How To: 5 Apps That Let You Make Calls Without Giving Out Your Real Number
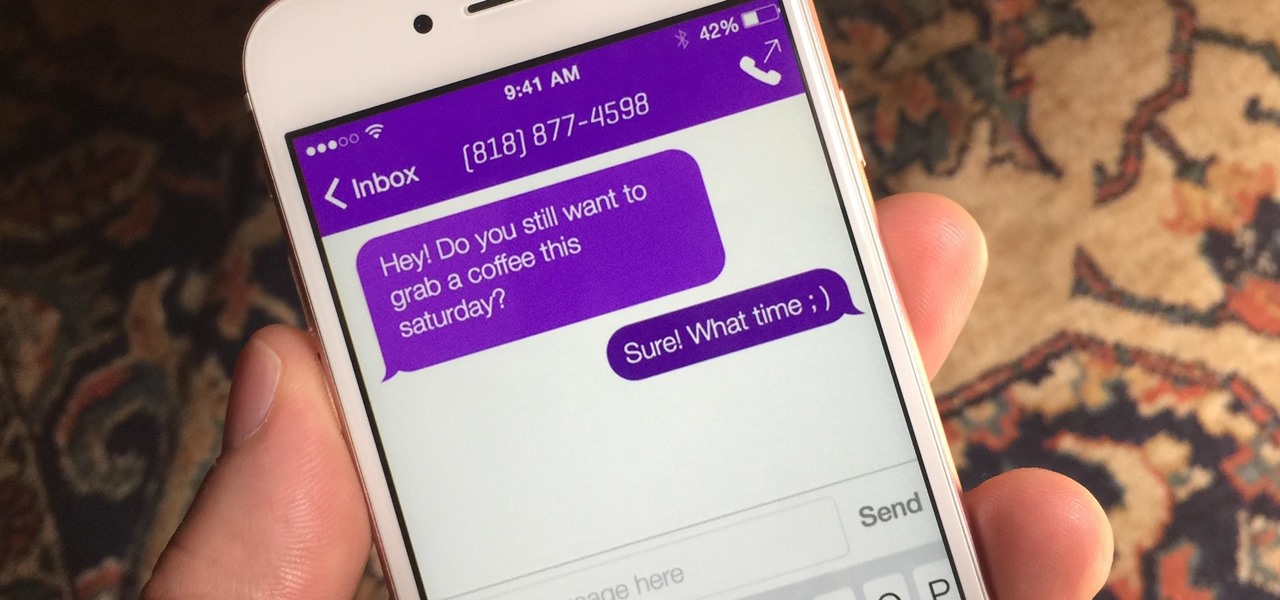
Throwaway phones aren't just for seedy criminals and spies—they can be useful for many everyday situations.


Throwaway phones aren't just for seedy criminals and spies—they can be useful for many everyday situations.

The HTC Vive and Valve's SteamVR make for one of the more compelling virtual reality experiences, mixing in real-world motion tracking with the immersive headset. But third-party manufacturers couldn't tap into the Vive's full potential and make creative new peripherals—until now.

Snapchat has already found a compelling way to create advertisements in augmented reality with their branded filters, but they continue to experiment with new ways to monetize the bridging of the real and digital worlds. Their latest idea, which requires users to "snap" an image to unlock content, could succeed where QR codes haven't.
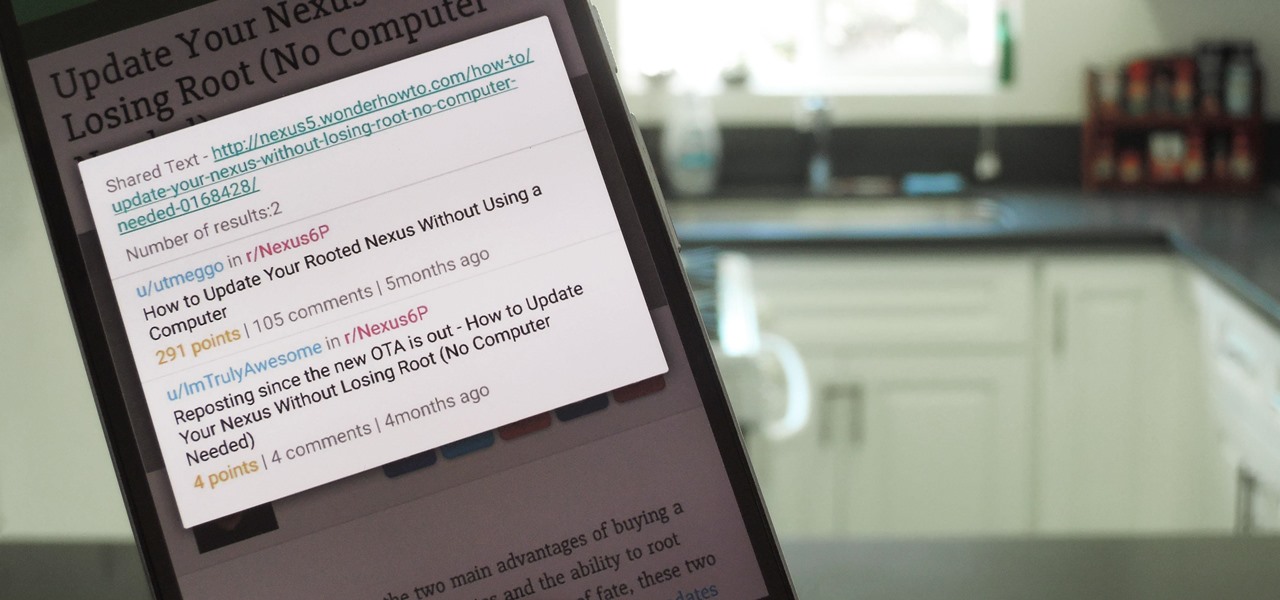
When you want to read product reviews, you go to Amazon—regardless of whether or not you intend on buying the product from their website. By the same sense, when you want to read discussions about certain topics you come across on the internet, there's no better place than Reddit.

Like previous installments in the Pokémon series, as you progress through Pokémon GO you'll be able to evolve your Pokémon into more-powerful monsters with new and more-damaging attacks. However, unlike older entries in the series, your Pokémon won't simply evolve when they reach a certain level. Instead, you'll have to "feed" them a certain amount of character-specific candy to induce the transformation.

When the Samsung Galaxy S7 and S7 Edge came to market in 2016, they were universally praised as being the pinnacle of Android smartphone design, even topping Consumer Reports' smartphone ratings.

Pokémon GO, the biggest augmented reality sensation ever, broke app store records this opening weekend. But it also did something even more important: it gamified physical activity.

The Moto X and Moto Z have a set of features that let you launch common shortcuts by shaking your phone in one direction or another. For instance, there's a chop gesture that turns on the LED flashlight, and a wrist-twist gesture that instantly opens the camera app.

This week has been quite a successful one for Google, thanks to non-stop news coverage of their developer-focused I/O conference.

Verizon customers who use the Samsung Galaxy S7, beware: a recent update installs new bloatware over your existing bloatware that installs new bloatware. Confused or pissed off? You should be, as this app can install new apps onto your phone without you knowing.

The desktop browser market has some stiff competition going on, but Opera has always been able to maintain its market share by offering innovative features such as a data saver option. With over 350 million users, it's safe to say folks are appreciative of the efforts being made by the web browser's development team.

Apple's MacBook line of laptops is quite famous for their extensive battery life, thanks to various technologies that Apple has utilized. However, all things must pass, and over time your MacBook's battery will degrade. Certain use scenarios can accelerate the degradation of the battery—from excessive usage to high temperatures to overloading the system—and this can all lead to the untimely obliteration of your battery.
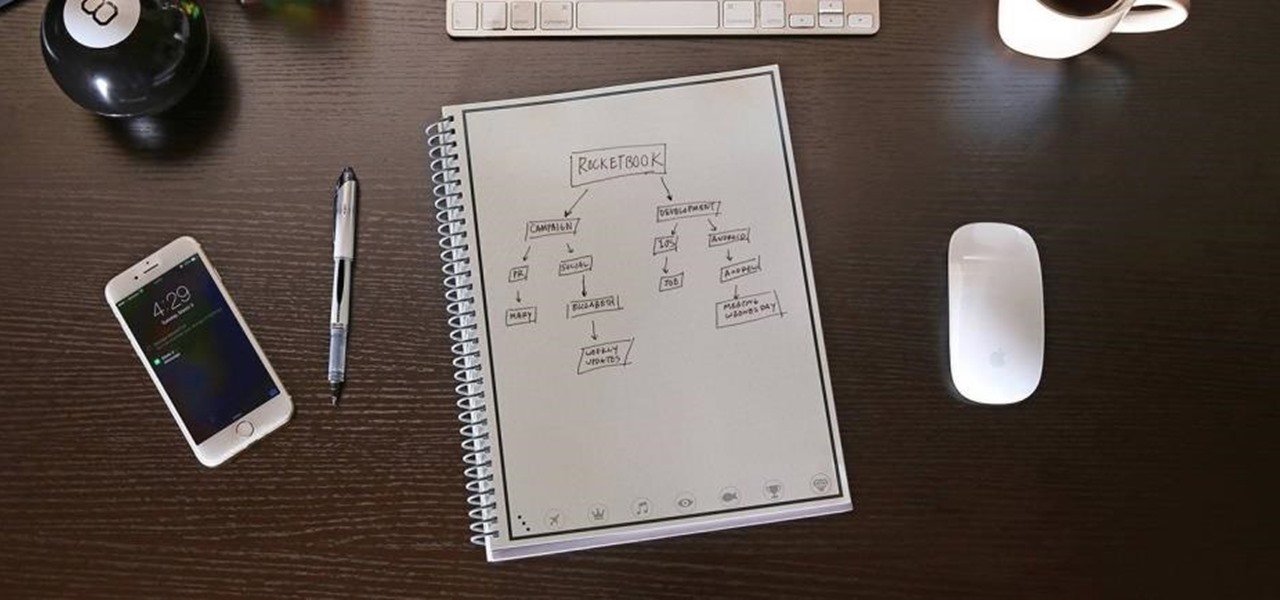
Pretty much every note you save on your computer, phone, or tablet can be uploaded to your cloud and viewed on any of your devices. But what about those notes you write down on actual paper? Well, those notes can also be cloud-friendly, thanks to the Rocketbook Wave.

Apple unveiled a 9.7-inch iPad Pro at their keynote event today, filling their roster to four different iPads. The smaller iPad Pro has the same screen size as the iPad Air 2, but comes with significant improvements under the hood. Keynote speaker Phillip Schiller rolled into the details: it's 40% less reflective than the Air with only 1.8% screen reflectivity, 25% brighter, produces 500 nits of light (making it "the brightest tablet available"), and has 25% greater color saturation. It also ...

The Stagefright exploit, which allowed for malicious code to be embedded in files on your device, is now very real in the form of Metaphor. Developed by software research company NorthBit, Metaphor is their implementation of exploits to the Stagefright library, and when executed, can access and control data on your device.

We've all been there—you're away from home, your phone's battery is quickly nearing zero, and you forgot to bring your charger. "Hey, does anybody have an iPhone charger?" you ask. Crickets. If you could understand cricket-speak, you'd know that they too were saying "Sorry, bud. We're all on Android."

A little-known company in India is making waves after announcing that it will sell an Android 5.1 Lollipop smartphone for less than $4 (or, more precisely, 251 rupees). The Freedom 251, from Ringing Bells, sounds almost too good to be true. Is that because it is?

There have been plenty of rumors and lots of speculation about the Galaxy S7 and S7 Edge, and now we're finally getting our first look at Samsung's newest flagships—in the form of two images.
I've been doing tutorials on Rasberry Pi and I would like to thank everyone that have both read the tutorials and gave me feedback on how well I'm doing. But now I've decided to take a small break and start a mini series that I'm hoping to be at least five tutorials. This doesn't mean I'm gonna stop posting Raspberry Pi tutorials, but since I'm learning so much at the same time I've decided to share some of that knowledge. Hence this tutorial. Please sit back, relax and read on.
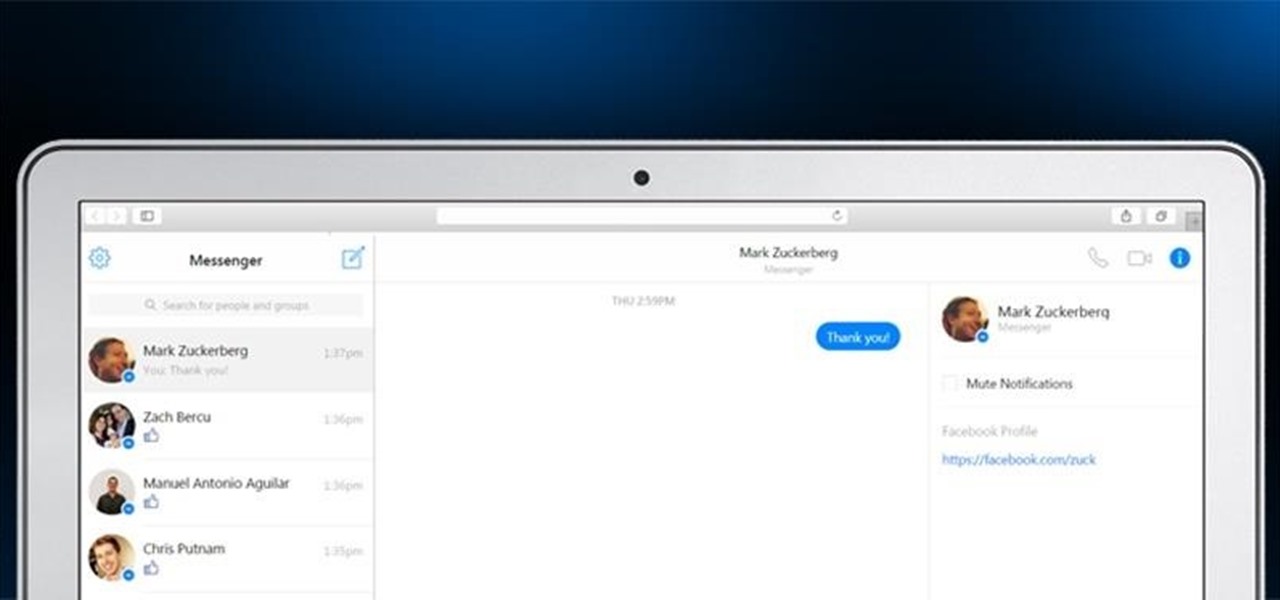
Facebook's Messenger apps for Android and iOS make it easy to navigate between conversations, helps you keep in touch with your friends or heckle your enemies, and even lets you tag yourself or others in the conversation with hilarious nicknames to keep things interesting.

Getting cool new features before everyone else is just plain fun. To be on the bleeding edge can require a lot of effort at times, since the fastest way to get an update is to find it as soon as it leaks, then get to work on sideloading the new version. Luckily, there's an easier way to get the latest features on your favorite apps, with WhatsApp being no exception.

One of the hottest trends in the food world right now is "spiralized" vegetables. I will confess that I am a bit suspicious of any diet or food fad that eliminates an entire food group for anything other than physician-ordered health reasons, but something really good has followed in the wake of the Atkins/paleo/gluten-free movements.

Before we dive into the world of frustration, I first would like to thank whoever of the admins and mods made the folder for Raspberry Pi in the How-To's, thank you. Now with that outta the way, this article is about Metasploit on Raspberry Pi (hence the title). I should say that I ran into a error, but I think I figured what the problem is. First of all this is not on Kali Linux, but on a regular Linux OS. With that said let's open up a terminal and begin.
Ready or not, the USB-C cable is about to take over your electronics. The new industry standard is fully reversible and packed with enough power to serve as a laptop charger or an HDMI cable, so it actually has the potential to replace every cord, wire, and connector in your house. In fact, the conversion has already started: The latest MacBook, Chromebook Pixel, and Nexus phones are sporting USB-C connectors out of the box.
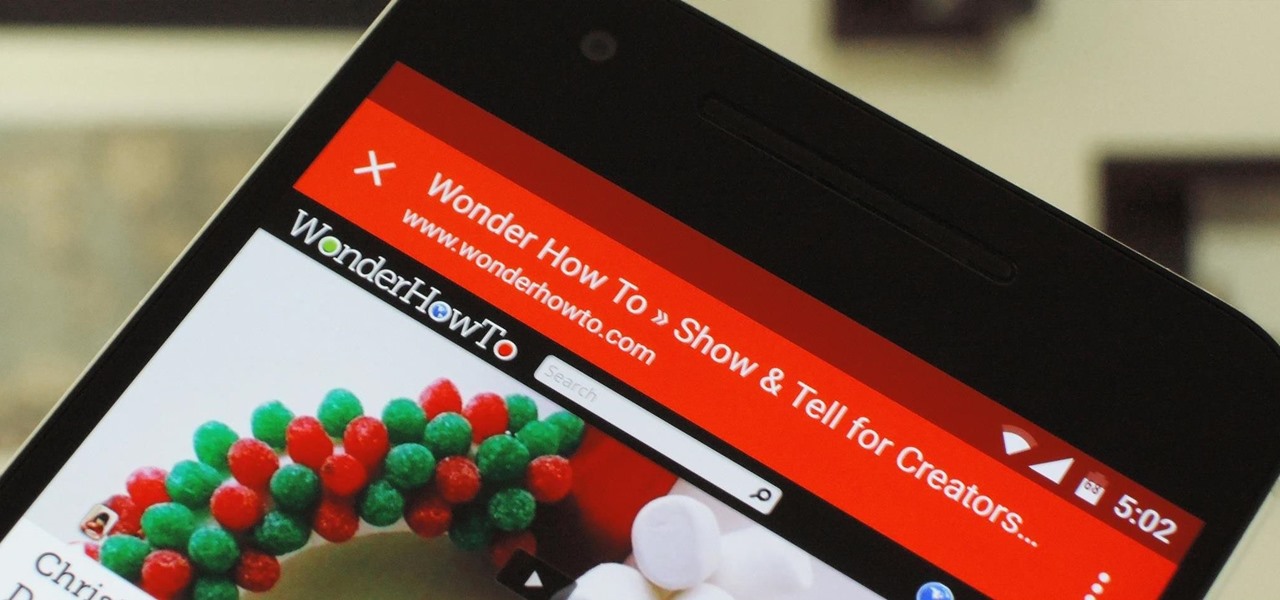
Android has a built-in browser called WebView that any app can use, which makes it easy for developers to display webpages without actually having to build an internet browser into their apps. But WebView is a stripped-down, bare bones browser with no ties to Android's default browser, Chrome, so none of your synced data like bookmarks, passwords, and history is available when an app is using WebView to display a page.
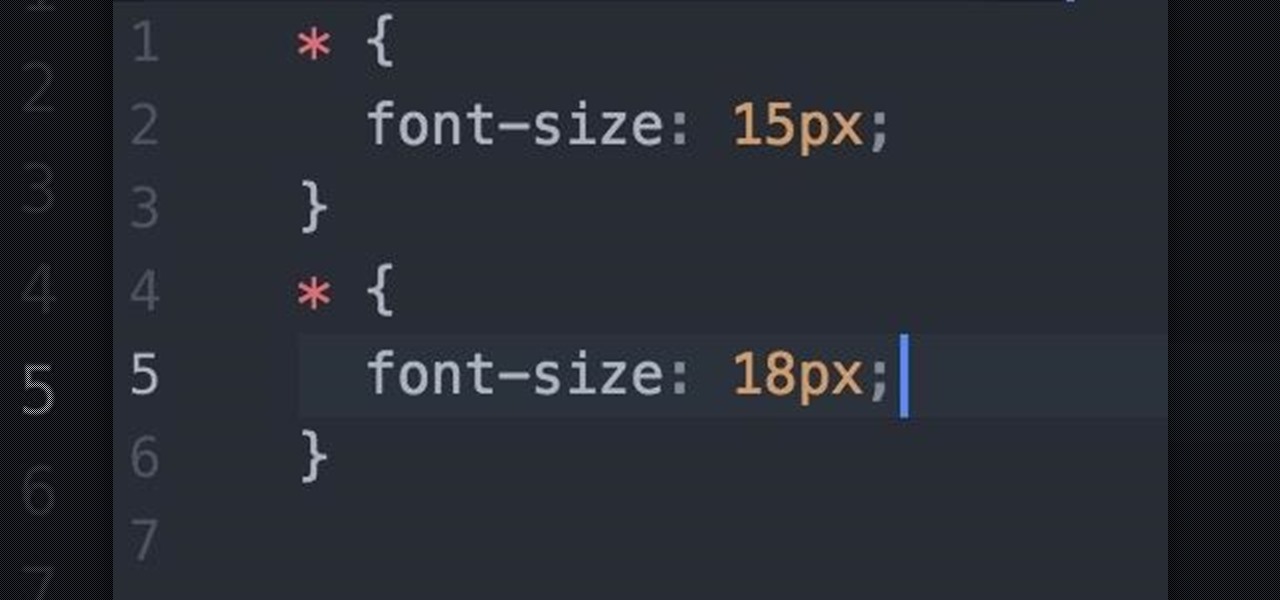
Welcome fellow Null-Byters! I would suggest you watch reading my last tutorial before we begin. In our last adventure, we began making a simple, ugly website. If we want it to make it look good, we should add some styling. But first, we need to understand the basics.
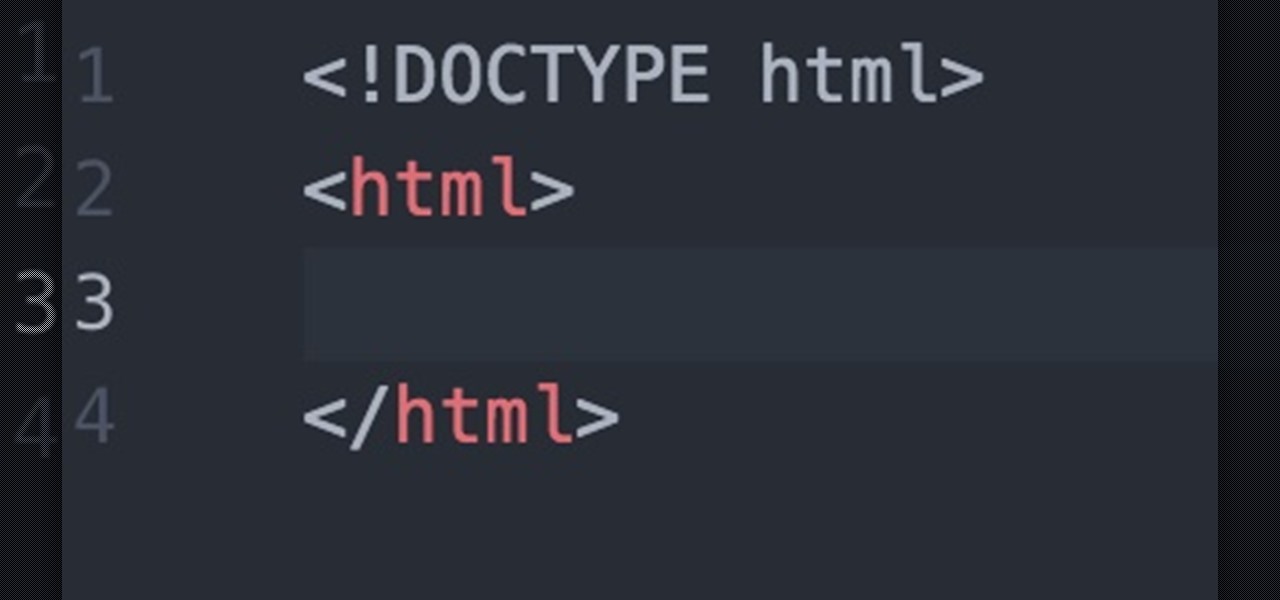
Hello fellow Null-Byters! In this "tutorial" we will be going basics of HTML. In the next tutorial, we will be going over CSS and then apply JavaScript.

Simmering or poaching food is a total pain sometimes. The problems are numerous: a layer exposed to air often dries out and creates a gross skin that can ruin the texture of the sauce, the poaching liquid evaporates too quickly and causes the poached protein to burn, and so on.
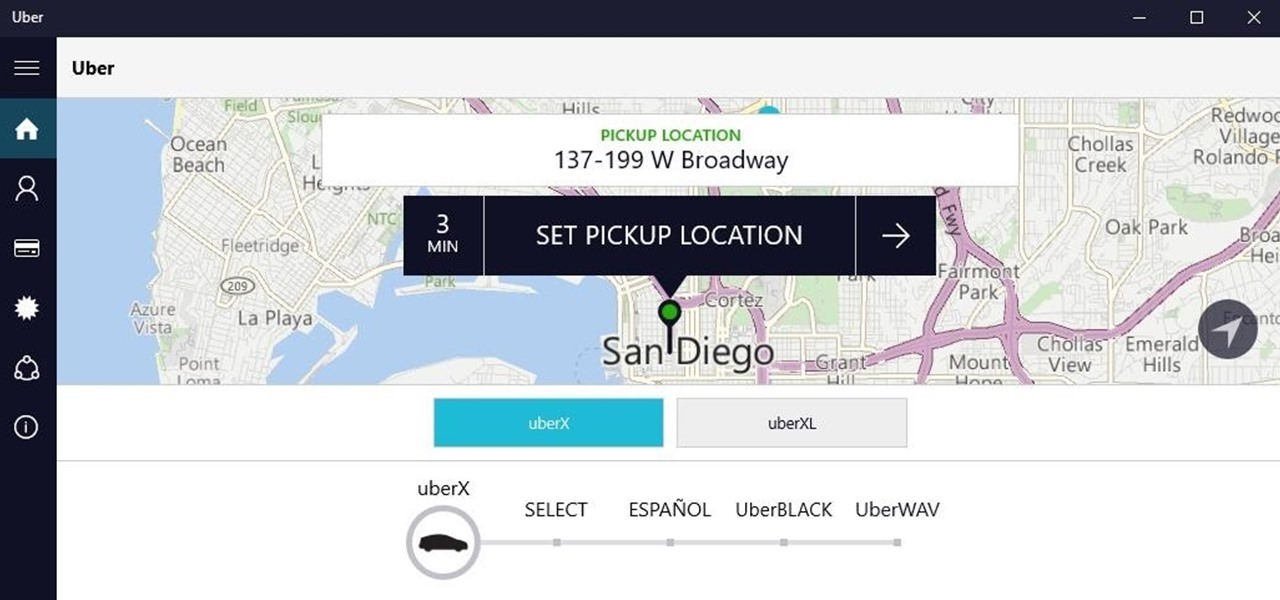
Windows 10 universal apps are actually pretty awesome—regardless of if you're using a desktop, laptop, tablet, or convertible, the same app automatically scales up or down to suit your device. Definitely cool, but the Windows Store is pretty bare-bones as it stands, so the downside is that you can't always find a good universal app for every purpose.
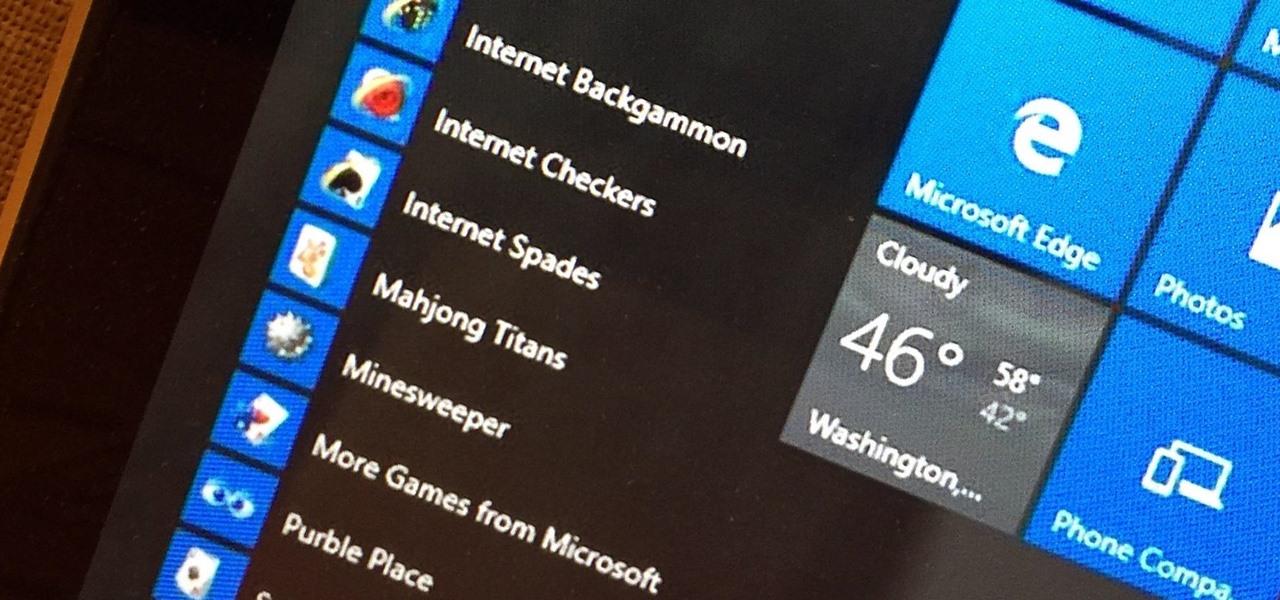
Microsoft's Windows 10 has proven to be a solid release by Microsoft, with faster adoption rates than its predecessor builds. The seamless integration of cloud services and tweaks both major and minor make using Windows easier than ever now. And it's almost enough to forget you ever used Windows Vista... almost.

Welcome back, my tenderfoot hackers! As most of you know, I am strong advocate for using Linux as a hacking platform. In fact, I would say that without knowing Linux, you will never become a professional hacker/pentester.
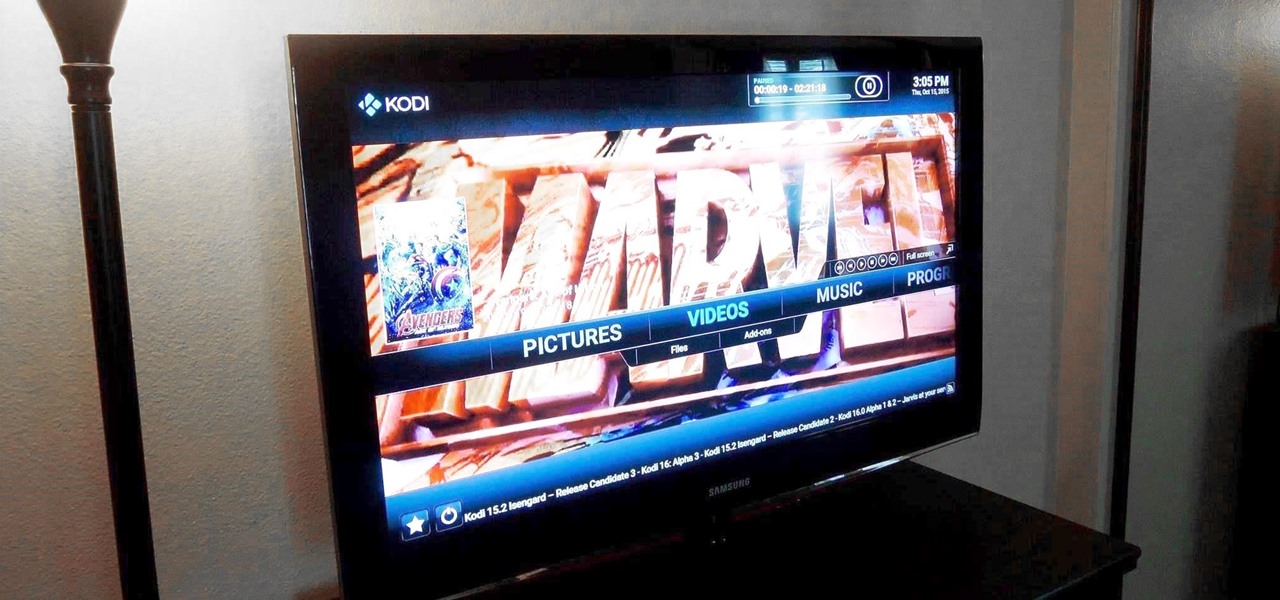
Amazon thinks that by simply removing an app from their Appstore, that they will stop users from accessing it. But with Android OS powering their Fire TV Stick and Fire TV, there really isn't anything they can do to prevent us from sideloading an APK onto the streaming media devices.

Everyone starts their mornings differently, but one common thread amongst the masses tends to be the consumption of coffee, albeit in many different forms—instant, pre-ground, K-Cups, Nespresso, and so on. And I'm sure that we all have our own preferred methods, as well.

Welcome back, my novice hackers! One of the most common questions that Null Byte readers ask is: "How can I evade detection by antivirus software on the target?" I have already talked about how AV software works, but to obtain a deeper understanding, what better way is there than opening up and dissecting some AV software?

Hello fellows nullbyters, first of i will start saying that im addicted to this community, i feel the challenge growing up so fast, all the newbies, amateurs,advanced and professionals hackers around trying their best to help the community, badly but we got some script-kids too but anyway, today we are going to learn how to install and use clanAV in kali linux.. INTRODUCTION

If you're a U.S. expat living, traveling, or studying abroad, or just someone who typically uses virtual private networks (VPNs) in order to access the North American video libraries of services like Hulu or Netflix, you were probably surprised to see that these video streaming services don't work on your Chromecast or Chromecast 2.

Android Beam is one of those features that makes you look at technology in awe, wondering how exactly something like that works.

!!!WARNING!!! !!!Because of misleading informations please wait for the new post about this same argument instead of reading this post!!!

Hello everyone Today I will show a different way to exploit a windows machine with a reverse https payload..."wait...why https? Isn't tcp good anymore?"
Hello! My name is An0nex. I am an ethical hacker who wants to share the art of hacking with all of you guys!