Join Patrick Hynds as he demonstrates how to set up the SQL Membership Provider to add Forms authentication to your ASP.NET 2.0 Web site, in this video tutorial. There are a few tips and tricks involved, such as using the aspnet_regsql.exe utility, which are covered in the video.

Here's how to access some hidden websites at the Internet Cafe in Grand Theft Auto 4 1) Go To Internet Cafe In GTA IV
Two tweaks (one for Firefox and one for Internet Explorer) to speed up your web browsing.
Learn how to export a web layout made in Photoshop and build an editable website layout in Dreamweaver, then convert the page to a template for future use and ease of editing.
One of the new technologies rolled into Adobe Illustrator CS3 is Kuler. Kuler first appeared on Adobe Labs and has become its own community where people are posting color groups left and right. Now you can not only take advantage of these color groups on the web and download them, but you can also get to them directly in Illustrator CS3.

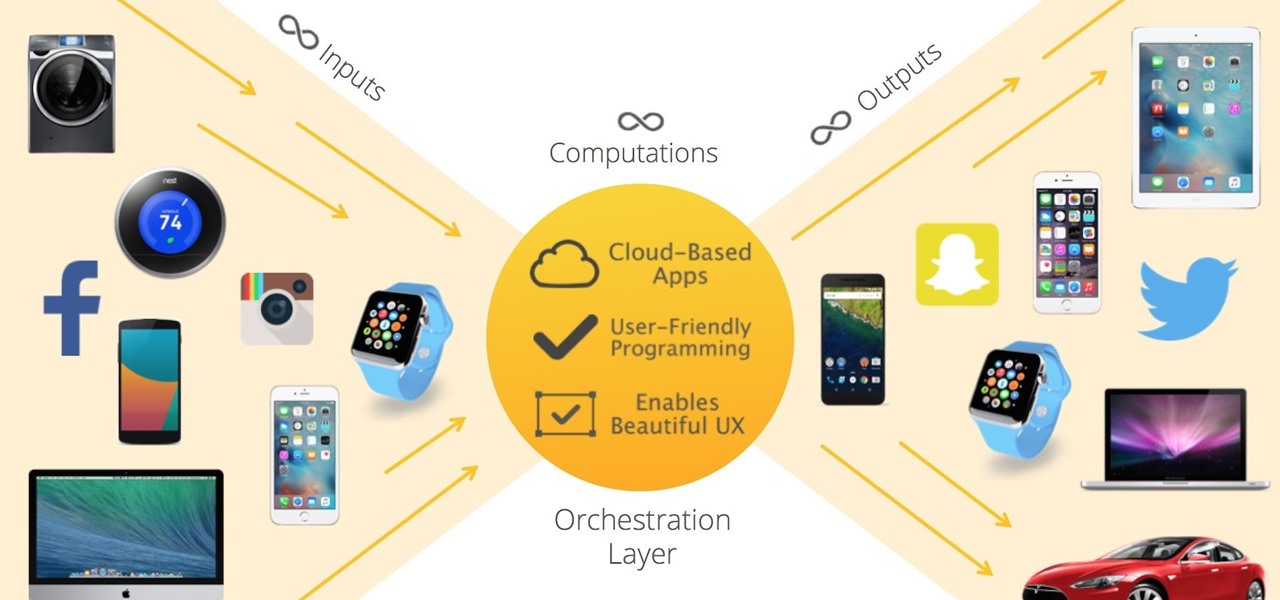
Even as we look forward to returning to work in person, the last year has changed how work can be done. That means there will always be a demand for good programmers and coders who can support the digital infrastructure of the online working world. The Backend Developer Bootcamp Bundle can give you the expertise you need to become a highly qualified programmer for only $29.99.

SEO is the name of the game. If you want your business or brand to succeed, ranking on the front page of Google is a boon. Getting to the front page of search engines takes work, but it's not impossible when you master SEO best practices.

Hacking web applications can sometimes be challenging due to the sheer amount of moving parts they possess. At the core of these apps are HTTP requests and parameters, but these things are often concealed from the user, due to security reasons, convenience, or both. However, a tool called Arjun can be used to discover hidden HTTP parameters in web apps.

Being stuck inside for the near future is less than ideal, but at least you have the world of eLearning to sharpen your skills while you kick back on your couch. Case in point, The 2020 Premium Learn To Code Certification Bundle has all the training you need to start coding like a pro right at home, and it'll only cost you $39 today.

It's OK to want an extended break when you're working or learning from home. Maybe you want to play a video game, spend more time with your family, hang out with your dog, or FaceTime with friends. But how can you do that when you're supposed to be in a Zoom video conference or class? Thanks to one Zoom feature on your iPhone, it may be easier than you think.

Whether you were exposed to the COVID-19 virus or just taking precautionary measures, self-quarantining is a tremendous disruption for anyone. Still, we all have to eat, pandemic or not. But unless you like eating canned food for two weeks, you're going to want to explore other options. That's why food delivery apps are going to be so necessary during such a hectic and uncertain time.

Filmed in what appears to be a single continuous shot, war film 1917 is now the front-runner to conquer the Best Picture category of the Academy Awards after bringing home the Golden Globe for Best Motion Picture in the drama category.

What better band than Pink Floyd, the pioneers of psychedelic and progressive rock, to show the music industry how to reinvent album art for the augmented reality age?

Web application firewalls are one of the strongest defenses a web app has, but they can be vulnerable if the firewall version used is known to an attacker. Understanding which firewall a target is using can be the first step to a hacker discovering how to get past it — and what defenses are in place on a target. And the tools Wafw00f and Nmap make fingerprinting firewalls easy.

As demonstrated by holographic experiences for the Microsoft HoloLens and the Magic Leap One, volumetric video capture is a key component of enabling the more realistic augmented reality experiences of the future.

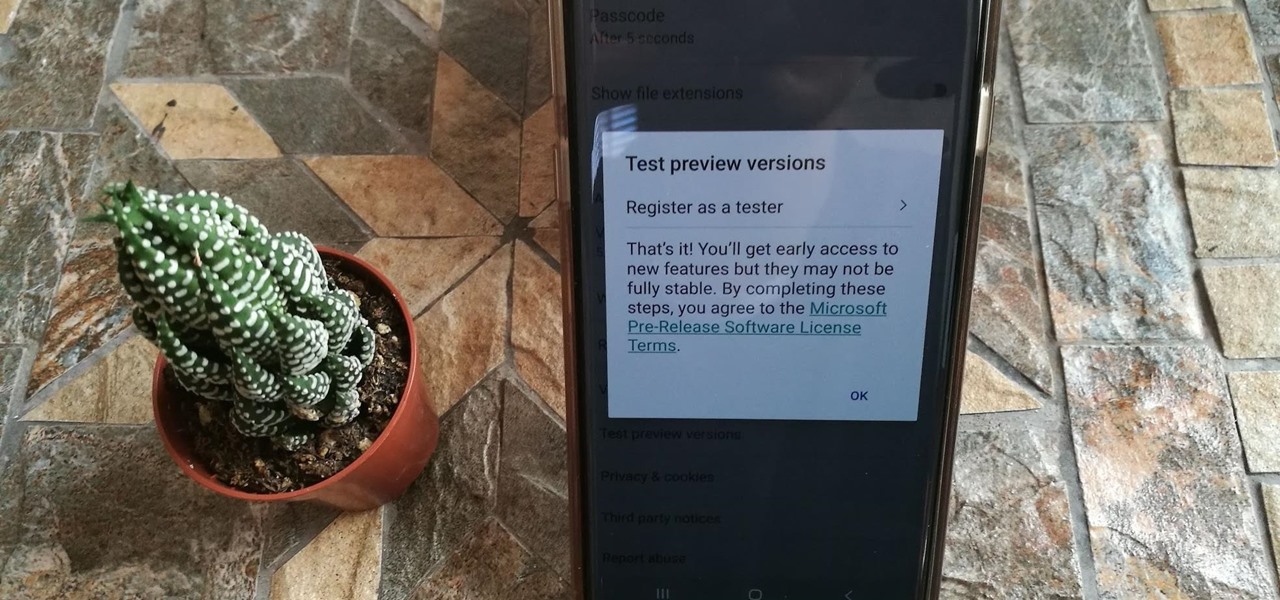
OneDrive has some really cool features, like being able to lock your files with a fingerprint. If you want to be on the forefront of these new features, you can sign up to the OneDrive beta testing program to get new feature before anyone else.

Automating port scanners, directory crawlers, and reconnaissance tools can be complicated for beginners just getting started with Kali Linux. Sparta solves this problem with an easy-to-use graphical interface designed to simplify a penetration tester's tasks.

Augmented reality platform maker Zappar and its marker-based augmented reality technology have been around well before Apple and Google brought markerless AR to mobile apps.

Auditing websites and discovering vulnerabilities can be a challenge. With RapidScan and UserLAnd combined, anyone with an unrooted Android phone can start hacking websites with a few simple commands.

If you've ever wanted to barge into Jerry Seinfeld's apartment like Cosmo Kramer, you can now do so without having to book a ride on the Peterman Reality Tour.

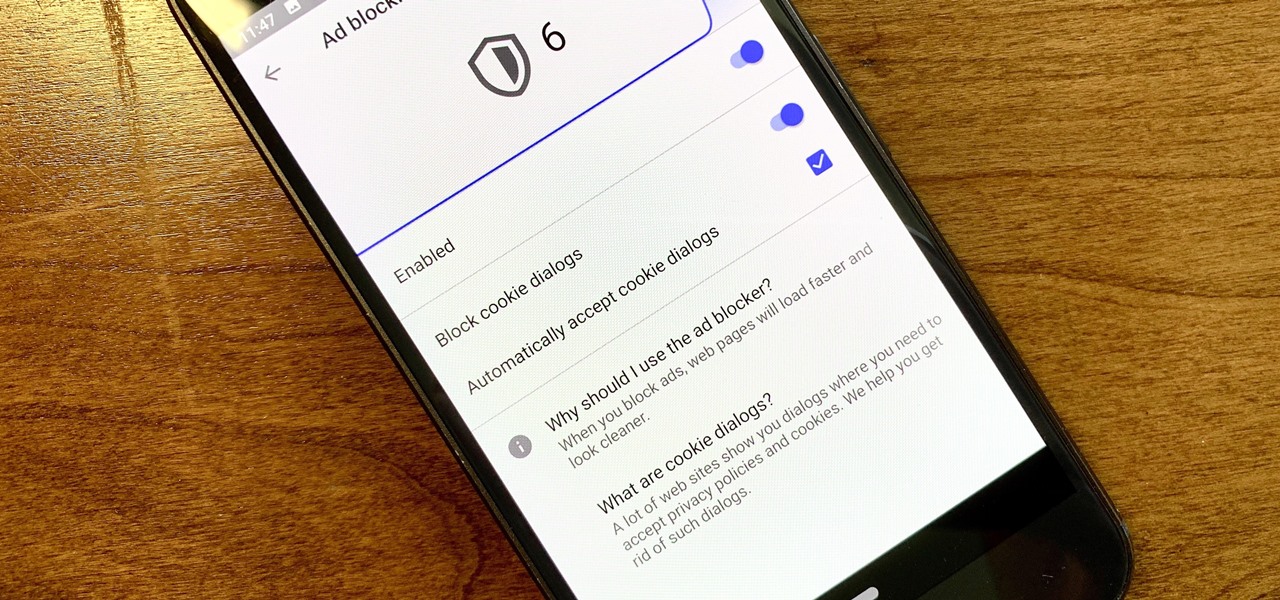
Ever since the GDPR was implemented, it seems every website on the internet needs to inform you of how its privacy policies have changed. If your web browsing experience has been marred by a constant barrage of these cookie pop-ups and privacy dialogs, you should know there's an easy way to block these web annoyances so you never have to tap another checkbox or accept button again.

It only takes a few commands to manipulate a MacBook's secure HTTPS traffic and pluck login passwords out of the encrypted data. Let's take Facebook and Gmail hacking to the next level by intercepting Safari and Google Chrome web traffic in real time.

Transferring hundreds of screenshots, webcam recordings, keystroke logs, and audio recordings between your VPS and a local Kali machine can be tricky. Services like Dropbox don't always have the best privacy policies and suffer data breaches just like any other website. To mitigate these risks, we'll use a secure, open source, and decentralized alternative.

With all the web applications out on the internet today, and especially the ones built and configured by novices, it's easy to find vulnerabilities. Some are more perilous than others, but the consequences of even the slightest breach can be tremendous in the hands of a skilled hacker. Directory traversal is a relatively simple attack but can be used to expose sensitive information on a server.

Developers can now publish augmented reality experiences that are viewable through the experimental version of Chrome and ARCore.

Consumers are chomping at the bit for augmented reality smartglasses from Cupertino's finest, but one market analyst is saying not so fast, Apple fans. Meanwhile, automotive AR is gaining speed, with the latest milestone coming courtesy of a major investment in waveguides by Continental. And although mobile AR apps have already arrived, retailer Target is taking a different approach. So why is Target tinkering with web-based AR? Answers below...

With its recent acquisition of 3D gaming engine PlayCanvas, Snapchat parent Snap, Inc. appears to be preparing a challenge to the existing players in the world of game development, particularly in terms of augmented and virtual reality gaming.

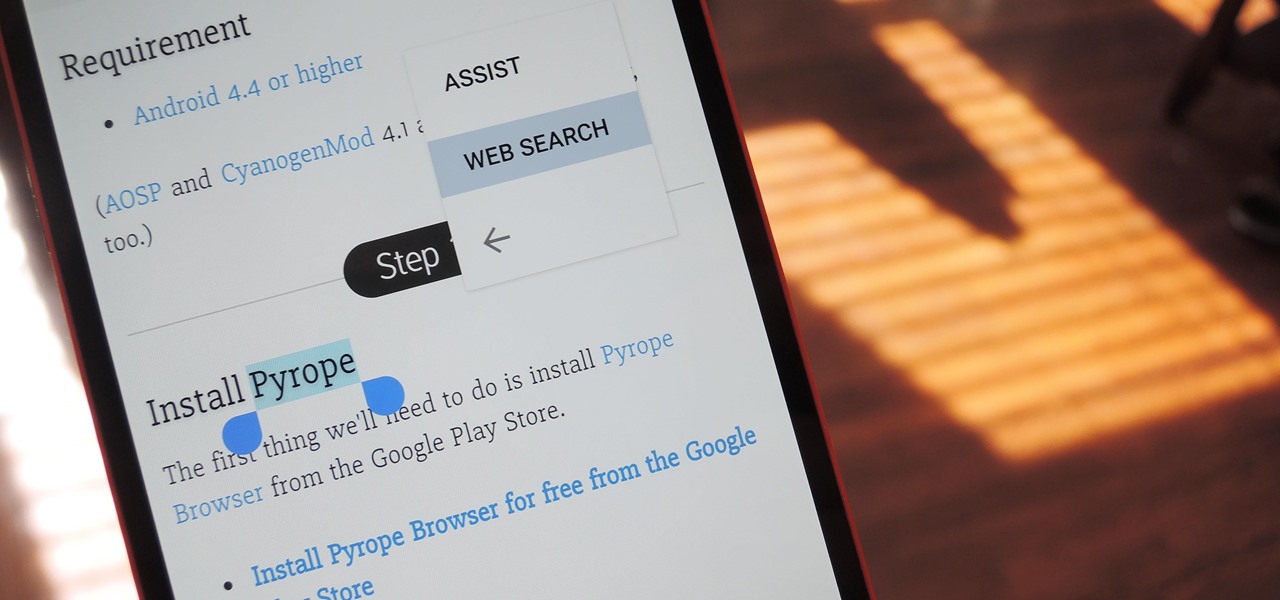
Chrome's text selection interface is pretty nice, but it could definitely use some improvements. For instance, when you're in Incognito Mode, you can't perform a web search for words you've highlighted. And when you're typing out a forum post or using any text input field, for that matter, there's no option to search or share any of the text you've written.

Mixed reality can give you the feeling that you've uncovered a hidden world layered into the physical one you already know. This can happen in so many ways, from a trading card that births a hologram or a first-person shooter with robots blasting through your walls. Xperiel—a California-based augmented and mixed reality company—wants to create a platform to make that a whole lot easier for developers.

Google is reportedly working on an iOS keyboard that brings key features to the iPhone, including Google's image and text search functions. (GIFs, yay!) According to The Verge, the keyboard has been in development and testing for months, and will act much like the Android version.

This Video is about my Trying a New Braid pattern for a Crochet Weave.

Welcome back, my hacker novitiates! Often, to hack a website, we need to connect to and exploit a particular object within said website. It might be an admin panel or a subdirectory that is vulnerable to attack. The key, of course, is to find these objects, as they may be hidden.

I will Show you in this Video How I dust my Ends... PLEASE NOTE:

This Video will show you How to Do Two Strand Twist. I had been practicing looking at different YouTube Videos

Welcome back everyone. As many of you know, reconnaissance is extremely important in any successful hack. Without proper reconnaissance, we won't know what we're about to get into, literally.
Have you ever used an open wifi, which after you connect displays a website to enter your credentials to get internet? That website is called captive portal and widely used in airports, hotels, universities etc. Have you ever wondered what would happen if someone would set up an open wifi with the same name displaying a very similar web page asking for credentials? Usually if there are multiple wifi networks with the same name and encryption, devices only display the one with the highest sign...

This is My Review of the Electric Hair Brush Straightener LCD Iron Brush. I have had a Bad Experience please Watch this Video for more info!

Hello, my web huggers! In today's tutorial we will learn how to use the Google Hacking Database (GHDB) developed by Exploit Database, to find vulnerable web servers and "juicy" information.

Welcome back, curious hackers! In today's tutorial, we will be diving deep into the manipulation of Google Operators, commonly referred to as "Google Dorks" in order to access Surveillance Cameras and other control panels.

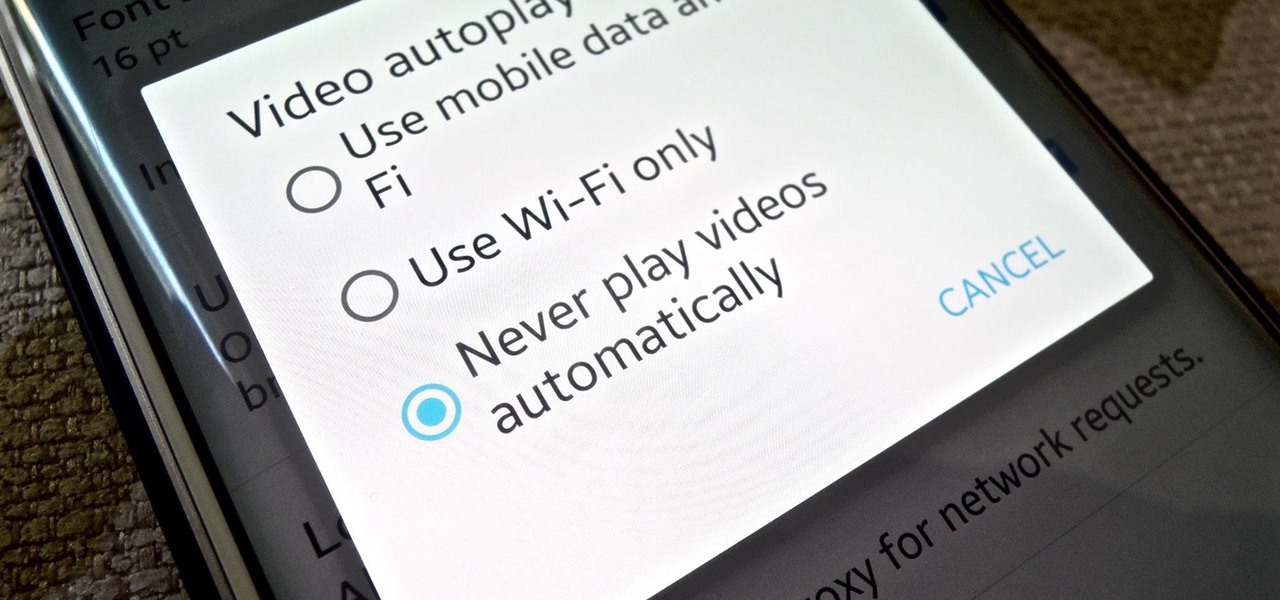
It's bad enough that we have to deal with autoplaying video advertisements all over the Web, so why do we have to be subjected to autoplaying videos on Twitter, too? Autoplay video are muted by default, but that doesn't make them any less annoying, especially if you have a small data plan on your phone.