Your social security number, credit card information, and medical history can fall into the wrong hands if you're not careful about how and where you share your data online. If you really care about your data, there are tools and techniques you can utilize to protect yourself from cyberstalkers, advertisers, and hackers in a time when digital lives are a high commodity.

During the keynote at WWDC earlier this year, Apple introduced the latest iteration of its mobile operating system, iOS 12. Despite a thorough demo on stage, Apple glossed over new eye tracking features that use ARKit 2. Developers can now use the TrueDepth camera on the iPhone X, XS, XS Max, and XR to determine where your eyes are looking, opening up incredible new possibilities for new apps.

Reconnaissance is the phase of an attack where a red team or hacker designs a strategy based on the information they can learn about the target, as well as what the available attack surface looks like. These scans can take time to discover relationships, but Raccoon OSINT scanner coordinates multiple automated scans to produce invasively detailed reports on a target with a single command.

A convincing domain name is critical to the success of any phishing attack. With a single Python script, it's possible to find hundreds of available phishing domains and even identify phishing websites deployed by other hackers for purposes such as stealing user credentials.

Identifying vulnerable devices and services on a target router can be difficult without leaving logs and other traces of an active attacker on the network. However, there is a way to covertly decrypt and view Wi-Fi activity without ever connecting to the wireless network.

Google updates the Play Store periodically, but the changes are usually subtle. A recent server-side update, however, is shaking things up quite a bit.

Netflix currently lets parents block content based on maturity rating, but it isn't a perfect system. Not all titles rated PG-13 are equal, for instance. That's why it's good news that Netflix is adding more controls for parents, by allowing account holders to bar individual movies and TV shows they deem inappropriate.

In just a few months, Binance has experienced explosive growth, overtaking its rivals to rank among the top three cryptocurrency exchanges in the world by trading volume. Without a doubt, Binance is now among the best sites for trading alt-coins like Ripple (XRP), Stellar (XLM), and NEM (XEM) to name a few.

When it comes to streaming your favorite movies and TV shows, there aren't many media players that are better than Kodi. With its fast performance and easy-to-use interface, it is definitely one of the best options. But what really sets it apart is its ability to add functionality.

So, you've gotten (or are getting) a shiny new iPhone 8 or 8 Plus. Congratulations! It's got great new features including the new A11 Bionic chip, wireless and fast charging, and portrait lighting. And let's not forget a much better battery ... right?

Nineteen days ago, several hundred people could have been exposed by a traveler with measles in Nova Scotia, Canada. The next day, someone flying from Minnesota to Nebraska may have spread the measles to other passengers. A couple weeks ago, it's possible that a man and his six-month old child spread the measles in several Seattle-based locations. Authorities are trying to locate persons who may have been in contact with these people. None of the persons with measles were vaccinated. Why?

New technologies in current-generations smartphones allow for much faster charging—Qualcomm Quick Charge 3.0, VOOC Flash Charge, and USB Type-C, for instance, can charge a phone up to 4 times faster than traditional methods. However, the majority of phones on the market still don't support these standards. So for the rest of us, I'll go over an easy tip that can charge any smartphone as much as 25% faster.

Welcome back, my greenhorn hackers! Throughout this series on Metasploit, and in most of my hacking tutorials here on Null Byte that use Metasploit (there are many; type "metasploit" into the search bar and you will find dozens), I have focused primarily on just two types of modules: exploits and payloads. Remember, Metasploit has six types of modules:

If you have a specific app you want to lock so that others can't access it, the most secure way of doing so is with biometrics. While there are options to lock apps with either a PIN or pattern, these can easily be figured out with a simple glance over your shoulder. It's much more difficult for someone to crack your fingerprint ID, unless they chop off your finger, of course.

Rumors have had Google making a foray into the mobile carrier world for quite some time, but today, the Mountain View tech giant finally made things official. The new service, dubbed Project Fi, will be a Mobile Virtual Network Operator, or MVNO, that uses existing Sprint and T-Mobile cell towers.

Once your furniture is finally moved in, settled upon a spot, and used for comfort or leisure, chances are it won't move very often. We tend to leave—and use—our furniture in the same spot for years, which can leave signs of great wear beneath, deeply indenting our carpeted floors and fancy rugs.

Each morning, we spend a significant portion of our time staring into the mirror. From choosing clothes and accessories to perfecting our hair, we try to make ourselves attractive. Yet catching others' attention doesn't have to rely on preening and primping. There's some truth to the maxim of beauty in confidence—all you need to make yourself more attractive is spray on your favorite scent.

When exercising at a high intensity, you know to expect some level of pain. That can make it difficult to identify when your body gives you a warning sign of injury. If you pay close attention, however, you can tell the good hurt from the bad. I talked to Dr. Brian Parr again, professor at the Dept. of Exercise and Sports Science at the University of South Carolina Aiken, who explained which symptoms of exercise are normal and which are bad:

so i have just signed up to this, and i dont know much about this website but i wanted to show my recent upload

Custom Timelines (CTs) allow you to control exactly which Tweets appear in a column on Tweetdeck. So if a particular event catches your eye as newsworthy you can tailor your CT to show what you consider to be the most relevant Tweets. These CTs can then be customized, shared and embedded on your website. This is a great way of increasing interaction on Twitter and sharing current, interesting and breaking news stories from any niche or subject

There's one reason why most of us have a Samsung Galaxy S3—because we don't want an iPhone. Yes, there are some pretty cool things about the iPhone aesthetically, but looks aren't everything. Anyway, with the nearly unlimited customizations options we have available for Android, cloning the iPhone-look is no problem—even the lock screen.

How to Henna Your Hair Tutorial Pt.2 Please Dont forget to Watch Pt. 1

Video: . How to Henna Your Hair Tutorial #1

Very interesting interview with the editors of the New York Times Lens Blog, a website which is totally dedicated to photojournalism and videojournalism.

Welcome back, my novice hackers! Most of my tutorials up until this point have addressed how to exploit a target assuming that we already know some basic information about their system. These include their IP address, operating system, open ports, services running, and so on.

Learning how to use other text panels in the designs gallery. This website design tutorial will teach you how to add a note panel, numbered panel and one additional text panel.

This web design Tutorial will walk you through process of linking to files on your computer. You can link file types including but not limited to Microsoft Word, PowerPoint, PDF, Videos and so on for download on your website.

In this web design tutorial we will show you how to protect yourself from losing your work just in case the program malfunctions, computer crashes or you accidentally forget to save document and so on. I highly recommend you utilize this Web Design Tutorial especially if you are working on large websites for clients.

There is a substantial number of helpful tools at your disposal in Microsoft Word when it comes to writing; grammar check, word count, dictionary, thesaurus, and tons more. One tool that doesn't necessarily make itself obvious is testing your document's readability. With this built-in tool, you can not only check your spelling and grammar, but also the reading level of your document.

This Professional Website design Tutorial will show you how to place text on a curve using the line tool. However you can put text on the outline of shapes and other objects.

In this web design tutorial learn how to repel text around objects. This Professional website design tutorial will also explain why it is important to have the objects in proper order for the repel function to work properly.

In this Web Design Tutorial you learn how to convert the mouseover state into a navigation menu. Once the navigation menu is created you will be able to use the navigation bar properties to make additional modifications to your website menu.

In this web design tutorial you will learn how to manage web design layers efficiently by using solo mode, hiding layers and locking layers. This Xara Web Designer tutorial will show you the importance of using these features to manage your website design.

In this video we're making a weather predicting light! Good luck! Video: .

Did YOU know...that African Americans have the highest rate of colorectal cancer, and that it is more likely to be advanced at diagnosis? The age for colonoscopy in ACG guidelines dropped to 45 for African Americans in 2009. This digestive ditty about colon cancer screening in Black Americans pays homage to Beyonce's iconic Single Ladies video. Help us to get the word out--Email this link to your African American colleagues and friends and post it to your Facebook or Twitter pals! We can prev...

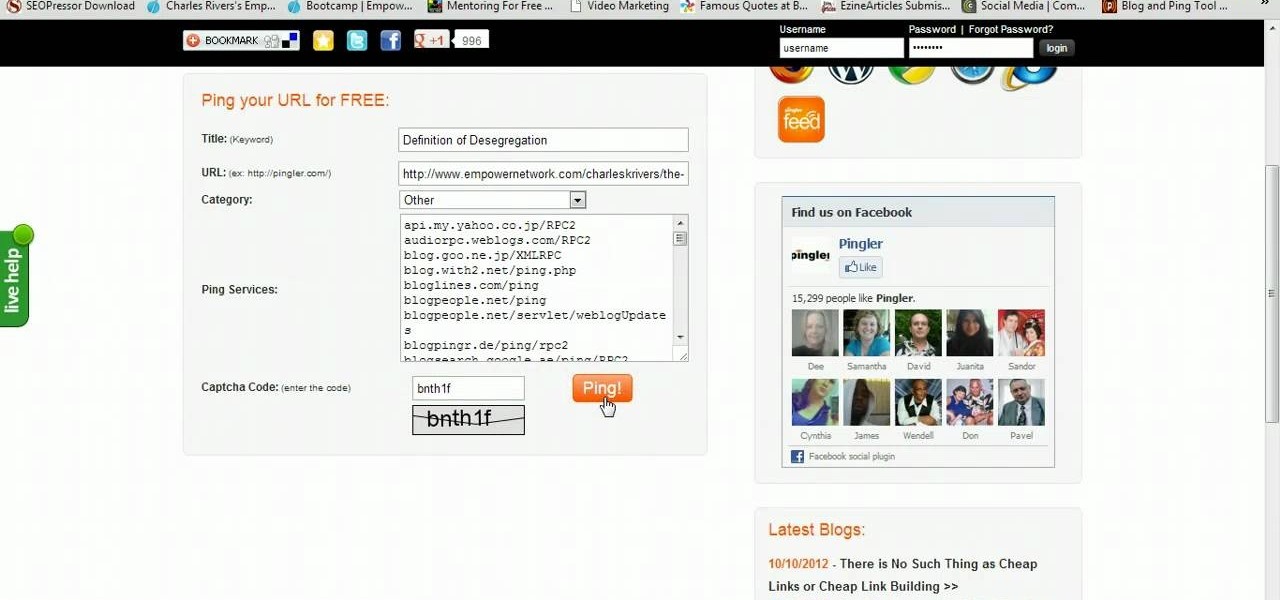
There are many people on the web today who, when they submit content wait for the search engine spiders to crawl and find out the content on their site has been updated. Wouldn't you like to know how let the search engines know ahead of time that your content has been udpated? In this short video I show you exactly this simple process of getting more attention to your sight than ever before

Wall framing. How to frame a wall. Whether you're re-sheeting an old wall or building a new timber frame wall, before you install the plasterboard or drywall, take the opportunity to have a really good think about what services or insulation qualities you might want to have in that space. There are issues to consider like electrical, plumbing, noggins for wall fixtures and insulation.

How to Draw a Mech. Watch me progress throug a mech drawing. I am very influenced from fantasy art. For more detail, please look at my art website at:

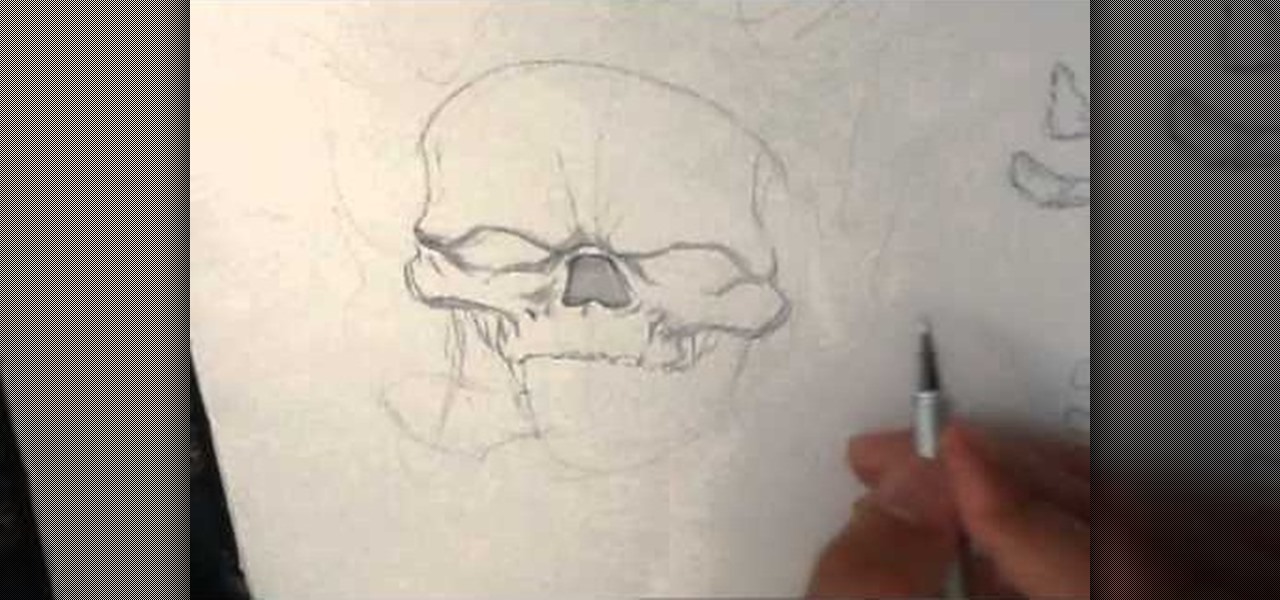
How to Draw a Skull on Fire, Drawings of skulls on different websites vary. In this video i draw a Skull on fire for tattoo art. Easy things to draw when you are really into skulls. Drawing sites like this are here to help. Go here: http://howtodrawfantasyart.blogspot.com/