News: Hi there looking forward to my site getting approval soon
Once I have I will be loading up some more stuff

Once I have I will be loading up some more stuff

Download these new posters off the LEGO site here
Microsoft office 2010 is the successor version of office 2007 and is code named as office 14. It is the first 64 bit version of office which is only compatible with Microsoft service pack 3, Windows vista and windows 7. It was released on April 15, 2010. It is the first Microsoft application which offers free online version of word, excel, PowerPoint and one note. These can be easily used with all the popular browsing software. The various functionality which are added in office2010 are descr...

Check out Dorkly.com

Good site for more detailed info about a swell and weekly forecasts

Have you ever tried check your e-mail for an important project at school? Were you blocked from the site because of the school's firewall? Stop the block by watching this video tutorial. By following its short and simple instructions, you will be able to access that e-mail at school and get that project turned in on time. By watching this video, you will be able to access any site at work or school and bypass any firewall that will try to stop you. Break through a Facebook firewall at school ...

As if answering Apple's major iPhone event on Tuesday, Chinese mobile giant Xiaomi held its own product launch event the following day.
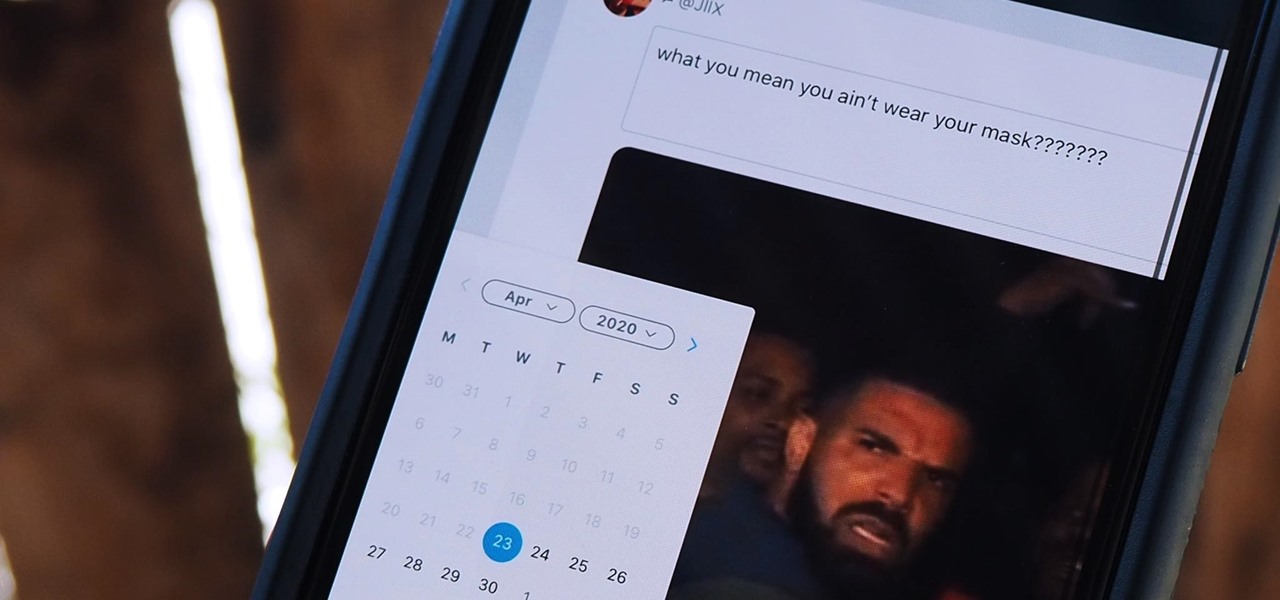
Twitter is a science. The smarter you post and engage with others, the better chance you have at building a bigger audience. Scheduling your tweets is one way to get there. Most engagement occurs at specific hours, but you may not be around then to post your tweet manually. While the official Twitter app on iOS and Android doesn't allow you to schedule, there is another way.

Lego has shipped several apps and products that add an augmented reality dimension to their playsets. But it has taken a reality TV show from Fox to allow brick fans to build with virtual bricks in augmented reality.

While some of us thought Apple might pass on a new beta update in favor of an official release, it appears iOS 13.3.1 is here to stay in beta testing. This time, it didn't take four weeks to get here. The third public beta for 13.3.1 is now available, eight days after the release of public beta 2.

In his famous 1996 "Content is King" essay, Bill Gates predicted that content is where tech companies will make money on the Internet. The adage clearly holds true in the current phase of augmented reality experience.
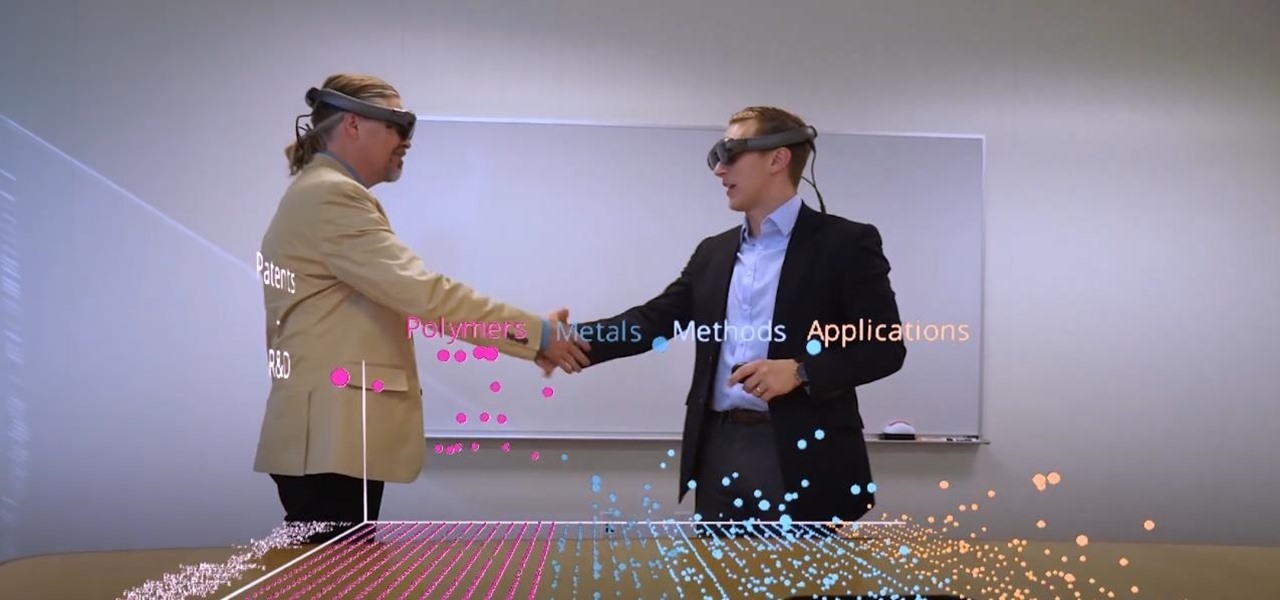
Thanks to the expanding universe of augmented reality tools being made available, increasingly, anybody can liven up sleepy office meetings with immersive computing.

Fans of the friendly neighborhood Spider-Man have yet another way to experience the web-slinger in augmented reality.

In the Tom Holland era, it appears to be impossible to promote a new Spider-Man movie without an augmented reality experience, a trend that continues with Spider-Man: Far From Home.
After improving hand-tracking and adding multi-user sharing features in the last Lumin OS update, Magic Leap has upped the ante yet again.

Months ago, we showed you some of the powers of Spatial, the HoloLens app that allows groups of workers to collaborate in augmented reality using 3D avatars.

Cross-site scripting can be one of the easiest vulnerabilities to discover, but to be successful with this type of attack, it is essential to learn how to get past filters. In the previous guide, we explored some ways to do this, such as abusing attributes and event handlers and tricking the application into accepting unusual characters. Now, let's take a look at more techniques used to defeat filters.
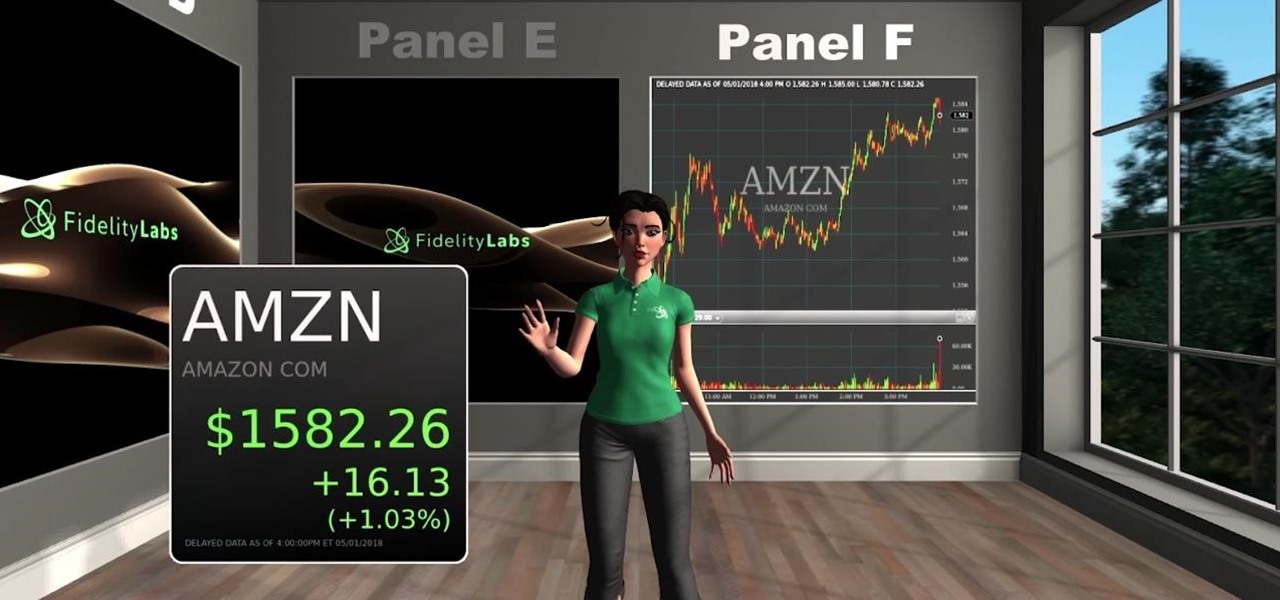
Amazon Web Service's do-it-yourself tool for building augmented reality experiences and VR has graduated from beta and is now available to all interested users.

While there are a variety of privacy-focused search engines available like StartPage and DuckDuckGo, nothing can offer the complete trust offered by creating one's own search engine. For complete trust and security, Searx can be used as free metasearch engine which can be hosted locally and index results from over 70 different search engines.
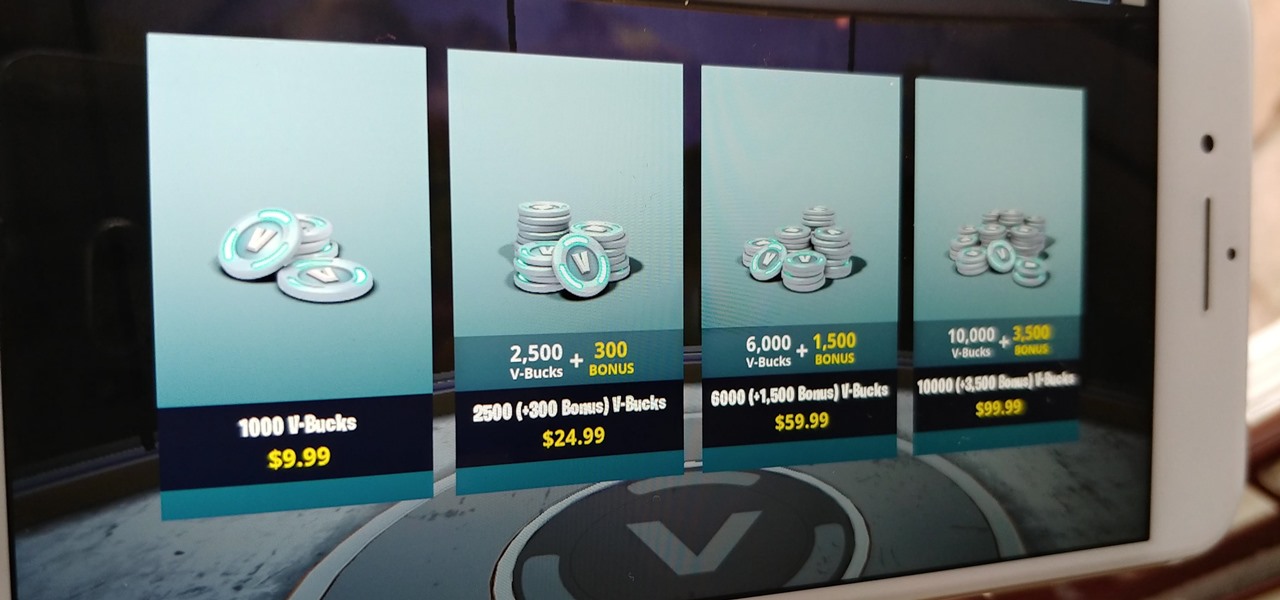
Thanks to its free-to-play strategy, many items in Fortnite Battle Royale require V-Bucks, the in-game currency. You can purchase V-Bucks with real-world money, but many would rather earn V-Bucks instead of getting nickeled and dimed by micro-transactions. While limited, there are a few ways to earn free V-Bucks in the game.

The internet is chock-full of fun and interesting content, but there's only so much time in the day for consuming it. That's when saving webpages for later comes in handy. If you don't want your bookmarks and favorites folders to clutter up fast, consider using the "Reading List" feature built right in Safari on your iPhone.

Snapchat just fast-tracked the majority of its app user base into the world of augmented reality production by making its Lens and Filter tools available to anyone with a web browser.

Amazon Web Services (AWS) opened its re:INVENT developers expo with a bang by launching Amazon Sumerian, a new tool that could become the dominant platform for building cross-platform augmented and virtual reality applications.

A virus easily spread among trout and salmon could make it harder to keep your favorite fish on the menu.

Bose Corp is the latest company trying to make another dollar off of you without your permission. Bose Connect, the companion app to the swag $350 Bose headphones, is not the Jane to your Jack that maybe we all hoped it to be.

A virtual design and construction services firm has built an augmented reality application that uses the Microsoft HoloLens to improve the efficiency of quality control on construction sites.

A scary piece of malware just got a lot more terrifying this week. Security firm Comodo reports that "Tordow," a banking Trojan first uncovered in September 2016, received a massive update this December.

A new hack has reopened an 8-year-old iPhone security loophole that Apple thought it had fixed back with iPhone OS 2.2. This is not one of those times when a theoretical attack gets identified and blocked quickly by Apple. On the contrary, it's a hack that actually exists right now, and it can have some serious real-world repercussions, so this is something all iPhone users need to be aware of.

Some of the best Android apps are not hosted on the Google Play Store, and that means you have to sideload them if you want to get their awesome functionality. But without the Play Store, these APKs are never automatically updated, so your only choice has been to scour the internet for a newer version when you need a bugfix.

Security journalist Brian Krebs recently suffered a record-breaking DDoS attack to his his website, clocking in at or near a whopping 620 Gbps of traffic. Krebs' site was down for over 24 hours, and it resulted in him having to leave his CDN behind.

Snapchat has already found a compelling way to create advertisements in augmented reality with their branded filters, but they continue to experiment with new ways to monetize the bridging of the real and digital worlds. Their latest idea, which requires users to "snap" an image to unlock content, could succeed where QR codes haven't.

Pokémon GO, the global augmented reality game that's brought fans out of their homes to catch Pokémon across the planet, has brought about plenty of real-world positives. Unfortunately, when players get power hungry and start taking game hacks too far, we all get a little screwed—both digitally and in real life.

The desktop browser market has some stiff competition going on, but Opera has always been able to maintain its market share by offering innovative features such as a data saver option. With over 350 million users, it's safe to say folks are appreciative of the efforts being made by the web browser's development team.

While attempting to hack a web app, there may come a point where the attacker may have to escape the default directory in order to access unauthorized files. This is known as a directory traversal attack. Much as the name implies, this attack involved traversing the servers directories. But in order to move to an unauthorized directory, we need to know where those directories are. Today we'll be building a tool to brute force these directory locations based on HTTP response codes. Before we g...

Getting cool new features before everyone else is just plain fun. To be on the bleeding edge can require a lot of effort at times, since the fastest way to get an update is to find it as soon as it leaks, then get to work on sideloading the new version. Luckily, there's an easier way to get the latest features on your favorite apps, with WhatsApp being no exception.

Since I first announced the new Null Byte recognition for excellence a few weeks ago, several of you have written me asking, "How can I study for this certification exam, and what material will be covered on the exam?" Now I have an answer for you. The White Hat Hacker Associate (CWA) will cover 14 domains or areas. Everything you need to know is here on Null Byte. There will be no questions that are not covered here on this site, guaranteed.

Recently, I've been experimenting with BeEF (Browser Exploitation Framework), and to say the least, I'm hooked. When using BeEF, you must "hook" the victims browser. This means that you must run the script provided by BeEF, which is titled "hook.js", in the victims browser. Once you've done that, you can run commands against the victims browser and cause all kinds of mayhem. Among these commands, there is an option to use the victims webcam. This is what we'll be doing here today, so, let's g...

Accidentally deleting important files can happen as easily as swiping left on something and watching it disappear into the ether. Of course, Apple allows automatic backups through iCloud, which ensures that your data is always stored safely in the cloud in case of emergency.

If you are anything like me, you have a knack for taking silly selfies of yourself, i.e., taking scotch tape and wrapping it around your face to make yourself look like the blob, or perhaps you like taking selfies of yourself in weird or unusual situations doing weird and unusual things.

With over a billion monthly active users, it seems that Facebook is nowhere close to being dethroned as the most popular social media service in the world (sorry, Ello). While their stats may be impressive, it doesn't mean that Facebook is as good as it can be.