Sitting in the Powell Library at UCLA was a constant thing for me. Directly after class, I would streamline my way there to study all night until my eyes shuttered to sleep. For the most part, my classes and professors managed to keep my studying online via PDFs, emails, long essays and journal entries.

Having a boring Facebook profile is lame! Impress your friends and flaunt your social networking skills by sprucing up your Facebook profile.

The first thing anybody really thinks about after watching Rear Window is how much they want their own telephoto lens. These days, they aren't cheap, so how do you go about spying on your neighbors without putting down so much dough?
Learn how to hack Google with this amazing video. This video will teach you how to hack Google by using advanced search operators and esoteric search terms to find “hidden” files and mp3s quickly and easily; you'll also learn how to use Google to hack unprotected Internet-controlled devices like webcams and security cameras. For more information on Google hacking, and how to get started using these hacks yourself, take a look at this instructional video!
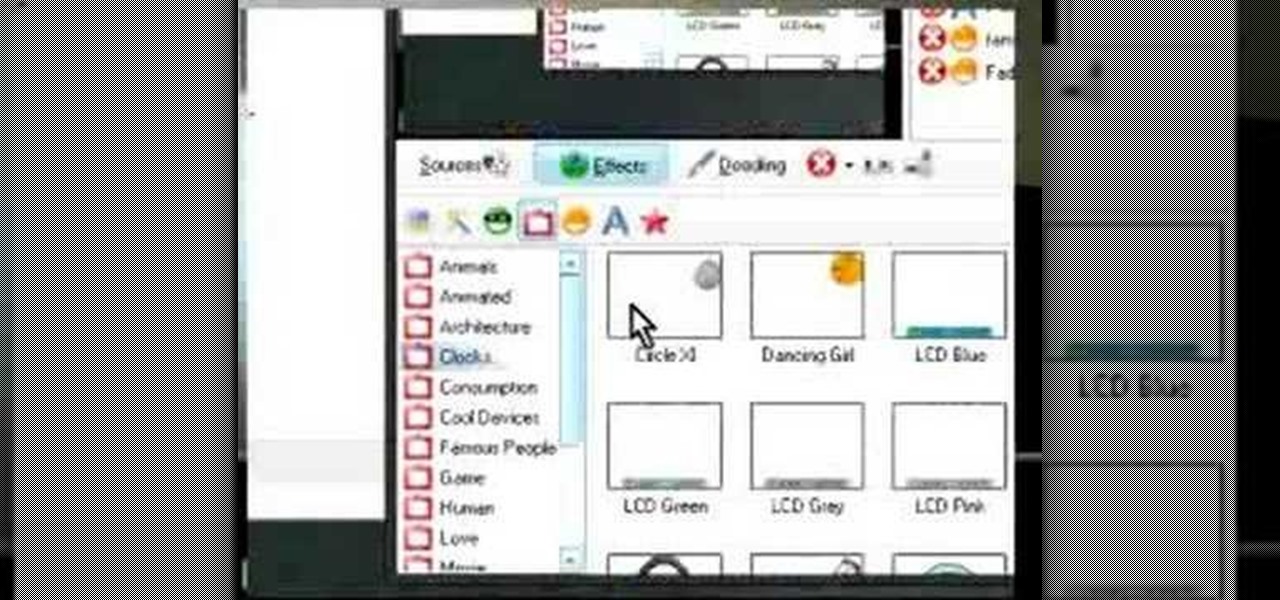
This software tutorial shows you how to configure WebCamMax and then how to use it to add notifications and emoticons to your web camera output or feed. If you want to add more info and customize your webcam videos, learn how you can do it with WebCamMax and this tutorial.

Recently, I've been experimenting with BeEF (Browser Exploitation Framework), and to say the least, I'm hooked. When using BeEF, you must "hook" the victims browser. This means that you must run the script provided by BeEF, which is titled "hook.js", in the victims browser. Once you've done that, you can run commands against the victims browser and cause all kinds of mayhem. Among these commands, there is an option to use the victims webcam. This is what we'll be doing here today, so, let's g...

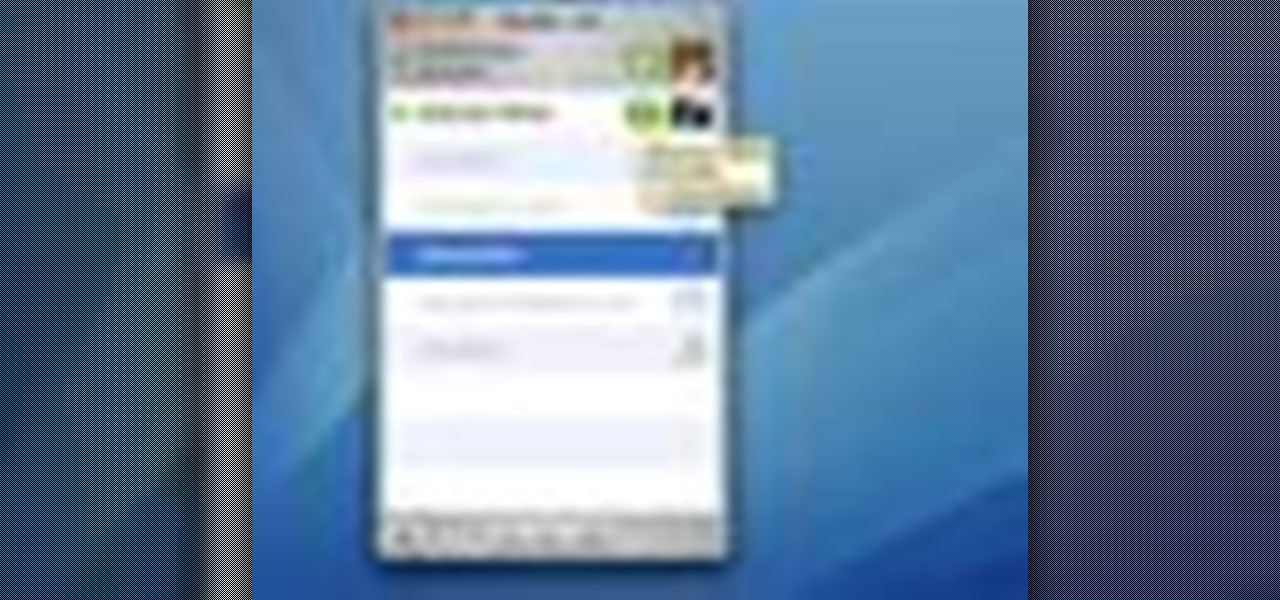
In this video we learn how to use iChat in Mac OS X. He explains to us that iChat allows us to chat with any person on our buddy list. He explains clearly about icons next to a person's name such as a camera which shows you can have a video chat with that person. Next he explains how to change your status, such as, whether you are available to chat or not. He then goes on to explain how to create your own buddy icon which is what people will see when they are chatting with you. You can create...

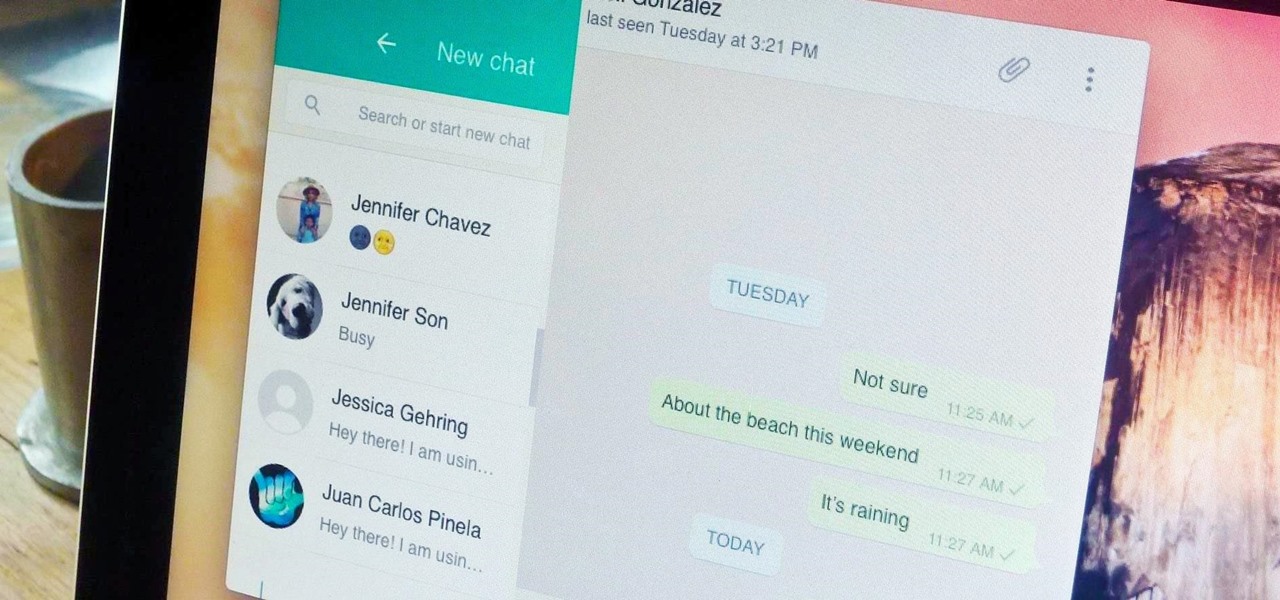
Boasting over 800 million users a month, WhatsApp has quickly become one of the most popular messaging services available today. Thanks to its low price, ease of use, lack of ads, cross-platform functionality, and great features, its popularity is well-deserved.

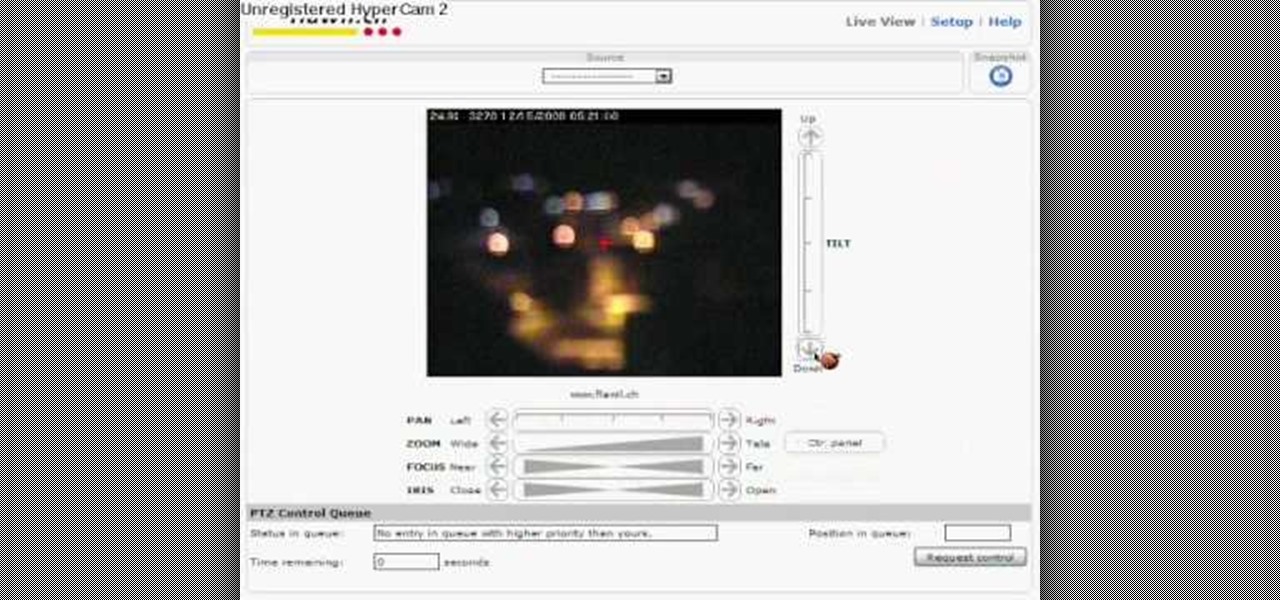
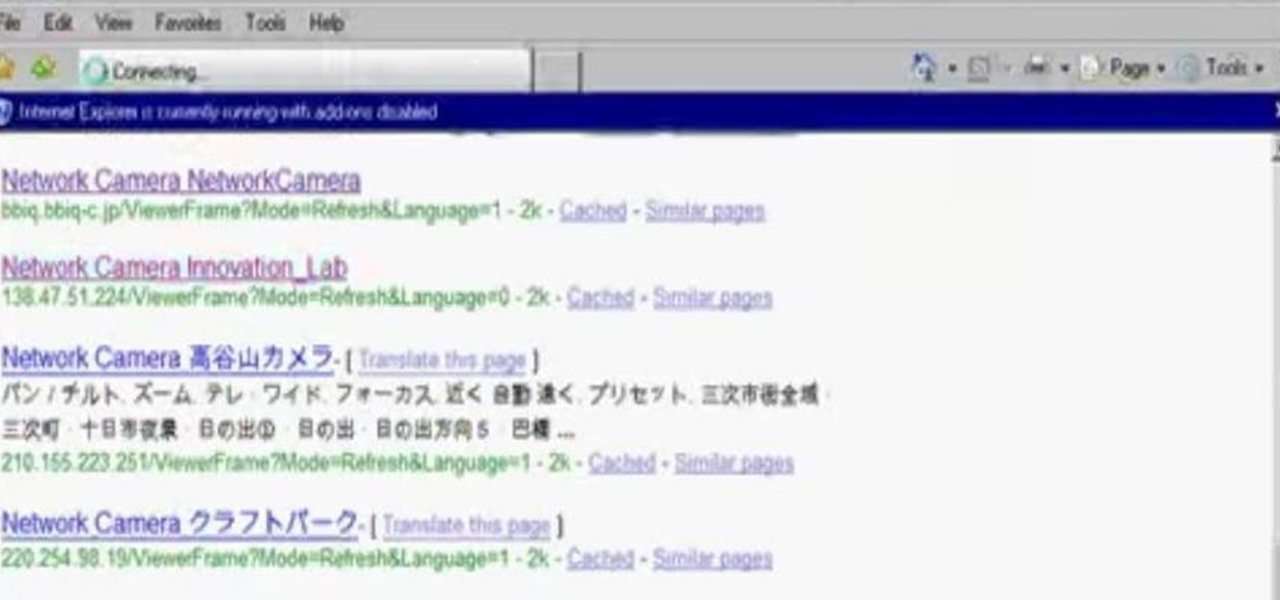
This tutorial will let you hack into a wide selection of web cams and online security cameras. The hack is actually quite easy, and is best done with a browser like Mozilla Firefox. Navigate to Google in your browser, and then type in "inurl:viewerframe?mode+refresh". This piece of code will open up a list of active webcams. Then just surf through your choices and watch whatever you want. You can even change the camera angle and zoom in and out of the picture!

Make stick figure animations using Magix softwareFirst, record yourself with a webcam using Magix music maker. This software is used to record, save and edit the entire video. A trial can be downloaded or it can be purchased. Second, edit the video. Third, save the edited video as and AVI file. Open the AVI file with Adobe image ready. This is only available in older versions of Adobe Photoshop. Next, draw stick figures into frames. Add blood. Export each frame as a gif file into a new folder...

Hacking into computer systems to steal passwords could be a bit complicated for the average everyday joe, but for all of your tech illiterate folks out there, there's any easy way to get that password, and all it takes is a camera.

People use browsers for all types of things, and in general, we trust a lot of personal information to them. That's why browsers are a perfect attack surface for a hacker, because the target may not even know they are infected and feed you all of the information you could want.

For the entirety of its existence, Snapchat has lived on mobile, but in its quest to lead the augmented reality industry, the company is now bringing those mobile AR experiences to desktops.

There are many ways you can protect your computer from unwarranted access. For instance, you can use Lockscreen Pro to lock your Windows 8 computer and then have the program snap a photo of the culprit using your webcam.

Thanks to Flutter, it's now possible to control the music on your computer simply by making a few hand gestures. The app is available for both Windows and Mac and uses your computer's webcam to monitor your hand movements. Through the use of a few simple hand movements, you can play, pause, forward or replay your music. Flutter works with iTunes, Spotify, Quicktime, MPlayerX and a few other programs.

A spectrometer is a device that splits light into all of the different colors it's composed of that can't be seen with the naked eye. It does this by using a prism to refract or bend the light. Jeffrey Warren over at Public Labs created a tutorial showing how you can make your own video spectrometer and create spectra like the one pictured below. Any guesses as to what the subject is? Believe it or not, that's what whipped cream looks like when viewed through a spectrometer. You can do this w...

Welcome back, my greenhorn hackers! Sometimes, we don't have a specific target in mind, but rather we are simply looking for vulnerable and easy-to-hack targets anywhere on the planet. Wouldn't be great if we had a search engine like Google that could help us find these targets? Well, we do, and it's called Shodan!

Another innovative use of augmented reality - we've seen transparent walls, t-shirts that play Rock, Paper, Scissors, an iPhone operated video game drone; and now, a tattoo that comes to life. Just tattoo a simple "barcode", point a webcam at it, and a flying animated dragon will appear, hovering.

Okay, net sleuths — this one's for you. If you've ever wanted to spy on other people on their computers, this video will show you how to use Google to hack unprotected webcams. All you have to do is enter the following into Google's search bar:

Ladies and gentleman, it's official—"Selfie" has been named Word of the Year by Oxford Dictionaries.

Welcome back, my neophyte hackers! Have you ever had a neighbor that you're certain is up to no good? Maybe you've seen him moving packages in and out at all hours of the night? Maybe you've seen people go into his home and never come out? He seems like a creep and sometimes you hear strange sounds coming from his home? You know he's up to no good, but you aren't sure what it is exactly.

Welcome back, my tenderfoot hackers! So many of you responded positively to my post about using the keylogger, as well as my post regarding turning on the webcam, that I decided that you might enjoy another similar hack. In this article, we will enable the audio recording capability on the remote system of your roommate.

You may not have thought of dorks as powerful, but with the right dorks, you can hack devices just by Googling the password to log in. Because Google is fantastic at indexing everything connected to the internet, it's possible to find files that are exposed accidentally and contain critical information for anyone to see.

Learn how to do a fake webcam on msn with Splitcam! Learn all the configurations. Easy and simple , can be use to play any video. Watch and learn.

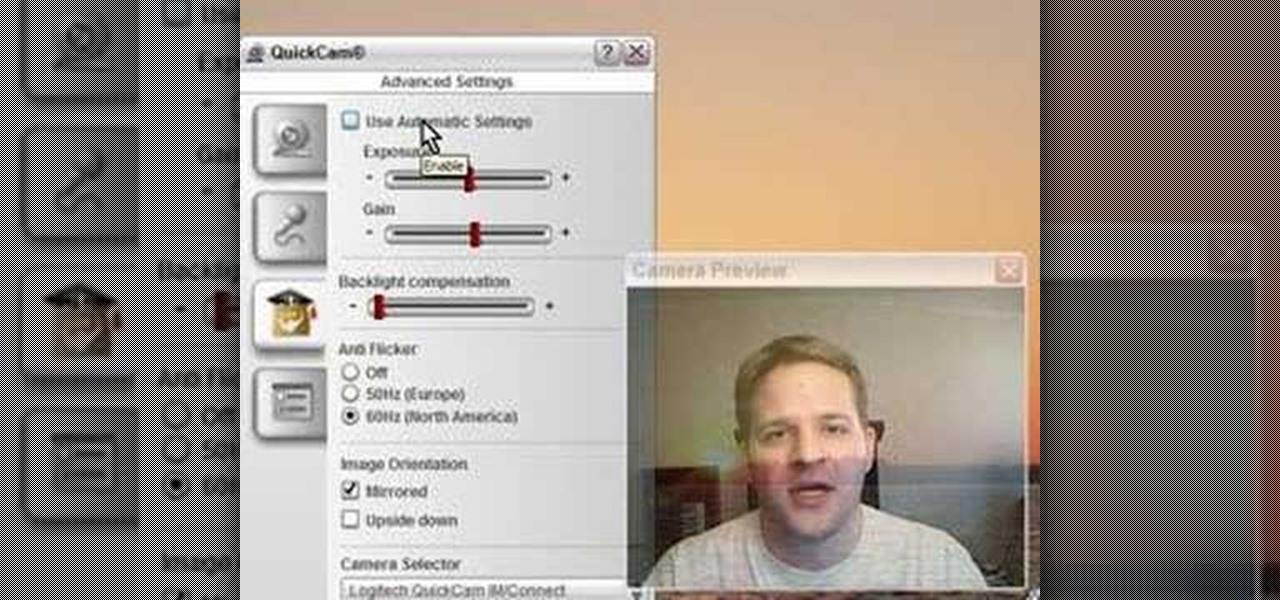
This video shows you how to get the most out of your webcam and get some decent picture quality out of it.

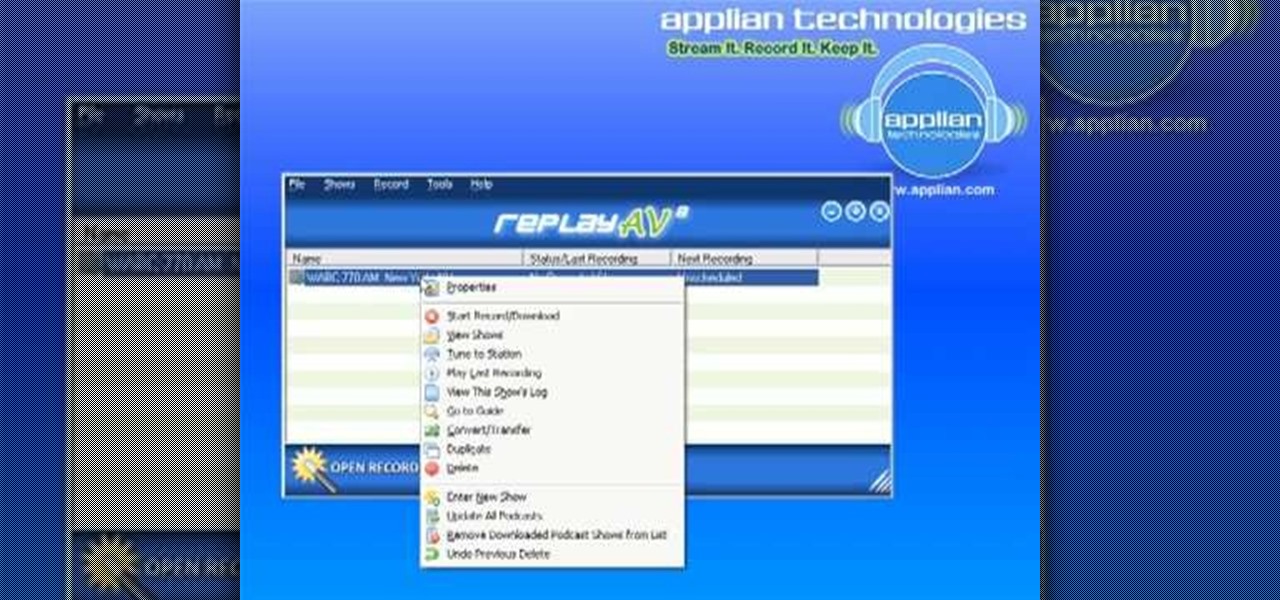
Replay AV is the newest software to come out for downloading steaming audio from the web. Replay AV allows you to download audio from different sources all over the web. You can even record radio broadcasts and set your account to record the station. This video will show you how to add a radio station to Replay AV.

Windows 10 is the most cloud-oriented version of Windows to date—yet, while this means you get some nifty new features, it also means some of your personal data is being shared with Microsoft's servers.

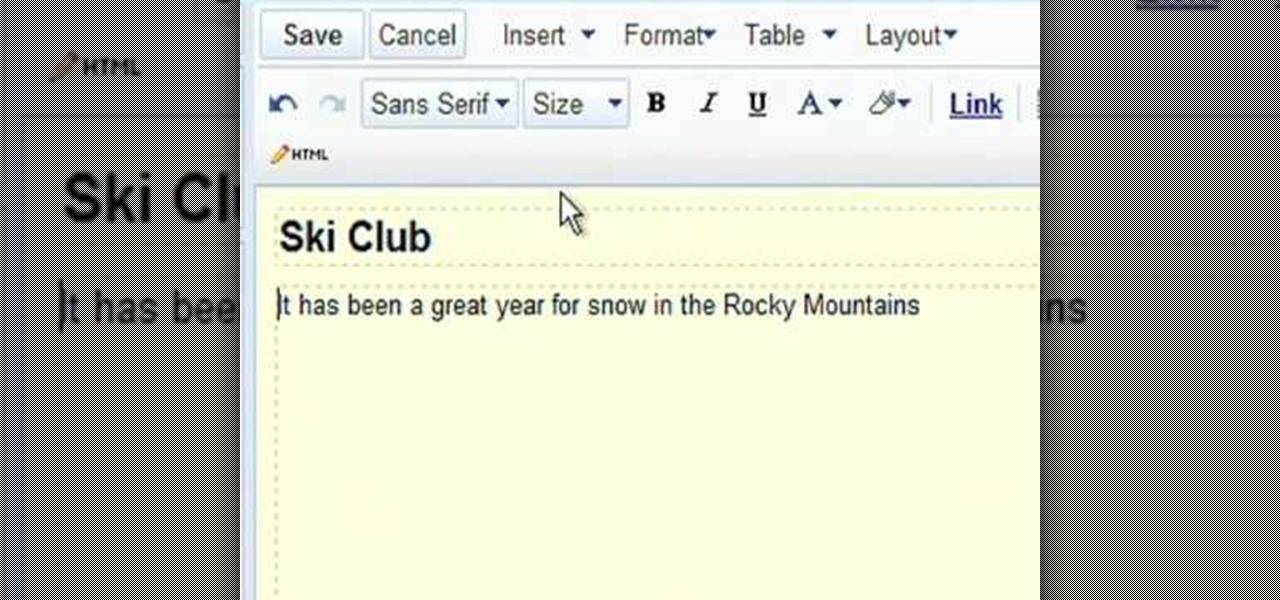
Radford Education teaches you how to create a website using Google Sites. You need to have a Gmail account for this. Go to Google and click More - Sites. After the login, click Create new site in the upper left corner. Complete all the fields, starting with the name of your site. You can also select your site theme below. Hit the Create Site button at the bottom, when you're done. You will then be taken to your brand new site.

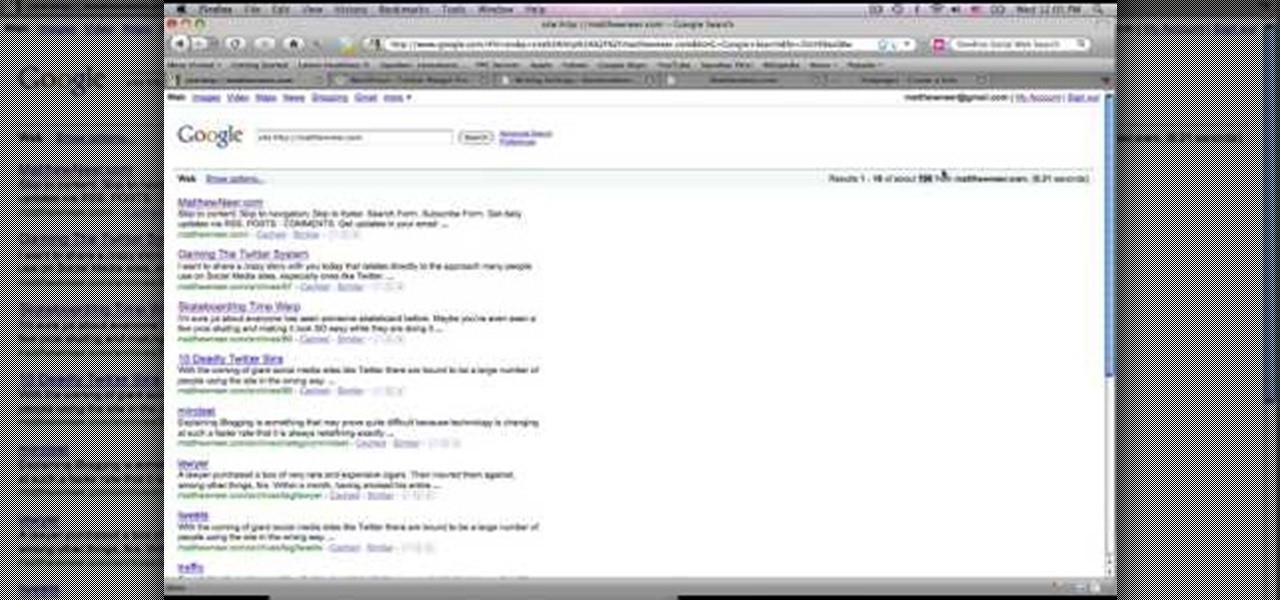
This video tutorial from MatthewNeer presents how to check your site's or blog's Google indexing.Type in Google word Site, press Space and then enter your site's or blog's URL address.Then press Enter or click Search button.Newly opened Google page will show all the pages from your site or blog which are already indexed in Google search engine.From search Results to the right you can see how many pages from your site are already indexed.According to the results you can reoptimize those pages ...

Greetings dear null byters, today we start a new series, we will start to attack users using social networking that are popular such as Facebook, Skype, and much more, and in part 1 of the series will engage users of Skype.

In this episode of Full Disclosure we are explaining the website attack known as Cross-Site Scripting (XSS). Cross-Site Scripting is a type of security vulnerability that affects web applications that do not sanitize user input properly. This kind of vulnerability allows an "attacker" to inject HTML or client side script like JavaScript into the website. Cross-Site Scripting is most commonly used to steal cookies. Cookies are used for authenticating, tracking, and maintaining specific informa...

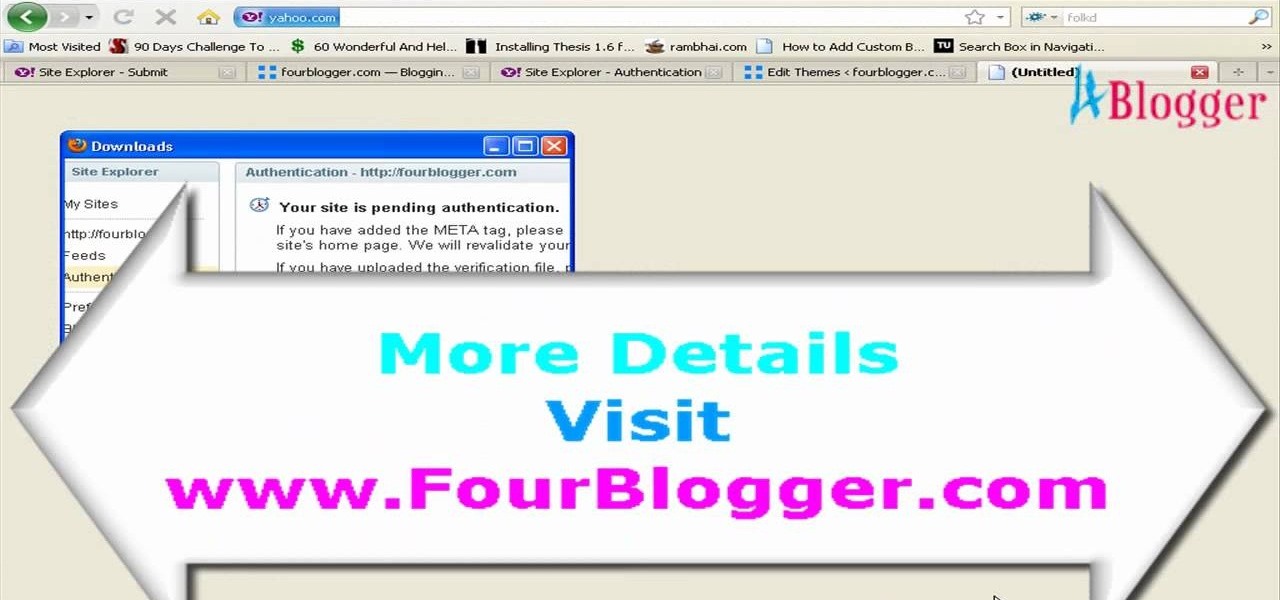
In this video, we learn how to submit your site to the Yahoo search engine. First, go to site explorer. Once here, submit your website or web page in the appropriate box. After this, enter the full URL of the site feed you want to submit. After you do this, go to the side bar and verify your site, or add a META tag, then go to your site. Now, copy the code that Yahoo gave you and paste it into your website. After you do this, your site will be submitted and you can search for it through the Y...

In a previous guide, I demonstrated how to extract images from a security camera over Wi-Fi using Wireshark, provided you know the password. If you don't know the password, you can always get physical with the Hak5 Plunder Bug. Using this small LAN tap, we can intercept traffic like images from a Wi-Fi or IP security camera if we can get physical access to the Ethernet cable carrying the data.

The new iPhone 5 was just revealed yesterday, and it's 18 percent thinner and just 1/5 the weight of its 4S predecessor. It's also taller with a larger screen, which gives you a fifth row for apps now. As far as speed is concerned, it has a speedy A6 chip and can tap into wireless 4G LTE networks for fast Internet. Both the iSight and front-facing FaceTime cameras were improved, too. The only downside seems to be the tinier "Lightning" connector, which replaces the standard 30-pin connector w...

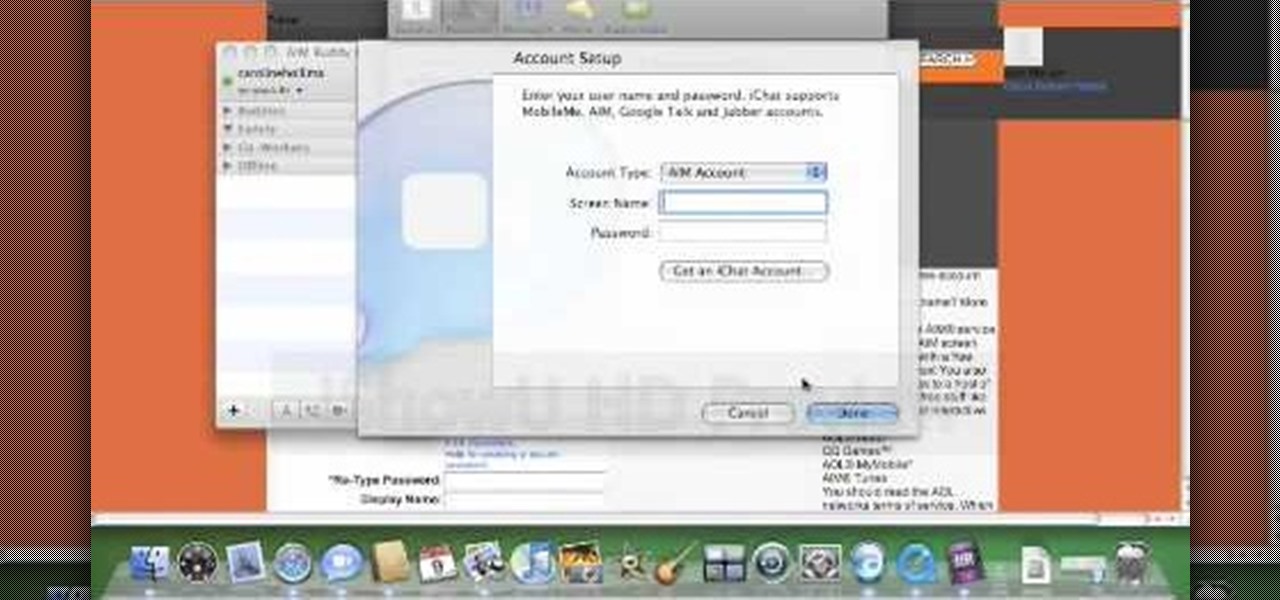
In this video, viewers are shown how to use the iChat feature on a Mac computer. To begin, the video creator instructs us to open Safari (or your preferred) browser and to navigate to www.aim.com. This is the AOL Instant Messenger site (AIM) and from here, you are able to create a screen name. This is important because you have to have a screen name with a instant messaging service to be able to chat using the iChat application.

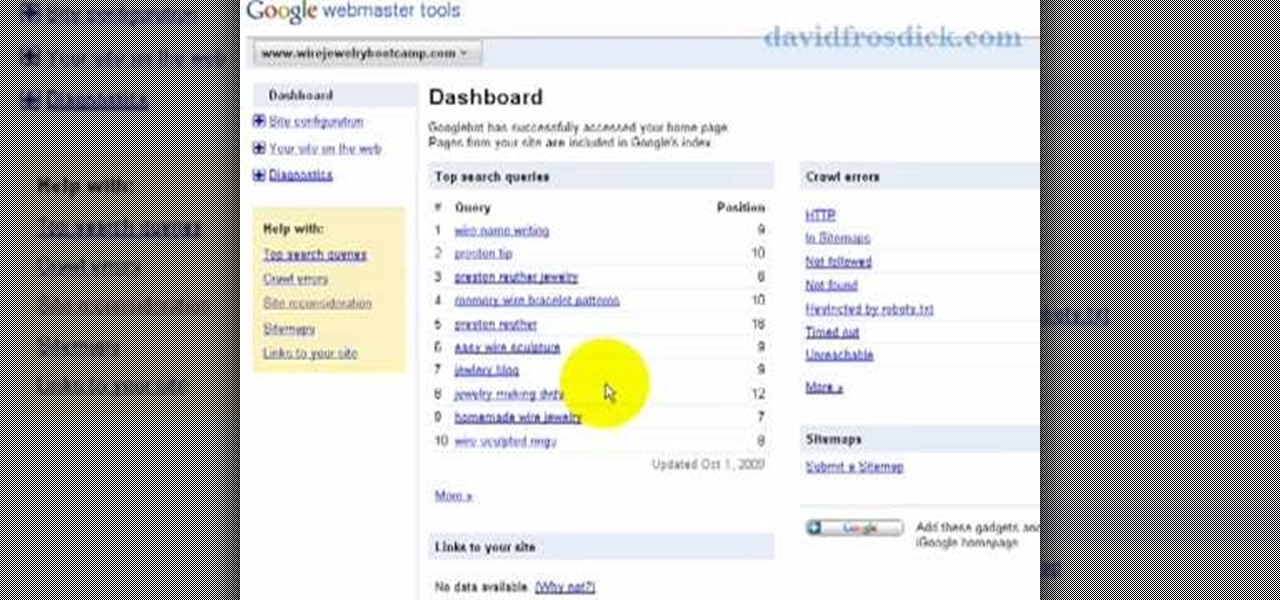
Freelance web developer and Internet marketer David Frosdick offers some tips and tricks in this video tutorial on how to add your site to Google Webmaster Tools.

In this video tutorial, Chris Pels will show how to deploy a web site using the Copy Web Site Tool in Visual Studio. First see how to connect to a remote web site and deploy an entire site to the target location. Next, learn how to synchronize an entire source and target web site. In addition, see how to copy and synchronize individual or groups of files including how the Copy Web Site tool provides status indicators of differences between files. As part of this process see how the tool provi...

In this video tutorial, Chris Pels will show how to configure an ASP.NET web site to use a specific version of ASP.NET/.NET Framework. First see how to identify what version of the .NET Framework a web site is associated with by viewing the script map in Internet Information Server (IIS). See how a script map is associated with the root in IIS and then with individual web sites. Next learn about the ASP.NET IIS Registration tool (aspnet_regiis.exe) used to configure IIS or an ASP.NET web site...

Google Sites makes it easy for anyone to create and manage simple, secure group websites. You can create and publish new pages with the click of a button, edit web pages like documents, and move content and pages around as you please. Information is stored securely online, and you decide who can edit or view the site. Google Sites is powerful enough for a company intranet, yet simple enough for a family website.

Producing professional video can be expensive and time-consuming. Green screens are cumbersome and require a lot of space, whereas dialing in the perfect lighting comes with its own challenges. For people working on a budget and space constraints, achieving the ideal background can be a nightmare.