The reviews for the Google Pixel phone have hit the web. There's a lot of praise, but not all are so positive. We've collected some of the best takes on the new devices from the top tech sites around.

Most of us work with a single monitor, but even with one or two extras, they still offer a rather confined workspace. Virtual reality, however, doesn't have such boundaries. As a result, VR headsets can work as excellent productivity tools. Windows can't just adapt on its own, however, so Envelop VR stepped in and created a new working environment to allow the desktop to expand beyond its traditional, rectangular bounds.

Several major web services—most notably Facebook—have horrendous Android apps that occupy way too much space and drain battery life at an alarming rate. Such issues have led to a new trend where third-party developers create minimalist "lite" apps that are essentially the mobile website bundled into a native Android wrapper, freeing up storage space and saving battery life without sacrificing many features at all.

Welcome back, my novice hackers! In this series, we have been exploring how a forensic investigator can find evidence of illegal or illicit activity. Among other things, we have examined the registry and prefetch files for artifacts and have done some rudimentary forensic analysis. For those of you who are seeking career as a forensic investigator or security engineer, this can be invaluable training. For hackers, it might be life-saving.
If you've ever used the YouTube mobile app for Android or iOS, you've probably noticed a cool little multitasking feature it has. While watching any video, you can simply swipe down on your screen to shrink the video down to a thumbnail view, which then allows you to browse the rest of YouTube while the original video keeps playing.

In Minecraft 1.9 New Command Blocks can be used to make elevators. You types different commands to achieve controlling the elevator for movement you like. This tutorial tells in Minecraft 1.9 how to use command blocks to make elevator. Lets just have a look at it!

You must have read news about hackers dumping the data online, recent one was Ashely Madison. It's only the big companies' data, which gets noticed once it is out. There are many other small leaks which don't even get a mention. So this article is the first one of my series which will help you to find hacked accounts. Some of you must already know about this, but this post is intended for the new learners. This also serves as an example of my learning how a good service can be used in other w...

Welcome back, my tenderfoot hackers! Well, the first season of Mr. Robot just ended and Elliot and fsociety successfully took down Evil Corp! They have effectively destroyed over 70% of the world's consumer and student debt! Free at last! Free at last! Of course, global financial markets crashed as well, but that's another story.

There's a reason that YouTube continues to be the most popular video sharing site on the planet—ever since its purchase by Google, they've always made sure to load YouTube up with extra features to keep it ahead of the pack.

Welcome back, my novice hackers! As we saw in my first tutorial on Facebook hacking, it is not a simple task. However, with the right skills and tools, as well as persistence and ingenuity, nothing is beyond our capabilities.

In today's world, we're constantly switching back and forth between all of our internet-connected devices. A PC may be great while you're at your desk, but the living room couch is tablet territory, and nothing beats the portability of a pocket-sized smartphone while you're on the go.

When streaming services like Spotify or Pandora compete for customers, the main differentiating factor is the size of their libraries. While these and comparable services usually run somewhere around $10 per month, a completely free alternative may actually have the most expansive library out there.

Welcome back, my greenhorn hackers, and happy New Year! Now that your heads have recovered from your New Year's Eve regaling, I'd like to grab your attention for just a moment to preview 2015 here at Null Byte. I hope you will add your comments as to what you would like to see, and I'll try to honor as many requests as I can.

Tired of playing old-school Game Boy Advance, Game Boy Color, Nintendo, and Nintendo DS games on your iPhone? We've got another retro video game system for you to add to your arsenal of emulators—Super Nintendo.

Apple released the iOS 8 Gold Master build to developers shortly after their WWDC event ended on Sept. 9th, which is jam-packed with tons of new features for iPad, iPhone, and iPod touch. The public version comes out on Sept. 17th, but if you can't wait to test out iOS 8, you can get it right now.

Remember when MITMing people to pentest webapps and log-ins you had to fire Ettercap,Arpspoof, SSLstrip, then look for credentials in the captured packets?

This is the best how-to's website that I've ever seen, and I wanted to join it. It taught me a lot, but, because I'm here to learn too, please correct me if I'm wrong.

There are over one million apps in the Google Play Store, and many of them are restricted to certain device types, brands, and Android systems.

It's time to trip out with your tablet. If you're not looking to drain that precious battery life with a fancy-looking live wallpaper, then apply an optical illusion that appears to be moving on your Nexus 7 (or any other Android device) instead.

LastPass is a password manager that's been around for some time, and has finally made its way over to Android for use with apps, not just websites.

Welcome back, my fledgling hackers! As nearly everyone has heard, Target Corporation, one of the largest retailers in the U.S. and Canada, was hacked late last year and potentially 100 million credit cards have been compromised. Happening just before Christmas, it severely dampened Target's Christmas sales, reputation, and stock price (the company's value has fallen by $5B).

If you're marginally inclined towards computers, you've probably been approached at some point by a family member who wants you to "fix" their system during a visit home. With the holidays coming up, these opportunities (or ambushes) are even more likely.

It's officially the holiday season, which means everyone will soon be traveling home to spend time with loved ones. And anyone who has any knowledge whatsoever of computers knows what else that means—family members left and right asking you to fix their various technical woes.

A mustachioed Italian plumber collects coins and battles bullets, plants, fish, mushrooms, and turtles in strange environments to save a princess held captive by a crazy, spiked-shell, bipedal tortoise.

If you want to play games that aren't in the iOS App Store, Apple makes it pretty tough for you. Usually, the only solution is to jailbreak your iPad or iPhone, but that's something most avoid because it will void the warranty and may cause potential bricking issues.

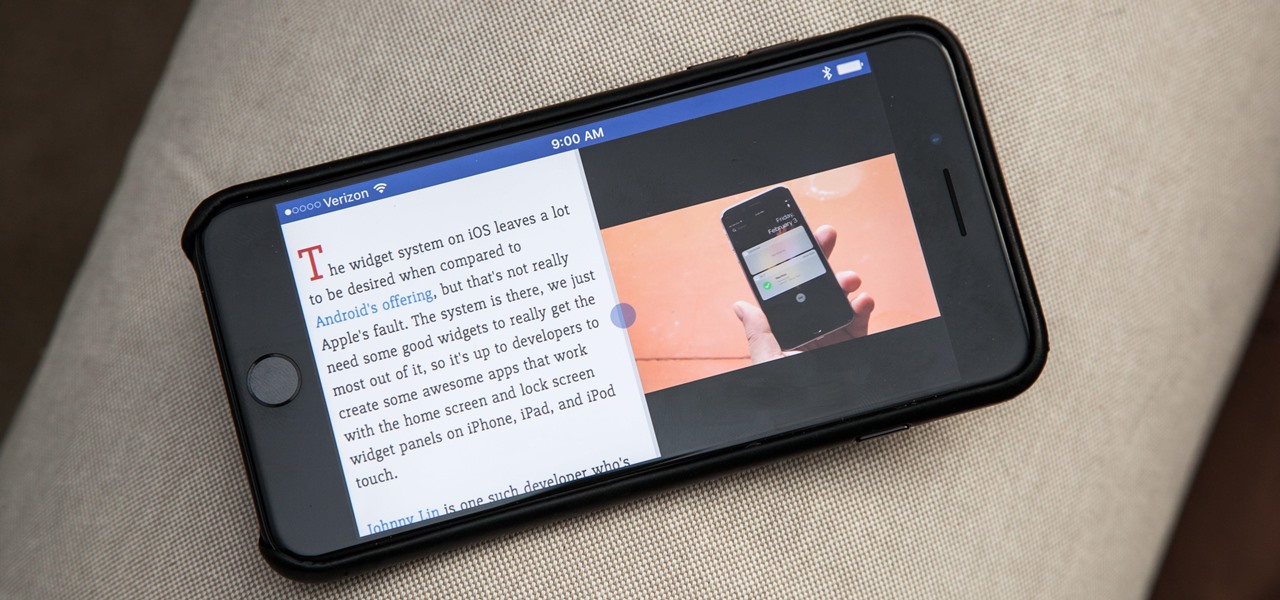
The iPhone has come a long way in its ten-year lifespan, but one thing still missing from the core user experience is native split-screen support. Sure, the displays on iPhones aren't nearly as large as an iPad's screen — which does offer "Split View" mode out of the box — but the iPhone 6 Plus, 6s Plus, and 7 Plus are definitely big enough to use two apps at the same time.

If you thought humans were reading your résumé, think again. Robots do, and their one solitary objective is to systematically crush the hopes and dreams of those who don't make the cut. Instead of paying a few humans to read thousands of résumés over a couple weeks, many companies use computer programs that can do the job in less than an hour. In fact, at least 90 percent of Fortune 500 companies use what they call an applicant-tracking system, aka rejection machines.

Remember that PSP you had? I pretty much dropped mine when smartphones became more prevalent in the mobile gaming scene. Why would I want to carry around a huge PlayStation Portable when I've already got an Android in my pocket?

Search Engine Optimization is important for every successful SEO or blogging campaign. Therefore it is required to be implemented in the correct manner. Google consider many factors while ranking a webpage and it keeps on changing. Some of the common SEO mistakes which you must avoid are as follows:

UPDATE: The whitehouse petition has received enough signatures to require a response from the government. Your voices have been heard! Now we wait...

While the majority of America was watching the Super Bowl yesterday, the crew over at the evad3rs was finishing its work on their untethered iOS 6.1 jailbreak called evasi0n. Well, the wait is finally over!

Streaming video has definitely changed how we watch movies and television shows, but with the constantly growing number of services out there, it can be hard to keep track of who's got what. Who's got Disney now? Starz? Netflix? Who knows. And when you add sites that let you rent or purchase titles, you could spend all evening trying to find something to watch. Here to simplify the process is a service called Can I Stream It?, which lets you search for your favorite movies and TV shows to fin...

The PlayStation 3 is a sweet gaming system, and even though Blu-ray discs didn't really live up to all the hype and there is still no HBO GO app available, I love my PS3. One of the coolest things about it is that you can customize it to look however you want. One of the most common ways to do this is by changing the wallpaper, but most people use their computers to transfer wallpaper images over.

The creation of private browsing was brought upon by the backlash against ad tracking and other ways that sites and agencies take away users' privacy online. People were tired of getting spammed with ads for Vitamin C pills simply because they visited WebMD. Private browsing is now built into all of the major browsers and is used frequently. While private browsing is more infamously known as the "Porn Portal," and does prove to be a great way of keeping racy content out of the sight of others...

What's your Twitter handle worth? If it's considered "desirable" (aka short and simple), it'll get you around 100 bucks, or, if you prefer, the affections of a teenage girl.

Later today, the Olympics are kicking off in London on NBC and its partner stations. However, if you don't have cable or a television with some good reception—or if you'd rather just follow the events on-the-go or at your desk—you're not out of luck. Photo by Locog

There's nothing worse than losing your phone—except losing your phone when the ringer is silent. If you're alone, it can be excruciatingly hard to find your lost device even if the ringer is on, considering most of us don't have landlines anymore. So, the next time you find yourself hunting for your phone, don't tear your house apart until you've tried some of these quick tips.

3D printing has been around for a while, but until recently it was used mostly for prototyping and research. Now, with technological advancements, it seems like everyone is using 3D printers, from crime scene investigators to garage hobbyists and hackers. Below are some of the most innovative uses people have come up with so far.

How to use uTorrent First of all we need to understand what uTorrent is. uTorrent is a file or a Micro-Torrent that helps you, the user, download stuff like documents, pictures, videos, or e-books. uTorrent is very, very, useful when you know how to do it. so hope fully this tutorial helps you learn to use uTorrent.

Here's another delicious Byte. Ucha Gobejishvili, a Georgian Security Researcher under the handle of longrifle0x, discovered two cross site scripting (XSS) vulnerabilities on the official website of Forbes. He discovered the hole in two different locations on the site, and has already informed the website of the vulnerability.