While much of the world is currently in some form of quarantine due to the COVID-19 pandemic, augmented reality (AR) gives us all the opportunity to see virtual content while stuck in our homes.

The COVID-19 pandemic has created a frenzy for news and information that is nearly unprecedented in the smartphone era, with a major side effect of misinformation. Now, major tech companies are making it easier to ask for advice about novel coronavirus from their respective digital assistants. Results may vary, but Apple and Google are the most useful at the moment.
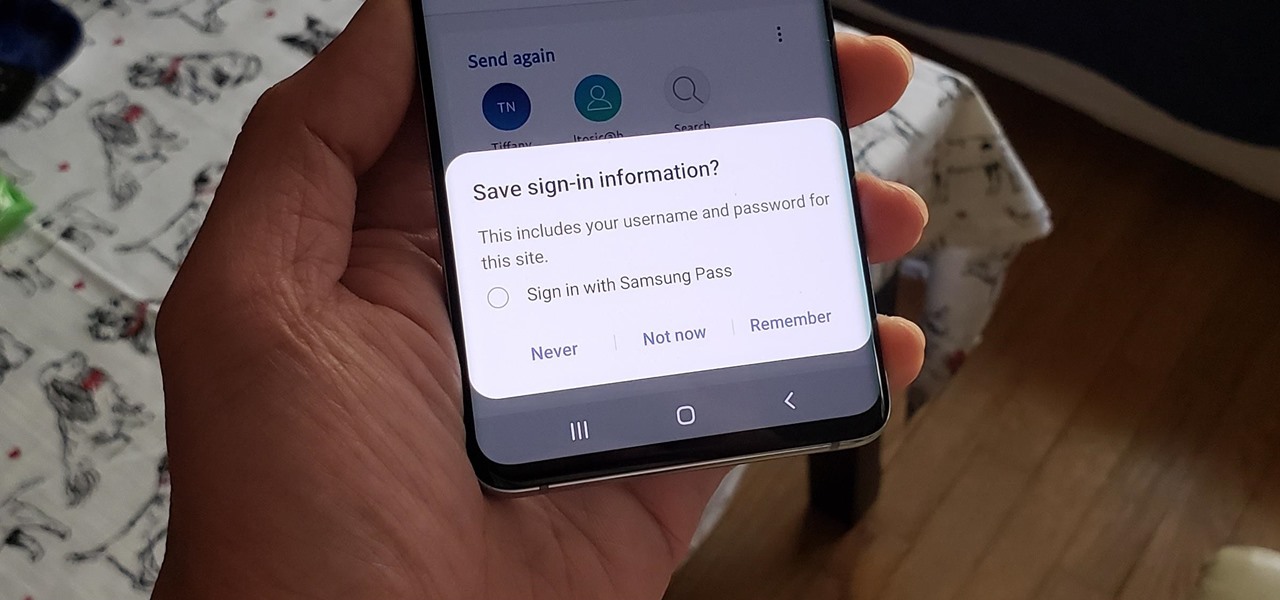
If you use Google Chrome on your computer, you've undoubtedly saved a ton of passwords since the browser always prompts you to. But Samsung uses their own password service on their phones by default, so you'll have to change a setting if you want to use your Chrome passwords to log into apps and sites on your Galaxy.
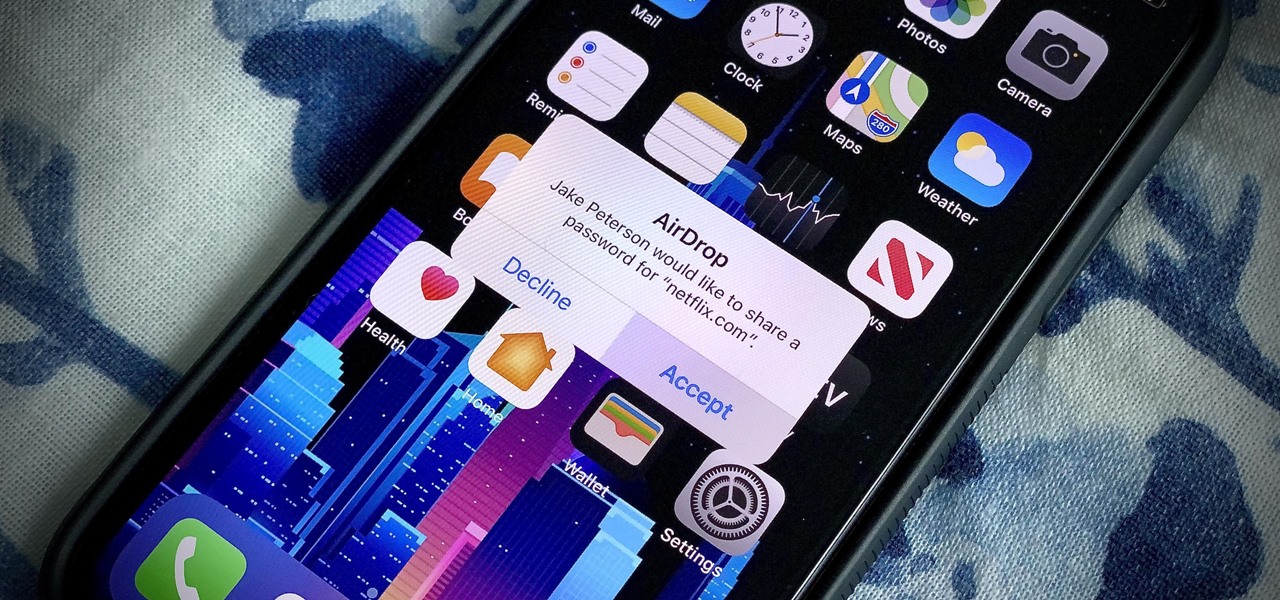
In iOS 11, Apple made it easier for you to share passwords with friends. Back then, it was just Wi-Fi passwords, which made sense. "What's the Wi-Fi?" gets old after a while. But now, whether you're running iOS 12 or 13, you can share any password you want with any iPhone around, all with one of iOS' best features: AirDrop.

Correctly identifying the underlying technologies that run on a website gives pentesters a considerable advantage when preparing an attack. Whether you're testing out the defenses of a large corporation or playing the latest CTF, figuring out what technologies a site uses is a crucial pen-tester skill.
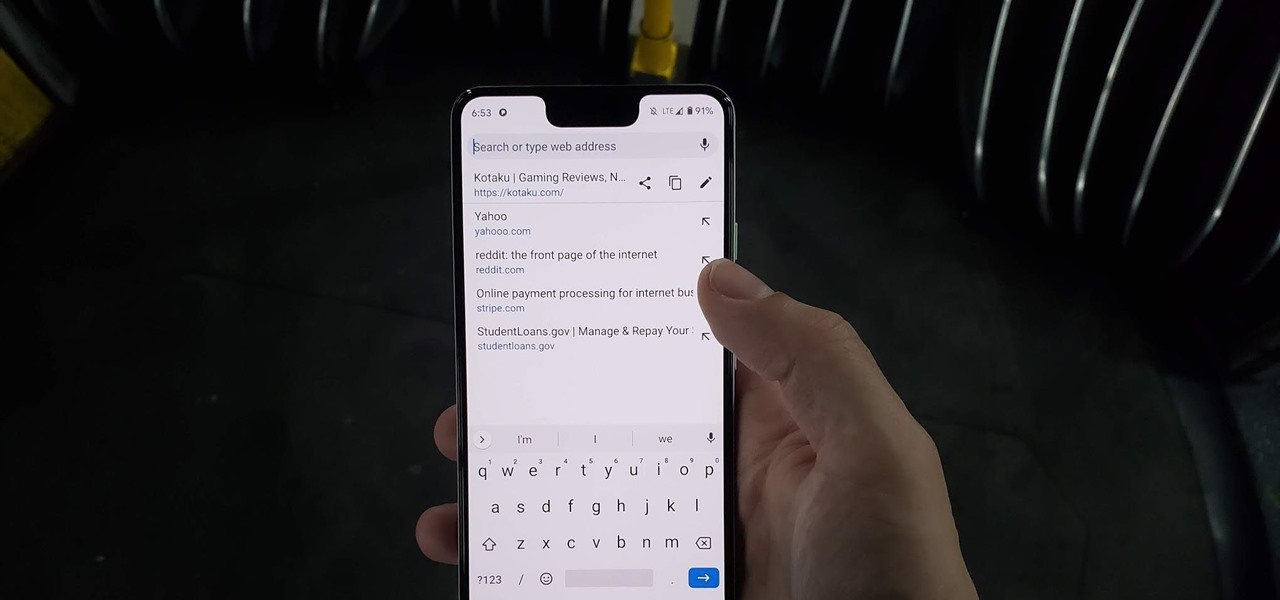
Chrome has just introduced some new UI elements for web exploration. The new URL bar is not intuitive. But once you get to grips with it, you will be so much more efficient in your address bar editing, pasting, and navigation.

Normally, when you scroll down a webpage in Safari on your iPhone, it automatically hides the bottom toolbar and minimizes the top Smart Search field. But as soon as you scroll back up, they both reappear, which can be pretty annoying if you don't need them. Apple's iOS 13 update brings many new features to Safari, one of which solves the toolbar issue so you can keep it hidden when reading.

We already know that major players like Magic Leap have been planting the seeds of augmented reality for mainstream consumers through wireless partnerships with AT&T, NTT Docomo, SK Telecom.

We know that Microsoft's HoloLens 2 is due to start shipping later this year, but despite the trickle of news about the device, we still don't know when.

While browsing the web on a computer, most of us are familiar with using Ctrl + F (or Command + F) to search for a specific word on a page — but what if you want to do that on mobile? If you're using Google Chrome, there's a simple way to search for specific words on iPhone or Android.

One of the best ways to dig into a website and look for vulnerabilities is by using a proxy. By routing traffic through a proxy like Burp Suite, you can discover hidden flaws quickly, but sometimes it's a pain to turn it on and off manually. Luckily, there is a browser add-on called FoxyProxy that automates this process with a single click of a button.

If you don't want the large and permission-hungry Facebook app on your phone, the perfect solution is to create an app icon for the Facebook mobile site on your home screen. The website version of Facebook doesn't run background tasks, has no distracting notifications by default, you won't be giving Facebook as much data, and your phone's battery life will be improved.

Gathering information on an online target can be a time-consuming activity, especially if you only need specific pieces of information about a target with a lot of subdomains. We can use a web crawler designed for OSINT called Photon to do the heavy lifting, sifting through URLs on our behalf to retrieve information of value to a hacker.

ARP spoofing is an attack against an Ethernet or Wi-Fi network to get between the router and the target user. In an ARP-spoofing attack, messages meant for the target are sent to the attacker instead, allowing the attacker to spy on, deny service to, or man-in-the-middle a target. One of the most popular tools for performing this attack is Ettercap, which comes preinstalled on Kali Linux.

For anyone using open source information to conduct an investigation, a balance between powerful tools and privacy controls are a must. Buscador is a virtual machine packed full of useful OSINT tools and streamlined for online research. This program can easily be set up in VirtualBox, and once that's done, we'll walk you through some of the most useful tools included in it.

Outside of a few headlining features, Apple focused on polishing things up in iOS 12. Instead of revamping functionality left and right and running the risk of releasing a buggy mess like iOS 11, this year's feature additions are smaller. Case in point, you can now show favicons in Safari — nothing groundbreaking, but a nice touch.

Hackers rely on good data to be able to pull off an attack, and reconnaissance is the stage of the hack in which they must learn as much as they can to devise a plan of action. Technical details are a critical component of this picture, and with OSINT tools like Maltego, a single domain name is everything you need to fingerprint the tech details of an organization from IP address to AS number.

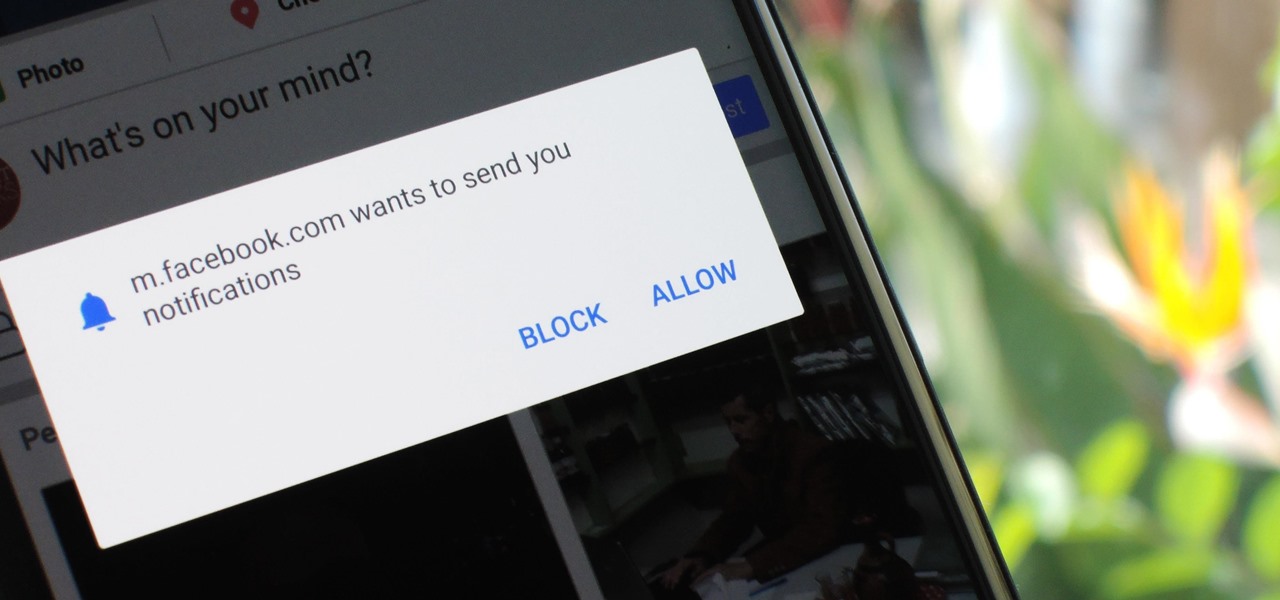
As the go-to browser for millions worldwide, Chrome makes web surfing a breeze with its simple interface and Google integration. But many websites are starting to ask if they can send you notifications, and this can interrupt your browsing. Thankfully, you can completely disable these prompts if you prefer.

Earlier this week, Snapchat announced a partnership with NBCUniversal regarding the 2018 Winter Olympic Games in South Korea. Starting on February 10, Snapchat will be streaming a feed of NBC's live broadcast of the Olympics in Pyeongchang.

Coinhive, a JavaScript cryptocurrency miner, was reportedly discovered on the BlackBerry Mobile website. It was placed there by hackers who exploited a vulnerability in the site's e-commerce software that allowed them to anonymously mine cryptocurrency every time the website was viewed. There's no doubt Coinhive, an innovative mining method, is being abused and exploited by hackers in the wild.

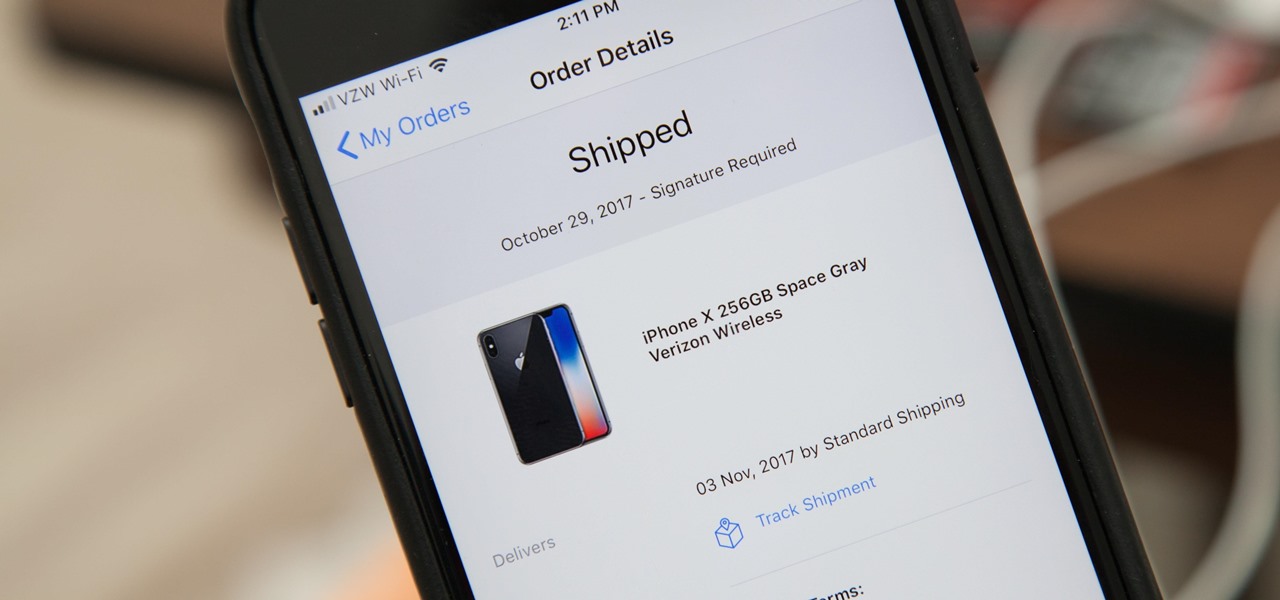
Current shipping estimates for the iPhone X are 5–6 weeks, but is there a chance you'll get yours tomorrow?

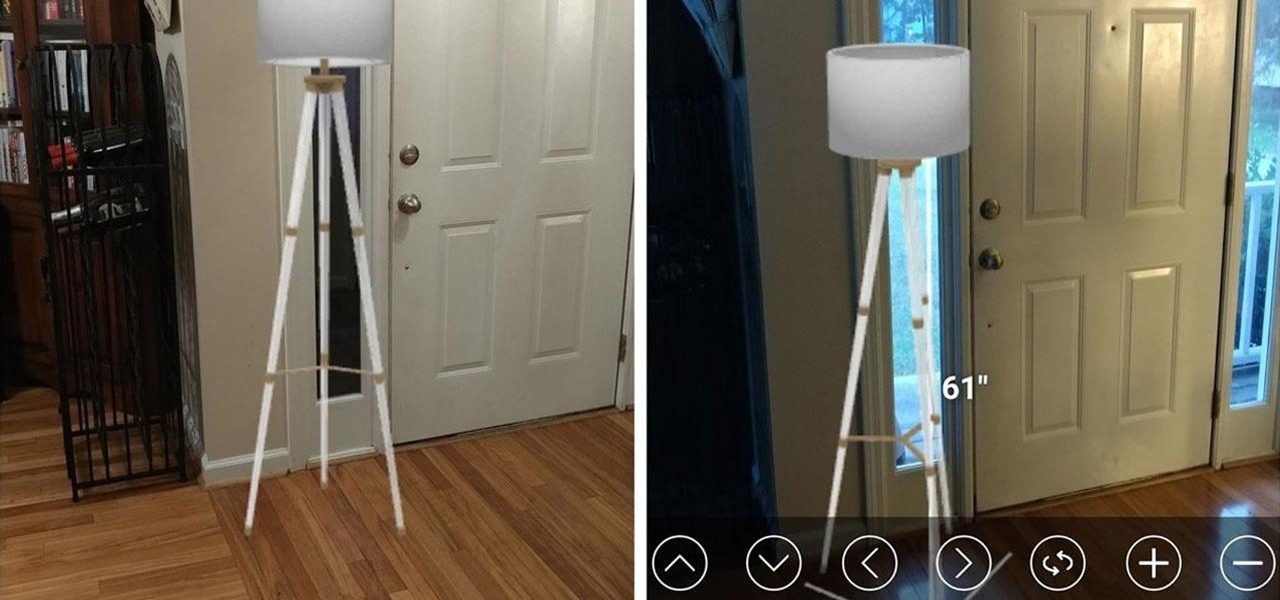
While some companies like IKEA and Lowe's zig towards ARKit to entice shoppers, Target has opted to zag to broader appeal with an augmented reality see-before-you-buy tool for its mobile website.

Buyers can't wait for their Tesla Model 3 to be delivered. But with no clear arrival date in sight, buyers are starting to get a little antsy waiting to see what the Tesla Model 3 will look like up close. Luckily, Tesla accessories seller EVANNEX partnered with technology firm Kinetic Vision to try and satisfy buyers for a while by creating an app that lets you view an augmented reality Tesla Model 3 that's nearly life sized.

After laying off 40% of its staff this month to cut costs, SoundCloud appears to be struggling to stay afloat. While blog posts from the company have assured fans that the music platform is not in danger of shutting down, some people aren't so sure this is the truth. Internet Archive — a non-profit dedicated to preserving websites and services — announced today that they will be conducting a partial backup of SoundCloud to safeguard the site's content in case of closure.

Two salsa dancers who also happen to be programmers are soon releasing an app called Dance Reality, made with Apple's ARKit. Through this app, you will be able to practice your dancing with augmented reality as your teacher right from your iPhone.

The producers of FX's animated series Archer have devised a plan to introduce augmented reality hijinks into its eighth and penultimate season with a new app for iOS and Android devices.

You may not know what HTTP is exactly, but you definitely know that every single website you visit starts with it. Without the Hypertext Transfer Protocol, there'd be no easy way to view all the text, media, and data that you're able to see online. However, all communication between your browser and a website are unencrypted, which means it can be eavesdropped on.

If you're tired of Google tracking you, but love how Chrome works, CyanogenMod has you covered. Their browser is called Gello, which is based off Chromium, Chrome's open-source counterpart. It's basically a souped-up version of Chrome—without all of the intrusive Google stuff. So if you're uncomfortable with Google displaying personalized ads based on your browsing history, or using your location to bring the "Physical Web" to your phone, you won't have to worry about any of that with Gello.

One of Android's biggest strengths is its ability to interact with other operating systems. When you plug your phone into your Windows PC, you instantly see all of the files it holds—and all it takes is a simple syncing app to do the same with Mac. To top that off, apps like Pushbullet and Join bridge the gap even further by allowing you to share links, files, and messages between all of your devices.

Welcome back, my novice hackers! As many of you know, recon is crucial to a successful hack/pentest. In most cases, hackers spend more time doing good reconnaissance than actually hacking. Without proper recon, you are simply guessing at what type of approach or exploit is going to work and, as a result, your time is wasted without any useful outcomes.

This Is for the Script Kiddies: This tutorial is about a script written for the How to Conduct a Simple Man-in-the-Middle Attack written by the one and only OTW.

Welcome back, my tenderfoot hackers! Web apps are often the best vector to an organization's server/database, an entry point to their entire internal network. By definition, the web app is designed to take an input from the user and send that input back to the server or database. In this way, the attacker can send their malicious input back to the servers and network if the web app is not properly secured.

Although they're often times the primary source of income for websites, on-site advertisements can annoy even the most tolerable reader. That's why ad blockers have been some of the most popular downloads on Firefox and Chrome for some time now, demonstrating that when it comes down to it, most people just want nothing to do with ads shoved in their face.

Star Wars season is definitely upon us. No matter where you turn, you can't go a day without being bombarded by merchandising and co-branding advertisements that attempt to draw a parallel between some character from a galaxy far, far away and a galactic cruiser like the Dodge Viper, or a midichlorian-laden power source like Duracell. Yep, it's kind of annoying, but at least we can get some fun out of it here and there.

Many websites are crowded with ads, pictures, and other irrelevant content that make it harder than necessary to read a simple article on your iPhone. In many cases, you have to zoom in just to get a better view of the text you're attempting to read—unless the webpage blocks zooming.

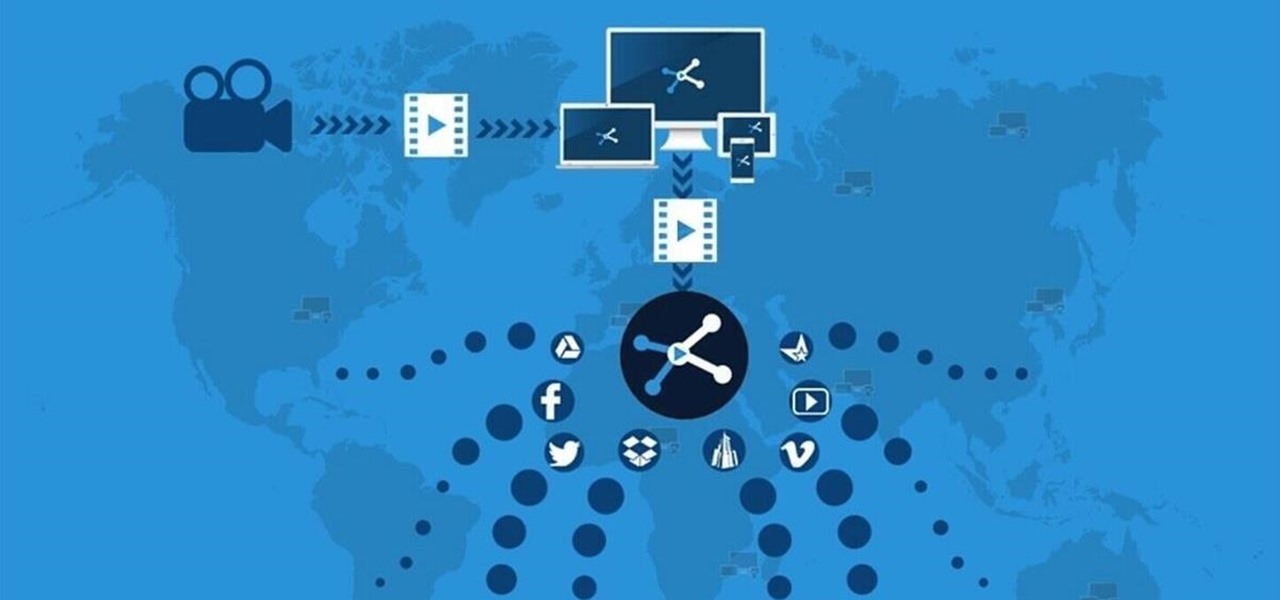
Are you tired of uploading videos to different sites separately? It's really time consuming and difficult. Finally, there is a way to upload and distribute your videos to YouTube, Facebook, Dailymotion, and many more video-hosting websites in one go. No need to upload to every site separately and one by one.

Do you remember the last time we used BeEF? Well, now we get to use it again, but this time with MITMf! We are going to auto-inject the hooking script into every webpage the victim visits!

In an attempt to remain a mobile-exclusive app, Instagram doesn't let users upload photos or videos from their computer. On the Instagram web app, you can pretty much only like and comment on items in your feed, but what about all of those photos on your computer that scream #tbt?

In a study attempting to observe virality in real time, two Microsoft engineers, Corom Thompson and Santosh Balasubramanian, used Microsoft's recently released Face detection API to create How-Old.net and track its usage in real time.

Since the Nexus Player is an Android device at heart, there are already several internet browsers that can be used on the streaming set-top box. Chrome, Firefox, and a few others will run perfectly fine, but the trouble with these is that you need a mouse to use them.