Learn how to design and create a stunning and unique logo for your business or website, using the gradient tool and texturizer features in Photoshop. Bert shows you everything you need to make a unique logo without Illustrator and just Photoshop.
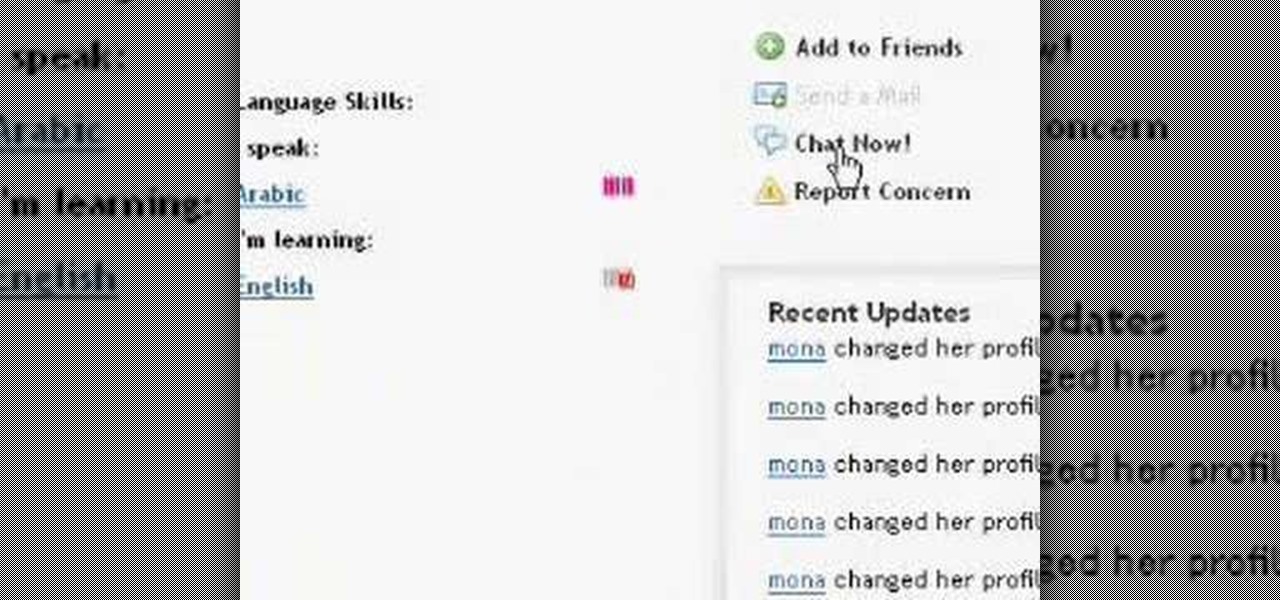
If you're learning a foreign language, it's helpful to have a native speaker to whom you can talk. In this tutorial video, you'll learn how to use italki.com to find a foreign language partner to practice speaking a foreign language. Italki.com is a free language learning website where you can find language partners with whom to practice speaking a foreign language; ask questions about learning a language; share files about language learning, like free textbooks and handouts; and get recommen...
Here's a fast lesson in hosting video on your own Drupal website using the FileField and jQuery Media modules. The Filefield and jQuery Media modules are a one-two knock out combination for allowing users to upload media files to fields in your custom content types and then playing back the media files in their matching player or handler. It represents a positive direction for treating fields containing files and is a great starting point for researching your own implementation of this recipe.

This video shows you how to use Apple iMovie HD to edit and upload your video footage to Vimeo. If you're new to Apple's iMovie and your new to the Vimeo video website, then this is the best tutorial for you.
This video shows different ways to save music from websites onto your computer.
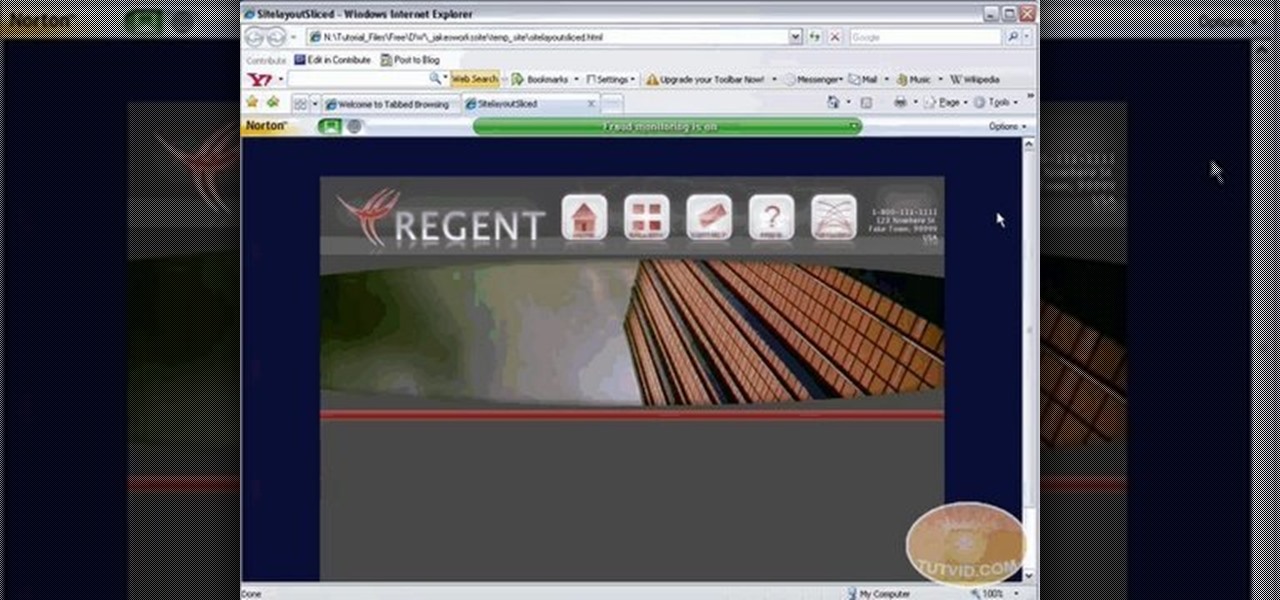
Learn how to export a web layout made in Photoshop and build an editable website layout in Dreamweaver, then convert the page to a template for future use and ease of editing.

Are you celebrating the independence day of your country? How about displaying a flag on your website? In this video tutorial you will learn how to make a flat flag wavy using a displacement map in Photoshop.

Once again, Samsung has certified its flagship Note series with an IP68 rating. With this rating, the Galaxy Note 20 and 20 Ultra have some degree of dust and water resistance.

Mobile privacy is one of the most pressing security issues in existence. Since we carry our phones with us everywhere we go, we need to ensure that we're safe from prying eyes.

So you've been playing Call of Duty Mobile for some time but can't seem to get MVP at the end of the battle. Well, since the game is a competition of players and bots, you're in an uphill battle. But you don't have to languish at the bottom. With the help of these tips, you might just nab your first MVP.

If you have friends who aren't privacy-conscious, you've surely heard the old "What do I have to hide?" excuse. Despite the fact that billions of people are using the internet each day, many of them don't know the dangers that can find them. And many don't know the tools to combat them.

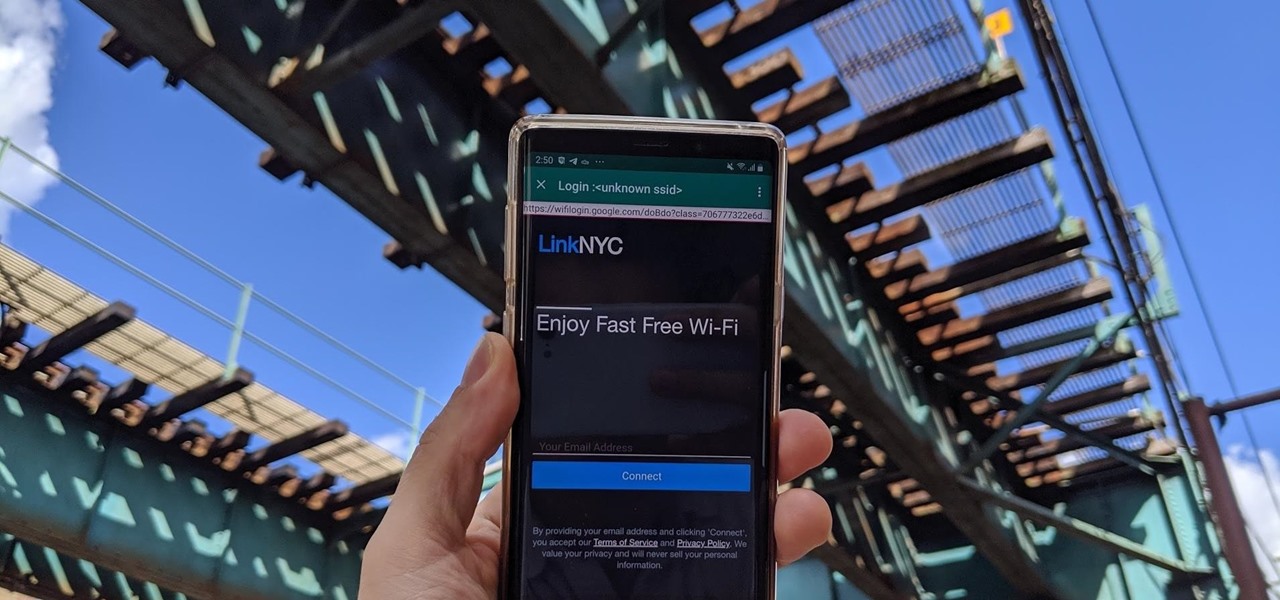
Public Wi-Fi networks that have a captive portal sign-in screen can sometimes be broken on Android. This seems to happen randomly and on some devices more than others. You'll get the "Sign into Wi-Fi network" notification, but it just doesn't work. If that's happening to you, you'll be glad to know an app can help fix the issue.

Apple's iOS 13 for iPhone includes new features in Safari that make browsing the web a little bit better when compared to iOS 12. Some changes are small while others add functionality that just wasn't there before. Plus, there are more security enhancements.

Phishing is the easiest way to get your password stolen, as it only takes one mistake to log in to the wrong website. A convincing phishing site is key to a successful attempt, and tools to create them have become intuitive and more sophisticated. SocialFish allows a hacker to create a persuasive phishing page for nearly any website, offering a web interface with an Android app for remote control.

OnePlus always seems to offer affordable yet powerful tools for videographers of all kinds. The camera hardware itself is crucial, but what's hardware without good software to highlight its real potential? It doesn't matter which version of the smartphone you have, they're all powered by the very same OnePlus camera app.

Stumbling upon a specifically tailored advertisement on your iPhone can be a bit disconcerting. But that's what happens when you let advertisers track your data. Some of you may appreciate more relevant ads in apps, but the rest of you might consider it a straight-up privacy invasion.

Web application vulnerabilities are one of the most crucial points of consideration in any penetration test or security evaluation. While some security areas require a home network or computer for testing, creating a test website to learn web app security requires a slightly different approach. For a safe environment to learn about web app hacking, the OWASP Juice Shop can help.

Just weeks after officially launching its mobile augmented reality toolkit, Google can now claim one of its first Android and ARCore app exclusives with the Curate app from Sotheby's International Realty.

Using just a small sticky note, we can trigger a chain of events that ultimately results in complete access to someone's entire digital and personal life.

Razer just released their first flagship Android smartphone, appropriately named the Razer Phone. While mobile gaming fans are sure to enjoy the Razer Phone, the buttery-smooth 120 Hz display makes this an appealing option for anyone in the market for a new phone. If you've just picked up the Razer Phone or it's piqued your interest, here are ten awesome tips to hit the ground running.

JavaScript is one of the most common languages used on the web. It can automate and animate website components, manage website content, and carry out many other useful functions from within a webpage. The scripting language also has many functions which can be used for malicious purposes, including stealing a user's cookies containing passwords and other information.

After numerous scandals like the Equifax data breach and the 2016 US election, cybersecurity has become a significant issue for Americans. Unfortunately, anytime we use our devices, we're open to a cyber attack — especially when we browse the web. However, there are ways that we can make it harder for hackers and data miners.

Dirty, malformed, and outright mischievous text strings have long been the enemy of interactive website developers. Strings contain any combination of letters, numbers, spaces, and punctuation, and are entered into text boxes on websites by users. These strings in particular can do everything from highlighting XSS vulnerabilities to soliciting 404 error pages.

We're inching closer towards the singularity—that point where technology advances to the steepest slope of the logistic function S-curve and simply skyrockets at a rate we've never seen before. Somewhere along the way, the line between humans and the tech we rely on will become blurred, and MIT's latest project might very well be a step in that direction.

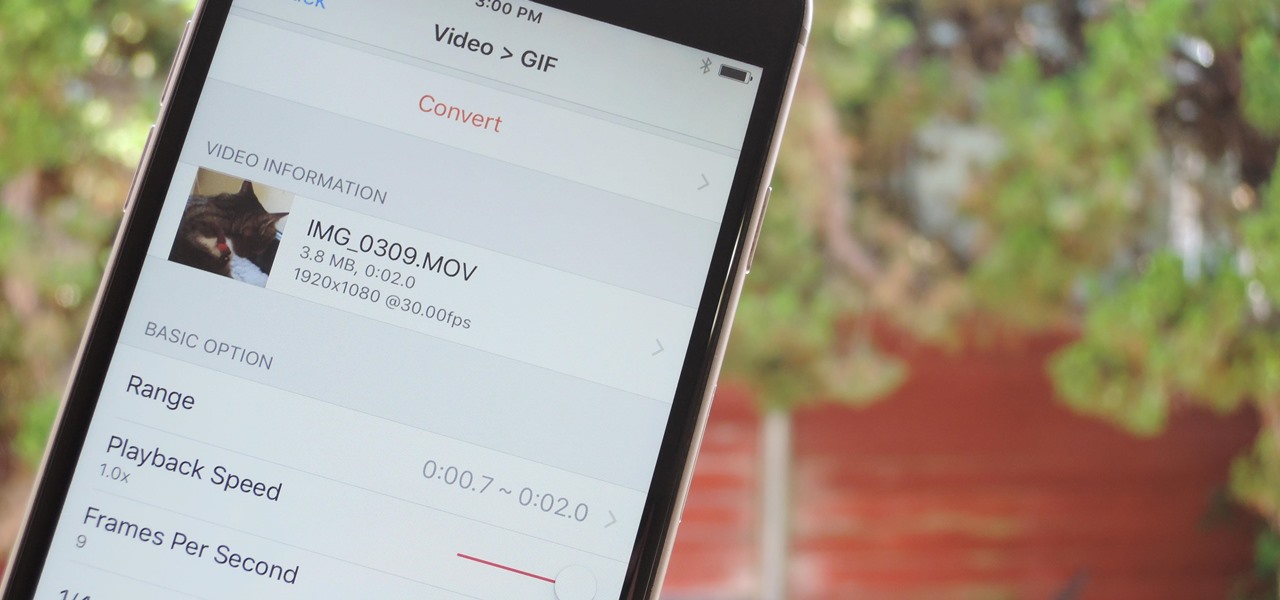
The internet has officially been taken over by GIFs—they're everybody's favorite method of communication these days, and nary a meme would exist without them. But even with the abundance of GIF-sharing websites, and even GIF keyboards, we're still a bit lacking in regard to creating GIFs on a mobile device.

Three smart devices shown at CES 2016 are making it easier for you to make stupid decisions. PicoBrew, Somabar, and 10-Vins demonstrated their systems for beer, mixed cocktails, and wine, respectively, and each one is attempting to change the way we enjoy our favorite potent potables at home.

There are a bunch of new and interesting features packed inside of Windows 10, but one of the most exciting ones is the Microsoft Edge web browser, the long-awaited replacement of Internet Explorer.

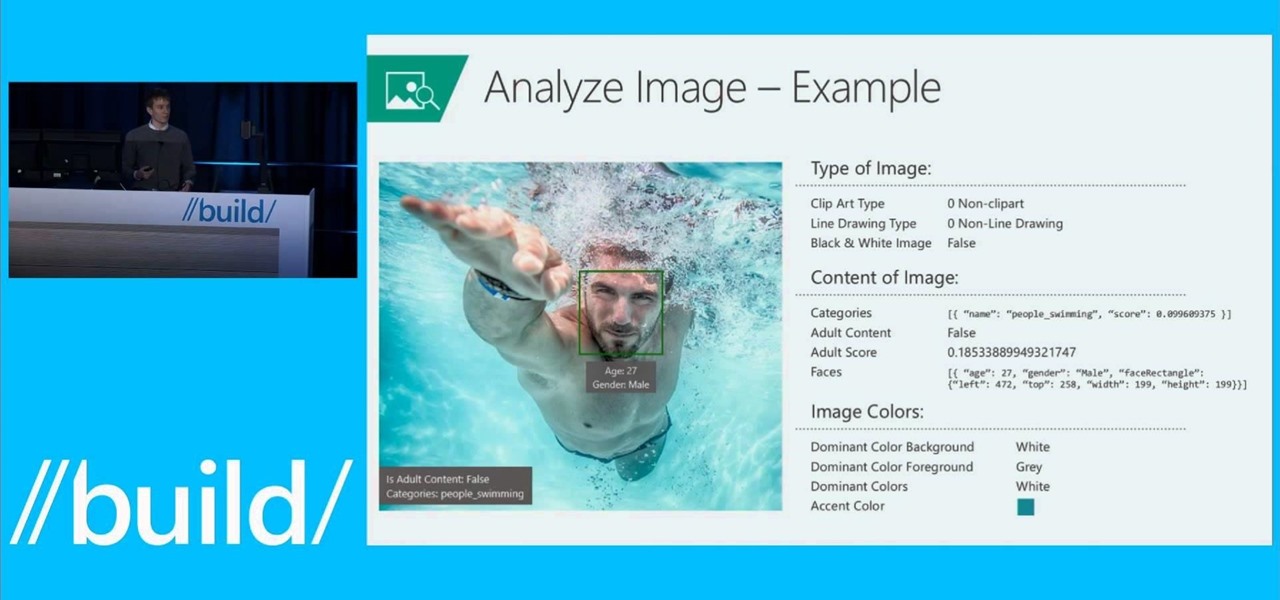
Microsoft is developing a new API project called poject "Oxford," and it includes face, speech, and more "smart" API technology. Despite being Microsoft, I actually found this to be very useful. ;)

Recently, a group of Duke University students got together to tackle an age-old problem with mobile devices. You see, mobile data coverage isn't exactly ubiquitous, and many folks have restrictive mobile data plans, which means internet connectivity is not always an option.

Welcome back, my novice hackers! In my series on cracking passwords, I began by showing off some basic password-cracking principles; developed an efficient password-cracking strategy; demonstrated how to use Hashcat, one of the most powerful password-cracking programs; and showed how to create a custom wordlist using Crunch. In this tutorial, I will show you how to create a custom wordlist based upon the industry or business of the targets using CeWL.

T-Mobile continues to make waves in the U.S. wireless market behind CEO John Legere's UnCarrier program. At the latest installment in a series of industry-challenging announcements, Uncarrier 5.0 unveiled Test Drive. The new program is set to allow would-be customers to try out the "latest generation" iPhone for seven days on T-Mobile's network without any financial commitments.

In a era where cyber security is becoming increasingly important, Comcast has decided to use its customers' routers to provide hotspot access to the public. A new program, outlined by Dwight Silverman over on the Houston Chronicle website, seeks to provide Xfinity customers with city-wide Wi-Fi hotspots by using, well...other customers' wireless routers.

Netflix has received a lot of publicity lately, and not because of its impressive worldwide library. From blog wars with Comcast to streaming deals with Verizon, it's easy to forget that the company exists for our entertainment, but sometimes that entertainment has drawbacks.

Welcome back, my novice hackers! There are SOOOO many ways to hack a system or network, which means you need to think creatively in order to be successful.

In this web design tutorial learn how to use the straight line tool. Although the straight line tool might seem like a useless tool I can tell you from experience it is very useful. Especially if you have ever attempted to draw a straight line with a tool other than the straight line tool. There are many ways you could use the straight line tool such as dividing content, design graphics, separating navigation menu headers and much more. My recommendation would be that you take a look at some ...

There are a number of reasons why you might want to trick a web server into thinking you're on a different operating system (OS) or web browser. One might be that you want to test the mobile version of your website from your computer. Or perhaps for some reason a website is restricted to a certain OS or browser and you wish to circumnavigate that barrier. Today's guide shows you how to do just that!

When browsing the web, I enjoy my privacy. It's reassuring that I can peruse the internet without the worry of having my activity tracked back to me, allowing me to leave fun, anonymous comments when I get the urge to troll.

Check out this informative video tutorial from Apple on how to add a photo album in iWeb '09.

Check out this informative video tutorial from Apple on how to add a countdown clock in iWeb '09.

Right out of the box, iPhone is incredibly easy to use. If you want to get the most out of every feature, you’ve come to the right place. This video tutorial straight from Apple will teach you how to browse the web with Safari on the Apple iPhone 3G. The iPhone redefines what a mobile phone can do.