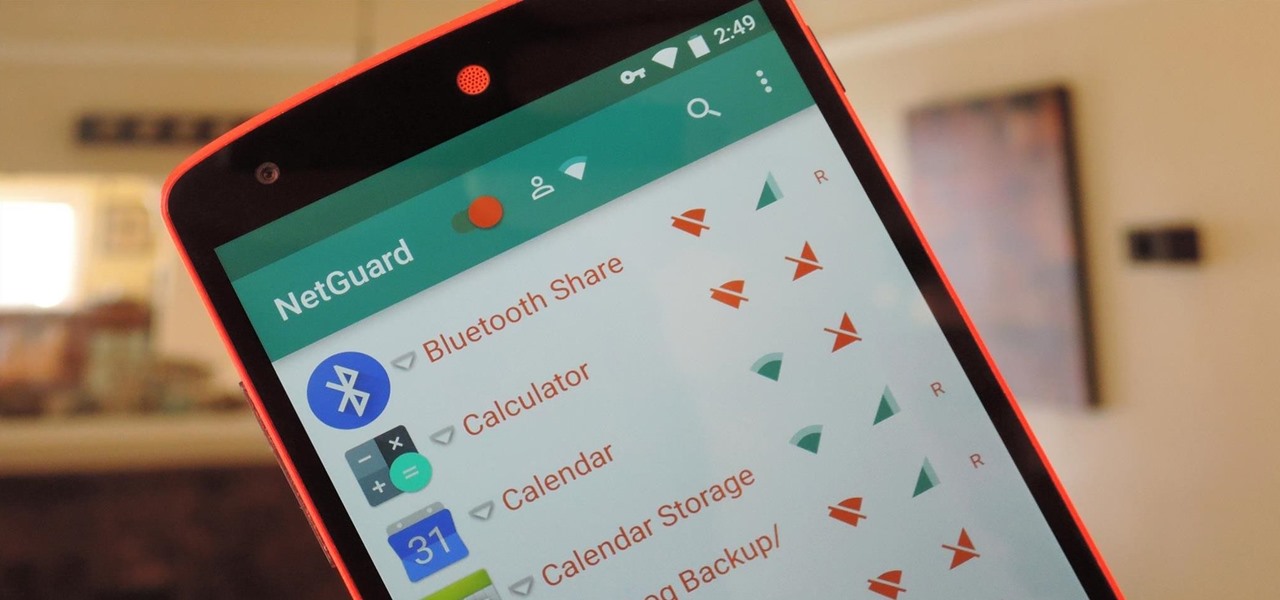
They are after you from all over the globe. Looking for ways to exploit you. Ways to hurt you. Not political terrorists, but rather "info terrorists." Each month thousands of websites get hacked into and have hidden links inserted into the pages by people wanting their spam sites to rank highly in the search engines.

XSS Shell is a cross-site scripting backdoor into the victim's browser which enables an attacker to issue commands and receive responses. During a normal XSS attack an attacker only has one chance to control a victim's browser; however, the XSS Shell keeps the connection between the attacker and the victim open to allow the attacker to continuously manipulate the victim's browser. XSS Shell works by setting up an XSS Channel, an AJAX application embedded into the victim's browser, that can ob...

If you have friends who aren't privacy-conscious, you've surely heard the old "What do I have to hide?" excuse. Despite the fact that billions of people are using the internet each day, many of them don't know the dangers that can find them. And many don't know the tools to combat them.
Many marketers are NOT using this powerful strategy to get free traffic and increase their brand exposure. It's as simple as signing up for a free Gravatar account and commenting on blogs in a similar niche. See some good examples and some bad examples...
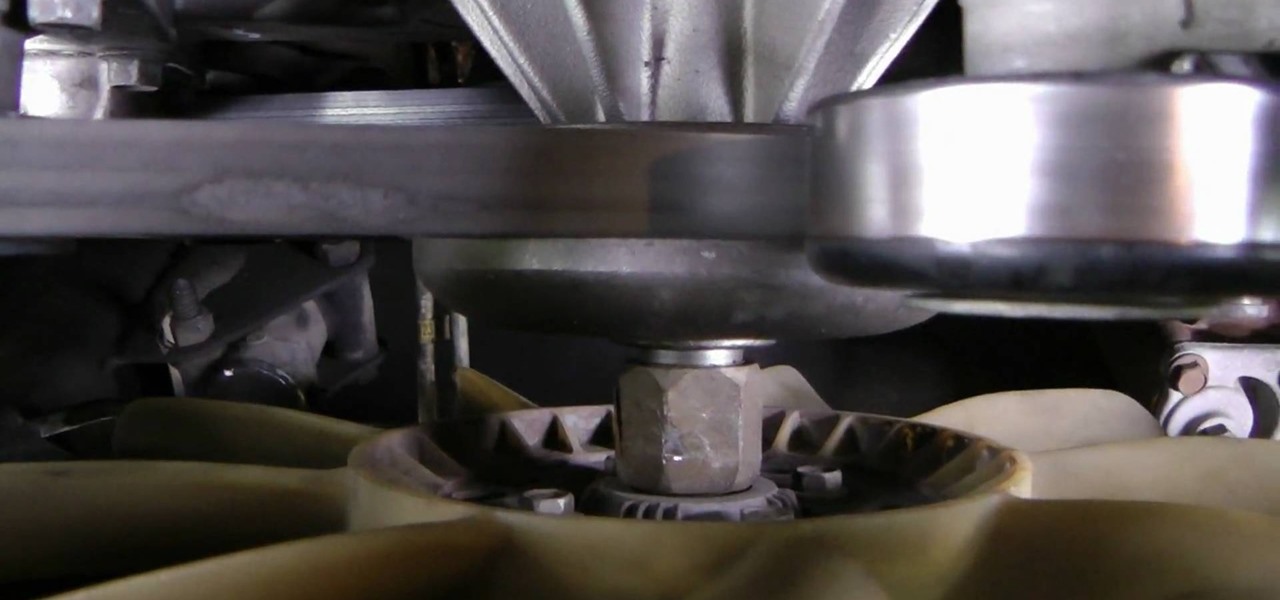
If your car overheats in traffic but not on the highway, you may have a broken radiator fan clutch. In this video you'll learn how to find and fix this problem on a truck, with special consideration for the massive size of such vehicles.

Welcome back, my hacker apprentices! In recent weeks, the revelation that the NSA has been spying on all of us has many people up in arms. I guess I take it all in stride as I just assume that the NSA is spying on all of us—all of the time. Don't get me wrong, I don't condone it, but I know the NSA.

This instructional video shows how change traffic lights from red to green, using science, and without actually having to know anything about magnetic fields or properties! Save gas, time, and frustration in your car and during your commute! Works great! See the test results! Yay for Kipkay! The trick in this video hacking tutorial will teach you how to get green lights on your bike or motorcycle that is too small or light to trigger the traffic light.

If you exceed your monthly mobile data limit, your cell phone bill can skyrocket pretty quickly. This is why a lot of people vigilantly monitor internet usage and even uninstall apps that use too much background data.

One of the best ways to increase traffic to your web site is to participate in social media. This video will show you how to optimize your social media posts so that they generate the most interest in your site and attract the most visitors.

SEO is the name of the game. If you want your business or brand to succeed, ranking on the front page of Google is a boon. Getting to the front page of search engines takes work, but it's not impossible when you master SEO best practices.

No website, service, or platform is immune to being abused or exploited by hackers, and Google Analytics is no exception. To better understand how Google Analytics can help deliver payloads and bypass security protocols, one might want to learn how to use Google Analytics from a user's perspective first.

Sniffing packets over a network is an easy way for hackers to gather information on a target without needing to do much work. But doing so can be risky if sniffing packets on an untrusted network because a payload within the packets being captured could be executed on your system. To prevent that, Sniffglue sandboxes packet sniffing to provide an extra layer of security.

It's common for IoT devices like Wi-Fi security cameras to host a website for controlling or configuring the camera that uses HTTP instead of the more secure HTTPS. This means anyone with the network password can see traffic to and from the camera, allowing a hacker to intercept security camera footage if anyone is watching the camera's HTTP viewing page.

Most users don't realize how much valuable data is in their network traffic. With a few simple tools, an attacker can quickly pick out cookies, passwords, and DNS queries from a macOS device as it covertly streams the victim's network traffic to the attacker's system. Here, we will cover two methods for analyzing packets flowing from a Mac.

Ever since the FBI took down the Silk Road and Dread Pirate Roberts last month, many questions have been raised about whether Tor still provides anonymity or not, and if it's now broken. I'll try to address that question here today succinctly from multiple angles, keeping it as simple and plain-language as possible. The Closing of Silk Road

Steam is an online platform that lets you download and play over 2,000 video games, from first-person shooters to RPGs, as well as a pretty long list of indie games. You can play on your PC, Mac, mobile device, or even your television, and it has a community of over 40 million gamers. Prices are different depending on the type of game and how new/popular it is, but they're generally about the same as what you'd pay for an Xbox or PlayStation version. They also have a decent list of free games...

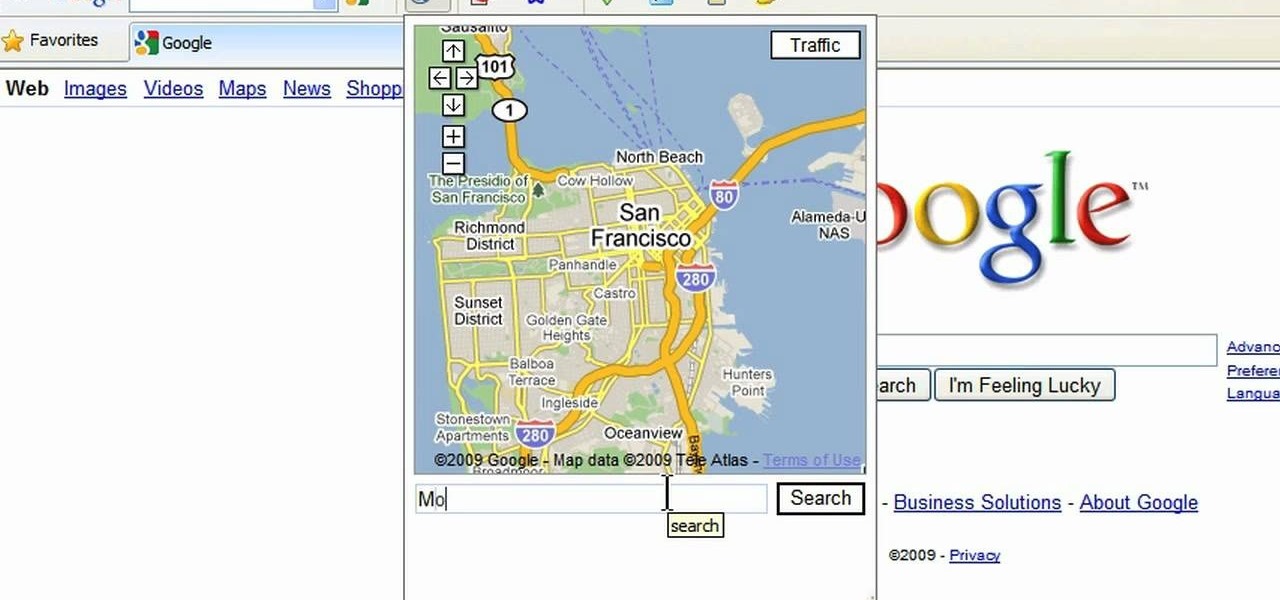
This is a video tutorial in the Computers & Programming category where you are going to learn how to avoid traffic jams using the Google Maps button on the Toolbar. Click on the Google Maps button on the toolbar. This will bring up the maps window. Here you type in the area in the search box, for example, "mountain view, ca" and click 'search'. On the next window click on the 'traffic' button and the map will then show you the roads that are clear of traffic jams in green color. There you go!

This video is a tutorial on how to ride a bike in traffic. The first rule is to obey the law. You would need to follow the laws of traffic as though you were driving a car. If there is a bike lane, use it. It is not a good idea to use the sidewalk as that is reserved for walkers and runners. Ride predictably by signaling your turns. The video tells the viewer which side of the road to ride on, and also provides tips. He also discusses how to ride with another cyclist. This is a very informati...

Hak5 isn't your ordinary tech show. It's hacking in the old-school sense, covering everything from network security, open source and forensics, to DIY modding and the homebrew scene. Damn the warranties, it's time to Trust your Technolust. In this episode, see how to set up SSH tunneling to securely transmit HTTP traffic.

It only takes a few commands to manipulate a MacBook's secure HTTPS traffic and pluck login passwords out of the encrypted data. Let's take Facebook and Gmail hacking to the next level by intercepting Safari and Google Chrome web traffic in real time.

With the rise of website encryption (TLS), sniffing passwords from network activity has become difficult. However, it's still possible to quietly exfiltrate a target's network traffic in real time to extract passwords and sensitive information. Pertaining to macOS, there are two methods for retrieving traffic from a backdoored Mac.

A shady practice in place by AT&T and Verizon Wireless—and possibly more wireless carriers—was recently uncovered. Outgoing data requests sent from devices on these service providers are being injected with a Unique Identifier Header (UIDH) that allows websites, the carriers, and potentially even government agencies to track your online activity.

Welcome back, my greenhorn hackers! Over the years, I have written many articles here on Null Byte chronicling the many the hacks of the NSA, including the recent hack of the Juniper Networks VPN. (By the way, my speculation in that article has proven to be correct. The NSA did embed a backdoor on those devices.)

Welcome back, my hacker novitiates! Many of you have probably heard of a man-in-the-middle attack and wondered how difficult an attack like that would be. For those of you who've never heard of one, it's simply where we, the hacker, place ourselves between the victim and the server and send and receive all the communication between the two.

Accidents are the worst. They're costly, time consuming and an all around pain in the butt. Rear-end collisions are among the most common types of accidents on the road. Take these simple precautions to avoid a rear-end collision.

While it may not sound scary right off the bat, Blue Coat Systems now has an intermediate certificate authority. If you don't know what a certificate authority (CA) is, or who Blue Coat is, who cares, right? But you should... whether you use Mac or Windows.

Welcome back, my tenderfoot hackers! Well, the first season of Mr. Robot just ended and Elliot and fsociety successfully took down Evil Corp! They have effectively destroyed over 70% of the world's consumer and student debt! Free at last! Free at last! Of course, global financial markets crashed as well, but that's another story.

Welcome back, my novice hackers! Previously in my "Spy on Anyone" series, we used our hacking skills to turn a target's computer system into a bug to record conversations and found and downloaded confidential documents on someone's computer. In this tutorial, I will show you how to spy on somebody's Internet traffic.

This video tutorial is about using Google Maps and the features in it. Google Maps help us to find the geography and even the traffic situations of a city. Google maps also provide a street view option that helps us to see how a place actually looks like from the ground. Neither of these views are real time. But now, Google Maps has added in a new option, which is the webcam. Just click on the more option in between traffic and map option. In the list that appears, just tick the webcam option...

Hak5 is at it again, with a plethora of somewhat accessible solutions to your technological problems. If you've ever needed to get through your school's firewall, or secure traffic tunneling, or try out applications in a fast, efficient manner? This video has it all and more.

In this video, we learn how to use the iPhone map app. First, go to Google Maps and click on the bottom to find your current location. This will show up in a blue button, which you can tap on to find out more information. The map will go in the direction your iPhone is facing and you can zoom in on information about places around you. You can also type in a place you are searching for, and get directions, then save them to your phone if you prefer. The key is the button on the bottom right wh...

Reconnaissance is the phase of an attack where a red team or hacker designs a strategy based on the information they can learn about the target, as well as what the available attack surface looks like. These scans can take time to discover relationships, but Raccoon OSINT scanner coordinates multiple automated scans to produce invasively detailed reports on a target with a single command.

I have came across a lot of members on the forum that didn't have a clear idea of what port forwarding is and what it does. So...Let's get started...

Welcome back, my hacker apprentices! I recently began a new series on digital forensics to show aspiring hackers what the forensic investigator can do and see while investigating a cyber attack. This is the second installment in that series and will focus upon network forensics. In other words, what can a network forensic investigator learn about the attacker during an investigation and how.

Want to make an Inverted Traffic Light cocktail like a champion bartender? This clip will show you how it's done. With the proper technique, mixing the perfect drink can be easy. So easy, in fact, that this free video bartenders' guide can present an overview of the process in about a minute's time. For more information, including a full list of ingredients and complete instructions on how to mix this drink yourself, take a look.

Collin teaches us how to race at Laguna Seca raceway in this tutorial. When coming out of the pit lane, wait for the workers to wave you on. Make sure there is not traffic around you because you will be doing over 100mph. Once you are sure there is no traffic, turn in the late turn so don't dual apex it as you are turning. By this time you will turn four and then turn five after this on the right hand side of the track. Next, turn six with a small amount of braking bringing the car out and ru...

In a previous guide, I demonstrated how to extract images from a security camera over Wi-Fi using Wireshark, provided you know the password. If you don't know the password, you can always get physical with the Hak5 Plunder Bug. Using this small LAN tap, we can intercept traffic like images from a Wi-Fi or IP security camera if we can get physical access to the Ethernet cable carrying the data.

We all know we shouldn't be using our smartphones while driving. But we also know many people do it anyway. Soon, however, the addicts among us may not have a choice but to kick their habit. A new app announced today by Samsung will block all calls and texts while you drive, stopping those who text and drive right in their tracks.

Hak5 isn't your ordinary tech show. It's hacking in the old-school sense, covering everything from network security, open source and forensics, to DIY modding and the homebrew scene. Damn the warranties, it's time to Trust your Technolust. In this episode, see how to hide secret data inside a photo.

While modern browsers are robust and provide a lot of functionality, they can be unlocked to do some pretty spectacular things with browser extensions. For hackers and OSINT researchers, these tools can be used to defeat online tracking, log in to SSH devices, and search the internet for clues during an investigation. These are a list of my top ten favorite browser extensions for hackers — and how to use them.