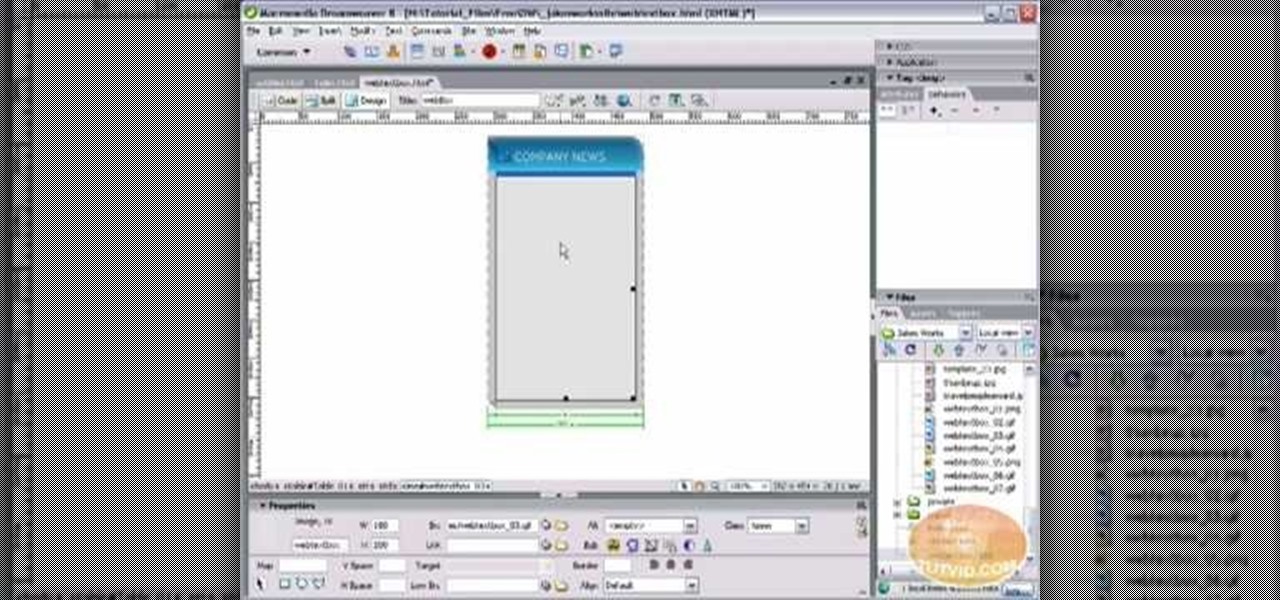
Learn how to create a web text box using Dreamweaver that get bigger or smaller depending on how much text you place in it. Also make a header that spans the users screen not matter what size.

The existing uninstall routine for the Mozilla Firefox web browser may leave profile data and a Program Files folder behind. This is how to remove it.
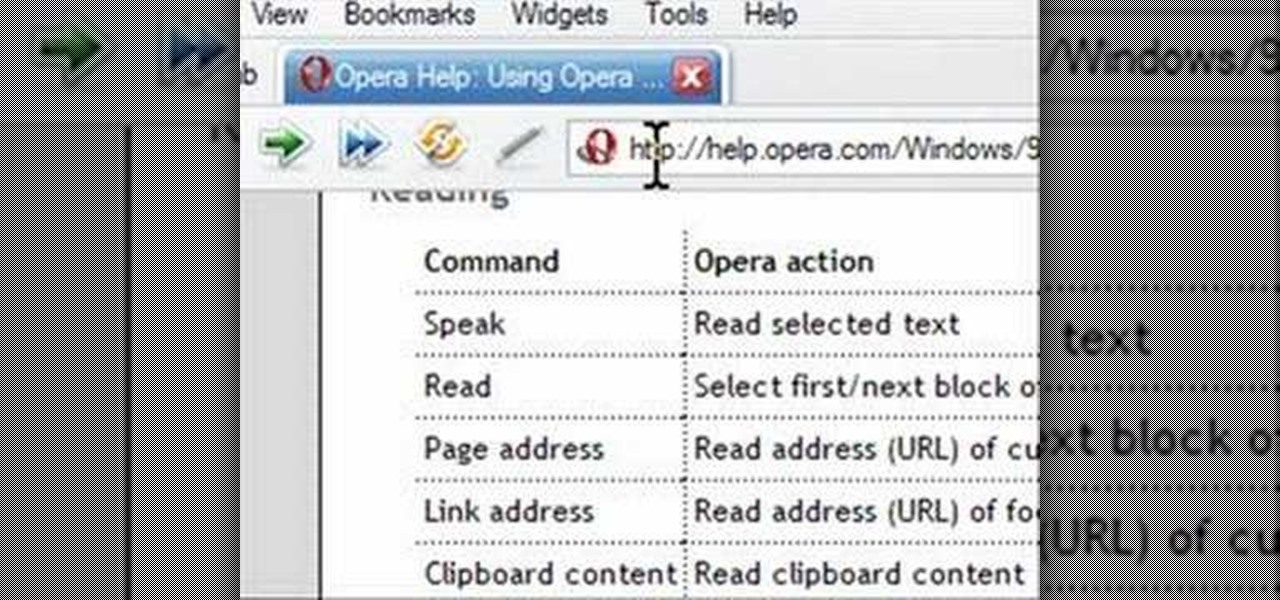
Opera has a feature where you can talk to it and it obeys your commands - and it works! No "voice training" required. Learn how to use Opera Voice.

For all you whos resolution it was to start making your own clothes and DIY'in, this week were taking a look inside the mysteries of the sewing machine plus a look at our 2008 top DIY web picks.

Backpacker magazine shows you how to build a plastic footprint for your tent--a skill taken from the Jan/Feb 2007 issue. Associate editor Jason Stevenson explains the nine steps to create a footprint, including how to cut webbing and punch grommets. Learn more Skills at www.backpacker.com.
Once your video is on the Web you can share it with friends and family in an instant. Learn how to export with Windows Movie Maker so the best possible version of your video is shared.

This video demonstrates how to connect a PSP to a home wireless network. To do this, just turn on your PSP, create a new network connection, and start the web browser on the PSP.

When you want to encode your video for DVD instead of for the web, there are a few extra steps you have to take. You have to split your source media into seperate streams. See how to do it in Compressor 3 in this tutorial.

Rebecca Katz explains how to export your finished project for the web using Apple iMovie. The final menu will allow you to title your film and save it to a location of your choosing.

Watch the Grillmasters at the Barbecue Web prepare some beef chuck burgers so juicy and full of flavor that it will no doubt become one of your favorite quick and easy BBQ recipes. It's quick and easy. All you need is 3-4lbs fresh ground chuck beef, tomatoes, sweet onions, sliced cheese if it's a cheeseburger you want, and any of your favorite condiments.

Trimming spare ribs into St Louis style ribs is demonstrated in this Barbecue Web video.

This video tutorial takes a look at how to create layers in Photoshop CS2 that build up to your signature. Then we'll pop over to Adobe ImageReady to put the finishing touches on animating that signature so that it can be used on the web or in your email application. Check out this Terry White's video now!

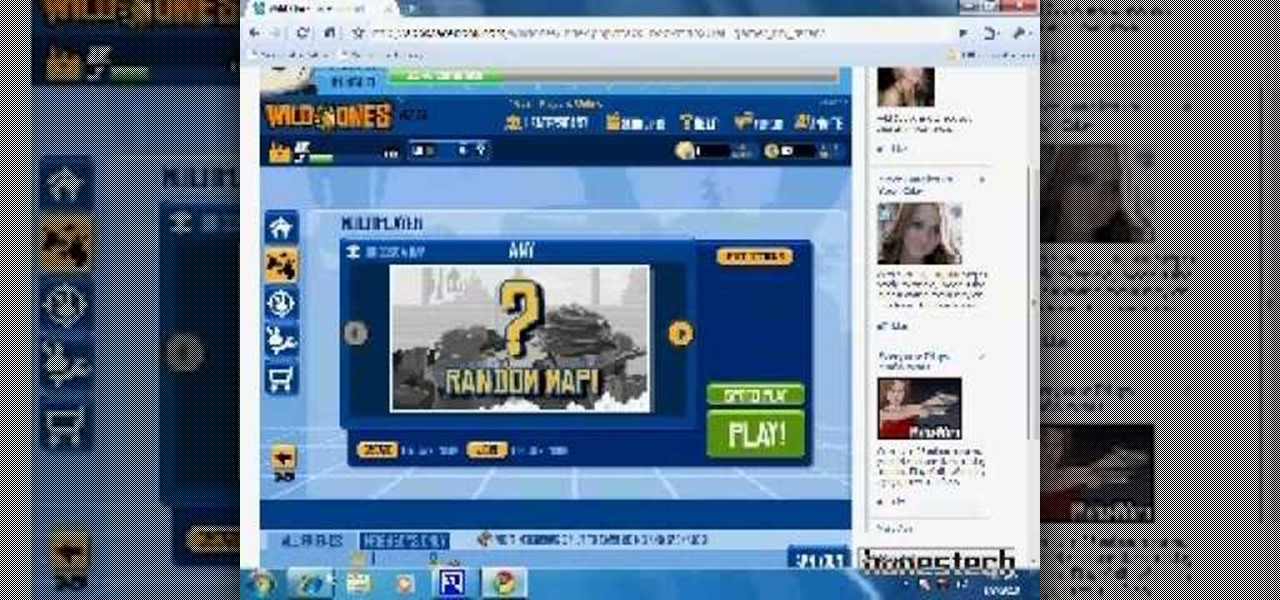
Do you find yourself getting rocked by your friends and relatives whenever you play Wild Ones on Facebook? A little more money would help right? This video will teach you how to use an easy cheat to acquire a theoretically infinite amount of money and coins. All you need are two Facebook accounts and two different web browsers and you can do this easily. Now get in there and buy yourself a better pet!

Identify pinion needle scaleWe are going to look at this insect because eggs are being laid. Two year old needles are being cast off. This is a sign of infestation. There is also sparse, open foliage. This tends to be a chronic infestation. The insect is the pinion needle scale. You can see tiny, bean shaped bumps on the 2 year old needles. The insects move to last years new growth and feast on the sap of the needle all summer. You can see egg masses and web on the trunk of the tree. The inse...

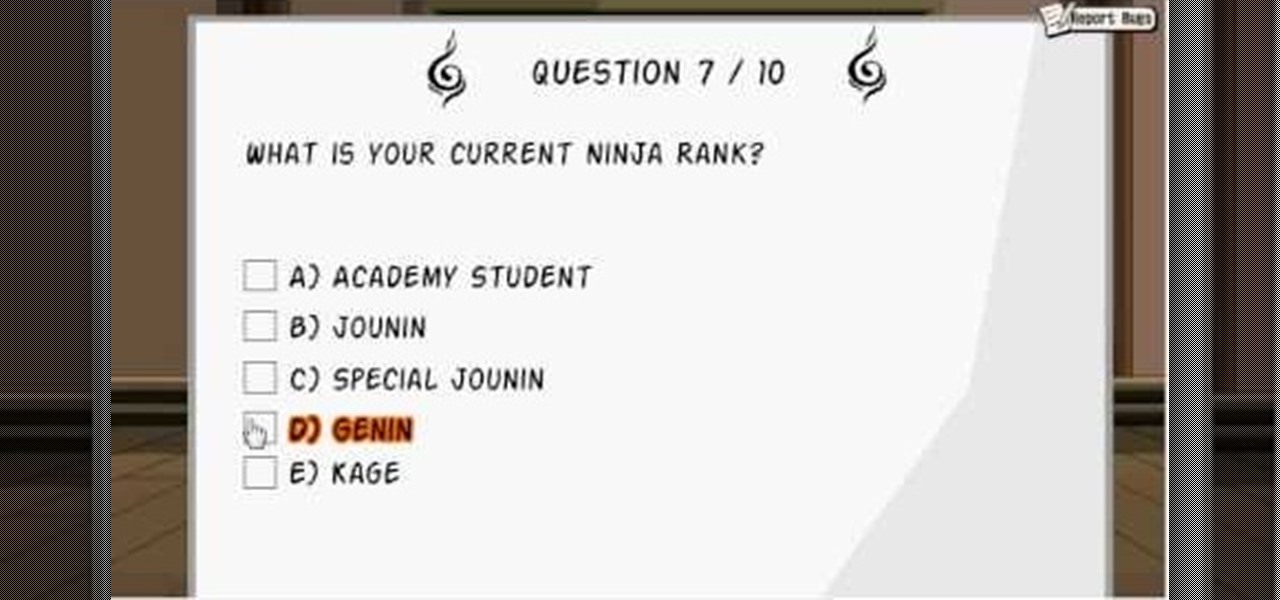
The chunin exam. It's one of the hardest parts of Ninja Saga. Can you pass the test? Or do you need a little help on this exam?

Systm is the Do It Yourself show designed for the common geek who wants to quickly and easily learn how to dive into the latest and hottest tech projects. We will help you avoid pitfalls and get your project up and running fast.

This is a great solution if you need to get something off your computer, but you are not home. Want access to your files stored at home? How about hosting a home web server? Static IPs are expensive, if you can even get one. We set up Dynamic DNS instead!

If you've been thinking about changing careers and you have just a little bit of time, The Ultimate 2021 Web Developer & Designer Super Bundle may be just what you need. This is also the perfect time to get it because it's on sale for $34.99, which is 98% off the regular price of $1,886. You'll get 14 courses that offer 39 hours of content on HTML, JavaScript, CSS, and more.

Penetration-testing frameworks can be incredibly useful since they often streamline certain processes and save time by having a lot of tools available in one place. Of course, the most popular pentesting framework is undoubtedly Metasploit, but there are many others out there that cater to particular needs. For auditing web applications and servers, Tishna comes in handy.

Web applications are a prime target for hackers, but sometimes it's not just the web apps themselves that are vulnerable. Web management interfaces should be scrutinized just as hard as the apps they manage, especially when they contain some sort of upload functionality. By exploiting a vulnerability in Apache Tomcat, a hacker can upload a backdoor and get a shell.

Smartglasses from Apple have become the holy grail of augmented reality, and 2020 has been the rumored time horizon for the product's arrival for the past two years. The latest analyst report sheds more light on its potential debut next year.

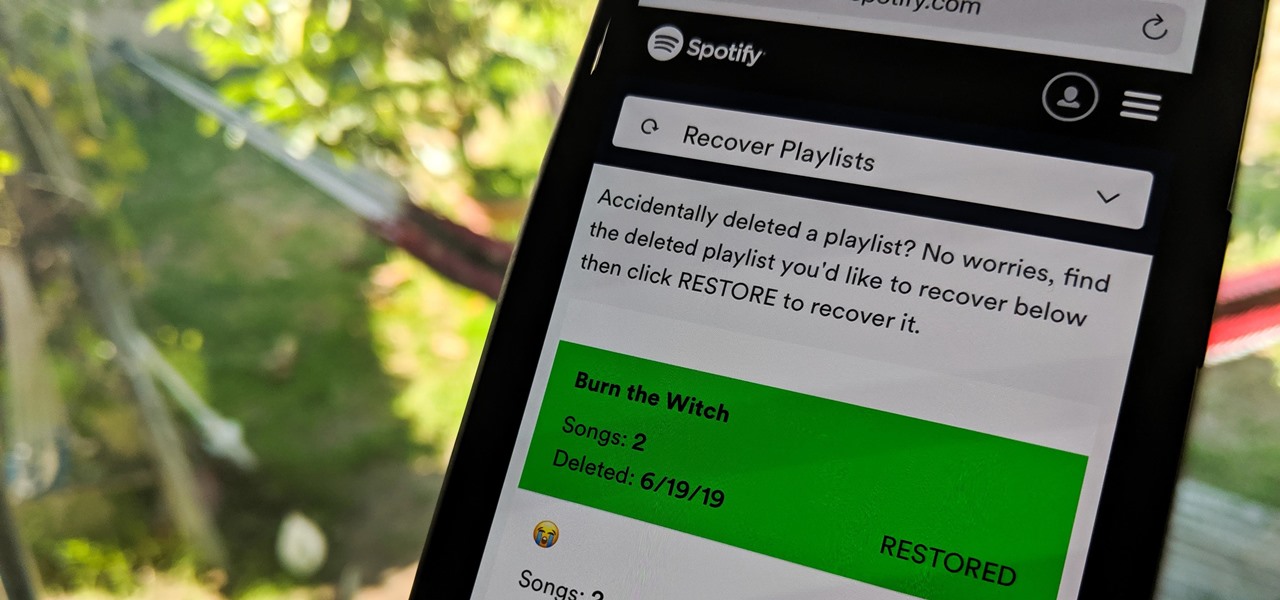
Absentmindedly or accidentally deleting your favorite Spotify playlist — which you spent hours or even days meticulously crafting — may seem devastating because there's no obvious way to bring it back. However, there is a hidden setting in the popular streaming service that can help you recover deleted playlists — you just need to know where to look.

Websites and web applications power the internet as we know it, representing a juicy target for any hacker or red team. TIDoS is a framework of modules brought together for their usefulness in hacking web apps, organized into a common sense workflow. With an impressive array of active and passive OSINT modules, TIDoS has the right instrument for any web app audit.

Nearly a year to the day after the unveiling Magic Leap One, Magic Leap has dropped another update to the Lumin OS that runs the device.

A simple security flaw can allow an attacker to gain a strong foothold with little effort on their part. When a web application permits remotely hosted files to be loaded without any validation, a whole can of worms is opened up, with consequences ranging from simple website defacement to full-on code execution. For this reason, RFI can be a promising path to obtaining a shell.

Yesterday, I talked about what I think is the most immediately mainstream-friendly app on the Magic Leap One is (Screens), and now we'll touch upon the runner-up: Helio.

Command injection is a technique used by hackers to execute system commands on a server, usually via a web application or some kind of GUI. This can happen when an application provides some sort of functionality to the user involving the use of system commands. When the input is not properly sanitized, commands not originally intended to be run are allowed to be executed.

Electronics maker Epson is courting developers to its Moverio smartglasses with an updated software development kit (SDK) and integration with a web-based tool for publishing augmented reality experiences.

Facebook, parent company of Instagram, has allowed you to download photos and other account data for some time now, but the data request feature is also now available on Instagram to meet the GDPR data portability requirement in the EU — and it's available worldwide, not just in Europe.

The latest cosmetics brand to launch its own augmented reality try-on tool is Cover Girl, which introduced its browser-based experience this week.

There are over 3 million apps in the Google Play Store, all optimized for the small screen in your hands. While that number sounds staggering, there are still many online tools and websites that require you to use a mobile browser since app development is expensive. However, that's where Progressive Web Apps (PWAs) come into play, a cost-effective way to turn websites into mobile apps.

During its third-quarter earnings call, Apple CEO Tim Cook said that "AR is going to change everything."

JavaScript is one of the most common languages used on the web. It can automate and animate website components, manage website content, and carry out many other useful functions from within a webpage. The scripting language also has many functions which can be used for malicious purposes, including stealing a user's cookies containing passwords and other information.

Before the release of the Galaxy S8, Samsung quietly uploaded one of their core TouchWiz apps to the Google Play Store as a beta. Samsung Internet, as it's called, has been a staple on all Galaxy devices for years now, but you can now try the browser on any Android phone.

Chrome apps and extensions are powerful tools for students: they can help optimize your web browsing experience by helping you take notes, check your grammar as you compose documents and emails, and even help you squeeze a little more juice out of your laptop's battery by freezing unused tabs and optimizing YouTube streams.

Hi guys, I'm gonna keep this short because I got assignments and a lot of notes to study and also other how-tos and forums to reads. lol...Since I'm keeping this short...no story time just scenario. And I want to thank n3stor for giving me the idea to post this.

Being an Google fanboy means that I pretty much use anything with the company puts out, so it's no surprise that out of all the cloud services out there, I stick with Google Drive. But, this is way more than just some blind allegiance.

When it comes to antivirus software, you don't want some fly-by-night developer having access to the sensitive data that these apps can scan. Luckily, most of the longest-tenured antivirus companies from the realm of desktop computers offer complete security suites for Android these days.

NOTICE: Ciuffy will be answering questions related to my articles on my behalf as I am very busy. Hope You Have Fun !!!

When Google Play Music launched a few years ago, I ditched iTunes and began using the service as my one and only source for listening to my personal music library. While All Access is great, I still prefer the radio feature on Spotify, so I still use that to discover new music.