Looking for ways to hack your favorite games without having to take the risks of Cheat Engine? This video shows you how you can hack the web game Swords and Sandals 2 without having to rely on any program at all.

Cheat Engine is a free program that you can use to hack into nearly any Flash game on the web. It's recommended you have these games running in Firefox. Then open up Cheat Engine when the game is running, and hack away!

When you load Firefox, you're automatically taken to whatever homepage you've set up, or the automatic homepage. But what if you wanted to make a couple home pages? How about three or four? Well, you can, and this video will outline the process of setting up multiple home pages in Mozilla Firefox.

Have you zoomed way in to read a poorly-made webpage in the browser on your Mac and left yourself with no idea how to return the page to normal size? This video will tell you that all you need to do is hit Apple-0 and you're set.
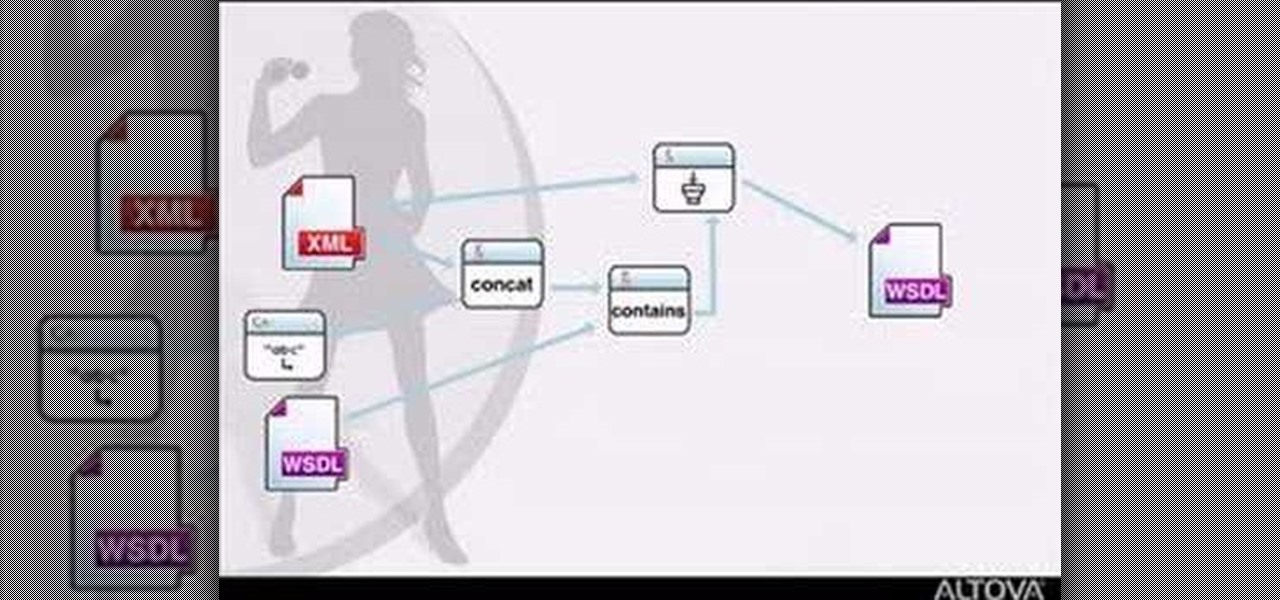
MapForce supports XML, databases, flat files, EDI and web services as the source and target of any mapping. In this tutorial, you'll take a look at how to use the different data sources available in MapForce.
We look at a nice and easy to use software on a modified Firefox browser where you can surf anonymous via the tor network.

Watch this video to learn how to make annotations in your YouTube videos. This adds a level of interactivity to your web videos that was not previously possible.

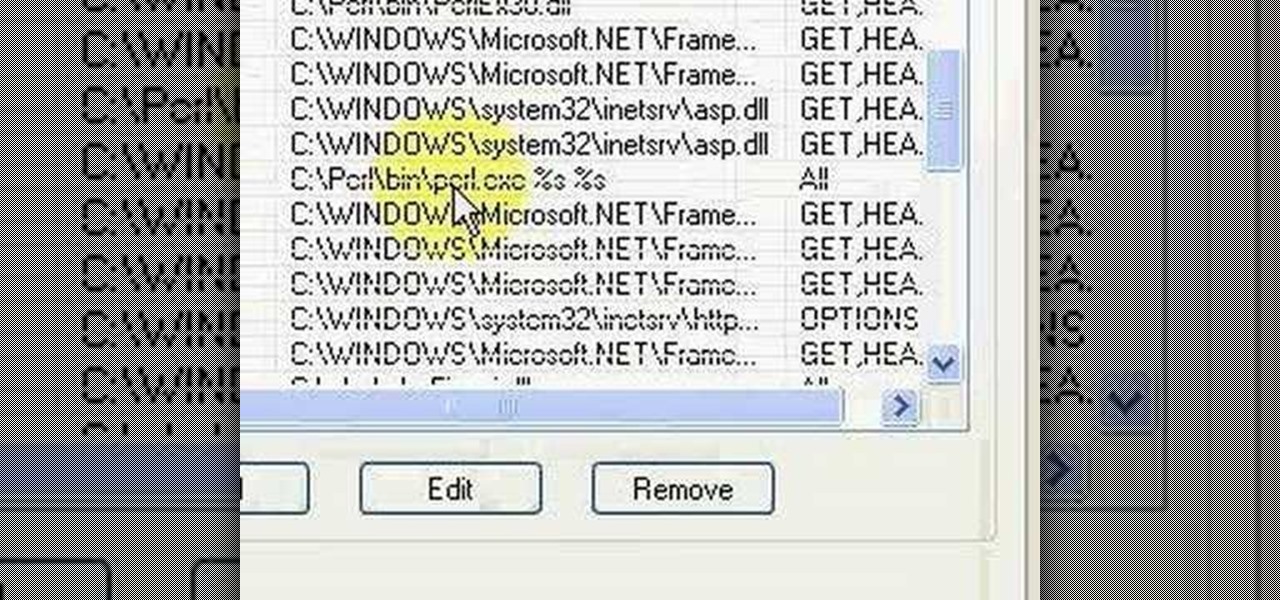
Brief 9-minute video demonstrates running "Hello World" Perl script on IIS and Apache Web Servers.

In this video you will see how to select from the various web hosting options to host a domain at GoDaddy.

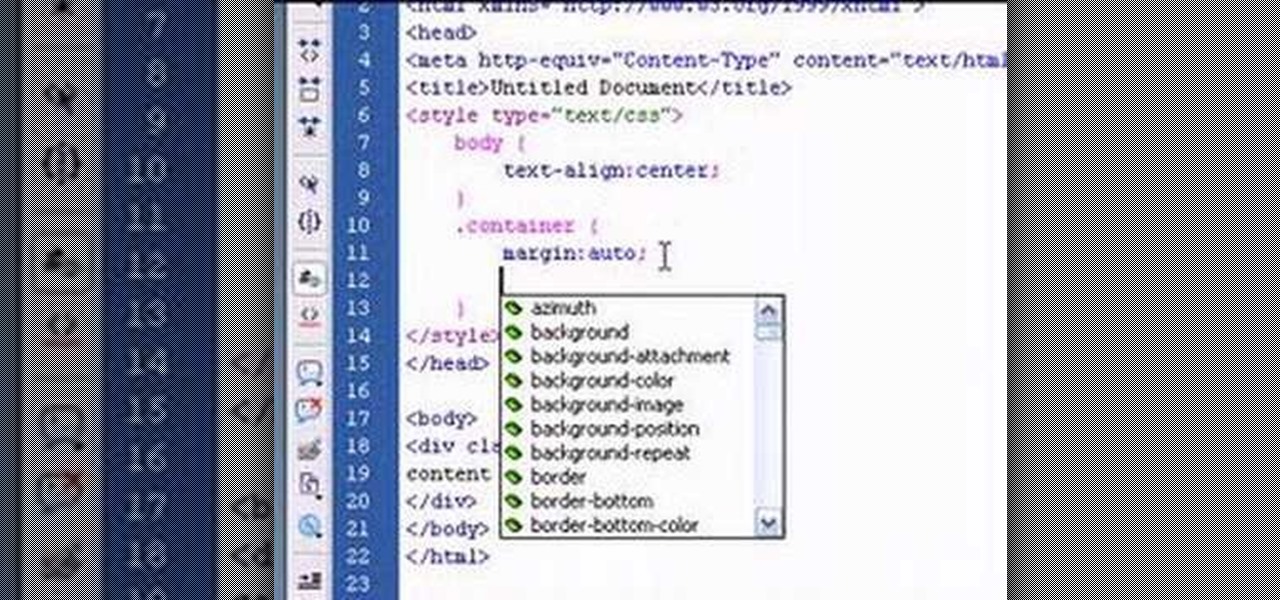
This tutorial will teach you how to horizontally center HTML elements on a web page using Adobe Dreamweaver.

The video is an episode of Indy Mogul. It opens with a man who tells us the topic of this show is to help people make fake prosthetics for a fish-man costume for Halloween. After an intro showing us that the show is about making homemade special effects and props on a cheap budget and a disclaimer the show tells us the ingredients we'll need to make the prosthetics. They are: clay, sunglasses, latex sheet, quarter-inch foam, styrofoam head and bald cap, and liquid latex. The show then demonst...

There are two types of people in this world: those who recognize Wordle grids of yellow, green, and gray/black blocks and those who do not. No matter which category you fall in, there's a Wordle-inspired game that's perfect for you.

Instead of responding to a WhatsApp message with short texts like "LOL" or thinking too hard about something meaningful to say, use an emoji reaction. They cut down on clutter in group chats and take up less space than typing emoji individually in a conversation. WhatsApp initially limited reactions to just six emoji, but a new update lets you use any emoji you want.

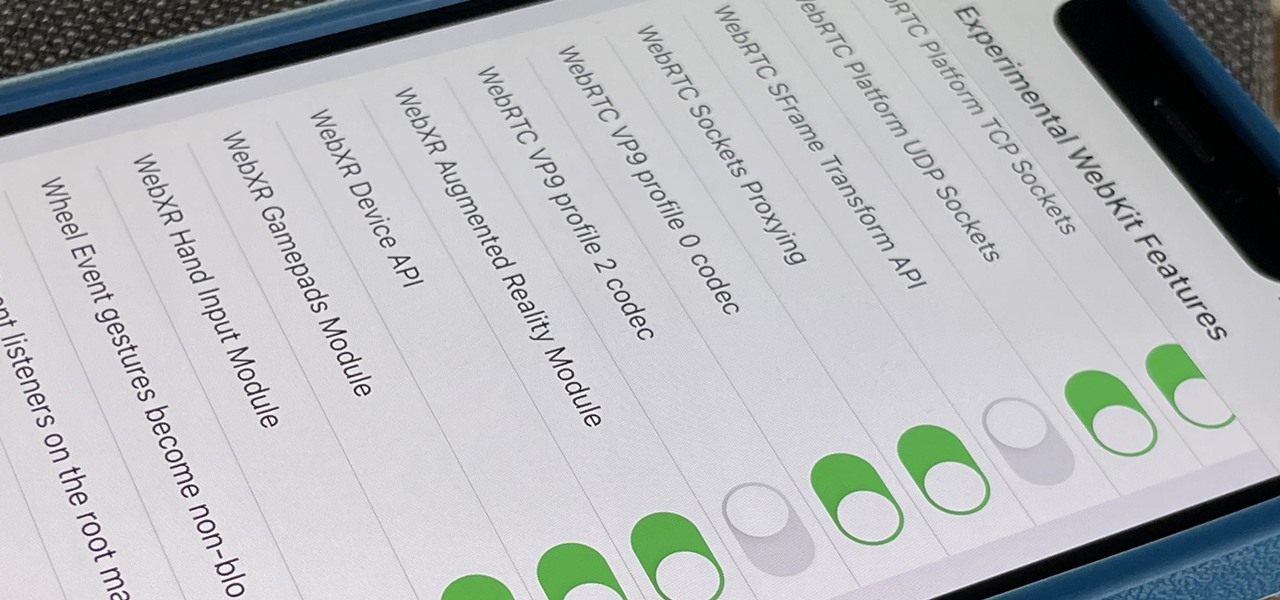
Safari's advanced experimental features give you access to new browser initiatives, upcoming web tools, element changes, behavior adjustments, and other preliminary feature tests in development by Apple. If you use them on your iPhone, you can either improve your Safari experience or wreck it. Resetting the flags provides a fresh start.

With fears over the COVID-19 pandemic subsiding, live concerts are returning. And Doritos wants to send music fans to a few of them via an augmented reality promotion.

If you're trying to get your start in the web development and IT field, then one of the best places to begin is by building confidence with your coding by practicing Python and sharing your work on Git & Github. The Learn Python & Django Developer Bundle can help get you up to speed in Python, Django, Git & Github, and more, and right now it's on sale for $29.99.

Web applications are ubiquitous in the modern online world, and knowing how to attack them is an increasingly valuable skill. But the key to a successful attack is good recon since it's easier to be focused and efficient with the more information you have. There are many fingerprinting tools available, such as httprint and WebTech, but there are even more that can aid us in reconnaissance.

There are so many things in place that make browsing the internet difficult. From geographical walls to malicious software and spying — there's a lot to consider any time you do the most basic of functions online. VPN.asia: 10-Year Subscription is a VPN that can streamline your security process and make browsing the web so much easier, and right now, it's on sale for just $79.99.

Becoming a successful web developer is more than knowing coding languages. Learning to craft functional, intuitive designs is as much coding as knowing how the user will interact with what you've built. The Complete Become a UI/UX Designer Bundle can take you from introduction to mastery in designing the best user experience, and right now, it's only $34.99.

Just as the NCAA men's basketball tournament is set to start later this month, USA Today has decided to trot out an augmented reality mini-basketball game to promote its bracket competition.

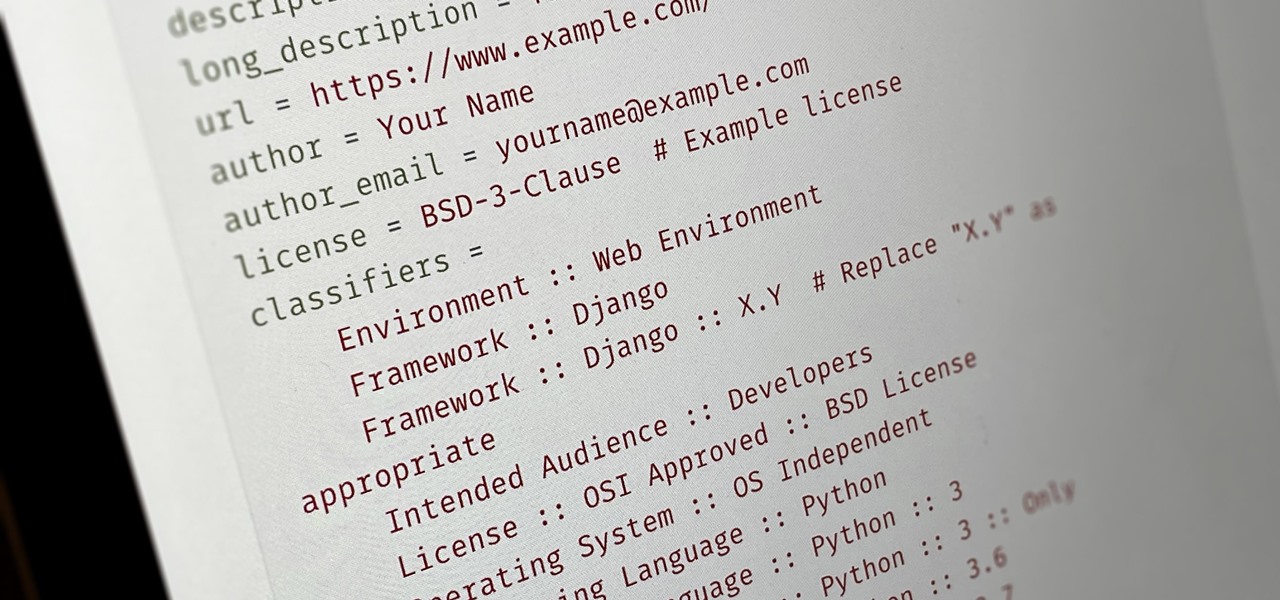
Everybody wants to build an app, but no one wants to start it from scratch. Building a full-blown application — or any other digital product for that matter — from the ground up entails some tedious work, which is why frameworks exist. Django, a Python-based framework, happens to be one of the best

When Treasury Wine Estates released 19 Crimes Snoop Cali Red this summer, named for its new partner in wine, rapper Snoop Dogg, it already came with the brand's signature AR-enhanced label.

Coders are accustomed to working remotely. The beauty of coding is that all you need is a laptop and a WiFi connection, which makes working anywhere a fairly simple transition. If you're looking for a career change, now might be the perfect time to give coding a try.

If you're a hacker, pentester, or any other type of Null Byte reader, and would like to create a website to showcase your services and skill set, you may not have the time or energy to do it the long way.

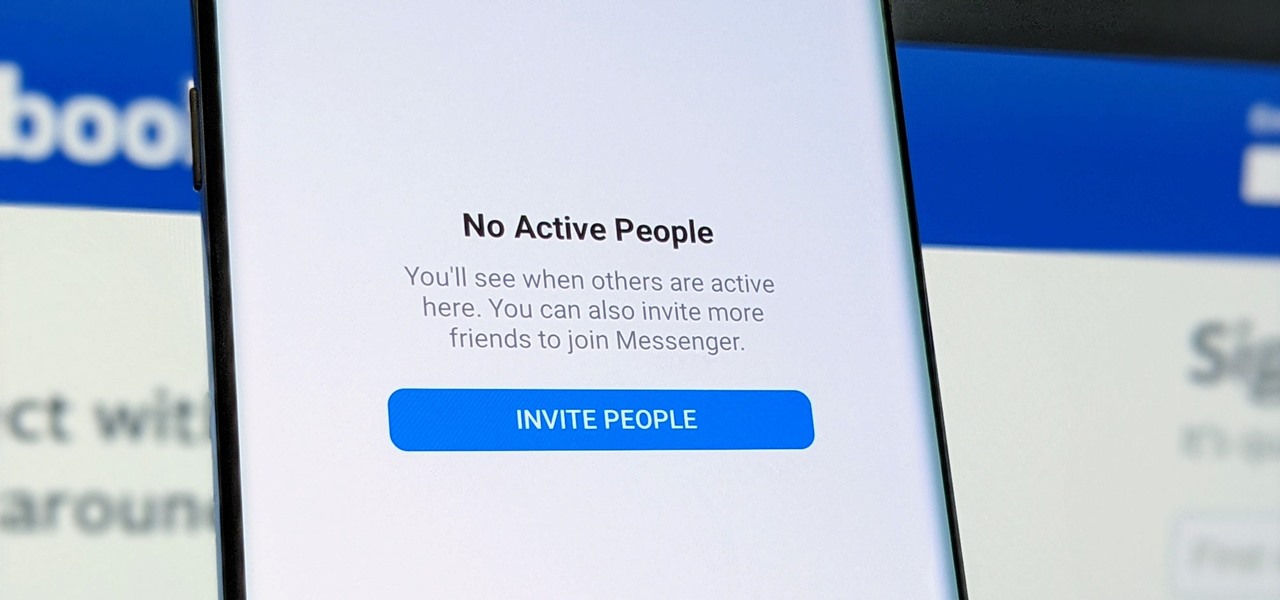
Facebook Messenger's user base has grown so much that it has taken over text messaging as the primary contact method for many people. However, sometimes you might want to hide your online status from specific contacts and appear offline to others. There's a neat little trick you should know that can help you achieve this.

It's no secret that learning how to code is one of the best things you can do if you want to land a high-paying career in a world that's heavily reliant on web and app development.

For all the benefits 5G brings to cellular data, it isn't without weaknesses, the biggest being privacy. Yes, the latest standard comes with breakneck downloads speeds up to 4.3 Gbps, but at what cost? Like with all things on the internet, 5G devices open opportunities for both good and bad actors.

Every single photo you take carries with it a considerable amount of seemingly "invisible" yet important information known as metadata. Although metadata is usually helpful to sort your photographs by location and date, that same information could potentially be used against you, especially if the pictures are taken during a precarious situation.

Determining the antivirus and firewall software installed on a Windows computer is crucial to an attacker preparing to create a targeted stager or payload. With covert deep packet inspection, that information is easily identified.

For enterprise augmented reality platform makers, remote assistance apps represent one of the greatest opportunities to show off the power of immersive computing. These apps enable experts to guide front-line workers or customers with AR prompts and other content in the field of view of their smartphones or smartglasses.

As fun as Twitter is, it can also quickly turn scary. Anonymous, aggressive, and troll accounts can attack you for your tweets and stalk your every move. While you could make your profile private and block users, there are lesser-known privacy and security features that you can switch to improve your safety online.

One of the first steps when pentesting a website should be scanning for hidden directories. It is essential for finding valuable information or potential attack vectors that might otherwise be unseen on the public-facing site. There are many tools out there that will perform the brute-forcing process, but not all are created equally.

Reconnaissance is one of the most important and often the most time consuming, part of planning an attack against a target.

Correctly identifying the underlying technologies that run on a website gives pentesters a considerable advantage when preparing an attack. Whether you're testing out the defenses of a large corporation or playing the latest CTF, figuring out what technologies a site uses is a crucial pen-tester skill.

If you have friends who aren't privacy-conscious, you've surely heard the old "What do I have to hide?" excuse. Despite the fact that billions of people are using the internet each day, many of them don't know the dangers that can find them. And many don't know the tools to combat them.

Apple's iOS 13 for iPhone includes new features in Safari that make browsing the web a little bit better when compared to iOS 12. Some changes are small while others add functionality that just wasn't there before. Plus, there are more security enhancements.

Gboard is often considered the best keyboard for iPhone or Android. Google made sure to jam-pack it full of features, and you should expect nothing but the best when it comes to Google's own first-party software. But with so many capabilities, a few things might slip through the cracks.

Imagine a scenario where you're nowhere near your iPhone, but it's on loud, and you really need to silence it. An alarm may be blaring, notifications could be spitting out sounds left and right, and calls may be ringing. Things can get annoying real quick for whoever's around it. Plus, all that attention makes it easy for someone to find and possibly steal your iPhone. Luckily, you can quiet it down.

Being an Android user and having friends who are in the Apple ecosystem does not need to be a pain. You can easily send high-quality videos to iPhone users, so don't feel handicapped without access to iMessage. Sending high-resolution videos to iOS users is easy with this fast video-sharing method.

One of the first steps in attacking a web application is enumerating hidden directories and files. Doing so can often yield valuable information that makes it easier to execute a precise attack, leaving less room for errors and wasted time. There are many tools available to do this, but not all of them are created equally. Gobuster, a directory scanner written in Go, is definitely worth exploring.