
How To: Can pears
A thorough, step-by-step guide to canning pears from a home economic expert. Episode includes printed recipe on website.


A thorough, step-by-step guide to canning pears from a home economic expert. Episode includes printed recipe on website.
How to get and use Lynx (a text-based web browser) to check your web site for SEO (search engine optimization).

DNS spoofing - how to use the hosts file in Windows XP to block unwanted spyware/popups/etc, block programs from reporting to a site, filter/block/redirect websites, and locally create forward lookups (IP to name resolution in network)

Learn how to improve your landscape business. Watch as the crew from Gopher Haul improves a lawn care business with new marketing material, truck and trailer signs and help create a website.
SEO specialist Aaron Wall demonstrates some on the page search engine optimization techniques that will help your site rank better in Google's search results. The key is to improve your site's SEO while keeping it user friendly.

Kipkay details how to surf the web secretly and leave no trace behind on your computer. Many websites collect personal data without you knowing it and you should surf anonymously.
You've probably seen that little bright orange "RSS" or XML square floating around on lots of websites and if you don't know what it is (or you do) and don't know how to use it, check out this video. Jimmy explains what RSS feeds are, how to subscribe to them and then how to read and use them.

Banners are beautiful advertising and decor pieces that you can use on your website, blog, or even on printed materials (because those still do exist). Check out this Photoshop tutorial to learn how to create a lovely golden banner that flows back on itself and has believable lighting. Ripples add to the realistic nature of this banner.
Learn how to capture a screen shot of your desktop, an active window, a website, or anything else use Microsoft Windows XP and without installing additional software.

Home accidents. It's up to you to protect your family… your children… from accidents in the home. And there's one place that seems to get the most attention when dealing with safety concerns… The kitchen is one of the busiest, most accident-prone rooms in the house. Design a kitchen that will keep your family and guests safe.

Cars are expensive to buy, replace or repair. Check out this video and learn how to avoid the most statistically dangerous parking areas. There is no guarantee that no one will touch your vehicle, but by take precautions you are much less likely to be targeted.

The life of a busy entrepreneur isn't easy. In addition to coming up with original business ideas and marketing strategies, you also need to be continually thinking about investors, overhead, the competition, and expanding your customer base — often with a limited budget.

Phishing is the easiest way to get your password stolen, as it only takes one mistake to log in to the wrong website. A convincing phishing site is key to a successful attempt, and tools to create them have become intuitive and more sophisticated. SocialFish allows a hacker to create a persuasive phishing page for nearly any website, offering a web interface with an Android app for remote control.

In 2019, the Raspberry Pi 4 was released with specs including either 1 GB, 2 GB, or 4 GB of memory, a Broadcom BCM2711B0 quad-core A72 SoC, a USB Type-C power supply, and dual Micro-HDMI outputs. Performance and hardware changes aside, the Pi 4 Model B runs Kali Linux just as well, if not better, than its predecessors. It also includes support for Wi-Fi hacking on its internal wireless card.
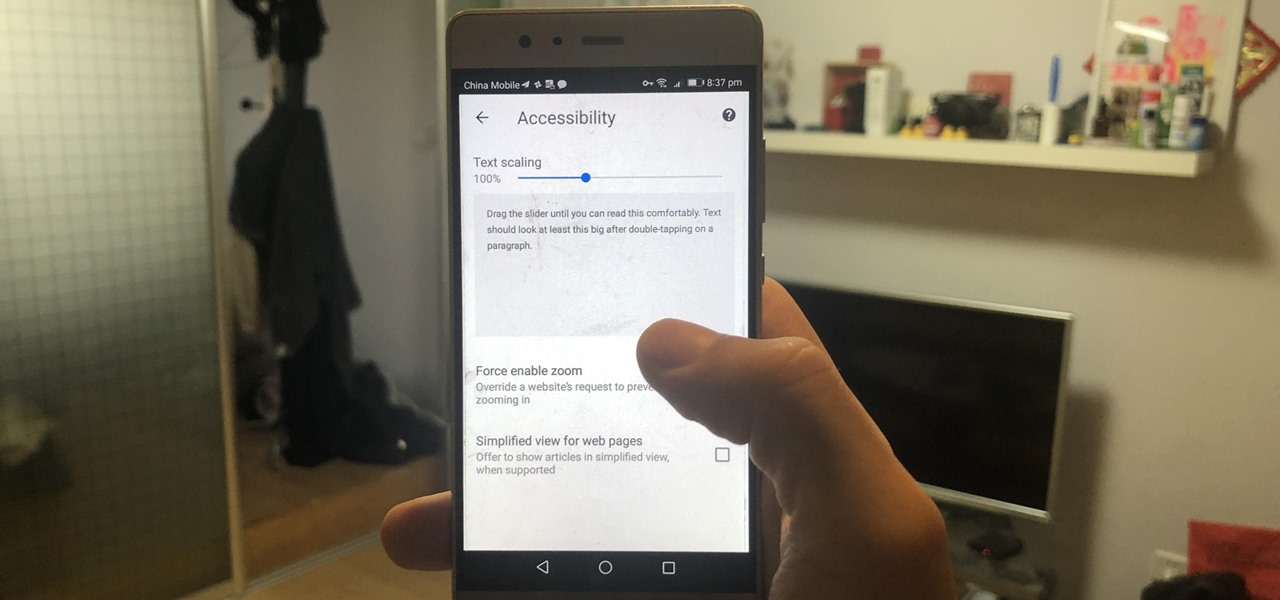
There are many reasons you might want to increase your text size in Google Chrome. The browser's accessibility options have a few tools to help the readability of text on websites. Changing the text scale, enabling zooming, and toggling the simplified view can customize Google Chrome to be perfect for you.

Microsoft.com is one of the most extensive domains on the internet with thousands of registered subdomains. Windows 10 will ping these subdomains hundreds of times an hour, making it challenging to firewall and monitor all of the requests made by the operating system. An attacker can use these subdomains to serve payloads to evade network firewalls.

The tactic of brute-forcing a login, i.e., trying many passwords very quickly until the correct one is discovered, can be easy for services like SSH or Telnet. For something like a website login page, we must identify different elements of the page first. Thanks to a Python tool for brute-forcing websites called Hatch, this process has been simplified to the point that even a beginner can try it.

Stumbling upon a specifically tailored advertisement on your iPhone can be a bit disconcerting. But that's what happens when you let advertisers track your data. Some of you may appreciate more relevant ads in apps, but the rest of you might consider it a straight-up privacy invasion.
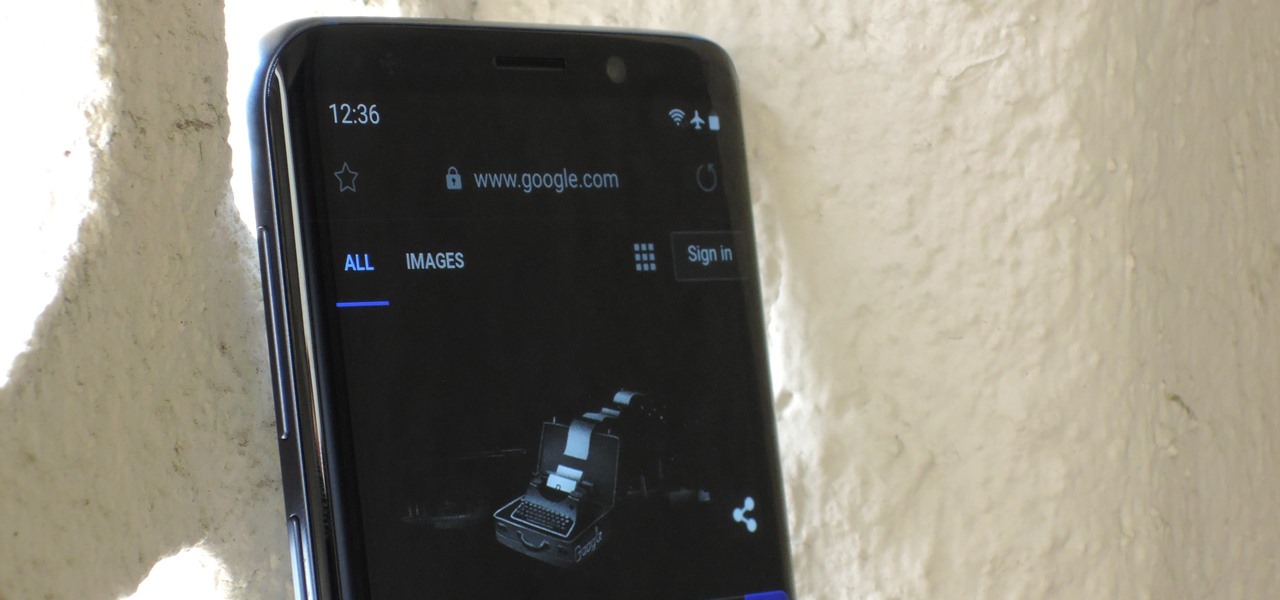
One of the headlining features in Samsung's One UI update is a new dark mode that turns stock apps and system menus black. But something you may have missed is what this theme does to the Samsung Internet app and all the websites you visit.

Web application vulnerabilities are one of the most crucial points of consideration in any penetration test or security evaluation. While some security areas require a home network or computer for testing, creating a test website to learn web app security requires a slightly different approach. For a safe environment to learn about web app hacking, the OWASP Juice Shop can help.

Leaked databases get passed around the internet and no one seems to notice. We've become desensitized to the data breaches that occur on a daily basis because it happens so frequently. Join me as I illustrate why reusing passwords across multiple websites is a truly awful practice — and compromise hundreds of social media accounts in the process.

Two-factor authentication (2FA) is a great way to add another layer of security to sensitive third-party apps and websites like Venmo. However, before iOS 12, to log into a particular 2FA-secured app or site on your iPhone, you'd have to memorize or copy the SMS code from Messages, then jump back in a timely manner to log in. Apple's latest iOS version streamlines this process.

While the security behind WEP networks was broken in 2005, modern tools have made cracking them incredibly simple. In densely populated areas, WEP networks can be found in surprising and important places to this day, and they can be cracked in a matter of minutes. We'll show you how a hacker would do so and explain why they should be careful to avoid hacking into a honeypot.

Your homepage should be the site you most likely need to check whenever you start a new session with Samsung Internet. However, times change — perhaps the site you're currently browsing is just what you need to see multiple times a day. In that case, you'll want to know a quick and easy way to set it as your default homepage.

Using just a small sticky note, we can trigger a chain of events that ultimately results in complete access to someone's entire digital and personal life.

Dating websites allow you to see a person in a very intimate context, framing their successes and accomplishments in life to an important audience. The information contained in these profiles often can't be found elsewhere, offering a unique look into the personal life of the user.

Last week, we told you about one of the first pairs of augmented reality smartglasses to get Amazon Alexa functionality, and now we're finally getting a look at how it works.

While Apple launched ARKit to enable developers to build augmented into mobile apps, Mozilla, the company behind the Firefox browser, is taking advantage of the platform to advocate for browser-based AR experiences.

JavaScript is one of the most common languages used on the web. It can automate and animate website components, manage website content, and carry out many other useful functions from within a webpage. The scripting language also has many functions which can be used for malicious purposes, including stealing a user's cookies containing passwords and other information.

Trendy restaurants are fun, but waiting in line isn't. Too often, we arrive at a location to find a queue between us and our dinner. If only we could know when wait times were down so we could go out at the optimal time.

The creative possibilities are part of what makes Apple's ARKit so exciting. We've seen new camera effects, painting, and new ways to tell stories through ARKit. Now, the app developer studio "Orb" has created an app to let you create scenes with 3D objects of your choosing.
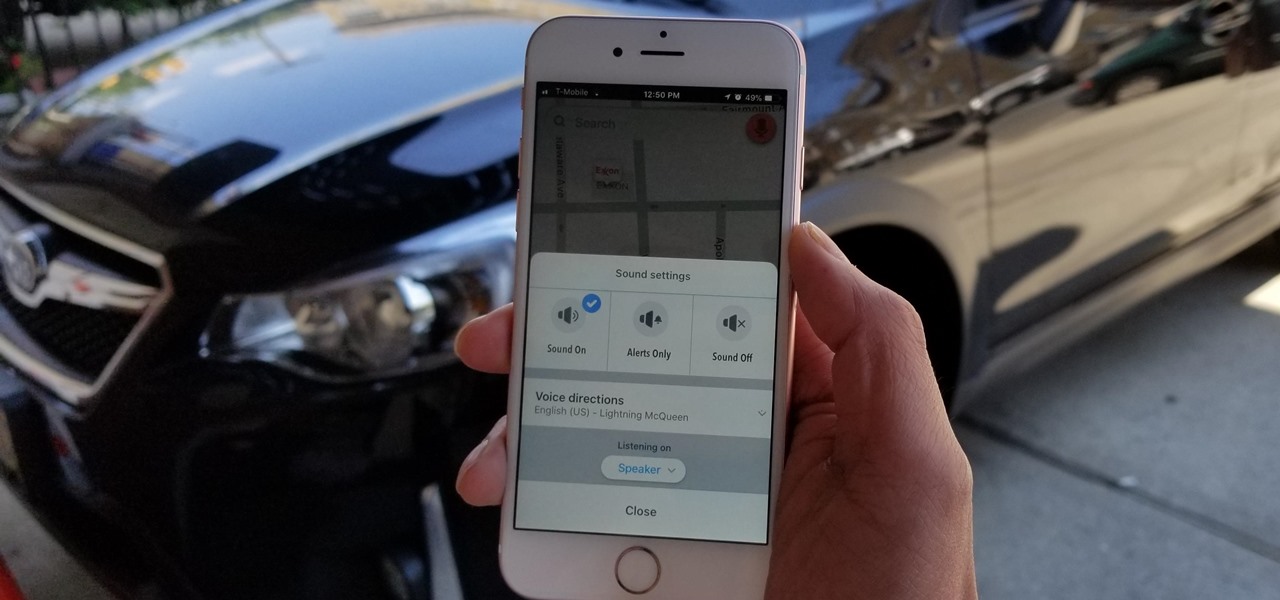
If you've been looking for an alternative to Google Maps, look no further than Waze. In addition to benefits like crowd-sourced traffic data, police trap locations, and road work avoidance, the app even lets you personalize the voices used for navigation and directions.
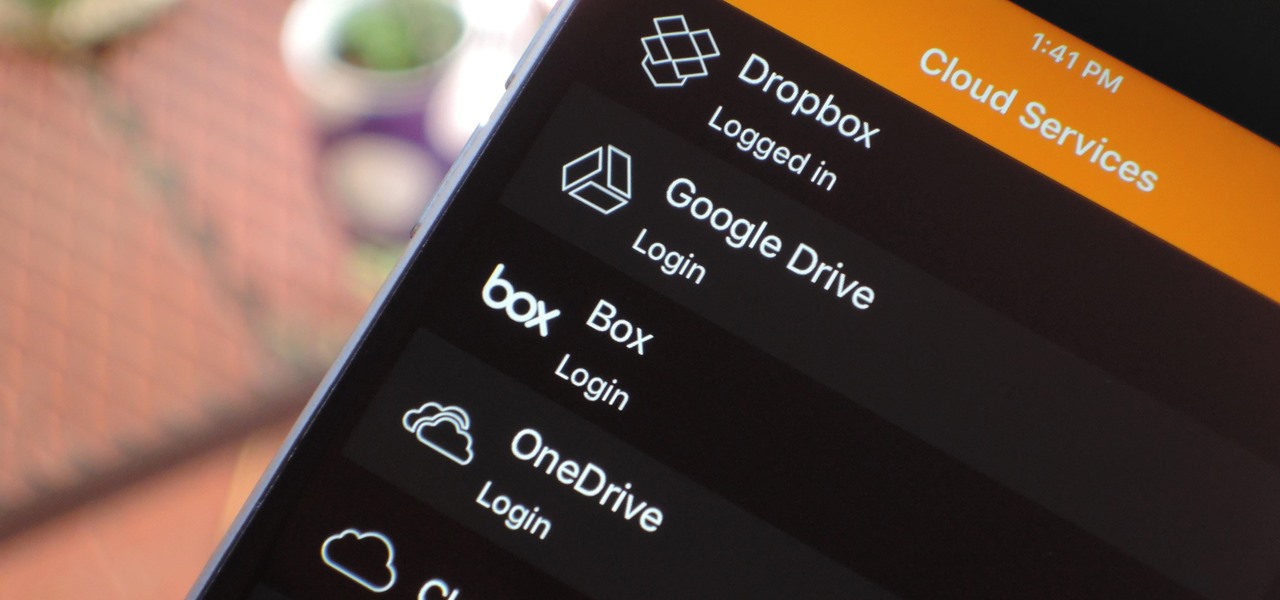
If you have movies and videos stored on Box, Google Drive, Dropbox, or OneDrive, you should definitely be using the VLC app for iPhone. After setting a few things up, VLC will let you stream videos directly from any of these services with a proper video player UI, complete with gesture controls.

Wegmans recently partnered with Instacart, an online grocery-delivery app, to bring your groceries right to you. The collaboration will begin in the suburbs around Washington, DC, and Wegmans plans to expand to other areas later on.
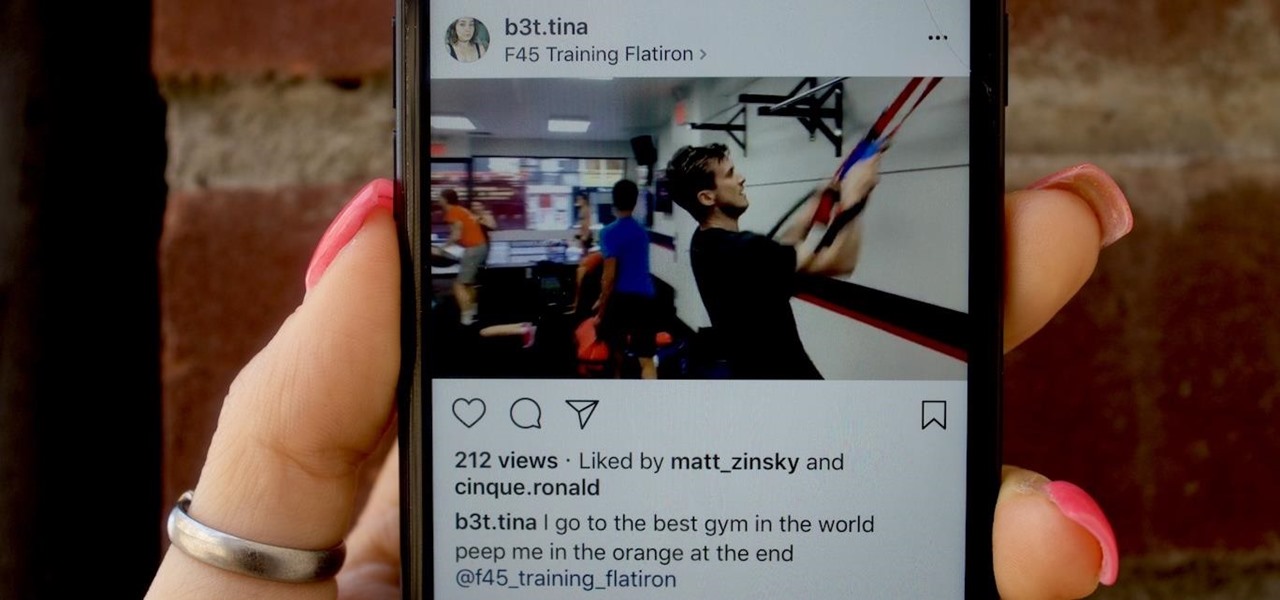
As you all journey along with me on my challenge to become some sort of Instagram expert, let me share with you one hack that is currently helping me out a lot. If you've ever wanted to put a line break in your posts, then keep on reading.

A fairly hidden feature in iOS 10 let you turn websites and documents into PDFs, but thanks to the new Markup function in iOS 11, this process has become a lot more streamlined.

Waymo has done a lot of things over the course of their driverless journey, but their solution to little birdies pooping all over a self-driving car's LiDAR system is definitely our favorite.

You would think most people would agree that you shouldn't use your smartphone while driving. Apparently, most people would be liars, according to recent data from the National Safety Council (NSC) and Zendrive.

While not quite a true self-driving car, Mercedes is gearing to release a vehicle with a plethora of assistive-driving features, some that might have you excited about what autonomous vehicles can do in the future.

At Adobe Summit 2017 this week, Adobe announced they are looking to occupy a new space in the market by combining their analytic capabilities with augmented reality. Teaming up with Microsoft, the company has combined Adobe Sensei software with the HoloLens, reports GeekWire. Together, the tech and software create a new tool for retailers to track their consumers' habits.