In recent weeks, major bank websites around the world have experienced outages after being have been hit with Distributed Denial of Service (DDoS) attacks. Although few, if any, of these banks have been totally knocked offline, these DoS attacks have dramatically slowed the response time of their websites to legitimate customers. The most recent victim was the Royal Bank of Scotland. Due to this attack, RBS customers were unable to access their accounts for about an hour last week.
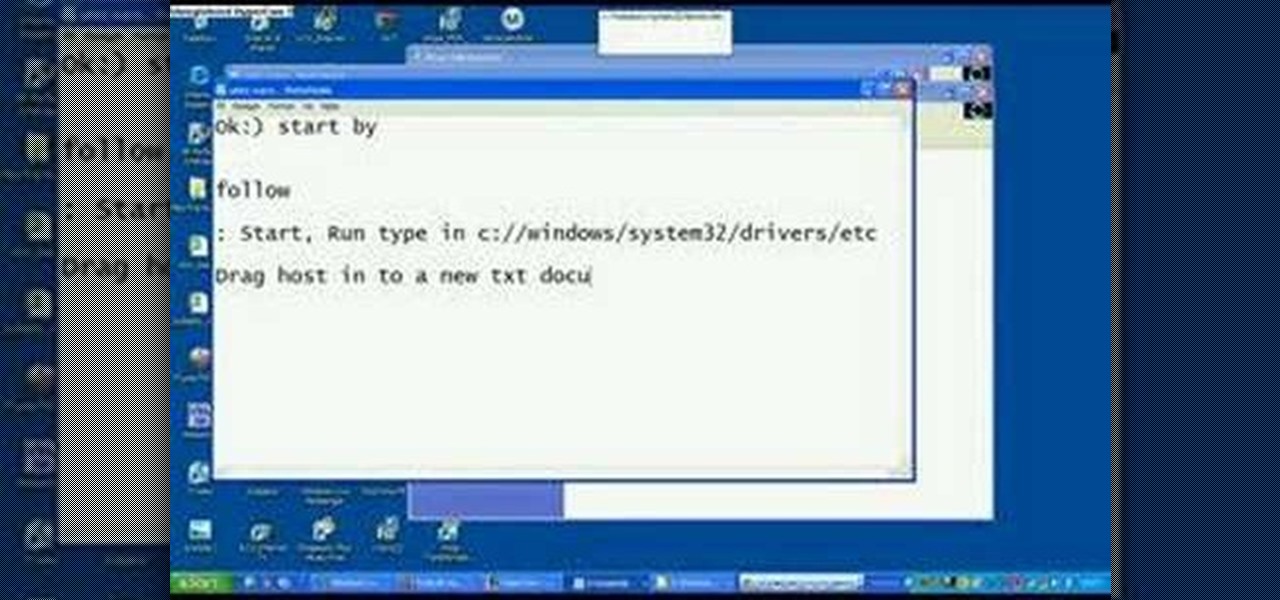
In this tutorial, we learn how to block a website. First, you will start by going to the start menu then go to "run". After this, type in "c://windows/system32.drivers/etc". After this, a new window will pop up on your screen. With this, you will drag the host into a text document. Then, type in the website that you want to block inside of this document. Once you are finished, type in the IP address of your computer next to that and save it. This will finish up the blocking of the website and...
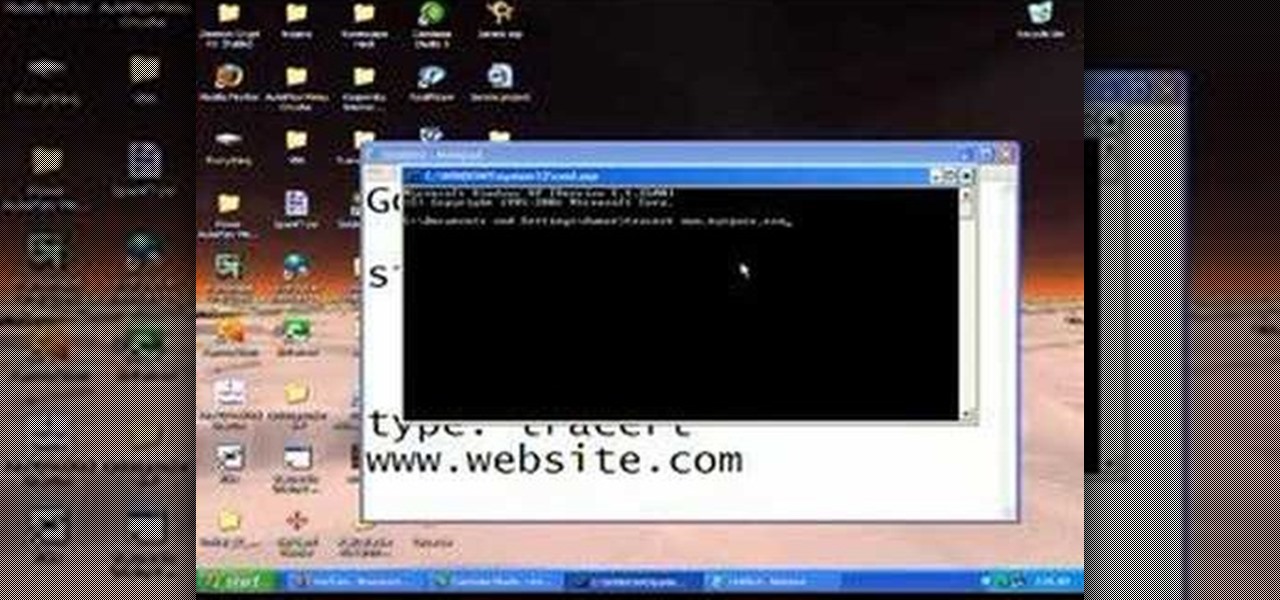
In this video, we learn how to hack school filters to get on Facebook with Tracert. First, go to the start menu and then type in "cmd" into where it says run. After this, type in "tracert" and then the website name. Wait for all of the information to fill in in the black screen. Then, copy and paste the IP address that appears inside. Now you can take this and use it to go to Facebook while you are at school. Or, you can go to any website that you'd like to that you normally can't go to at sc...

In this tutorial, we learn how to set up a Tumblr blog. First, log onto the Tumblr website by clicking the sign up button. Enter your email address, a password, and the URL you want your Tumblr website to be at. After this, click the sign up button. Now, you will be brought to a welcome page and start changing your settings. Click on customize, then add a title, description, and upload a picture. You can also click on the theme, colors, and feeds tab to change more preferences. When you are f...

In order to play SWF files, you need to download SA Flash Player. You can find this program on a website called Mega Upload. For FLV files you need to download the applian FLV player. You can find this program at a website called applian technologies at the address http://applian.com. Once you have downloaded and installed these programs, you will be able to do such things like watch videos you couldn't previously access and play games on your computer that, again, were not available before. ...
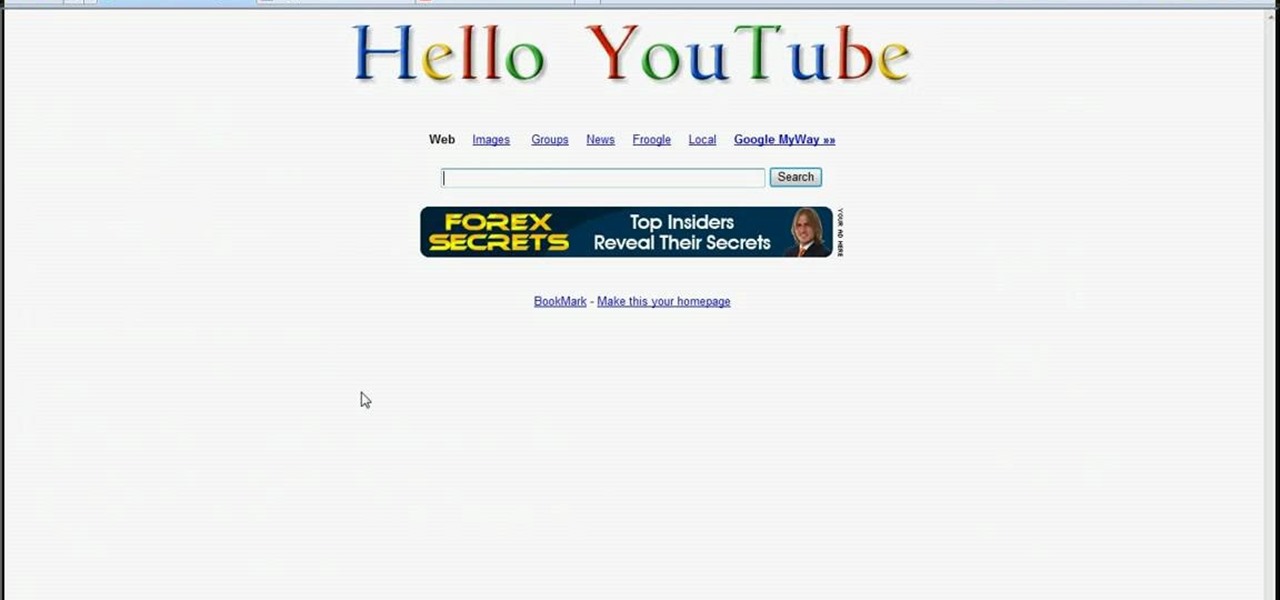
In this video the instructor shows how to make Google say your name. To do this, first, open up your favorite web browser and go to the website GoogleMyWay. This opens a page where it says that you can design your own Google web page. Now type your name into the first box and click to make it. This generates a URL for you. Copy the URL into the address bar of the browser and open the page. This opens a Google-like website with your name on it. Now, if you like to make this your home page, the...

Learn how you would bypass a school’s web filters so that you can go to content sites that are always blocked in examples of YouTube. Click the ‘Start’ button and then click on ‘Run’ and type in cmd and hit enter on your keyboard. This will bring up a command prompt where you type in ‘ping’ and then when that populates the next prompt you enter in the website to bring up the IP address. By entering the populated number you can get into a website from the search field of a web browser. It incl...

Business cards are a great way to keep tabs on the contacts we network with. So why shouldn't our smartphones make them even more useful? Enter Google Lens, which will help you save, search, and expand on the contact information found on all of the business cards you've collected.

Doxing is the act of finding one's personal information through research and discovery, with little to no information to start with. You may have seen doxing in the news, for instance when not so long ago, hacker team Anonymous doxed and reported thousands of twitter accounts related to ISIS. Doxing can be useful for finding the address of a coworker, or simply investigating people on the internet. The tutorial I will provide to you now will teach you the basics of doxing and how you can prot...

The Lab Rats, Andy Walker and Sean Carruthers, explain Media Access Control (MAC) addresses. Filtering MAC addresses allow you to very specifically control access to your wireless network.

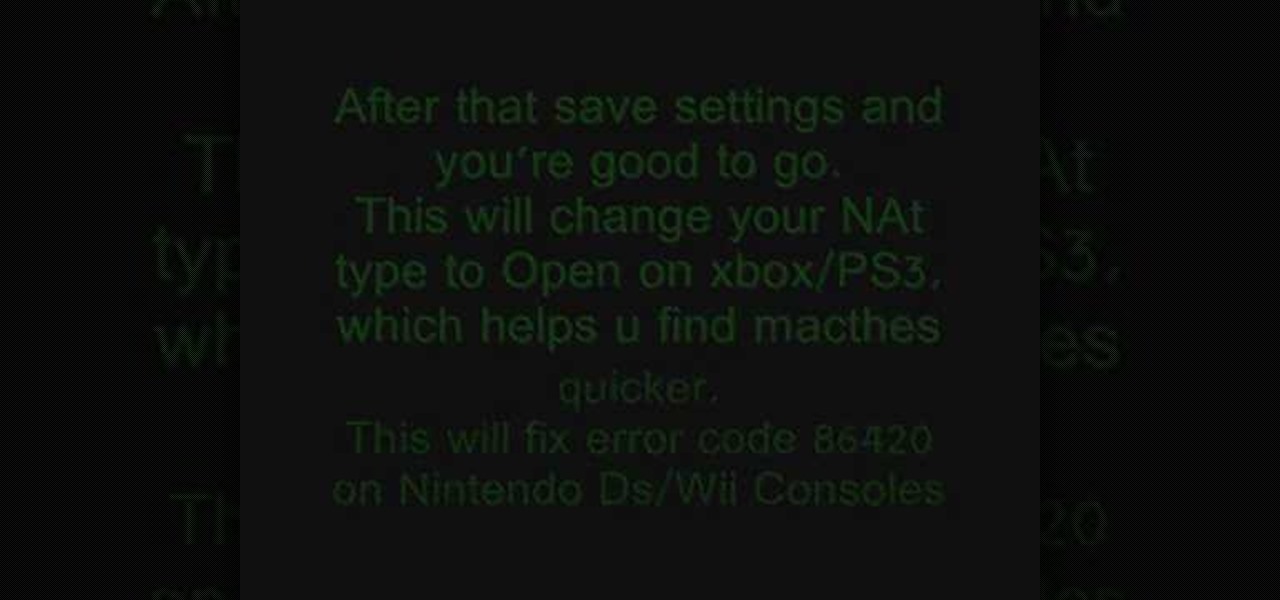
In this tutorial, we learn how to fix error code 86420 and change your NAT type to open. First, go to the website to change the settings for your Linksys router. Next, go to the applications tab that says "applications and gaming". After this, go to port range forwarding, then write in a name next to where it says "application name". Under "start" write the number 1 and under "end" write 6553, then keep "both" marked under protocol. Next, enter in the last 3 digits of your console's IP addres...

Reconnaissance is the phase of an attack where a red team or hacker designs a strategy based on the information they can learn about the target, as well as what the available attack surface looks like. These scans can take time to discover relationships, but Raccoon OSINT scanner coordinates multiple automated scans to produce invasively detailed reports on a target with a single command.

Security researcher and iPhone hacker pod2g has brought attention to a flaw in Apple's iOS that allows the user to change the reply address of an SMS message. This bug has been a part of the iPhone's SMS since the first iPhone in 2007, but Apple has yet to address it. Basically, there's a section in the text payload called User Data Heading (UDH) that controls some advanced features, one of which is the reply address. By changing the reply address of a text message, you can make someone send ...

If you're like most people running Mac OS X, you've got quite a large number of entries in your Apple Address Book. In this how-to, you'll find instructions for organizing your addresses into groups for easy access in Address Book, other applications, and even sync devices such as other Macs, iPods and iPhones. For more on using groups in Apple Address Book for Mac OS X, watch this video tutorial.

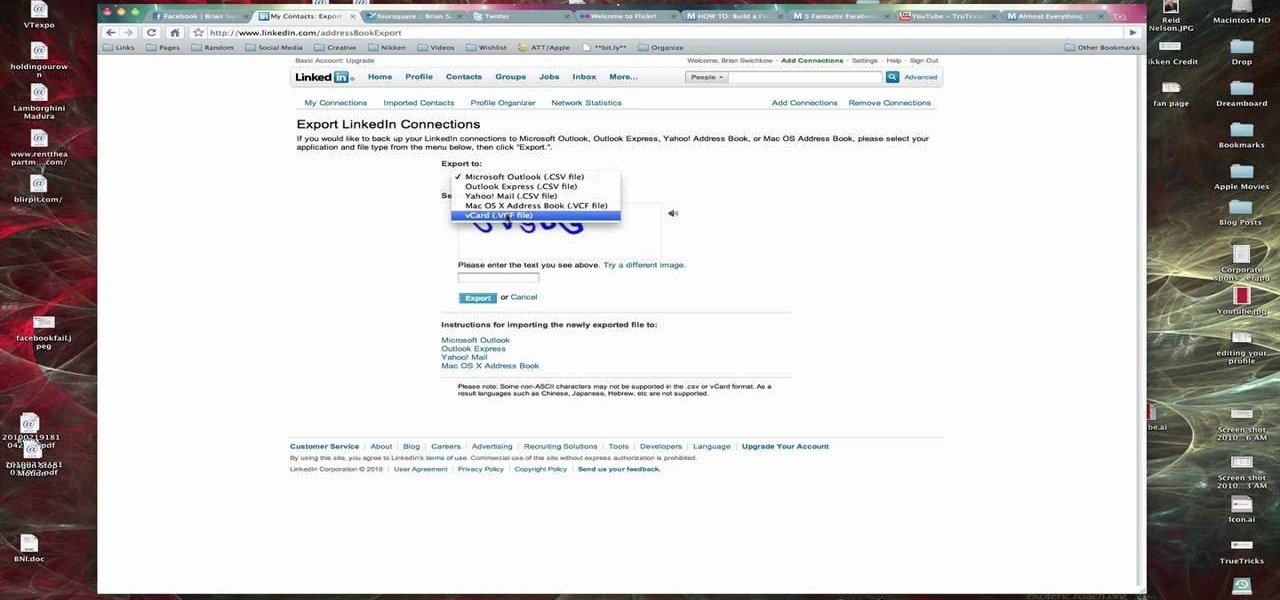
In this Computers & Programming video tutorial you are going to learn how to export LinkedIn contacts to an address book. LinkedIn is great for keeping your contacts in your professional network. To export your contacts go to home page and click on ‘contacts’. Now your full network of contacts will be displayed. On the right hand bottom, click on ‘export contacts’. On the next page select where you want to export the contacts, type in the security code and hit ‘export’ and all the contacts wi...

If you have friends who aren't privacy-conscious, you've surely heard the old "What do I have to hide?" excuse. Despite the fact that billions of people are using the internet each day, many of them don't know the dangers that can find them. And many don't know the tools to combat them.

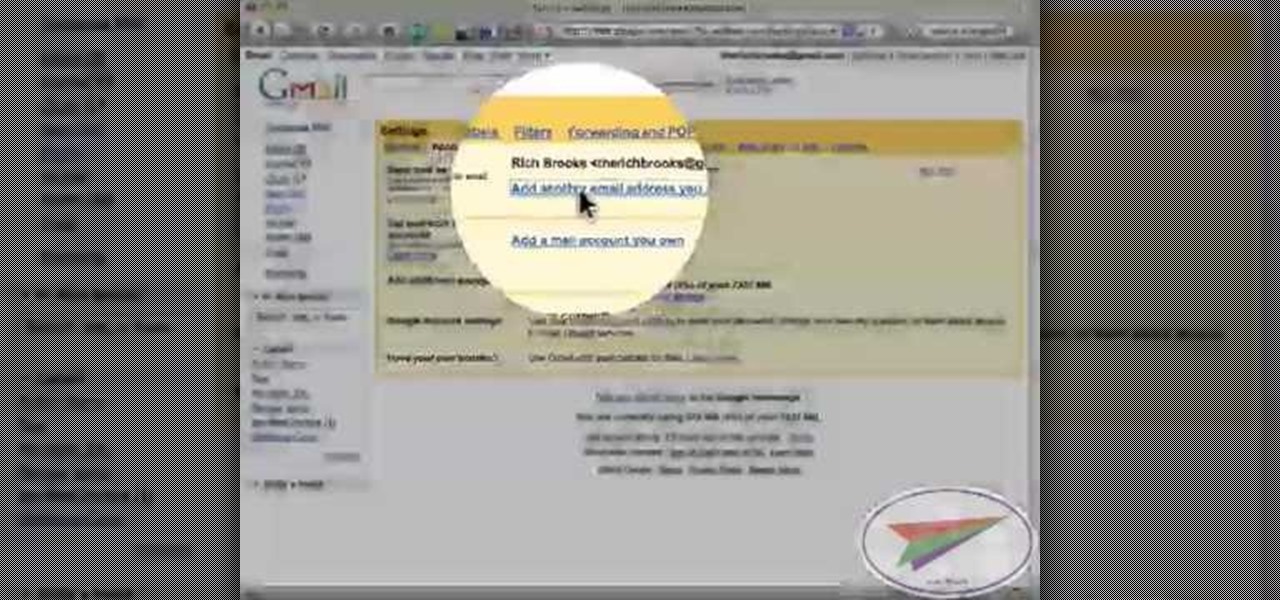
In this video from flytenewmedia we learn how to send from separate email addresses using Gmail. This is great for small businesses. To make it look like you are sending it from your other email address, and not Gmail, follow these steps. Click on Settings then click accounts. You need to add another email address that you own. Click on next step. Now Gmail will send a verification. click on the inbox and click the link within the gmail that you just received. Now it will say confirmation suc...

1. Type in WWW.sendthisfile.com in the web toolbar and press enter 2. Click on Register found on the top right side

Big business is on the web these days and you don't have to build a shopping website or blog to get involved.

Right out of the box, iPhone is incredibly easy to use. If you want to get the most out of every feature, you’ve come to the right place. This video tutorial straight from Apple will teach you how to use GPS maps and the compass on the Apple iPhone 3G. The iPhone redefines what a mobile phone can do.

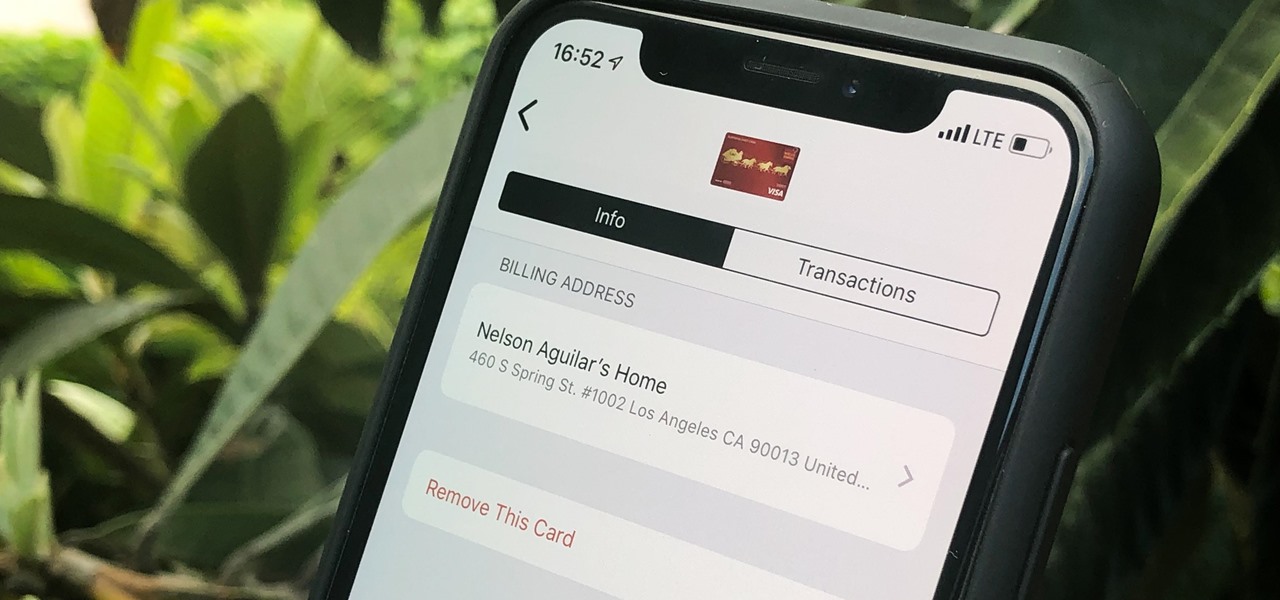
Apple Pay can be used at retail stores, restaurants, markets, and millions of other locations in the US and abroad. It's used to buy everything from clothing to groceries and vending machine snacks, so it's important to ensure that the cards in your Wallet are always up to date with the correct billing and shipping addresses.

Your social security number, credit card information, and medical history can fall into the wrong hands if you're not careful about how and where you share your data online. If you really care about your data, there are tools and techniques you can utilize to protect yourself from cyberstalkers, advertisers, and hackers in a time when digital lives are a high commodity.

Leaked databases get passed around the internet and no one seems to notice. We've become desensitized to the data breaches that occur on a daily basis because it happens so frequently. Join me as I illustrate why reusing passwords across multiple websites is a truly awful practice — and compromise hundreds of social media accounts in the process.

Using just a small sticky note, we can trigger a chain of events that ultimately results in complete access to someone's entire digital and personal life.

If you're a U.S. expat living, traveling, or studying abroad, or just someone who typically uses virtual private networks (VPNs) in order to access the North American video libraries of services like Hulu or Netflix, you were probably surprised to see that these video streaming services don't work on your Chromecast or Chromecast 2.

All kinds of people pretend to be someone they're not on the internet, including scammers, people attempting to wind others up, hackers and web predators. Almost all of these people will leave bases uncovered and they're all easy to expose when you understand how to. Here are my favorite ways of finding out when somebody is lying quickly. Image Search

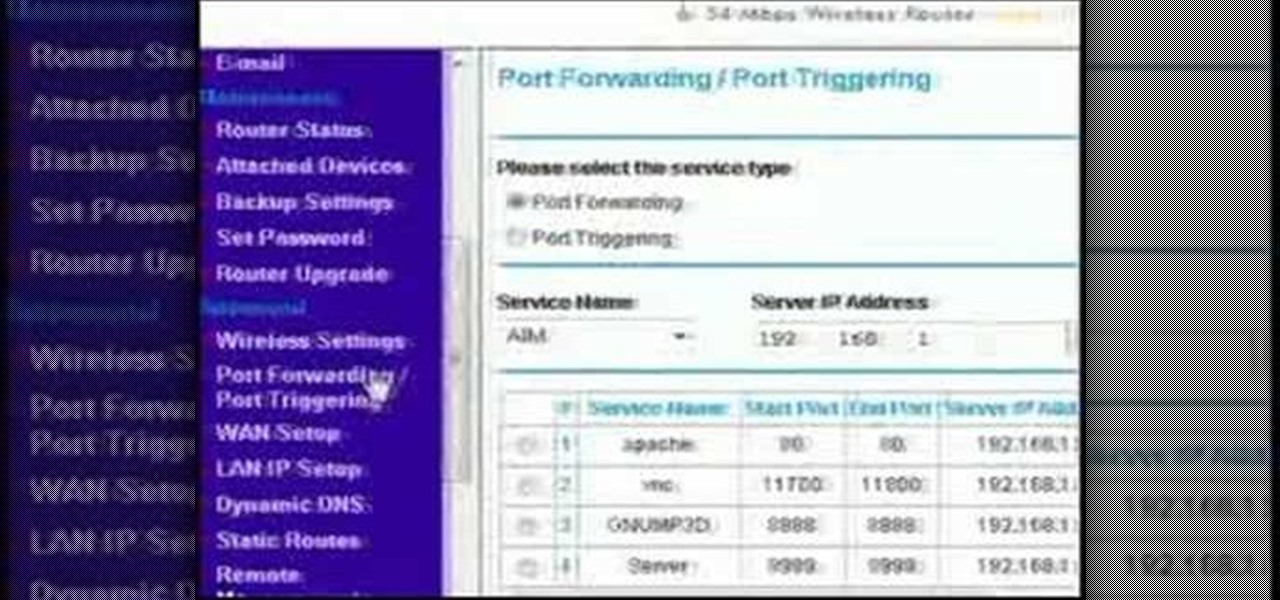
This video discusses how to bypass your router to access your server. In the search window type in CMD to open up a command prompt. Then type in ipconfig to bring up the ip configuration. You want to look for the ip address for the default gateway and the one for your computer. They should both start with 192.168. Once you find them open up internet explorer and type in the ip address for your default gateway and it should then prompt you for a user name and password. Log in and look for a po...

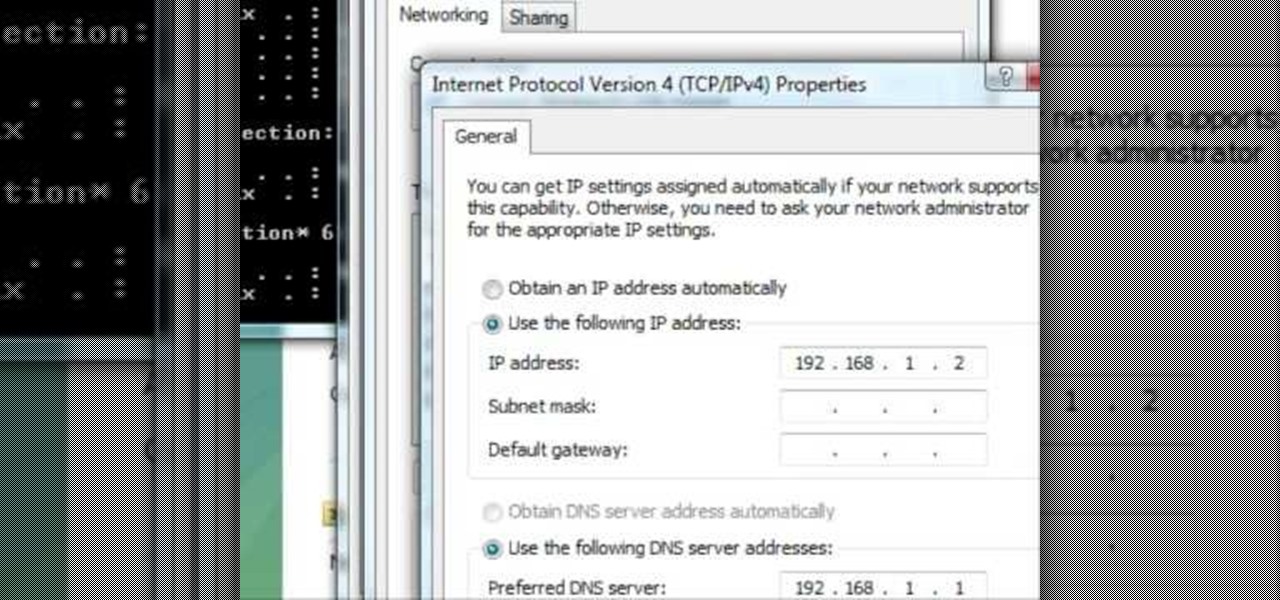
In this tutorial, we learn how to change an IP address in Windows Vista. First, open up cmd on your desktop and a new window will pop up. When the black window comes up, type in "ipconfig". You will now see your IP address, leave this window open and open up the control panel. Once in the control panel, click "view network status and tasks", then click on "view status". After this, click "properties" then click "internet protocal version 4" and click on "properties" again. Now, type your IP a...

If you have any Google applications, like Gmail or Google Calendar, that you want to sync to your new Android enabled mobile phone, it's a simple task to complete. There's nothing hard about it, but if you think you need help, Best Buy has answers. The Best Buy Mobile team explains how simple it is to sync Google apps with your Android cell phone.

In this video tutorial, viewers learn how to find an I.P. address. Every computer that has Internet connection has a unique identifier called a Internet Protocol Address. This video provides 2 methods on how to find your I.P. address. The first method is to simply open your web browser and search on the Internet. The second method is to click on the Start menu and select Control Panel. Click on Network and Sharing Center. Right-click on your connection and select Status. There, users will be ...

In this video we learn how to use the address book in Windows XP. First go to Start, All Programs, Accessories, Address Book. You can choose to make it your default vCard viewer. Now in the address book, create a new contact by clicking new contact. Fill in the name and email address and click on add. Now there's an email associated with this record. You can also set up information about home address as well. It's important to put as much information as you know so it makes it easy to sort. W...

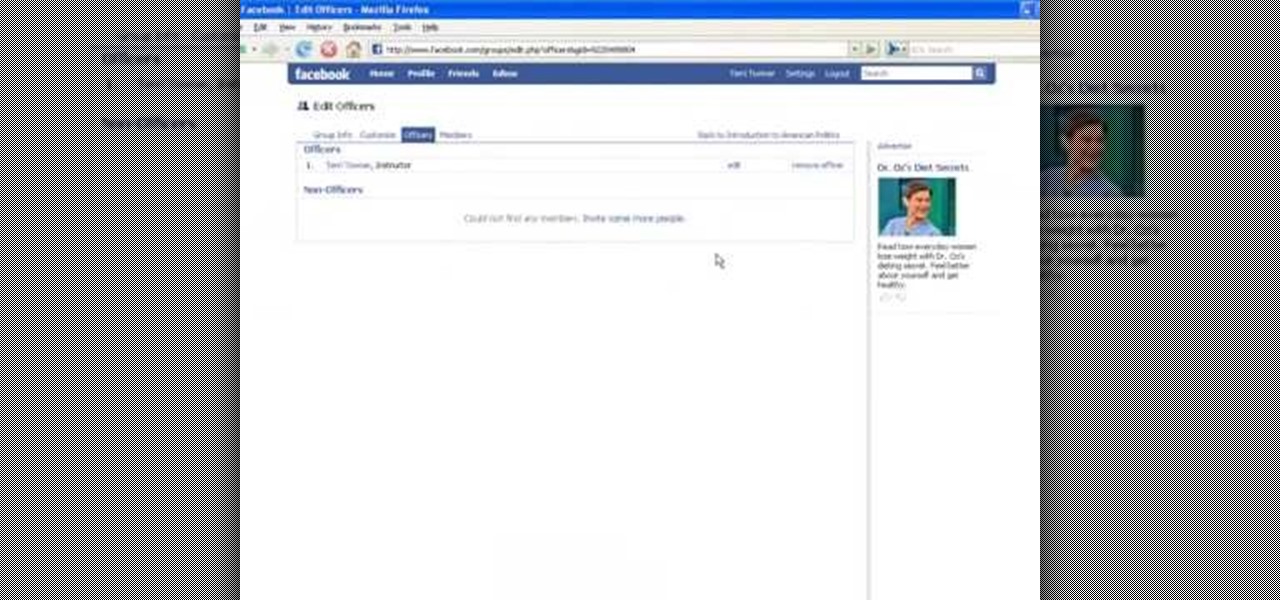
In this tutorial, we learn how to set up a group on Facebook. First, log into your Facebook, then click on "groups", then click "create a new group". Now, give your group a name, description, news, email address, and contact information. When finished, click on "create group". Now you will be able to customized your group by adding images. Once you do this, you can add a website and change your different options. Allow only instructors to upload photos, because students may decide to upload i...

Patrick Norton and Veronica Belmont from Tekzilla will show you how to dual boot Windows 7 and download videos from YouTube. The hosts show viewers how to dual boot Windows XP Pro32 bit and Windows 7 RC 1 64 bit. In the first step as always you will want to back up your hard drive and at the very least they recommend to back up your most important files. In the case that something goes terribly wrong you can use a free program called EASEUS to make a complete image of your whole drive, this a...

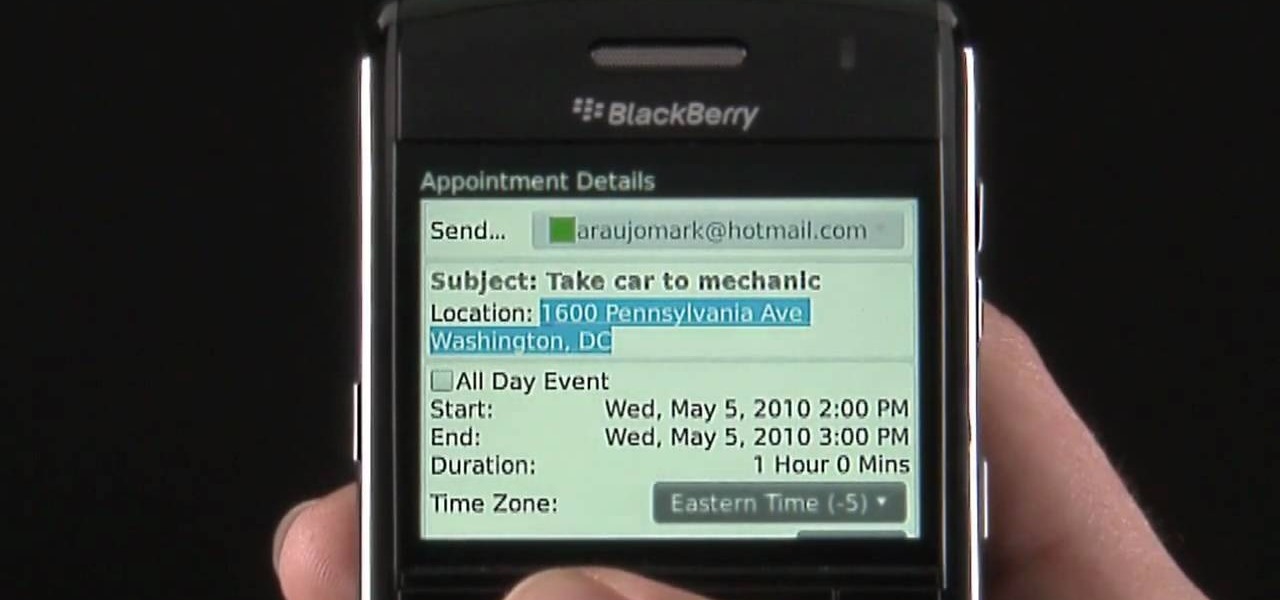
Learn how to take advantage of the Address Recognition feature built into the BlackBerry Bold 9650 phone. This clip will show you how it's done. Whether you're the proud owner of a BlackBerry smartphone or are merely considering picking one up, you're sure to be well served by this video guide. For detailed information, including step-by-step instructions, take a look.

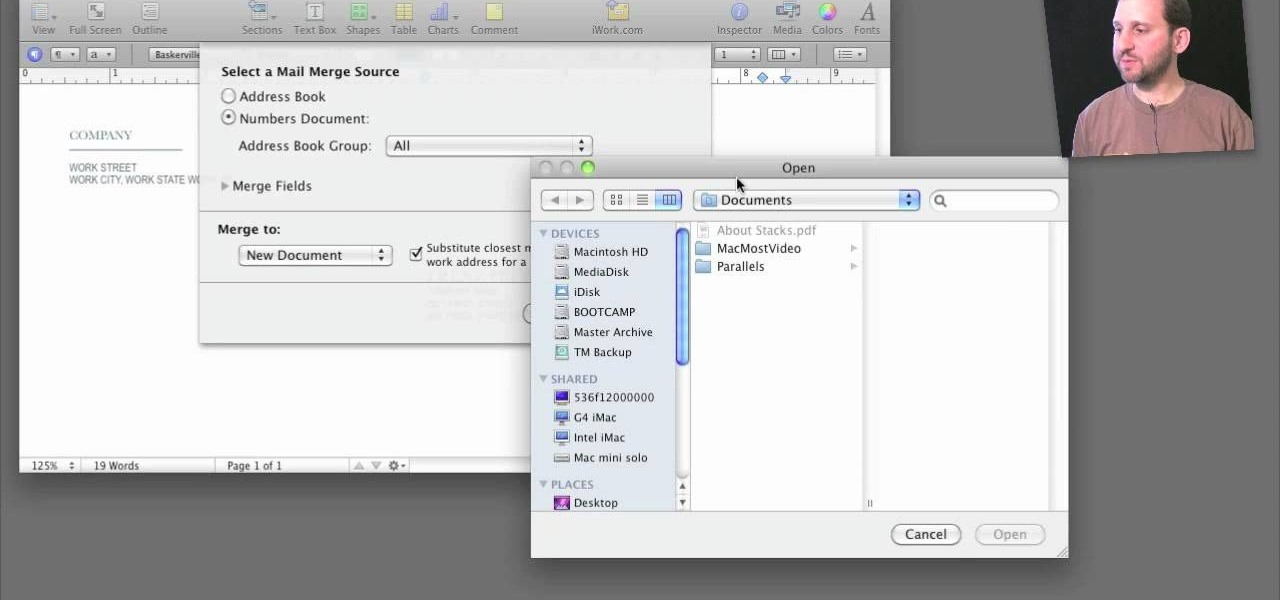
A step-by-step guide that will walk you through Mail Merge on a Mac computer. You will gain how to prep and print envelopes, letters or any document that you need to send to different names and addresses on each item. You can pull the data from your address book or from a Numbers Spreadsheet and will see how to modify and merge the information you will need to successfully set up your documents.

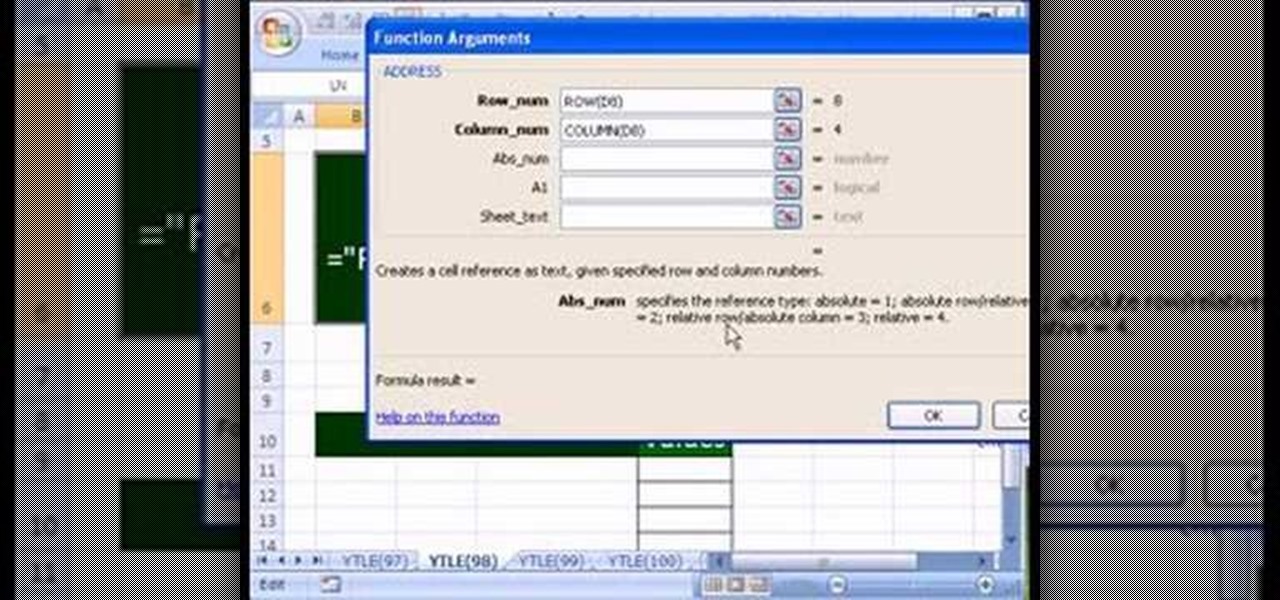
Love Microsoft Excel? This clip contains a tip that just might induce you to. With this free video tutorial from ExcelIsFun, the 98th installment of his "YouTubers Love Excel" or YTLE series of free video MS Excel lessons, you'll learn how to use the ADDRESS function to make labels in templates easier for users to understand.

Now you can make sure your home address is in the right location on Google Maps. If it's not, you can move it to the correct spot. Try it at maps.google.com!!

Before attacking any website, a hacker or penetration tester will first compile a list of target surfaces. After they've used some good recon and found the right places to point their scope at, they'll use a web server scanning tool such as Nikto for hunting down vulnerabilities that could be potential attack vectors.

The easiest way around a security policy is to find users who don't follow it. The Have I Been Pwned database identifies accounts with information breached by major third parties like Yahoo and LinkedIn. With Maltego, hackers can locate breached accounts created using company email addresses, potentially giving attackers access to a company account if the employee reuses a compromised password.

After numerous scandals like the Equifax data breach and the 2016 US election, cybersecurity has become a significant issue for Americans. Unfortunately, anytime we use our devices, we're open to a cyber attack — especially when we browse the web. However, there are ways that we can make it harder for hackers and data miners.