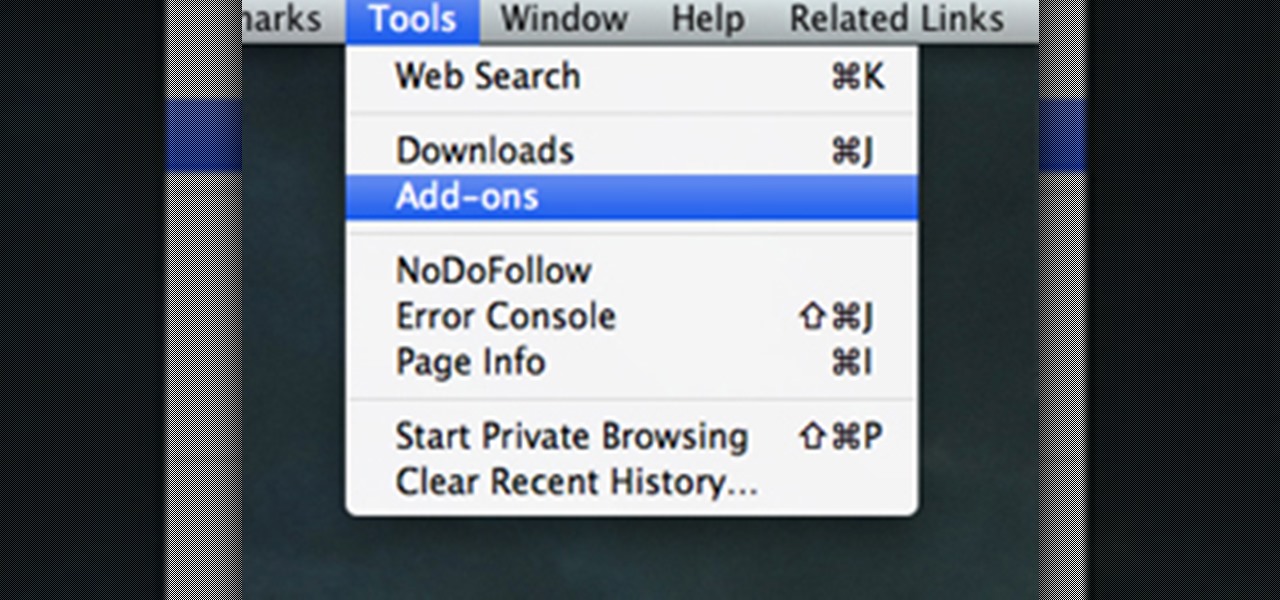
Have you ever had the problem where your grid lines will NOT show up in elevations?!?!?! This is of course after you have checked your VG settings and maximized 3D extents, still NOTHING! Chances are the elevation view is not perpendicular to the grid lines. In most cases this makes sense, how is Revit going to know where you want to intersect the infinite planes of the grid lines. In this Revit tutorial David Fano establishes the point of intersection as the point where the site boundary and...

If you have aftermarket headlights (or any headlight with condensation inside), there are a few things you can do to remove condensation (and prevent it from happening again or at all) from inside them. Click through to the site below for detailed written instructions. Prevent and Remove Condensation Inside Headlights | AutoHow.TV.

A quick-stop-rescue is harder for a beginner to perform. But allows the sailboat to stay closer to the COB. It is also easier to keep site of the COB during the maneuver. Shown in the picture is the a final approach to the COB on a close reach. (Whether one approaches an COB on a close reach or in-irons will depend on your boat's maneuverability, position after your jibe, wind and sea conditions and helmsman's ability.) Quick stop when a victim is in the water while sailing.

If you're looking to get started with your training in web development, a natural starting point is learning to code with Python and then saving and sharing your work on Git and GitHub. These are standard tools of the industry, and mastering them will put you one big step closer to succeeding in the professional sphere.

With iOS 14, Apple finally lets us change the default browser on our iPhones. No longer do we need to settle for Safari if we'd prefer another option like Chrome or Firefox. However, we encourage you to consider switching your browser or your search engine — or both — to Ecosia. Here's why.

The career prospects for talented and trained IT professionals are nearly endless. As the world becomes more interconnected by the day, companies of all sizes are looking for people who can install, maintain, and troubleshoot a wide variety of networking infrastructures and web-based platforms.

The Pi-hole project is a popular DNS-level ad blocker, but it can be much more than that. Its DNS-level filtering can also be used as a firewall of sorts to prevent malicious websites from resolving, as well as to keep privacy-killing trackers such as Google Analytics from ever loading in the browser. Let's take a look at setting a Pi-hole up and customizing a blacklist to suit your needs.

Following someone on Twitter is an investment. You virtually agree to have their opinions, tirades, and hot takes spewed across your timeline. It can get annoying real quick if they're known to post controversial comments periodically. However, there are other ways to stay updated on someone's tweets without you having to hit the follow button and go all in.

The future of smartglasses for consumers seems ever dependent on Apple's entry into the market. Coincidentally, the exit of Apple's long-time design chief Jony Ive has shed some light on that eventual entrance.

A hacker with privileged access to a Windows 10 computer can configure it to act as a web proxy, which allows the attacker to target devices and services on the network through the compromised computer. The probes and attacks appear to originate from the Windows 10 computer, making it difficult to detect the attacker's actual location.

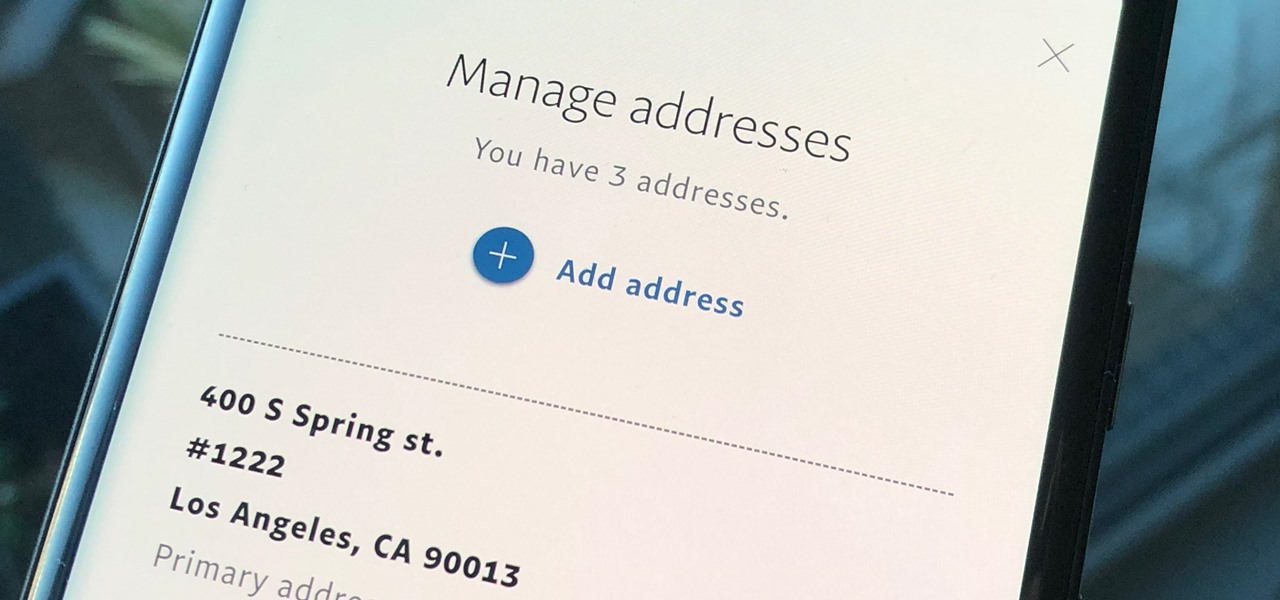
Whenever you move into a new home, whether that's a house or apartment, changing addresses on all your online accounts is one of the most monotonous tasks that needs to be done. It's even more tedious when you have to update both shipping and billing addresses. But it's necessary, and if you regularly use PayPal, it'll be one of the first places you'll want to update.

This week, the recurring theme in augmented reality can be summed up fairly succinctly: content is king.

It's common for IoT devices like Wi-Fi security cameras to host a website for controlling or configuring the camera that uses HTTP instead of the more secure HTTPS. This means anyone with the network password can see traffic to and from the camera, allowing a hacker to intercept security camera footage if anyone is watching the camera's HTTP viewing page.

This week, we continued our NR30 series highlighting the leaders of augmented reality space by profiling the venture capitalists and strategic corporate investors that sustain the industry.

OnePlus has now officially upgraded both the 5 and 5T to Android 8.1 Oreo. As implied by the version number, this isn't a huge update from Android 8.0 Oreo. However, OnePlus has included a few of their own features as well.

Shodan calls itself "the search engine for internet-connected devices." With so many devices connected to the internet featuring varying levels of security, the special capabilities of this search engine mean it can provide a list of devices to test and attack. In this tutorial, we'll use Python to target specific software vulnerabilities and extract vulnerable target IP addresses from Shodan.

While IKEA is collaborating with Apple for its ARKit furniture app, Marxent is ready to help the rest of the interior decorating and home improvement crowd with their apps.

In order for software developers to do their jobs as new hardware reaches the market, they will need the right tools to get their projects off the ground and into augmented and mixed reality devices. There have been completely new approaches to development when it comes to AR and MR, and these are some of the faces behind them.

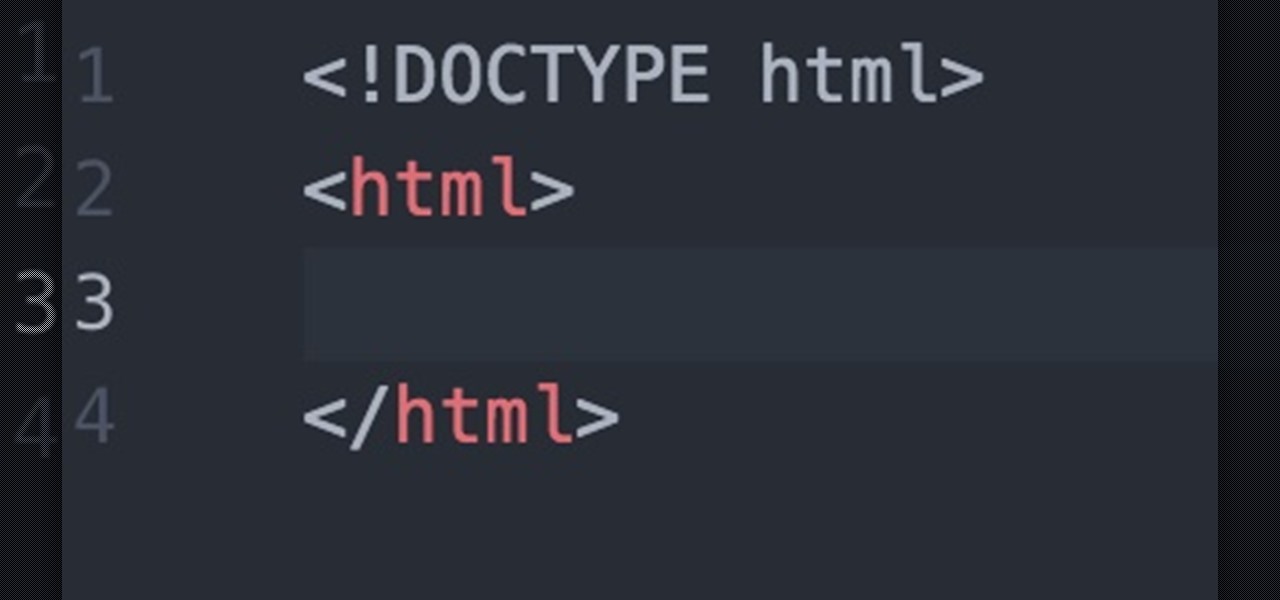
Hello fellow Null-Byters! In this "tutorial" we will be going basics of HTML. In the next tutorial, we will be going over CSS and then apply JavaScript.

It would only make sense that Google is one of the most active app developers on the Android platform, particularly when you consider that they develop the platform itself. From my count, there are an astounding 117 unique apps that the search giant and its subsidiaries have published on the Google Play Store.

It's been a while when the major web browsers first introduced HTTP Strict Transport Security, which made it more difficult to carry Man In The Middle (MITM) attacks (except IE, as always, which will support HSTS since Windows 10, surprised?).

Welcome back, my amateur hackers! Over the course of the next year, we will be developing our own zero-day exploits. In my first article in this series, I introduced you to buffer overflows, which are the source of some of the most lethal exploits, particularly the "remote code execution," so we are focusing our exploit development here on a buffer overflow.

Welcome back, my novice hackers! New hackers often ask me the same question: "What is the easiest platform to hack?" My response is always the same—it is not a platform, but rather a particular piece of software that is easiest to hack, which is on nearly every client-side system. That software is Adobe Flash Player.

Each day, we read about another security breach somewhere in our digital world. It has become so commonplace that we hardly react anymore. Target, J.P. Morgan, iCloud, Home Depot, and the list goes on and on.

With its growing popularity, it's clear that the Chromecast isn't going away anytime soon, with options for casting games, cloud files, music, and much more. But not all content providers are in a hurry to add support for the device, and SoundCloud is one of them. While My Cloud Player is by no means an official SoundCloud app, it comes pretty darn close.

Welcome back, my greenhorn hackers! In a previous tutorial on hacking databases, I showed you how to find online databases and then how to enumerate the databases, tables, and columns. In this guide, we'll now exfiltrate, extract, remove—whatever term you prefer—the data from an online database.

While Siri has never been my favorite, after using her in the new iOS 7, I have definitely become a fan. If you want to know why, check out the newest cool features that Siri has to offer!

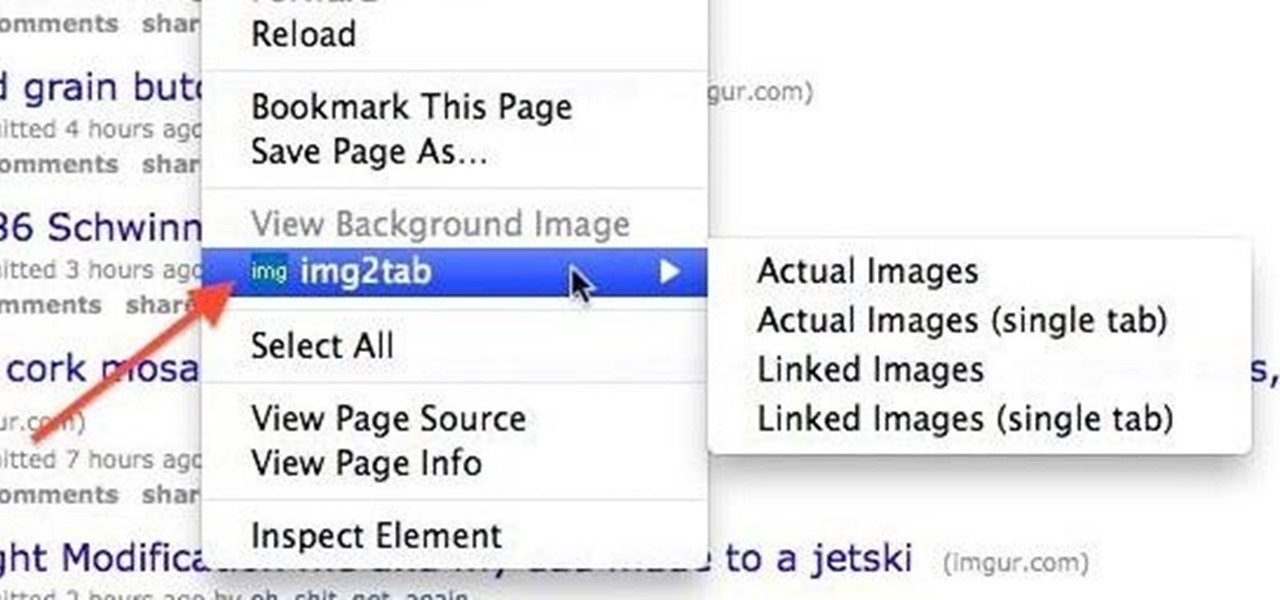
When you're looking at a site with a lot of links to images, it can get really old having to open each one individually. Not to mention loading so many pages can take forever.

This may be an old trick, but it is still very useful. Head.js proudly proclaims that it is the only script you need in your head. You can use it to parallel load all your scripts. This is much faster than loading them one by one.

PDF files are awesome because they're easy to share and they prevent the format on your document from being messed up, no matter what system or program it's opened in. Their biggest downside, though, is how difficult they are to edit or change once they're made.

Introduction In the competitive world of today's video game scene, PC gamers are known to squeeze out the best possible visuals in their games. Every few months a new video card rolls out, and RAM is ever increasing; constant upgrading is the norm of staying ahead the curve. One of the most important things a PC gamer looks at is how many FPS (frames per second) he gets. It defines his gaming experience.

Last week Amazon set their sights on the mobile app market, launching their Appstore for Android. This week they're attacking Android devices once again, but that's not all—they're getting into the online storage biz.

After years of false rumors and abandoned hopes, the day has finally come. Verizon Wireless is finally getting the Apple iPhone!

There's a whole lot of brouhaha going on right now about the hidden plug-ins being installed unknowingly in the Mozilla Firefox web browser, with companies like Apple, Microsoft and even Google being named top offenders.

In this video tutorial, viewers learn how to clear their cache in Internet Explorer. Begin by opening the web browser. Then click on Tools from the top menu and select Internet Options. In the General tab under Browsing History, click on Delete. When the Delete Browsing History window opens, click on Delete Cookies and click OK. To automatically clear cookies, click on Settings under Browsing History and check Every time I visit the web page. Then finish by clicking OK. This video will benefi...

Tracing any IP hostname or web address free online is demonstrated in this video. To trace any IP, website and hostname free online firstly go to the websiteGeoLocationWhen the webpage appears you will get a find option. Enter your IP address, website or hostname here. Then click the find option. Your IP hostname or web address is traced. So easy. Quick and simple to use. Your IP address, city, country, continent and time zone will be displayed in a rectangular box in your location in the wor...

Microsoft ASP.NET is a free technology that allows programmers to create dynamic web applications. ASP.NET can be used to create anything from small, personal websites through to large, enterprise-class web applications. All you need to get started with ASP.NET is the free .NET Framework and the free Visual Web Developer. In this video tutorial, you'll learn how to call a stored procedure within VB.NET. For more information, and to get started calling stored procedures for yourself, take a look.

From Smart Web Printing to recyclable HP inkjet cartridges, it's never been easier to be environmentally conscious.
On May Day in 1971, the US Army rounded up approximately 7,000 protesters into a stadium in Washington, DC that they treated like a make-shift prison camp. Have things changed in the past 40 years? Now a Department of Defense document has been leaked to the Web that details "Internment and Resettlement Operations." The manual outlines policies for processing detainees in internment camps domestically and abroad and how to "re-educate" unruly activists. Alex Jones, host of the Alex Jones Show,...

Business owners and marketeers are diverting from traditional marketing techniques, including billboards, radio and TV advertising, brochures, and any other outdoor promotions, to cheaper but effective Internet marketing strategies. Under the new arrangement, business owners reach out to the final consumers through advertising on the World Wide Web.