
How To: Install a solar powered wireless security camera
Video tutorial showing how to make your own solar-powered wireless security camera using an off-the-shelf solar panel and any wireless webcam. See creator site for more detailed graphics.


Video tutorial showing how to make your own solar-powered wireless security camera using an off-the-shelf solar panel and any wireless webcam. See creator site for more detailed graphics.

Welcome back, my greenhorn hackers! Sometimes, we don't have a specific target in mind, but rather we are simply looking for vulnerable and easy-to-hack targets anywhere on the planet. Wouldn't be great if we had a search engine like Google that could help us find these targets? Well, we do, and it's called Shodan!
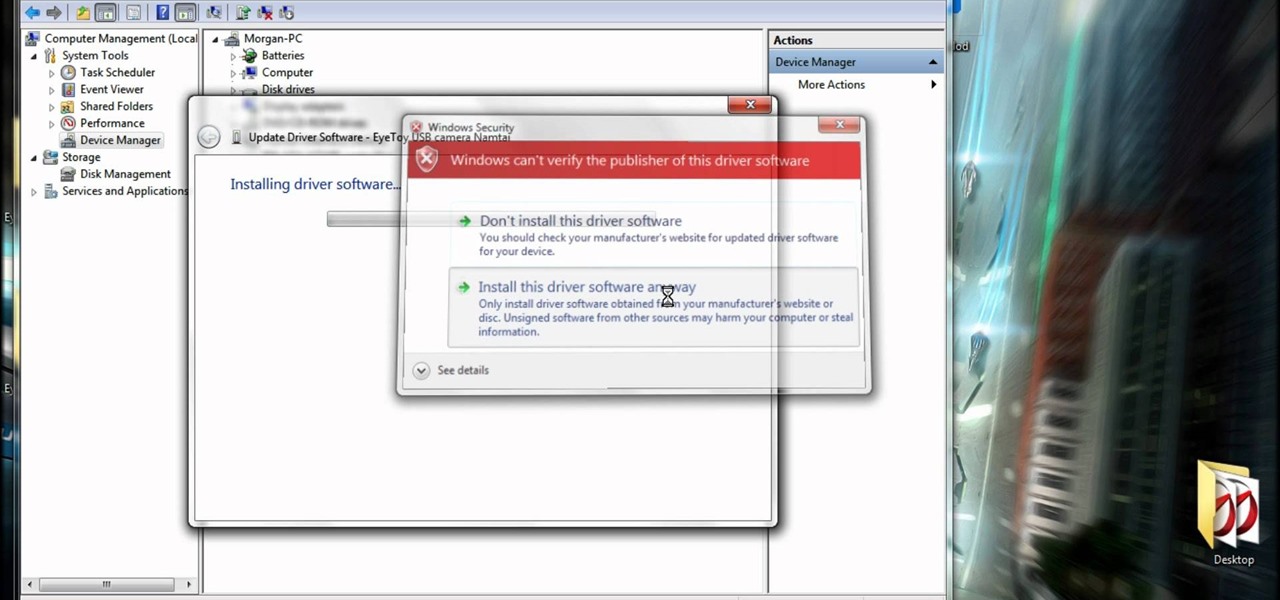
If you have a PS2/PS3 Eyetoy, but don't want to go and spend $30+ dollars on a new webcam, then this is for you.

You don't need a rotoscope or special lip syncing equipment - you can create the stop motion effect with any digital SLR - even a webcam! All you need to do is add an adapter, as shown in this tutorial.

Have your ever wanted to build a bird feeder? Do you want to know what types of birds live in your neighborhood? If the answer to one of these questions is yes, then this video is for you. Bre Pettis will teach you how to make two different types of bird feeders and then how to attach a webcam to the feeders so you can watch the birds.

Most of us work with a single monitor, but even with one or two extras, they still offer a rather confined workspace. Virtual reality, however, doesn't have such boundaries. As a result, VR headsets can work as excellent productivity tools. Windows can't just adapt on its own, however, so Envelop VR stepped in and created a new working environment to allow the desktop to expand beyond its traditional, rectangular bounds.

Aaron Betsky, director of the Cincinnati Art Museum and previous director of the Netherlands Institute of Architecture, reports on the world's first postage stamp to employ augmented reality. Dutch advertising agency Gummo, the NIA and the Dutch postal service teamed up to present five unbuilt models by different Dutch architecture studios in 3D form. When held in front of a webcam, the illusion of a 3D building is projected in your hand. By slowly moving the stamp, you can experience the vir...
Sitting in the Powell Library at UCLA was a constant thing for me. Directly after class, I would streamline my way there to study all night until my eyes shuttered to sleep. For the most part, my classes and professors managed to keep my studying online via PDFs, emails, long essays and journal entries.

Having a boring Facebook profile is lame! Impress your friends and flaunt your social networking skills by sprucing up your Facebook profile.

The first thing anybody really thinks about after watching Rear Window is how much they want their own telephoto lens. These days, they aren't cheap, so how do you go about spying on your neighbors without putting down so much dough?
Learn how to hack Google with this amazing video. This video will teach you how to hack Google by using advanced search operators and esoteric search terms to find “hidden” files and mp3s quickly and easily; you'll also learn how to use Google to hack unprotected Internet-controlled devices like webcams and security cameras. For more information on Google hacking, and how to get started using these hacks yourself, take a look at this instructional video!
In this video we learn how to use iChat in Mac OS X. He explains to us that iChat allows us to chat with any person on our buddy list. He explains clearly about icons next to a person's name such as a camera which shows you can have a video chat with that person. Next he explains how to change your status, such as, whether you are available to chat or not. He then goes on to explain how to create your own buddy icon which is what people will see when they are chatting with you. You can create...

Department store chain Target is the latest retailer to offer an augmented reality cosmetics app for customers to virtually try on lipstick.
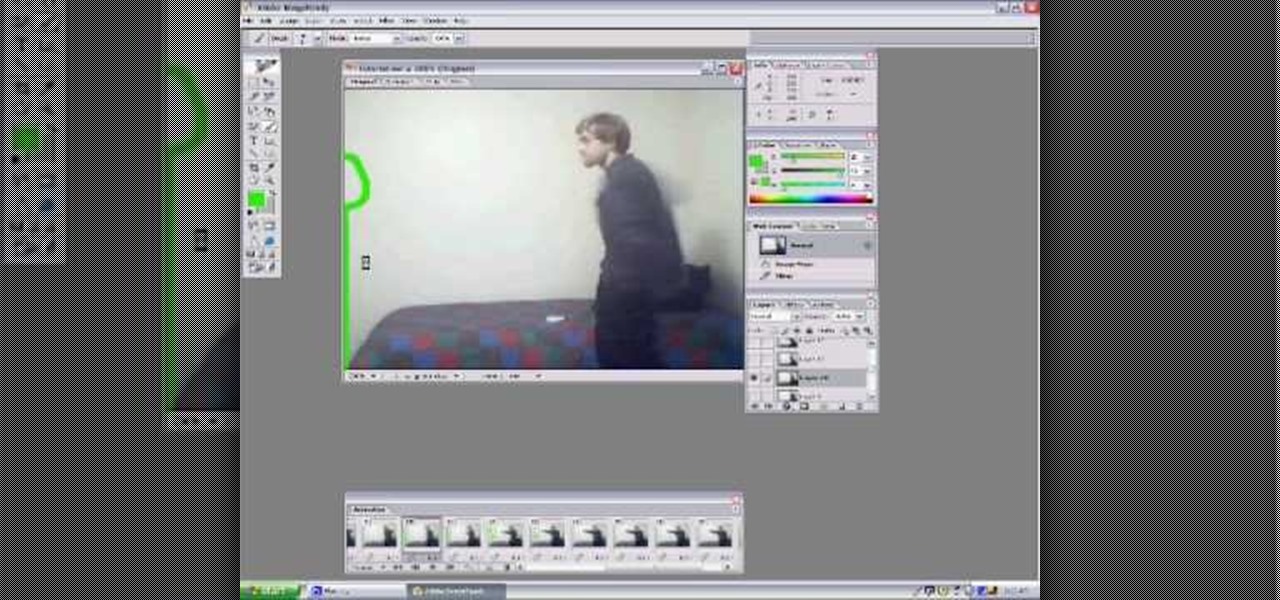
Make stick figure animations using Magix softwareFirst, record yourself with a webcam using Magix music maker. This software is used to record, save and edit the entire video. A trial can be downloaded or it can be purchased. Second, edit the video. Third, save the edited video as and AVI file. Open the AVI file with Adobe image ready. This is only available in older versions of Adobe Photoshop. Next, draw stick figures into frames. Add blood. Export each frame as a gif file into a new folder...

Hacking into computer systems to steal passwords could be a bit complicated for the average everyday joe, but for all of your tech illiterate folks out there, there's any easy way to get that password, and all it takes is a camera.

For the entirety of its existence, Snapchat has lived on mobile, but in its quest to lead the augmented reality industry, the company is now bringing those mobile AR experiences to desktops.

There are many ways you can protect your computer from unwarranted access. For instance, you can use Lockscreen Pro to lock your Windows 8 computer and then have the program snap a photo of the culprit using your webcam.

Thanks to Flutter, it's now possible to control the music on your computer simply by making a few hand gestures. The app is available for both Windows and Mac and uses your computer's webcam to monitor your hand movements. Through the use of a few simple hand movements, you can play, pause, forward or replay your music. Flutter works with iTunes, Spotify, Quicktime, MPlayerX and a few other programs.

A spectrometer is a device that splits light into all of the different colors it's composed of that can't be seen with the naked eye. It does this by using a prism to refract or bend the light. Jeffrey Warren over at Public Labs created a tutorial showing how you can make your own video spectrometer and create spectra like the one pictured below. Any guesses as to what the subject is? Believe it or not, that's what whipped cream looks like when viewed through a spectrometer. You can do this w...

The response to the COVID-19 pandemic means that social distancing has become the new normal. It also means that more Americans are using video conferencing to connect with colleagues working from home or friends and family in quarantine because of the new coronavirus.

Another innovative use of augmented reality - we've seen transparent walls, t-shirts that play Rock, Paper, Scissors, an iPhone operated video game drone; and now, a tattoo that comes to life. Just tattoo a simple "barcode", point a webcam at it, and a flying animated dragon will appear, hovering.
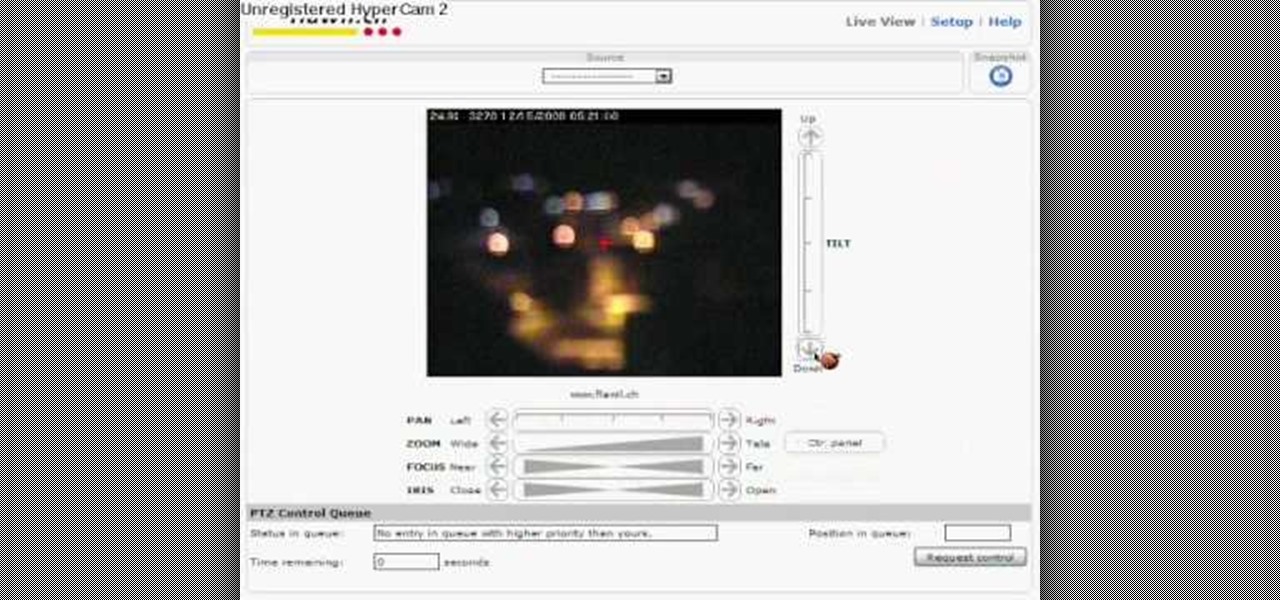
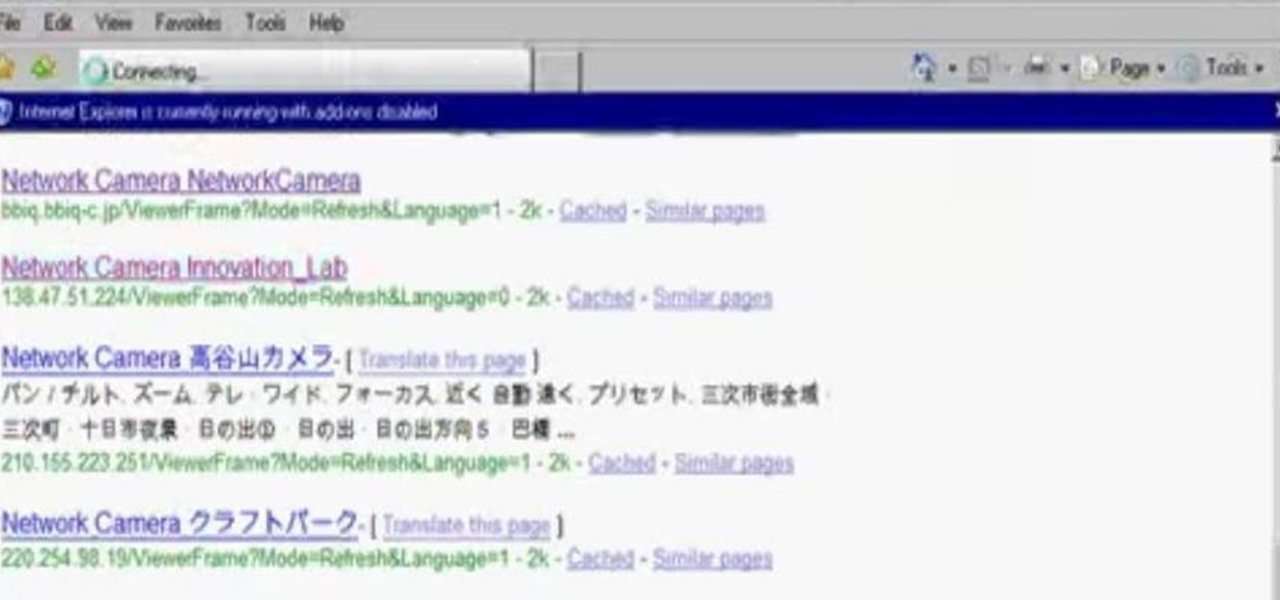
Okay, net sleuths — this one's for you. If you've ever wanted to spy on other people on their computers, this video will show you how to use Google to hack unprotected webcams. All you have to do is enter the following into Google's search bar:

Welcome back, my hacker novitiates!

You may not have thought of dorks as powerful, but with the right dorks, you can hack devices just by Googling the password to log in. Because Google is fantastic at indexing everything connected to the internet, it's possible to find files that are exposed accidentally and contain critical information for anyone to see.

Not too long ago I showcased ReCam, a free app that lets you schedule recordings and use your Android device as a security or spy camera of sorts. While useful, this app required you to schedule when to record in advance, resulting in you possibly missing the footage you intended to record (assuming your scheduling wasn't as on-point as you wished).

Welcome back, my tenderfoot hackers! Not too long ago, I showed how to find various online devices using Shodan. As you remember, Shodan is a different type of search engine. Instead of indexing the content of websites, it pulls the banner of web servers on all types of online devices and then indexes the content of those banners.

Welcome back, my novice hackers! New hackers often ask me the same question: "What is the easiest platform to hack?" My response is always the same—it is not a platform, but rather a particular piece of software that is easiest to hack, which is on nearly every client-side system. That software is Adobe Flash Player.

Welcome back, my neophyte hackers! Have you ever had a neighbor that you're certain is up to no good? Maybe you've seen him moving packages in and out at all hours of the night? Maybe you've seen people go into his home and never come out? He seems like a creep and sometimes you hear strange sounds coming from his home? You know he's up to no good, but you aren't sure what it is exactly.

Welcome back, my tenderfoot hackers! So many of you responded positively to my post about using the keylogger, as well as my post regarding turning on the webcam, that I decided that you might enjoy another similar hack. In this article, we will enable the audio recording capability on the remote system of your roommate.

Welcome back, my novice hackers! In this third installment of my Hacking Web Apps series, we will look at the authentication of web applications. Remember, there are many ways to hack web applications (as I pointed out in my first article), and cracking authentication is just one method.

I may not be a parent just yet, but I've dealt with enough worrisome mothers to know that keeping a watchful eye over your child is of the top-most importance. Since most people cannot afford to stay right by their child's side 24/7, developers are always looking for ways to make the pain of stepping away a little less stressful for parents.

In a previous guide, I demonstrated how to extract images from a security camera over Wi-Fi using Wireshark, provided you know the password. If you don't know the password, you can always get physical with the Hak5 Plunder Bug. Using this small LAN tap, we can intercept traffic like images from a Wi-Fi or IP security camera if we can get physical access to the Ethernet cable carrying the data.

Learn how to do a fake webcam on msn with Splitcam! Learn all the configurations. Easy and simple , can be use to play any video. Watch and learn.
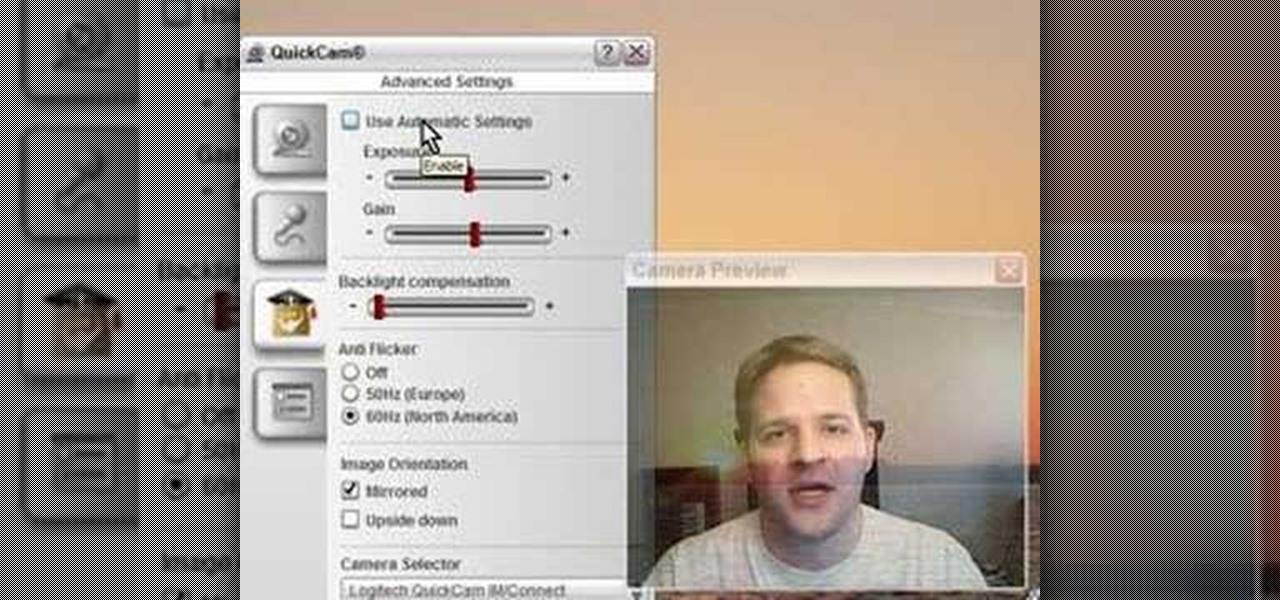
This video shows you how to get the most out of your webcam and get some decent picture quality out of it.
In this video tutorial, Chris Pels will show how to create a web service in ASP.NET and then call the service from another ASP.NET web site. First, learn how to create an .asmx component which represents a web service in an ASP.NET web site. When creating the web service learn how to control several aspects of the web service functionality with web service attributes. Next, see how to test the web service in the Visual Studio web service test page. Then learn how ASP.NET allows many .NET data...

One of the best uses for an old Android device is to turn it into a security webcam that can be accessed over the internet. But most of the time, this is a rather difficult process, because existing apps usually require you to mess around with network settings and configure a personal web server.

Welcome back, my budding hackers! Metasploit, one of my favorite hacking/pentesting tools, has so many capabilities that even after my many tutorials on it, I have only scratched the surface of it capabilities. For instance, it can be used with Nexpose for vulnerability scanning, with Nmap for port scanning, and with its numerous auxiliary modules, nearly unlimited other hacking related capabilities.

The new iPhone 5 was just revealed yesterday, and it's 18 percent thinner and just 1/5 the weight of its 4S predecessor. It's also taller with a larger screen, which gives you a fifth row for apps now. As far as speed is concerned, it has a speedy A6 chip and can tap into wireless 4G LTE networks for fast Internet. Both the iSight and front-facing FaceTime cameras were improved, too. The only downside seems to be the tinier "Lightning" connector, which replaces the standard 30-pin connector w...

Google is one of the most powerful forces on the Internet, and their technology can be the key to helping you find success in whatever your online endeavor might be, from web design to filmmaking. This video is a part of their Google Webmaster Series, offering help to webmasters the world over on how to best utilize Google in their work. This video will show you how to optimize your deep web content, like databases and forms, to be crawled by Google using a few simple tricks.

The browser on your Android-powered cell phone offers numerous features that enhance your overall web experience. Some of the great features include double-tapping to zoom in, searching for text on webpages, sharing websites with friends, and copying and pasting. There's a lot more, so watch this video tip from Google to see how to fully enjoy your web browser.