In the battle for best stock Android flagships, there are really only two choices: Google Pixel phones and OnePlus phones. Although the latter isn't true stock Android, it is impressively close and usually paired with more impressive hardware than the Pixel lineup. The latest is the OnePlus 6T, which will be a bit controversial for fans this year.

With all the controversy around the Pixel 3 XL, the regular-sized Pixel 3 might be the phone of choice for most users. Thanks to the huge boost in screen size, the little brother is now an easier pickup for those who like a bigger screen. And once more, the internals are the same, giving you the same experience as the 3 XL without the display notch.

The "controversial" Pixel. No phone in the history of Google's Pixel lineup deserves this title more than the Pixel 3 XL. For some (including myself), the design is a welcome change that embodies the modern design of 2018 flagship phones. For others, it has an ugly huge display notch that destroys symmetry.

Apple's successor to the iPhone X is a beautifully made smartphone with much of the same characteristics, including a 5.8-inch OLED screen, two storage choices, and Face ID. But many features set the iPhone XS apart from its predecessor, as well as the other 2018 lineup of iPhones, making it a worthy choice to upgrade to if you're in the market for a new mobile device.

Think back to when you last wanted to transfer some music or videos to your friend's smartphone and how difficult and slow it was. As powerful as our phones are, the default file sharing options are limited. There are, fortunately, some better options which make moving files easy, secure, and painless.

It's possible to stream a MacBook's entire computer screen without using Apple's Screen Sharing application and without opening any ports on the target device. A hacker with low user privileges on the backdoored Mac may be able to view a victim's every move in real time no matter where they are.

Apple's next big developer event happened on June 4, and it was the first glimpse of iOS 12 that anyone's seen. While there were lots of rumored features to be unveiled at WWDC 2018, Apple concentrated mostly on squashing bugs and making iOS work as seamless as it did years ago. Still, we had hoped that Apple would have added these features in iOS 12, but only a few made the cut.

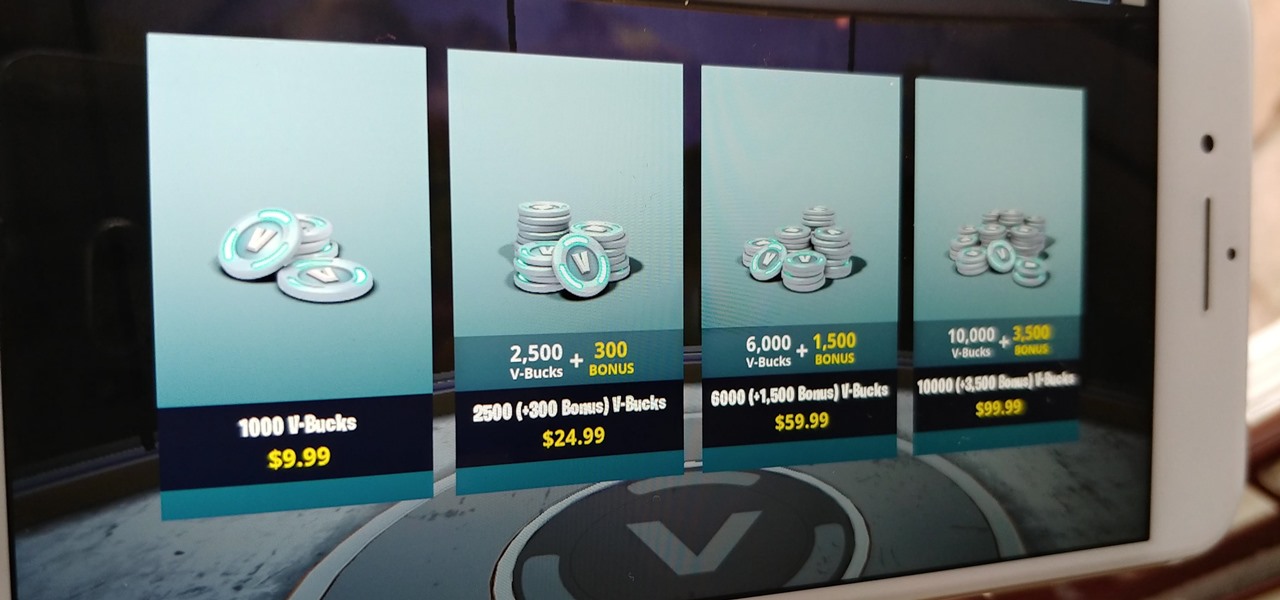
Thanks to its free-to-play strategy, many items in Fortnite Battle Royale require V-Bucks, the in-game currency. You can purchase V-Bucks with real-world money, but many would rather earn V-Bucks instead of getting nickeled and dimed by micro-transactions. While limited, there are a few ways to earn free V-Bucks in the game.

Your iPhone has a lot of personal information contained within it, so of course you want your device to be secure. You don't want that information getting into the wrong hands — or any hands other than your own, for that matter.

On April 7, 2017, residents in Dallas, Texas, woke to the sound of emergency sirens blaring all over the city. No one could shut them off, and after repeated efforts to contain the situation, the city had to shut down the entire system. While the media reported a sophisticated computer hack was responsible, the truth was much less high-tech.

Apple just unveiled a red iPhone and iPhone 7 Plus, dubbed the iPhone 7 (PRODUCT)RED Special Edition, to commemorate the ongoing global fight against AIDS. Apple fans the world over are sure to swarm in and gobble up the initial stock shortly after the new color is released at 8:01 a.m. (PDT) on March 24, 2017, so we'll go over some tips to help you secure a red iPhone before it's sold out.

We're nearly done getting our Mac set up for hacking. If you haven't checked out previous tutorials, I'd recommend you do so first before diving right into this one.

There's a lot of great things to be excited about with iOS 10 on your device. You can remove annoying stock apps, search emails better, remember where you parked, and much, much more. Seriously, there's actually more outstanding features in iOS 10 than in Apple's latest iPhone 7 models.

It's always a pain to make sure you have enough storage on your smartphone. Pictures and videos occupy a lot of space, so your music library has to take a back seat—otherwise, you might see that pesky "Storage Full" notification at any time.

Hello NullByte! This will be my first How To series.

In this day and age, maintaining your privacy is a perpetual battle, and doing so with an internet-connected device like your smartphone is even more of a struggle. Every website you visit, every app you install, every message you send, and every call you make is a potential vulnerability that could expose you to prying eyes.

Welcome back, my hacker apprentices! A you know, Mr. Robot is my favorite TV show this year, and not just for the realistic hacking. Rami Malek, the actor who plays Elliot, is incomparable in his depiction of a young man with social anxiety who is alienated from a superficial, materialistic society and wants to make a better world. I believe we will see a lot more of this actor in coming years.

Edit: Some of the methods I show you may be difficult, or not work at famous or high quality hotels.

While most of us don't think twice about dragging a pattern or using Touch ID to open our phones, or entering a password in for our email and bank accounts, these features are there to protect some of our most private information. Only problem is, they don't do a good job of it.

What separates the work habits of the ultra-productive from us mere mortals struggling to check items off our never ending to-do lists? While the answer to that question is by no means simple, one undeniable factor in their success is a clearly defined, highly organized workflow.

Welcome back, my neophyte hackers! Many newbie hackers seem to be confused regarding the process or methodology to employ a successful hack. Most want to simply go straight to the exploit without doing the due diligence to make certain that the hack will work and you won't get caught.

Welcome back, my fledgling hackers! A short while ago, I did a tutorial on conducting passive OS fingerprinting with p0f. As you remember, p0f is different from other operating system fingerprinting tools as it does not send any packets to the target, instead it simply takes packets off the wire and examines them to determine the operating system that sent them.

For over 20 years, a tiny but mighty tool has been used by hackers for a wide range of activities. Although well known in hacking circles, Netcat is virtually unknown outside. It's so simple, powerful, and useful that many people within the IT community refer to it as the "Swiss Army knife of hacking tools." We'll look at the capabilities of Netcat and how the aspiring hacker can use it.

You'd think the ability to block calls from certain numbers would be built in to most phones by now, but that's certainly not the case with the iPhone.

YouTube is the third most popular website in the world, after Google and Facebook. Millions of subscriptions happen each day on YouTube, with over 800 million unique users visiting each month. In that timespan, roughly 4 billion hours of video are watched, with 72 hours of video uploaded every single minute.

An internet connection has become a basic necessity in our modern lives. Wireless hotspots (commonly known as Wi-Fi) can be found everywhere!

So your friend started humming "Who Let the Dogs Out" and now you CAN'T get it out of your head. Oh yes you can! This helpful little video shows you what unhearit.com can do for you. This website generates random catchy tunes, so you can dump what's in your head and move on to something fresh. Here comes Lady Gaga!

Tired of running around and destroying blocks with a sword? Or your fist? Looking for a solution that involves explosives, a little ingenuity, and a much faster destruction rate!? Well, you ask, and you receive! In this video you will learn how to make your very own canon! Just remember, the water is NECESSARY to keeping the canon intact, since it absorbs the shockwaves of the TNT. Enjoy!

How to track an email address. Useful if you meet someone who says they are from somewhere e.g. LA as given in the video and you don't believe them. Go to the Rate a Bull site type in their email address and then hit return or 'find them'. The site will give you options to see information about them on the internet, MySpace, Facebook or other site or track the email. The site gives instructions on how to track the email via outlook, outlook express and other mail programs and the video shows ...

Try This! Very funny phone trick for your friends! Learn how to use the website phonetrick.com to prank call your friends. Instructions are simple.

SalaryExpert.com or Salary.com are two great Websites designated to informing people of expected salaries of particular job fields, so people know what to expect when offered a salary. Know what salary amount to expect when being offered a job in a particular job from a career adviser in this free video on job guidance.

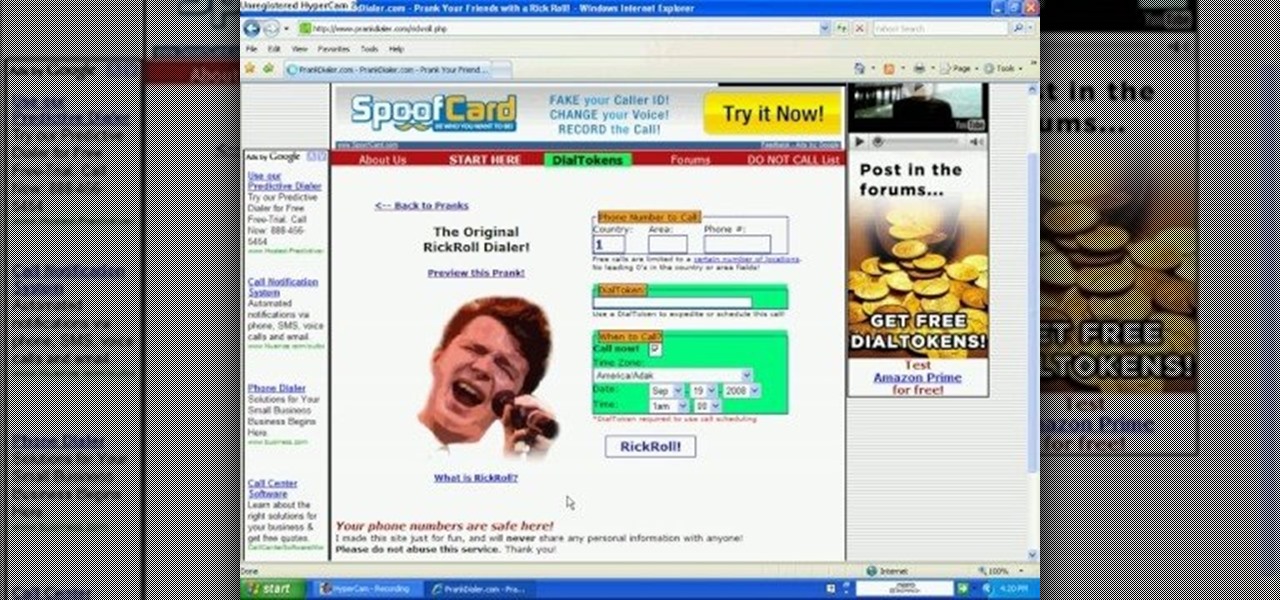
This video tutorial will show you how to make a crank call without a cell phone or a land line rotary... all you need is the Internet... the glorious Internet, and a little known website called prankdialer.com. Youcan't make any kind of prank call you like, you can even Rick Roll somebody with "Never Gonna Give You Up." After you dial and send the crank call, all that's left is to laugh.

This tutorial shows you how to create a pitch bend effect in Ableton Live. There is a problem in doing the pitch bend effect as shown in the video: All gets out of midi sync. This is EASY to fix. Follow these steps:

A long series of code is required to hack any JavaScript web page. Watch this video to learn how to hack a Java website to edit it for your pleasure.

A short tutorial on how to use the ip deny manager to deny the access to website from particular IP address using cPanel. This Video is provided to you by scandicsoft,(wwww.scandicsoft.fi)

If you want a calendar of events on your website, or just want everyone to know what you do all day, this video is for you. Learn how to embed your Google Calendar in a webpage using Contribute software.

A quick guide on using the wonderful internet tool StumbleUpon - a great way to find new and interesting websites.

This tutorial is perfect for updating your website for that Halloween theme, or perhaps you just need a spiderweb. Whatever it's for, if you need to make a spiderweb in Flash, you'll want to watch this video.