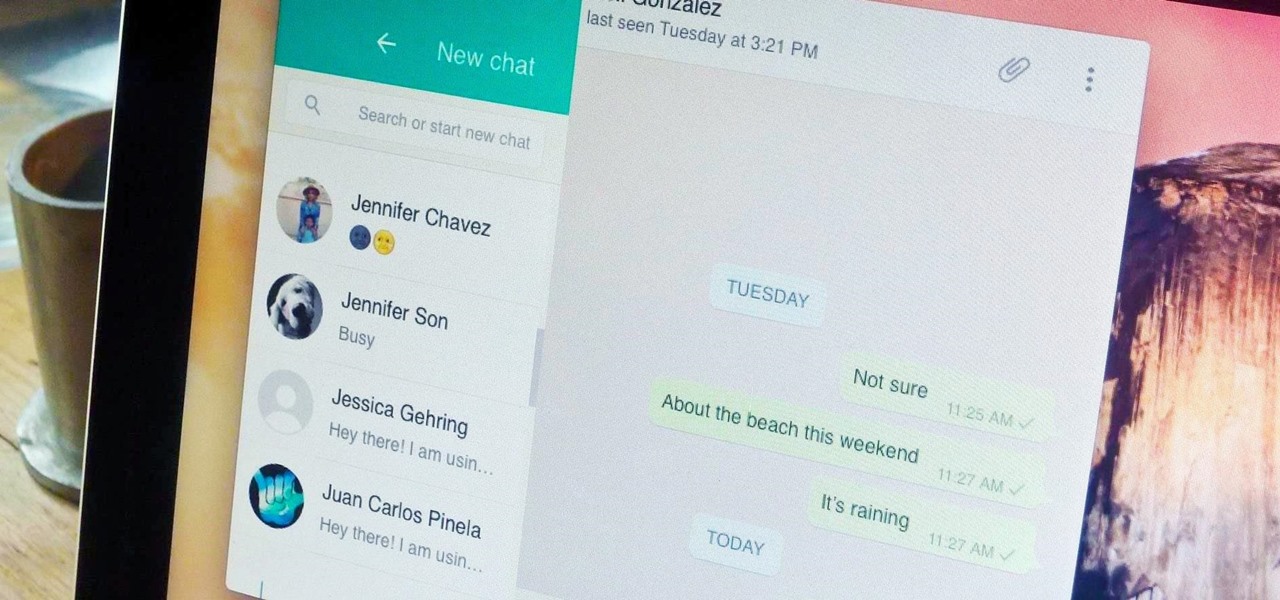
Boasting over 800 million users a month, WhatsApp has quickly become one of the most popular messaging services available today. Thanks to its low price, ease of use, lack of ads, cross-platform functionality, and great features, its popularity is well-deserved.

Android Lollipop still doesn't have a simple way to add a custom lock screen wallpaper, so when I came across Corgi For Feedly from developer Stan Dmitriev, I had to check it out. What sets Corgi apart from other lock screen replacements is that it connects directly to your Feedly account to display top stories from your favorite RSS feeds as your background.

Google Play Music is one of the best streaming services out there. It allows users to upload as many as 20,000 of their own songs for free, then stream them all to any device without ever paying a dime. If you upgrade to their All Access subscription, you get these features in addition to an expansive on-demand library of songs (and beta-access to YouTube Music Key).

Apple's keyboard has a set of media controls to navigate the music playing on iTunes, allowing you to play, pause, skip, and replay songs and videos. Unfortunately, these controls are exclusive to iTunes; if you're playing music from Spotify, Pandora, or the myriad of other online web-based services (Amazon, Rdio, SoundCloud, etc.), you're out of luck.

With so much Flash content still available on the web, it's unfortunate that Google no longer supports mobile Flash Player on Android. Loading a webpage only to be met with a "Plug-in Error" is never fun, and it can inhibit your mobile browsing experience as you attempt to watch a video or play an addicting Flash game.

Welcome back, my hacker novitiates! When we are trying to find vulnerabilities in a website to attack, we need a solid web server vulnerability scanner. Internet-facing web apps can open enormous opportunities for us as they are often riven with vulnerabilities and can often offer an entire point to the internal network and resources.
Canvas fingerprinting is the web's trickiest privacy threat, but it's not impossible to stop. With all the media attention it's gotten lately, it's time we lay out exactly how to detect and prevent this invasive tracking technique.

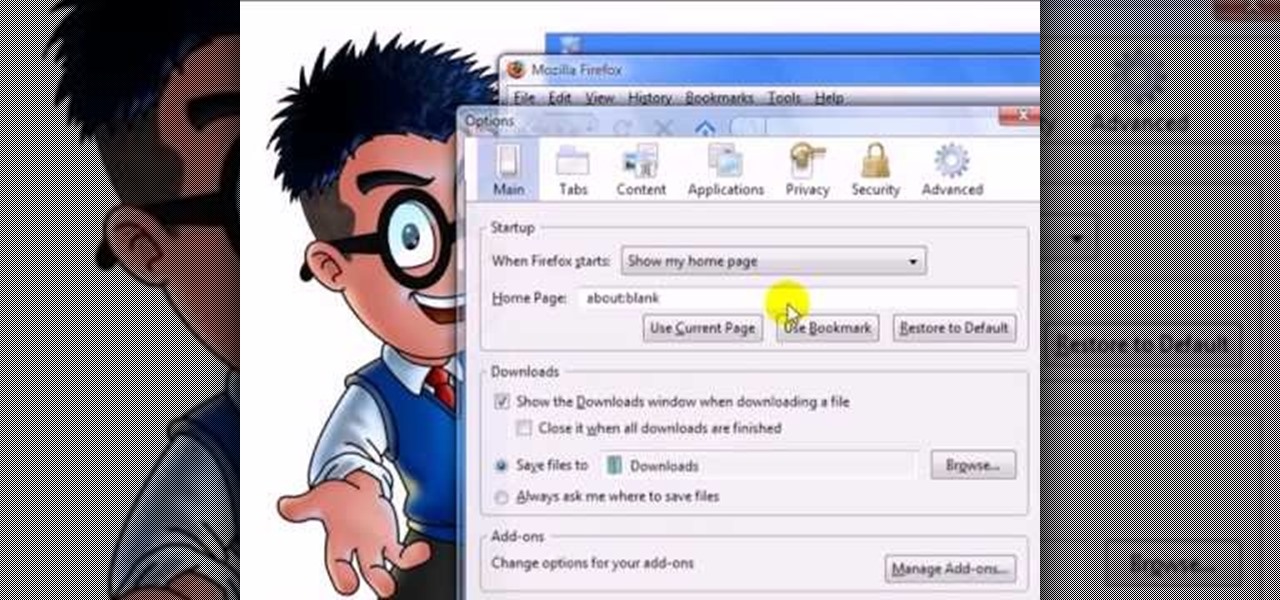
This video will help you how to set browser home page. Video: .

This video will show you how to set Google chrome and Mozilla Firefox browsers home page. With this pc tutorial video you could set browser home page in your PC.

Google recently updated their TOS to reflect the email scanning practices they use in Gmail, which are used to display more relevant ads, among other things.
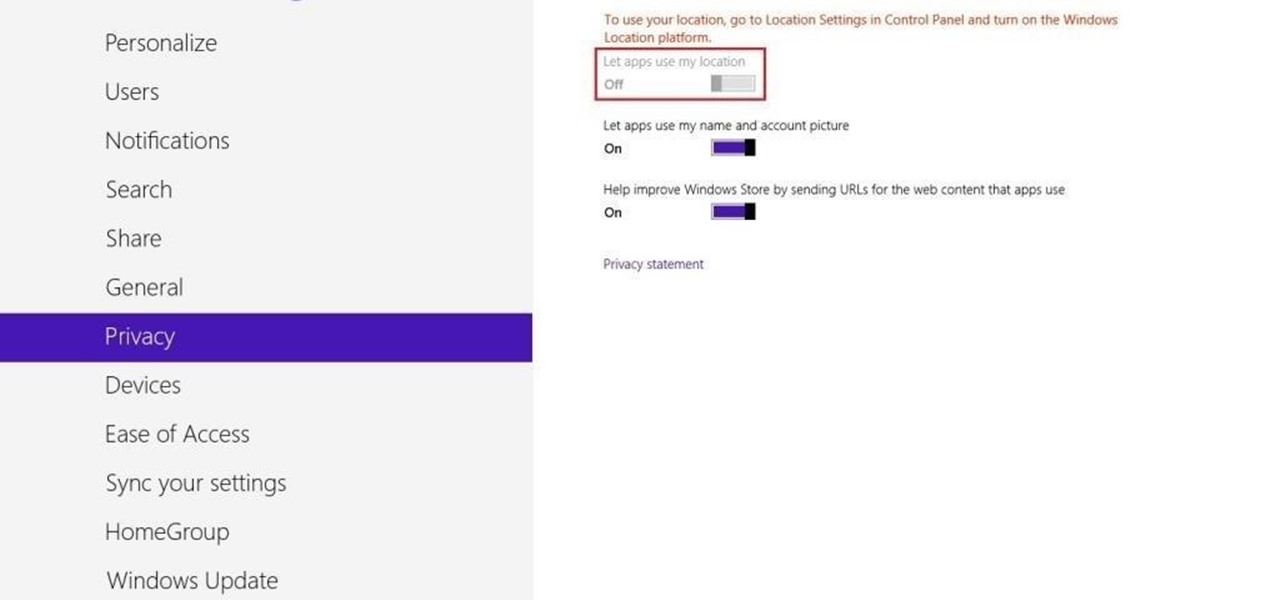
Not only does your mobile phone auto share your location. Now Windows 8 does the same thing. I'm going to show you the two (2) ways to disable that.

Video: . Outre Velvet Remi Tara 2-4-6 Tutorial