When creating an aesthetically pleasing image, sometimes more is more. Blending images together and blurring the edges is a great method for creating desktops featuring multiple photos of hottie Sam Worthington, or simply for creating a pretty website background.
Cultivating a strong online presence can have a huge impact on your employment prospects or help you get that dream store up and running in no time. Whether you're looking for work or building a brand, being able to create and maintain a professional website is essential in the modern workforce.

Few things are more important than search engine optimization when it comes to increasing a brand's visibility online. Regardless of whether you're launching a new business from scratch or working as a marketing professional at a major corporation, you need to ensure that you're drawing the most people to your website and affiliate links by utilizing the latest and most powerful SEO tools and methods.

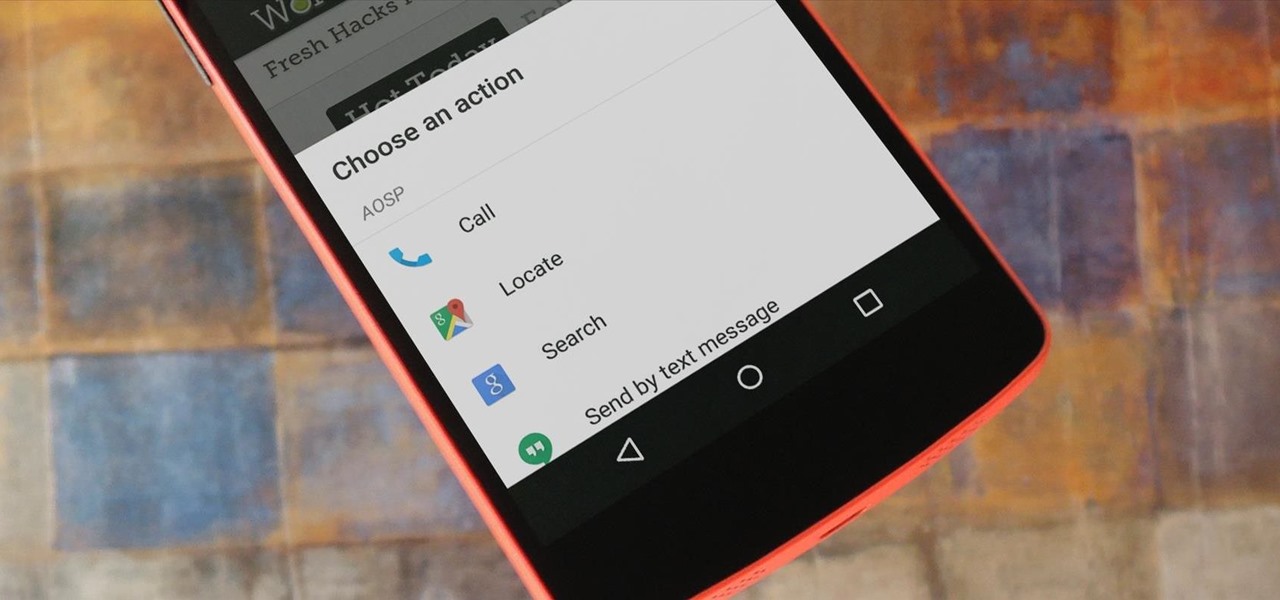
You might prefer a dedicated button, whether physical or digital, to bring up your digital assistant. Pixel phones have the squeeze function to bring up the assistant, but what about OnePlus phones? Luckily, OnePlus has included a feature that uses your power button to act as your assistant button of sorts.
It's now standard for websites to have a mobile version. Conveniently, we can browse the web with a mostly mobile-optimized experience. But what if you want the desktop experience on mobile? If you want, you can browse the mobile web and see only the desktop version of websites on Android devices.

While modern browsers are robust and provide a lot of functionality, they can be unlocked to do some pretty spectacular things with browser extensions. For hackers and OSINT researchers, these tools can be used to defeat online tracking, log in to SSH devices, and search the internet for clues during an investigation. These are a list of my top ten favorite browser extensions for hackers — and how to use them.

Auditing websites and discovering vulnerabilities can be a challenge. With RapidScan and UserLAnd combined, anyone with an unrooted Android phone can start hacking websites with a few simple commands.

Kali Linux, by default, probably doesn't have everything you need to get you through day-to-day penetration testing with ease. With a few tips, tricks, and applications, we can quickly get started using Kali like a professional white hat.

Bookmarks and favorites are handy options for saving interesting websites you come across while surfing the web on Android but are far from ideal when it comes to instant access. Thankfully, Google Chrome gives you the added ability to save webpages and progressive web apps directly to your home screen for added convenience.

Now that we have our payload hosted on our VPS, as well as Metasploit installed, we can begin developing the webpage which will trick our "John Smith" target into opening our malicious file. Once he has, we can take over his computer.

The internet is full of fun, cool, and interesting websites. Bookmarks and favorites can help keep your favorite pages on hand, but they aren't the most convenient method. In iOS, Apple lets you save whatever webpages that you want to the home screen, so you'll have as easy access to them just as you do apps on your iPhone.

Hello people, I'm back for Part-3. In this part, as promised, we are going to create a client program and then we are going to test it with our server program made in Part-2.

Alright so last time I gave you a homework assignment. This week we're gonna look at my version of the UDP-Flooder.
Hey everyone. Only found the site a few days ago but really loving it. Been

Welcome back everyone! In the last training session we covered basic file input and output. We're going to leave this topic for a bit and start on something that will change the way we write scripts, classes.

Welcome back, my tenderfoot hackers! Web apps are often the best vector to an organization's server/database, an entry point to their entire internal network. By definition, the web app is designed to take an input from the user and send that input back to the server or database. In this way, the attacker can send their malicious input back to the servers and network if the web app is not properly secured.

Welcome to a tutorial on crypting technology. In this article, we will be discussing types of crypters, how they work and why they work. After defining these, we will then make our own basic crypter using the function I gave to you as a task to complete by yourself in the previous tutorial.

Welcome back, my greenhorn hackers! Over the years, I have written many articles here on Null Byte chronicling the many the hacks of the NSA, including the recent hack of the Juniper Networks VPN. (By the way, my speculation in that article has proven to be correct. The NSA did embed a backdoor on those devices.)

to stay secure, you dont just need Tor, and a VPN. You need good browsing habits. What are Browsing Habits You Ask?

Hello All, So to recap in part 1 I went through setting up the dchp server. Part 2 detailed the bash script. Now in part 3 I will post the entire bash script. I am doing this in its own post because Part 2 is just way to much info on one post IMO.

Hello everybody Joe here. Today I will be demonstrating how you can find XSS vulnerabilities in a website and what you can do with them

In recent weeks, major bank websites around the world have experienced outages after being have been hit with Distributed Denial of Service (DDoS) attacks. Although few, if any, of these banks have been totally knocked offline, these DoS attacks have dramatically slowed the response time of their websites to legitimate customers. The most recent victim was the Royal Bank of Scotland. Due to this attack, RBS customers were unable to access their accounts for about an hour last week.

hello my dear colleagues, I made a visit to nullbyte and found that there is not a complete tutorial about the google dorks, so I felt the need for this tutorial, and seeing that there are many newbies around, so here's a tutorial that will teach you how to use google to hack.

For the most part, when you're copying text on your Android device, it's because you intend on pasting it into a different app than the one you're currently using. For instance, you might be looking at a posting on Craigslist. So you copy the seller's phone number, then head to your home screen, switch over to your phone app, paste it into your dialer, and finally make the call.

NOTICE: Ciuffy will be answering questions related to my articles on my behalf as I am very busy. Hope You Have Fun !!!

If you took a big step back and really looked at the world, you'd see how downright silly our nations look when they put up fences to separate themselves from one another. Creatures big and small roam free while respecting each other's space, but humans create borders and physical barriers to delineate their cultures.

With all of the different websites we use in our day-to-day lives, keeping track of our numerous login credentials can start to become a hassle. This has created a market for password managers that aim to centralize these account credentials and generally streamline the process of logging into our favorite sites.

Welcome back, my novice hackers! Before we try to attack a website, it's worthwhile understanding the structure, directories, and files that the website uses. In this way, we can begin to map an attack strategy that will be most effective.

Taking pictures, sharing your location, and making calls are easy enough to do with an Android device, but for the most part, they all require your screen to be on with some sort of swiping and pressing actions. Dedicated shortcut keys are virtually non-existent on any modern day phone, but their utility is something that can be very useful.

Welcome back, my budding hackers! Recently, I showed you how you could exploit the widely disseminated OpenSSL vulnerability that has to become known as "Heartbleed". Although the world has known about this vulnerability for over a month now, it will likely take many more months—or even years—for everyone to close this vulnerability.

Welcome back, my greenhorn hackers! Although we have focused primarily on technical hacks here, social engineering can sometimes be especially effective. This one requires a bit of technical skill, but not too much. In addition, it's limited by how specific a target you can choose—but it will work.

Welcome to this short and easy tutorial on hacking and DDosing (is that even a word I don't know) anyways lets get started

When we think of search it's usually in regards to the internet. But when you are using a smartphone, searching your device itself can be just as important and useful.

Hello, today I will tell you about how you can create a page through wordpress. this is a performance for those who have scarcely been touched wordpress. This guide will put you through basis and create a user and a website among millions of people.

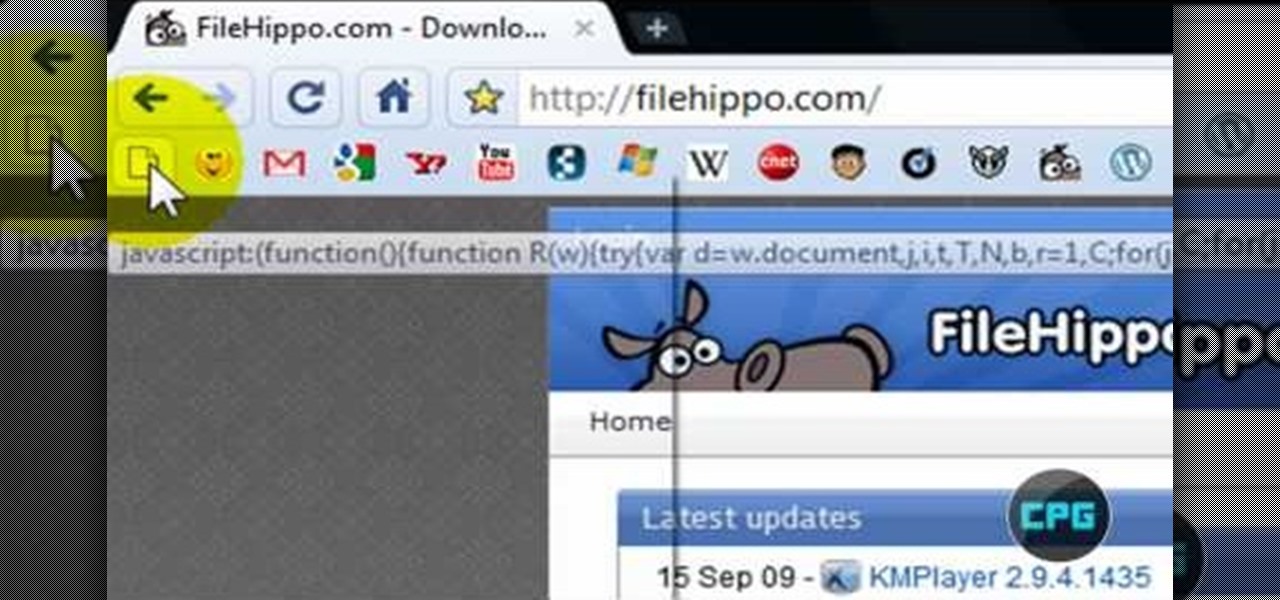
In this video from MegaByteTV we learn how to block ads on a web page using the Google Chrome browser. If you see an ad on a website, click the icon which is actually a shortcut to a JavaScript code. It will then block the flash on a JavaScript website. Automatically all of the flash on a page will be blocked. You can do this by using the link provided in the box underneath the video. Copy and paste the JavaScript code into a new bookmark on your browser. Right click the bookmark bar and hit ...

Let's be honest here: While the web opens up a whole new, vast world of dating opportunities, it simultaneously opens up the possibility of creeps, stalkers, and just plain crazy types.

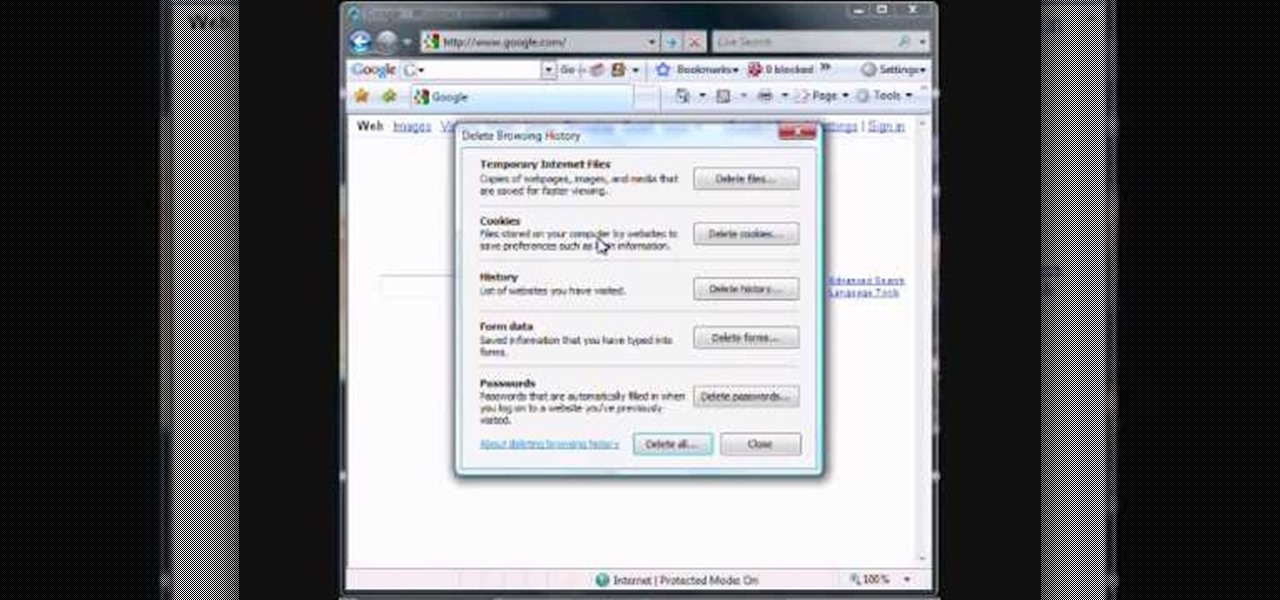
In this tutorial, we learn how to clear your browsing history in Internet Explorer. First, go to the tools button and then click on 'delete browsing history'. Click that and then a new window will pop up. If you want to clear everything, click 'delete all' and then 'yes'. The temporary internet files are fine to delete, this is just info that is saved after you visit a website. Cookies are bits of information that a site stores on your computer to remember who you are. The history is simply w...

In this tutorial, we learn how to download and use torrents. First, go to the website: uTorrent and download the software. After this, install it on your computer and then open it up! From here, go to the website torrentz and use the search box to find what you want to download. After you find the item you want to download, you can click on it and then choose to download it with your uTorrent software. Now, it will appear in your software and tell you when it's done downloading. When finished...

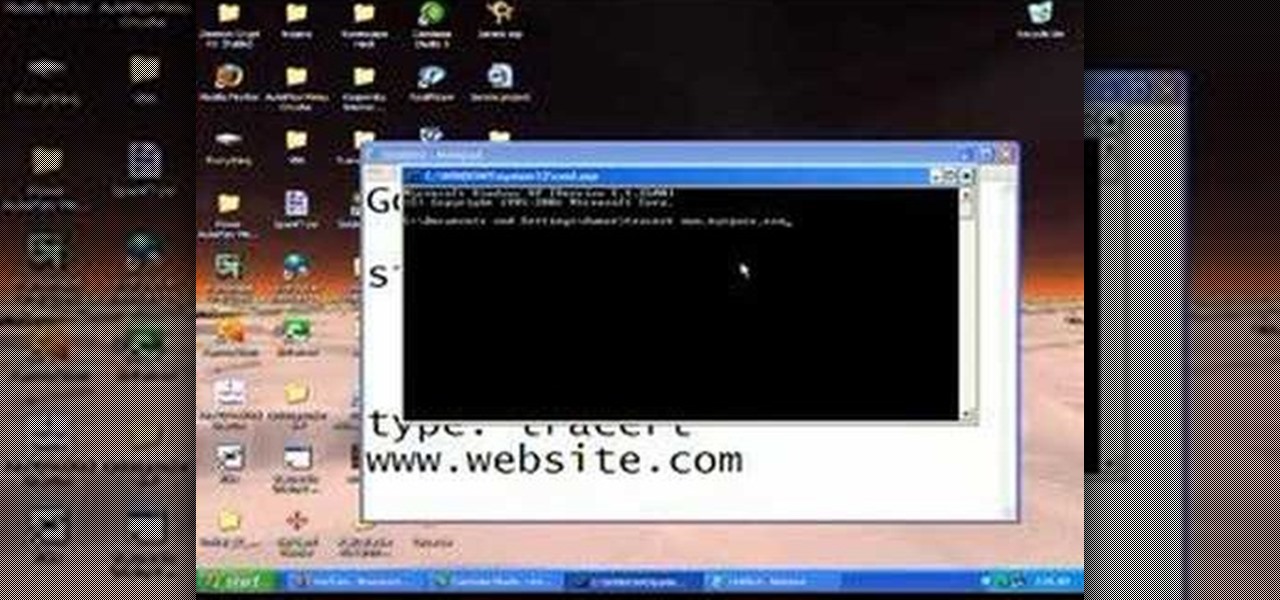
In this video, we learn how to hack school filters to get on Facebook with Tracert. First, go to the start menu and then type in "cmd" into where it says run. After this, type in "tracert" and then the website name. Wait for all of the information to fill in in the black screen. Then, copy and paste the IP address that appears inside. Now you can take this and use it to go to Facebook while you are at school. Or, you can go to any website that you'd like to that you normally can't go to at sc...

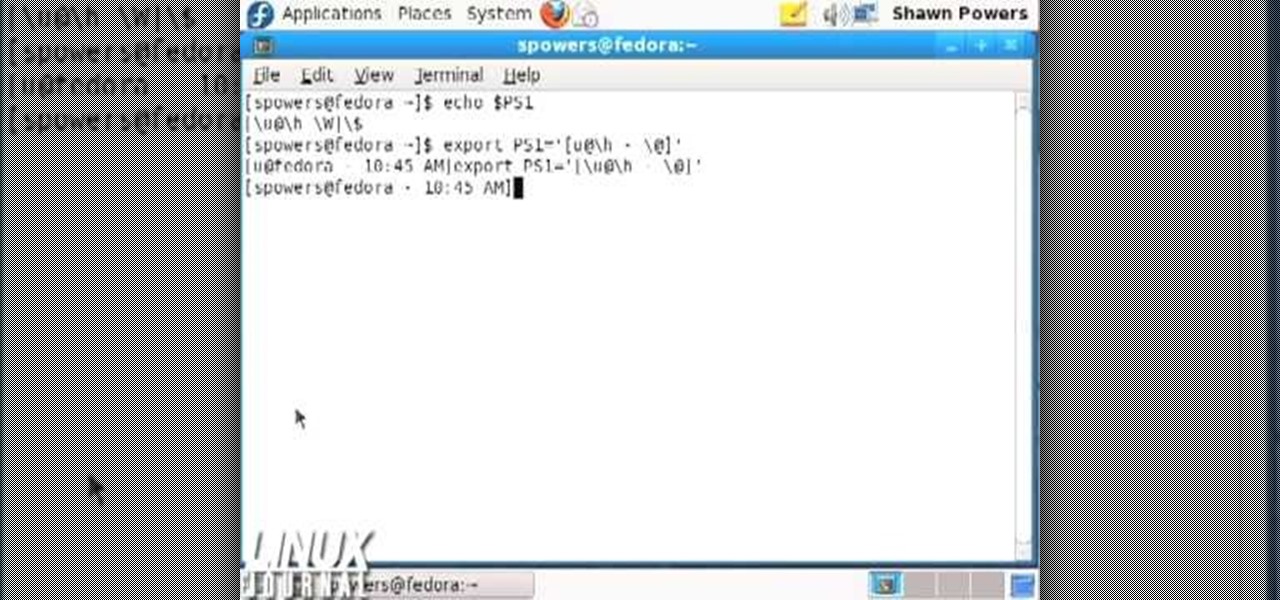
In this tutorial, we learn how to customize bash prompts with the PS1 variable. The PSI variable will say what something does. You can change this using the export command. Basically, you just type in the same thing and add in something. You can do this by simply typing it in using your keyboard. After this, press enter on your keyboard, then continue to change more things. There are a ton of different things you can do with this. You can find more from the website: http://pastebin.com/f2309f...