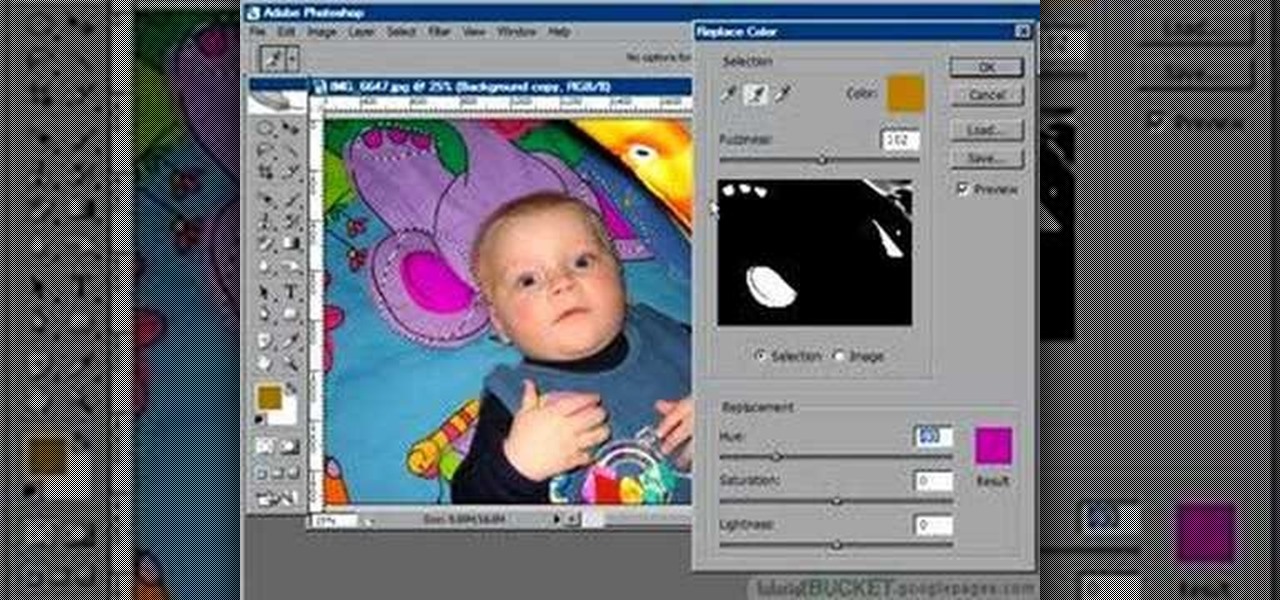
The replace color command is a nifty tool in Photoshop that enables you to change a color in an imagine very quickly and effectively. The tool requires that you make a copy of the original layer, as the replace color command is a destructive function. It requires parts that you want replacing to be selected first, to change the color of the desired areas. The result is a very realistically edited image, that is extremely fast and easy to accomplish.
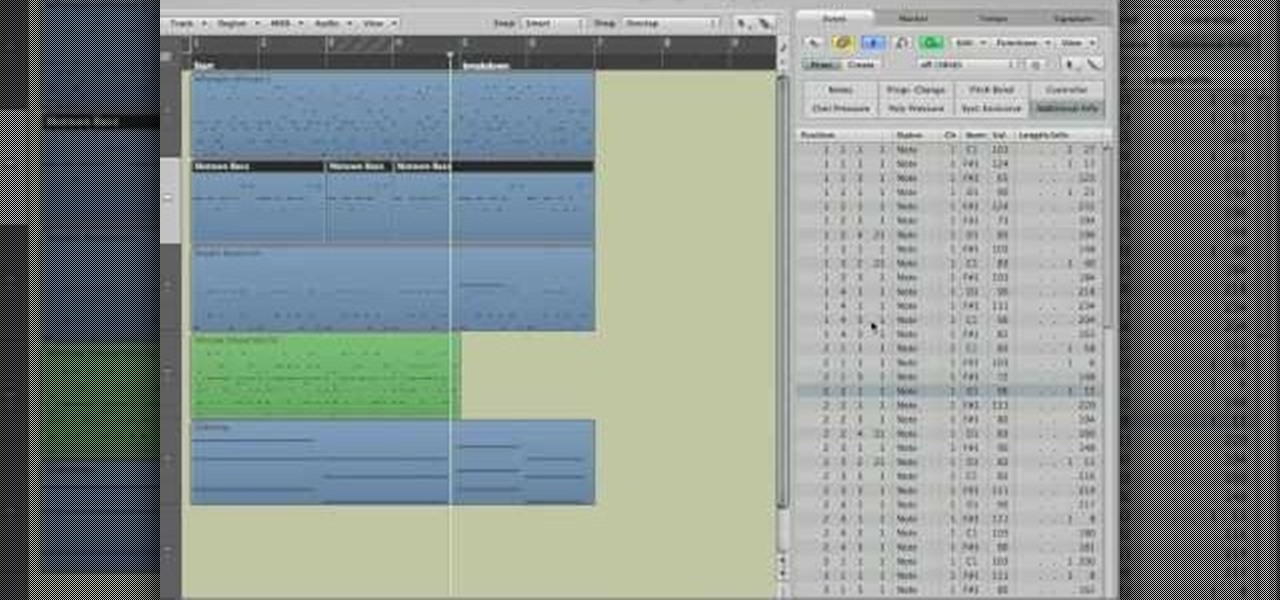
Get to know how to use Logic Pro's arrange page in this short tutorial. Use the arrange area to work with the audio of your song. Change the timeline by choosing a time and beat. Use the toolbar area to do some functions. Use the icons to easily open up media and list areas. Use the bin to store your audio. Use the browser to look for your audio songs. Use the event list editor to edit your MIDI information. Use the inspector to view the channel strips of your track. Use the editors in the bo...
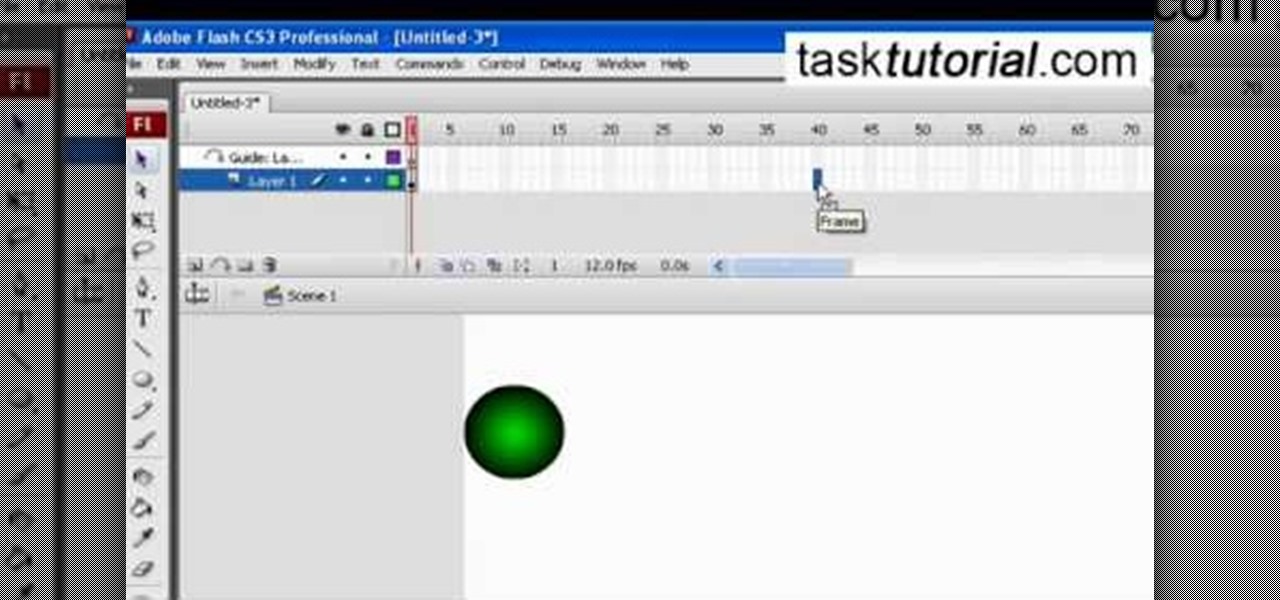
This tutorial video, from tasktutorial demonstrates how to create animation using the motion guide function in Flash. You will learn how to create an object, in this case, a ball, and create an animation that makes it appear to bounce. The guide shows you, how to add a motion guide by selecting a key frame and drawing it in. Then you will learn how to snap the object to your guide line, and add motion to it by selecting another key frame between the first and last frames, and snapping the obj...
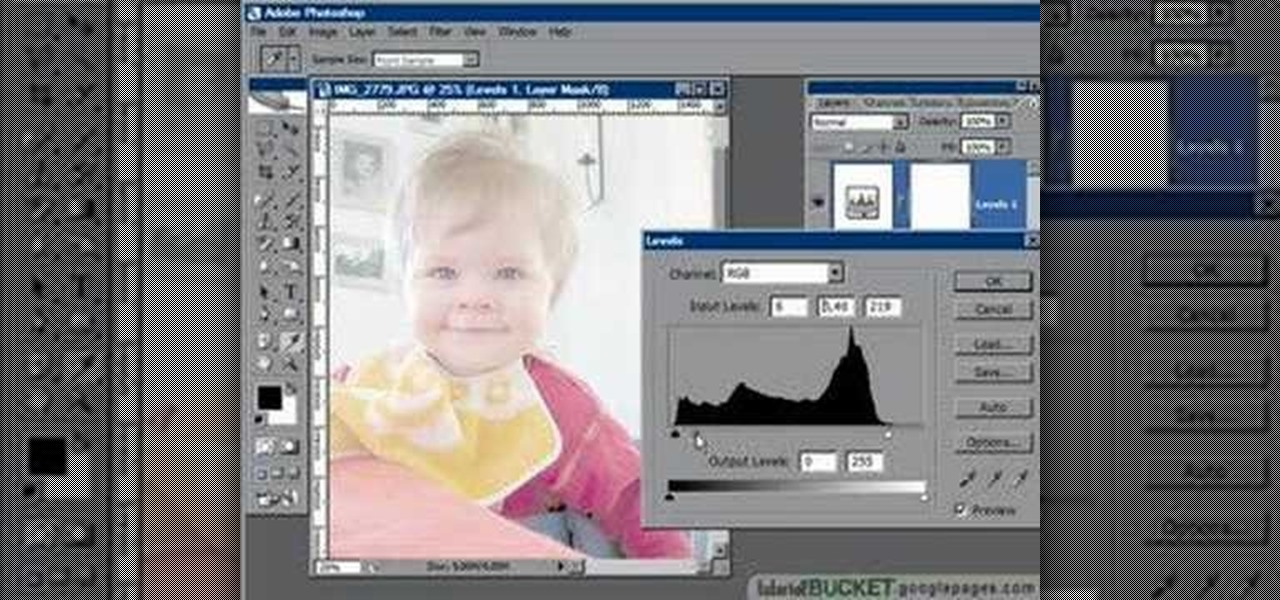
In this video tutorial the instructor shows how to perform basic lighting corrections in Adobe Photoshop. The levels tool is the Photoshop's most used command which has many features to it. Its most basic function is as a lighting correction tool. In this video open an image and work on its adjustment layer so that you do not damage the original picture. Now choose the levels option by right clicking and it shows a pop up window which contains a histogram which shows the population of the col...
This video makes you understand Flash Cookies and teaches "How to remove them" to keep your privacy.

Illustrator is a great tool for creating individual artwork. Creative and clever, it has many functions, one of which is mosaic. If you want to make your illustration or design appear to have a myriad of tiny 'squares' like a Roman mosaic, this guy can help you do it. The short clip explains clearly how to bring the chosen effect to your design. You can see on screen exactly how to do it, so you're not left in the dark, searching every menu for the right tool.

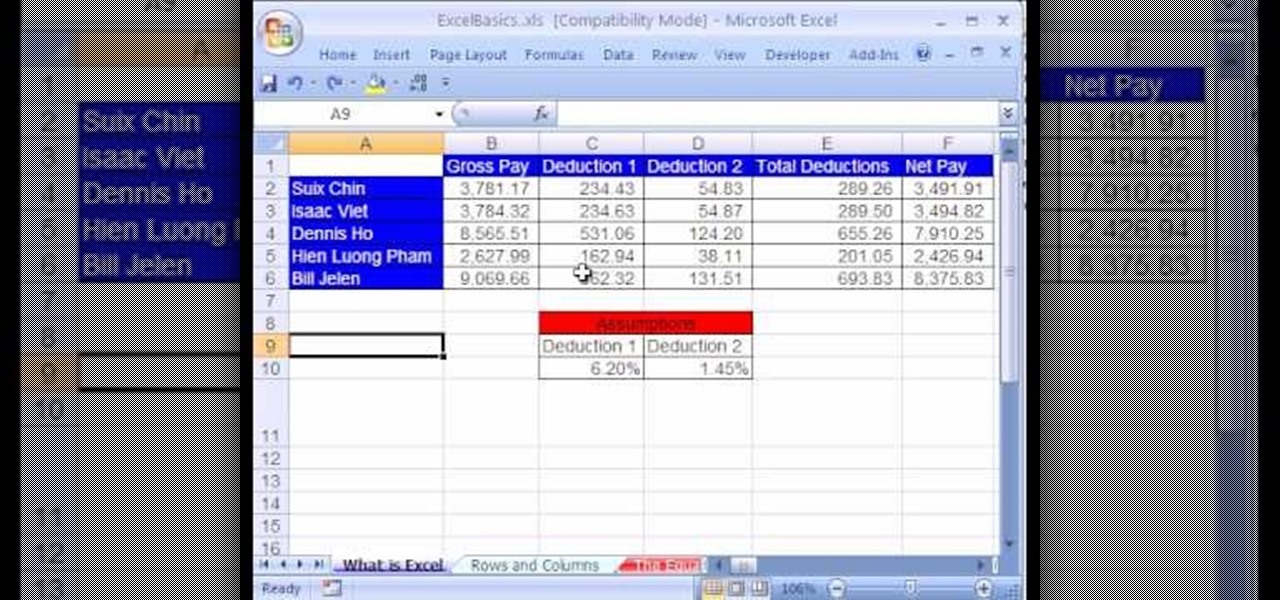
This video is all about the keyboard shortcuts that are used in Microsoft Excel of the latest version. If you really need speed and efficiency then watch this video for its shortcut keyboard buttons. After typing all the data, if you need to see the page setup with the help of the mouse than it will take a pretty long time. By opting for keyboard shortcuts you can save much of your time and can invest it in another work. If you press 'alt' button then it will show keyboard shortcuts on the sc...

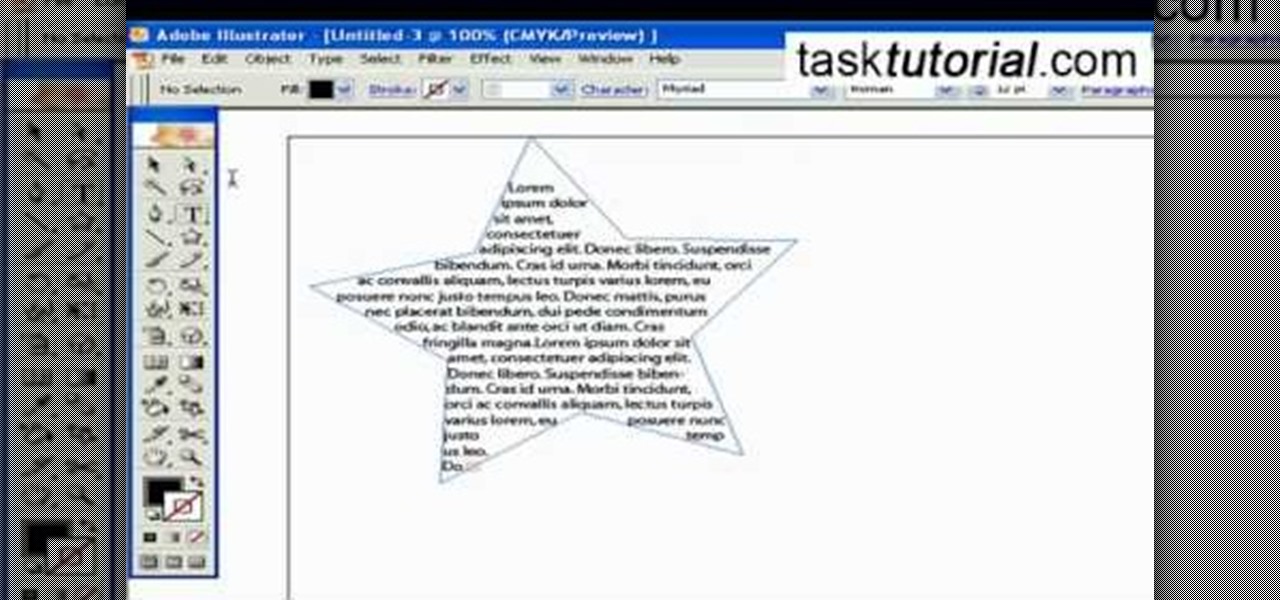
If you want to be serious about using Adobe Illustrator, then learning how to use type is an essential part of your skill set. Type can help you with a wide range of assignments, from designing logos to image building and much more. There are a number of settings and functions when using Type, so it's important to know all of the options that are available to you. This video tutorial will teach you how to use the area type tool in Illustrator.

Most people don't use their cameras to make movies (really bad quality and a sort of user-generated content feel are probably the culprits) but cameras with a record function are great for those impromptu memory-making moments when your dog tries to do a handstand or your grandma unloads the biggest belch ever.

Hacker Defender is one of the most widely deployed rootkits in the world. It is a user-mode rootkit that modifies several Windows and Native API functions, which allows it to hide information (files, processes, etc.) from other applications. In addition, Hacker Defender implements a backdoor and port redirector that operates through TCP ports opened by existing services. This means it is not possible to find the hidden backdoor through traditional means, like launching a remote port scan agai...

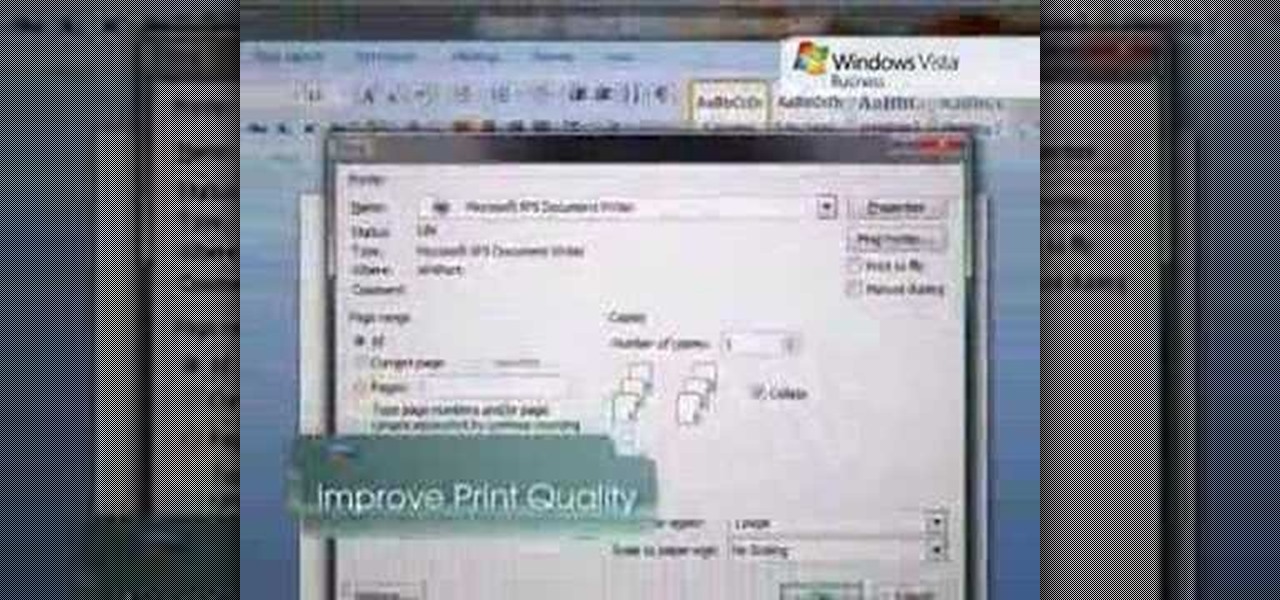
While printers are not normally considered to be at the leading edge of computer technology, these devices have evolved at a lightning pace over the years. Before today's low cost, high-quality inkjet and color laser printers, we used low-quality dot matrix printers and slow laser printers where quality and performance of printing was often questionable. Additionally, documents that looked correct on screen often came out looking differently on paper, due to differences between what the scree...

Cosmo Crow and Mark Hannah take you on a tour of the Sony DSR cameras in these how-to videos. The first video segment deals more with setting up the camera tripod. Then, Mark and Cosmo continue their tour of the Sony Camera with an in depth explanation of the Lens and all its functions. Finish up with the final installment, which will teach you how to operate the switches on the main body of the Sony Camera. Watch this video tutorial and learn how to set up and use the Sony Camera.

Everyone needs a great website. Whether you want to launch the new business you've been dreaming about in 2021, increase your brand's web presence and bring it into the digital realm, or promote yourself and your portfolio, a fully optimized website is the way to do it — and the results can be life-changing.

Whether you want to build your own website for your business, start your new lucrative career in web development, or gain a wealth of projects to add to your portfolio, this course will help you do it. And right now, "The Complete Web Developer Course" is on sale for just $14.99 — a staggering 92% discount off the regular price of $199.

If you're a hacker, pentester, or any other type of Null Byte reader, and would like to create a website to showcase your services and skill set, you may not have the time or energy to do it the long way.

No website, service, or platform is immune to being abused or exploited by hackers, and Google Analytics is no exception. To better understand how Google Analytics can help deliver payloads and bypass security protocols, one might want to learn how to use Google Analytics from a user's perspective first.

On March 13, President Trump announced during a briefing in the Rose Garden that Google was building a COVID-19 screening website to help Americans understand if they might have the new coronavirus. If likely infected, the site would also include the location of a local drive-through testing site to visit. So how can you access the screening website?

The business world is currently figuring out how to deal with the coronavirus crisis, with many offices opting to work remotely for at least the next few weeks as a safety precaution. Predictably, this has thrown remote meeting software back into the spotlight, especially augmented reality solutions.

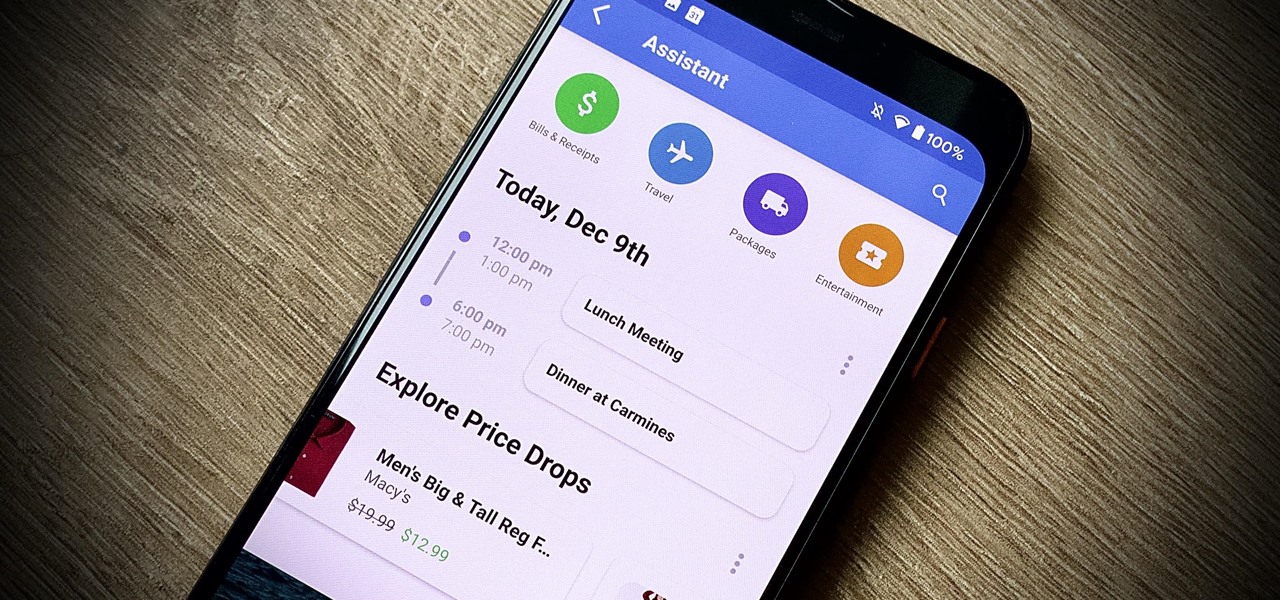
Edison Mail's big Assistant update means more features and functions for you in a convenient, efficient package. One of the most significant changes to come with the 1.17.0 (iOS) and 1.12.0 (Android) updates is calendar functionality for all connected email accounts. Other apps, like Spark, have had this for some time, but we're excited that Edison has finally jumped aboard the bandwagon, too.

Search engines index websites on the web so you can find them more efficiently, and the same is true for internet-connected devices. Shodan indexes devices like webcams, printers, and even industrial controls into one easy-to-search database, giving hackers access to vulnerable devices online across the globe. And you can search its database via its website or command-line library.

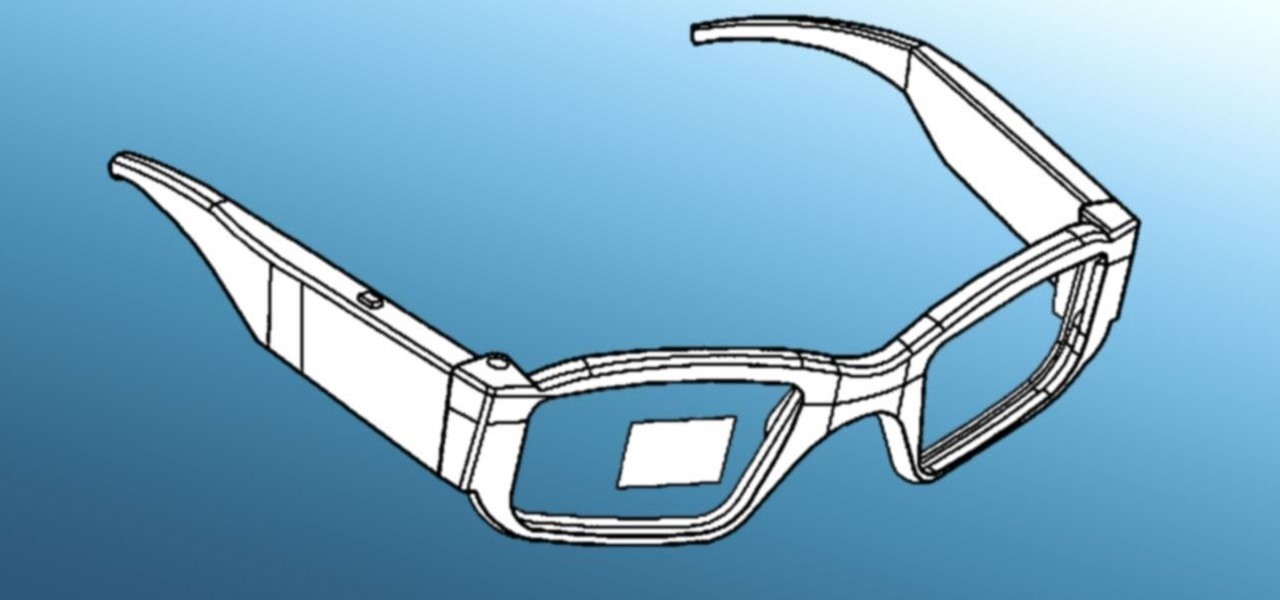
Historically, patents have never been a rock-solid source for uncovering the future of a company's product pipeline. However, sometimes, the images you find in the patent application search archives are so convincing you have to pay attention.

Complex shell scripts can be implanted into photo metadata and later used to exploit a MacBook. In addition to obfuscating the true nature of an attack, this technique can be used to evade network firewalls as well as vigilant sysadmins.

While North has yet to add third-party app support to its Focals smartglasses, the company has been diligent as of late in its efforts to add more functionality to the bare-bones AR device.

Before attacking any website, a hacker or penetration tester will first compile a list of target surfaces. After they've used some good recon and found the right places to point their scope at, they'll use a web server scanning tool such as Nikto for hunting down vulnerabilities that could be potential attack vectors.

The tactic of brute-forcing a login, i.e., trying many passwords very quickly until the correct one is discovered, can be easy for services like SSH or Telnet. For something like a website login page, we must identify different elements of the page first. Thanks to a Python tool for brute-forcing websites called Hatch, this process has been simplified to the point that even a beginner can try it.

One of the headlining features in Samsung's One UI update is a new dark mode that turns stock apps and system menus black. But something you may have missed is what this theme does to the Samsung Internet app and all the websites you visit.

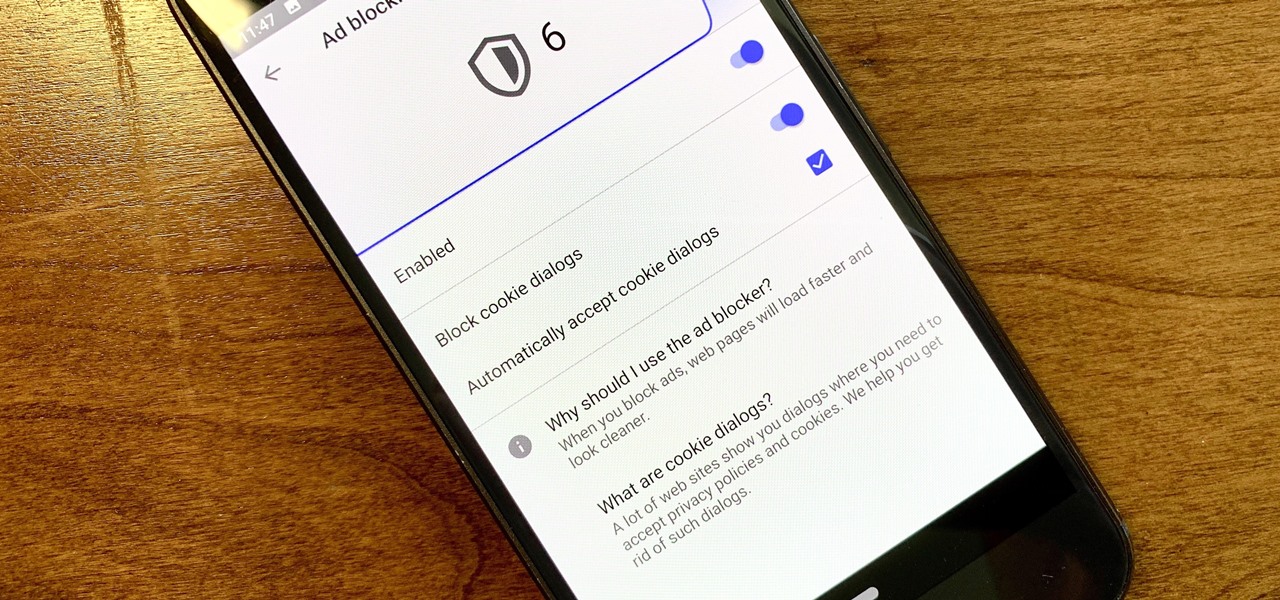
Ever since the GDPR was implemented, it seems every website on the internet needs to inform you of how its privacy policies have changed. If your web browsing experience has been marred by a constant barrage of these cookie pop-ups and privacy dialogs, you should know there's an easy way to block these web annoyances so you never have to tap another checkbox or accept button again.

The latest preview build for Microsoft HoloLens is packed with new sharing features, including support for the Miracast protocol.

Two-factor authentication (2FA) is a great way to add another layer of security to sensitive third-party apps and websites like Venmo. However, before iOS 12, to log into a particular 2FA-secured app or site on your iPhone, you'd have to memorize or copy the SMS code from Messages, then jump back in a timely manner to log in. Apple's latest iOS version streamlines this process.

Enterprise augmented reality software maker Scope AR is bringing the powers of its two productivity apps together like the Wonder Twins into the form of a single app.

When we are building programs that communicate over a network, how can we keep our data private? The last thing we want is some other lousy hacker sniffing our packets, so how do we stop them? The easy answer: encryption. However, this is a very wide-ranging answer. Today we're going to look specifically at how to encrypt data in Python with dynamically generated encryption keys using what is known as the Diffie-Hellman key exchange.

German groups ZF Friedrichshafen AG and HELLA are collaborating to add to their autonomous portfolios with camera and radar development.

We're inching closer towards the singularity—that point where technology advances to the steepest slope of the logistic function S-curve and simply skyrockets at a rate we've never seen before. Somewhere along the way, the line between humans and the tech we rely on will become blurred, and MIT's latest project might very well be a step in that direction.

The biggest corporation we know today is called Google, I bet you've heard of it yeah? How Google Tracks You:

Welcome to the final tutorial of the series on standard C. This article will cover the linked list abstract data type (ADT). There will be a lot of abstraction to try to deliver the understanding in the most basic way for easiest interpretation of what they are and how they work, then we will get into the guts of it and learn the technical code underneath. For those who have yet to grasp the concept of pointers, it's advisable that you do that first before approaching this. Having learned thi...

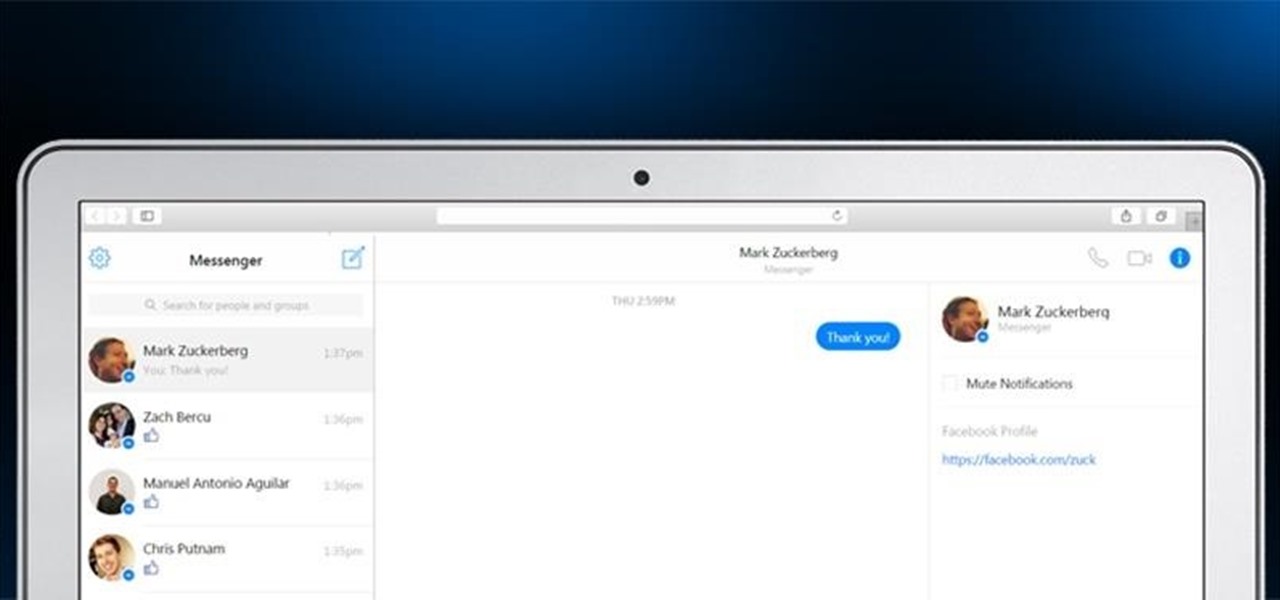
Facebook's Messenger apps for Android and iOS make it easy to navigate between conversations, helps you keep in touch with your friends or heckle your enemies, and even lets you tag yourself or others in the conversation with hilarious nicknames to keep things interesting.

How's it goin'? In this tutorial, we will learn about the security issues of the popen and system functions. I've seen a few people attempting to run command line utilities or whatever it is they require with calls to these two functions but may not know the security implications which come along with it. I will show you using an example from the wargame IO Smash The Stack.

First of all, Merry Christmas and Happy New Year to all Null-Byters that learn and teach in this wonderful site. In this article we will explore the basics of the meterpreter's IRB (Interactive Ruby Shell).

Hello everyone Today I will show a different way to exploit a windows machine with a reverse https payload..."wait...why https? Isn't tcp good anymore?"

Greetings, hackers and friends! I know it has been a while since I posted a tutorial, and hopefully I can make up for that by posting a series.