The future of smartglasses for consumers seems ever dependent on Apple's entry into the market. Coincidentally, the exit of Apple's long-time design chief Jony Ive has shed some light on that eventual entrance.

The next libSSH or OpenSSH exploit may be just around the corner. Keep your SSH service out of Shodan's database before hackers find new ways to bypass the password protecting the server.
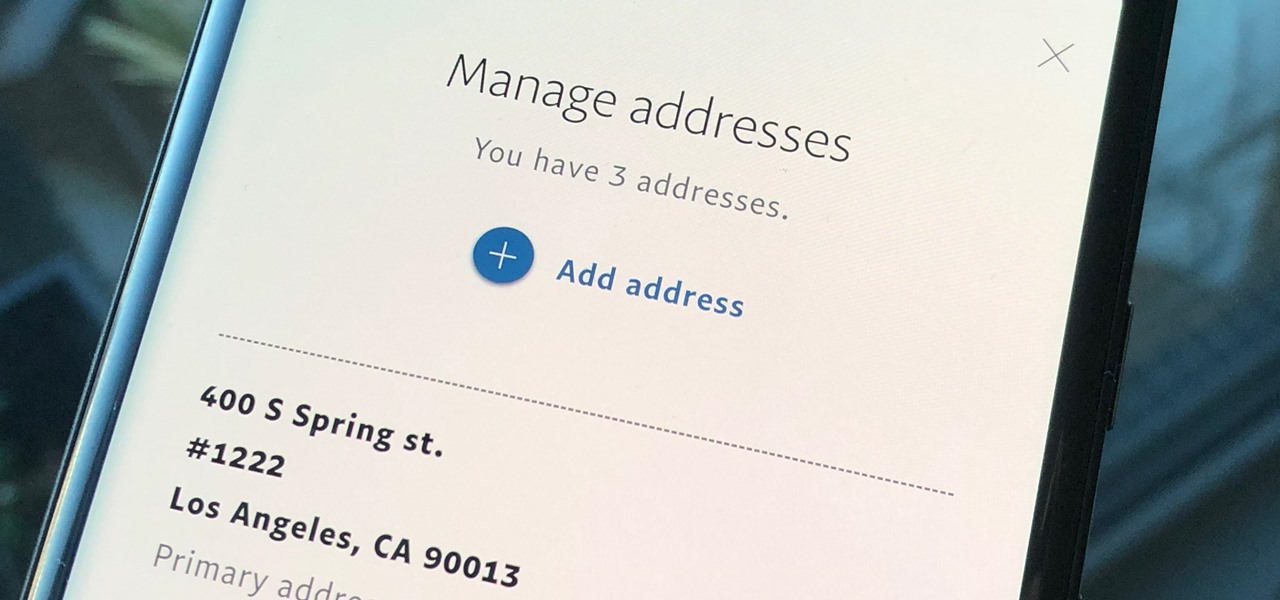
Whenever you move into a new home, whether that's a house or apartment, changing addresses on all your online accounts is one of the most monotonous tasks that needs to be done. It's even more tedious when you have to update both shipping and billing addresses. But it's necessary, and if you regularly use PayPal, it'll be one of the first places you'll want to update.

Websites are often misconfigured in ways that allow an attacker to view directories that are not ordinarily meant to be seen. These directories can contain sensitive information such as private credentials or configuration files that can be used to devise an attack against the server. With a tool called Websploit, hackers can scan targets for these hidden directories without difficulty.

This week, the recurring theme in augmented reality can be summed up fairly succinctly: content is king.

The macOS 10.14 security update tried to make parts of the operating system difficult for hackers to access. Let's take a closer look at how its new feature works and what we can do to spoof the origin of an application attempting to access protected data.

This week, we continued our NR30 series highlighting the leaders of augmented reality space by profiling the venture capitalists and strategic corporate investors that sustain the industry.

Hackers rely on good data to be able to pull off an attack, and reconnaissance is the stage of the hack in which they must learn as much as they can to devise a plan of action. Technical details are a critical component of this picture, and with OSINT tools like Maltego, a single domain name is everything you need to fingerprint the tech details of an organization from IP address to AS number.

Identifying vulnerable devices and services on a target router can be difficult without leaving logs and other traces of an active attacker on the network. However, there is a way to covertly decrypt and view Wi-Fi activity without ever connecting to the wireless network.

OnePlus has now officially upgraded both the 5 and 5T to Android 8.1 Oreo. As implied by the version number, this isn't a huge update from Android 8.0 Oreo. However, OnePlus has included a few of their own features as well.

While iOS 11.3 doesn't have as many new features as iOS 11.2, there's still a lot to love about Apple's latest update for iPad, iPhone, and iPod touch, even if some of the best features we were expecting didn't make the cut.

While IKEA is collaborating with Apple for its ARKit furniture app, Marxent is ready to help the rest of the interior decorating and home improvement crowd with their apps.

In order for software developers to do their jobs as new hardware reaches the market, they will need the right tools to get their projects off the ground and into augmented and mixed reality devices. There have been completely new approaches to development when it comes to AR and MR, and these are some of the faces behind them.

If you purchased something from iTunes, the iOS App Store, iBooks Store, Apple TV App Store, or the Mac App Store and it doesn't work, didn't download, is buggy, or wasn't what you thought it was, you can get a full refund from Apple—you just have to know how to ask.

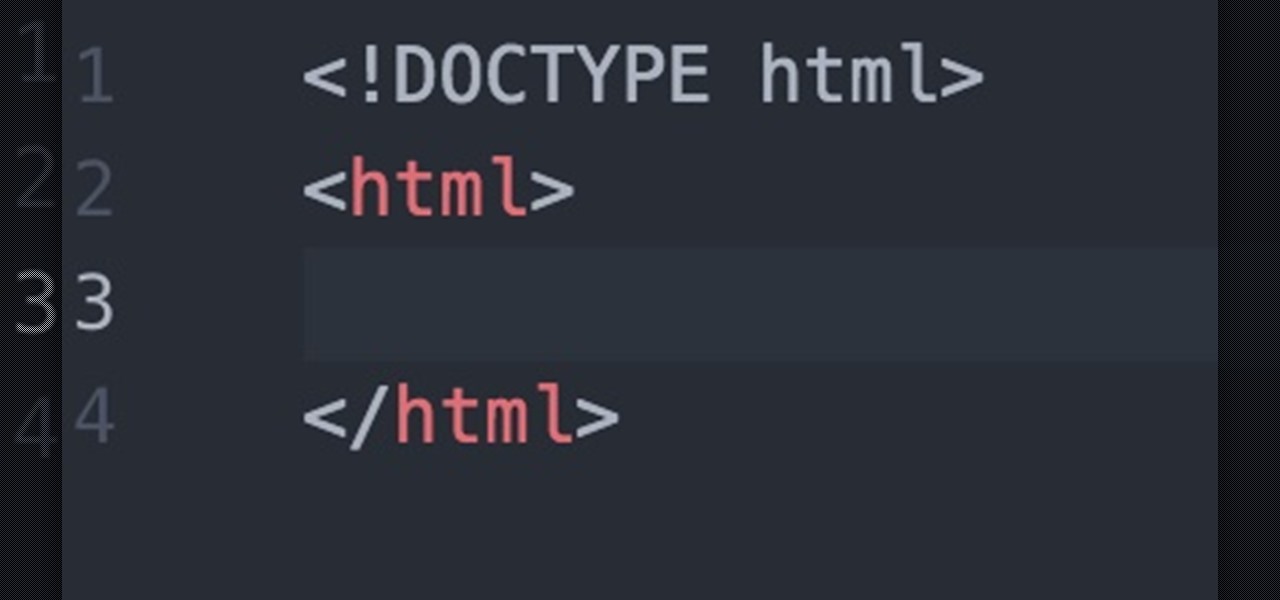
Hello fellow Null-Byters! In this "tutorial" we will be going basics of HTML. In the next tutorial, we will be going over CSS and then apply JavaScript.

Welcome back, my greenhorn hackers! Throughout this series on Metasploit, and in most of my hacking tutorials here on Null Byte that use Metasploit (there are many; type "metasploit" into the search bar and you will find dozens), I have focused primarily on just two types of modules: exploits and payloads. Remember, Metasploit has six types of modules:

It would only make sense that Google is one of the most active app developers on the Android platform, particularly when you consider that they develop the platform itself. From my count, there are an astounding 117 unique apps that the search giant and its subsidiaries have published on the Google Play Store.

We are most certainly not machines. We all need some downtime every once in a while to set our sanity scales back in balance, which in turn, makes us more productive workers. This is a premise that several forward-thinking employers fully understand, but these types of companies are few and far between in corporate America.

There are tons of greasy drippings that can be used to flavor up any dish, but none will ever be more delicious than animal fat. The bigger and fatter the animal, the juicier and tastier their fat is. For those of you who have had your fill of bacon-anything, here's your next obsession. It's called caul and its very existence will divide those that are serious about their animal fat flavoring from the pretenders.

Welcome back, my amateur hackers! Over the course of the next year, we will be developing our own zero-day exploits. In my first article in this series, I introduced you to buffer overflows, which are the source of some of the most lethal exploits, particularly the "remote code execution," so we are focusing our exploit development here on a buffer overflow.

With its growing popularity, it's clear that the Chromecast isn't going away anytime soon, with options for casting games, cloud files, music, and much more. But not all content providers are in a hurry to add support for the device, and SoundCloud is one of them. While My Cloud Player is by no means an official SoundCloud app, it comes pretty darn close.

This time it's serious. Really. The largest web security vulnerability of all time went public on Monday, April 7th, 2014, resulting in widespread panic throughout the Internet as system administrators scrambled to secure their websites from the OpenSSL bug known as Heartbleed.

Welcome back, my greenhorn hackers! In a previous tutorial on hacking databases, I showed you how to find online databases and then how to enumerate the databases, tables, and columns. In this guide, we'll now exfiltrate, extract, remove—whatever term you prefer—the data from an online database.

While Siri has never been my favorite, after using her in the new iOS 7, I have definitely become a fan. If you want to know why, check out the newest cool features that Siri has to offer!

Google Reader is soon to be no more. Yesterday, the company announced that the service will be shutting down as of July 1, 2013, as part of Google's second "Spring Cleaning."

Our attention spans have vastly shortened thanks to the Internet and our subsequent procurement of information from it at a rapid pace. It's tough to pay attention to something for a good amount of time, unless it's ridiculously interesting and stimulating. It's gotten so bad for me that I keep checking my phone every ten minutes—I even did it during a midnight showing of The Dark Knight Rises.

Not everything that Facebook does is in the best interest of its users. Just look at past examples such as social ads, facial recognition, and instant personalization. Users were perfectly fine without these, and they still are. And now there's another annoying problem that Facebook users have to deal with—the ticker.

Autodesk Maya, affectionately known as just Maya to its users, is a 3D computer graphics software that makes it easy to create impressive, realistic models of real-life - or imagined - objects. Super useful for graphic designers, film makers and web designers, the program is one that you should study if you're looking to go into one of the fields above.

Last weekend, some unlucky Gmail users inadvertently had their email accounts wiped out. Actually, it was 0.02 percent of all Gmail users—or roughly 40,000 of the 200 million who use the email service, due to an "unexpected bug" which affected copies of the data. Gmail does make backup files of everything, so eventually everyone will reclaim their email history. In fact, as of yesterday, Google has successfully restored all information from their backup tapes and has started returning everyon...

If you didn't know already, December 5th, which is today, is the Day of the Ninja. It's an unofficial holiday where people across the world dress like a ninja, engage in ninja-related activities and spread information about ninjutsu online. But for web-gamers, the Day of the Ninja is the best time of year to get some Ninja Saga action in.

Before there was digital music and fancy computers and music software, people use to employ the power of the electric color organ (now more commonly known as the "light organ") to add some visuals in sync with their music. MAKE shows you how to build your own sound-to-like circuit— your very own light organ!

If you're a filmmaker or graphic designer, you need a good way to present your work, and in today's age, you need a website portfolio. But really, anyone in the visual arts could benefit form a web portfolio, and the easiest way to make on is in WordPress. This video series will guide you through setting up a WordPress site using pages to create a portfolio website.

In order to access blocked videos and websites, you will need to set up a proxy service in the U.S., if you are trying to use Hulu. Go to a list site.

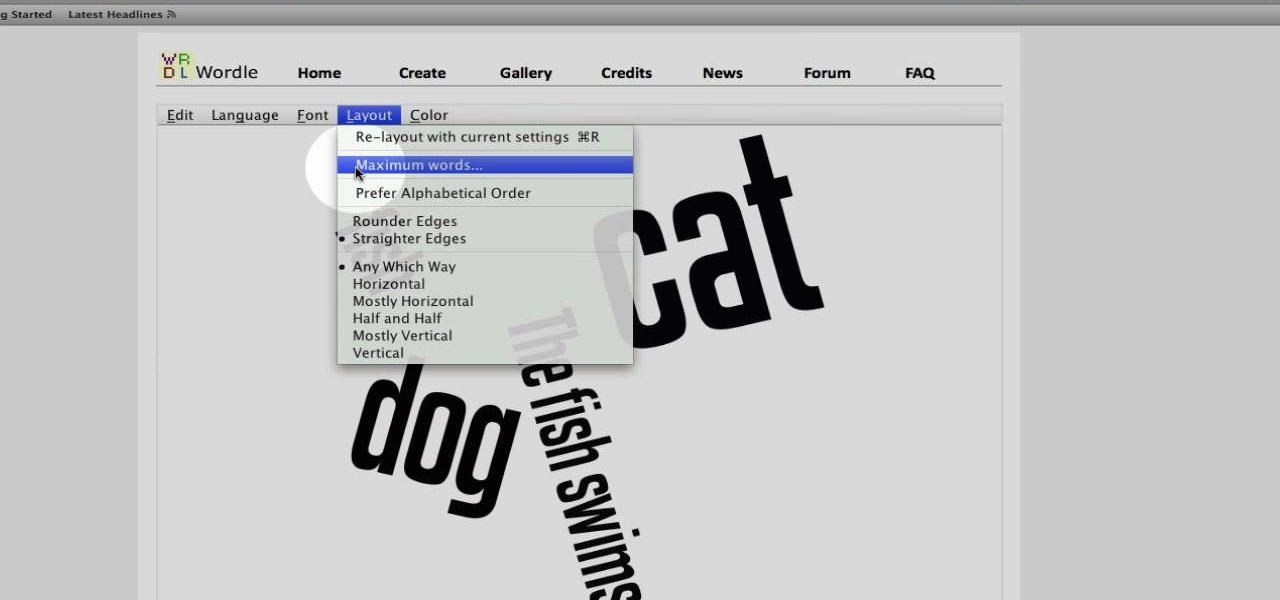
This video tutorial belongs to the Computers & Programming category which is going to show you how to use Wordle to create word clouds. Go to Wordle and click on the 'create your own' link. In the first box, type in your text, and in the second box enter the URL of any blog, blog feed or any other web page that has an Atom or RSS feed. In the 3rd box enter your del.icio.us username, if you have one. After typing in, hit 'go' and you get your Wordle file with the words written in different sty...

In this video tutorial, viewers learn how to clear their cache in Internet Explorer. Begin by opening the web browser. Then click on Tools from the top menu and select Internet Options. In the General tab under Browsing History, click on Delete. When the Delete Browsing History window opens, click on Delete Cookies and click OK. To automatically clear cookies, click on Settings under Browsing History and check Every time I visit the web page. Then finish by clicking OK. This video will benefi...

Scrabble isn't just for playing Scrabble anymore— there's a whole world of uses for the game and its pieces. One particular use is in jewelry— those Scrabble letter tiles are the perfect size for creating DIY pendants!

St. Valentine's Day is coming up soon in February, but do you have a special outfit planned for that special someone? Well, even if you don't have a valentine, this tattered heart black shirt will show the world you care. See how to make a tattered heart Valentine's Day T-shirt in this video from GiannyL.

One of the most important things in a person's life is sleep (some of us don't get enough of it, and some of us get too much). Why not make it one of the most comfortable things, too? Having the right sleeping attire is great for comfort, especially when you make them custom yourself. See how to make pajama tank top in this video from GiannyL.

Sleep is one of the most important things in a person's life. So why not make it one of the most comfortable things, too? Having the right sleeping attire is great for comfort, especially when you make them custom yourself. See how to make pajama pants in this video from GiannyL.

You can add USB ports to your PS3 at home. Put two new ports onto the back of your PS3 for a total of six ports to get even more out of your machine. You will need a basic knowledge of circuitry and some electrician equipment to do this the right way. This video will show you how to add USB ports to your PS3. Keep in mind that this video does not show you how to reassemble it so be sure to keep track of your work.