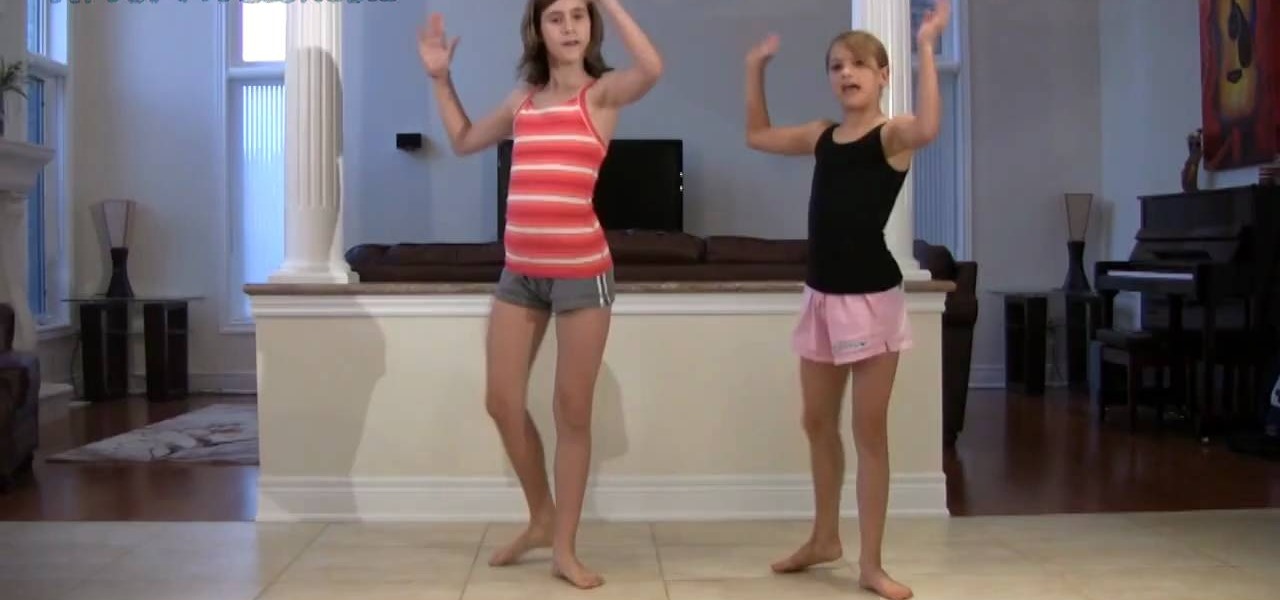In this video tutorial, viewers learn how to browse web pages without a mouse. Users will need to use the Mozilla Firefox browser. When you're in the Firefox browser, press F7 or click on Firefox, click on Preferences and select the Advanced tab (Mac OS X). Now check "Always use the cursor key to navigate within pages". This will activate character browsing, allowing the user to use the arrow keys to move up and down the page. Holding Shift will allow users to select a text. This video will b...
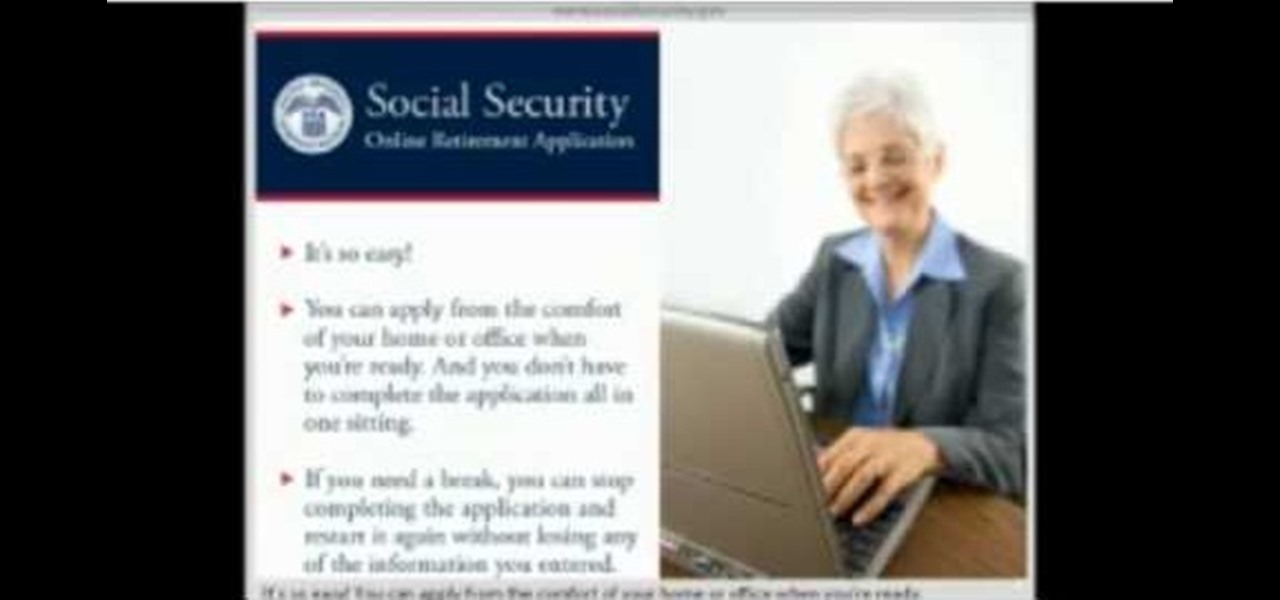
When you decide its time to retire, you will most likely need to cash in your Social Security benefits. In this official two part tutorial, presented by the American Social Secuity Administration, learn exactly how to use their website and apply online. Applying online is very easy, and takes a lot less time than applying in person. By applying online for social security, you will bypass all of the long lines and waiting that usually happens in one of the offices. Plus, you won't ever have to...

Want to disguise your URLs so that they appear suspicious? In the style of websites such as Tiny URL that take your original URL and give you a shortened one to post on your blog or twitter feed, Shady URL takes your original URL and gives you one that might convince people not to click it. Go to Shady URL and paste the URL you wish to disguise. Click submit, and on the next page it will give you a URL that looks, well, shady. It might include something about a mail order bride or an investme...
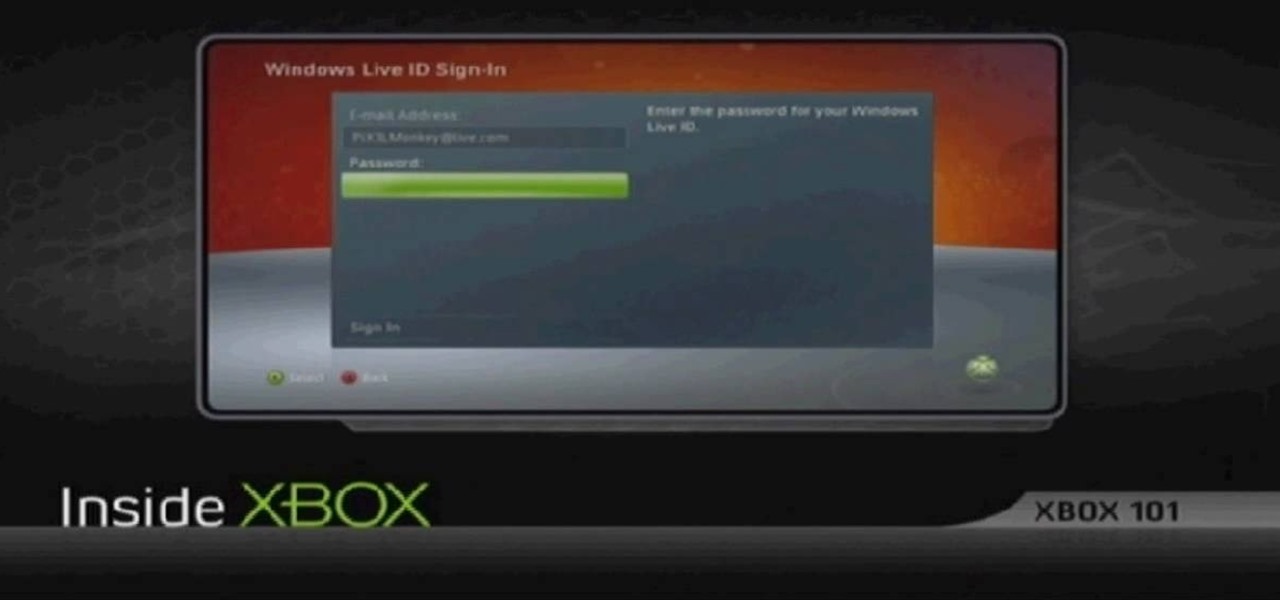
Learn how to update your contact information on your XBox 360 in simple steps. First to update your information through the XBox website go to My XBox and select 'Manage profile'. Now click 'Contact information' and update you information and details. To do it from your XBox 360 console go to My XBox and select 'Manage account'. Now click on 'Contact information' and then update your details. Do not give fake details because if you are selected for any offers you cannot be contacted.

Watch this tutorial to learn how to draw a hand giving a thumbs up. Make sure to pause the video after each step and look at the screen every few seconds while you are drawing.

Have you ever found yourself calling up a company, only to be denied due to not calling from the number listed on your account? Thanks to a website called Spoofcard, this is no longer an issue! SpoofCard let's you spoof the number you are calling from, as well as modify your voice (Male -> Female or vice versa). Best of all, it all looks completely legitimate.

Kids... it's dance time! Check out this dance video tutorial on how to do the Miley Cyrus Hoedown Throwdown dance. This dance is from the Hannah Montana movie from 2009 where Miley Cyrus performs the Hoedown Throwdown in Tennessee.

Check out this informative video tutorial from Apple on how to build songs in GarageBand '09.

Check out this informative video tutorial from Apple on how to mix songs in GarageBand '09.

Right out of the box, iPhone is incredibly easy to use. If you want to get the most out of every feature, you’ve come to the right place. This video tutorial straight from Apple will teach you how to make calls and use voicemail on the Apple iPhone 3G. The iPhone redefines what a mobile phone can do.

Household Hacker brings you fun hack how to projects in a variety of areas: electronic hacks, computer hacks, pranks, etc. Search Household Hacker on WonderHowTo for more videos by this creator. In this video, learn how to make YouTube paper.

In this video I show you how to get a Flash plugin to allow you to play videos in safari. Your iPhone/iPod Touch does not have to be jailbroken to do this. If you are having problems not getting the email make sure you look in your bulk or spam folder of your email. Just click the activation link in the email refresh the safari page and everything should work.

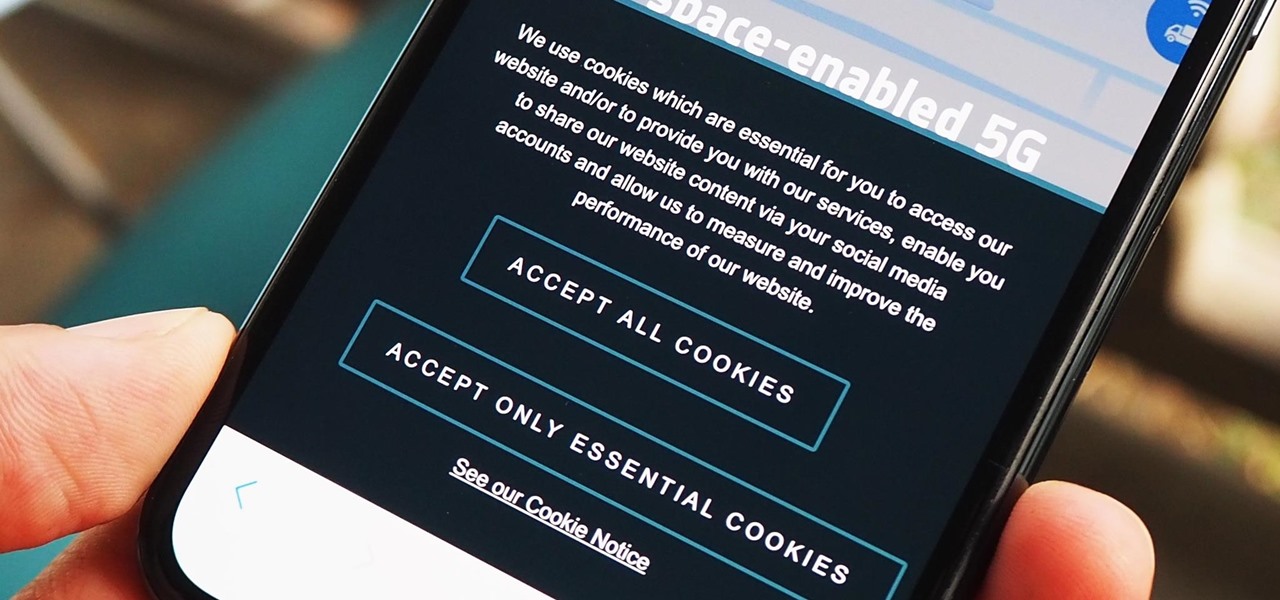
As a means to combat annoying and intrusive advertisements in Safari, Apple added native support for content blockers on the iPhone. Instead of being bombarded by notifications, banners, and pop-ups, content blockers prevent them from opening, which can also be said about those annoying cookie consent notices that many websites now have.

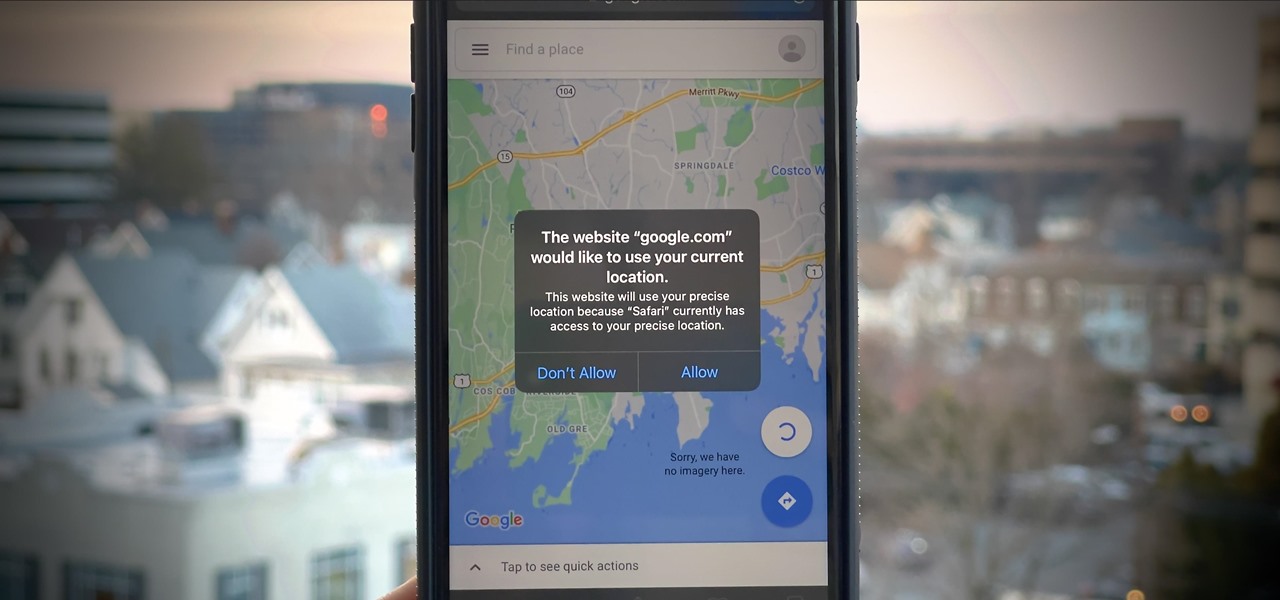
If you surf the web on your iPhone, you no doubt run into this problem all the time: a website wants your location. It can happen when performing a location-based task, such as using a store locator, or whenever a web app just wants to deliver better ads or local recommendations. If you're tired of allowing or denying permission each time, there's an easy way to stop the annoying security pop-ups.

The gold standard in any business is reaching the front page of Google. You need to get your brand in front of audiences. While it can seem daunting, it's not impossible when you master SEO best practices.

The Pi-hole project is a popular DNS-level ad blocker, but it can be much more than that. Its DNS-level filtering can also be used as a firewall of sorts to prevent malicious websites from resolving, as well as to keep privacy-killing trackers such as Google Analytics from ever loading in the browser. Let's take a look at setting a Pi-hole up and customizing a blacklist to suit your needs.

It's pretty much a given at this point that Facebook has a lot of data on us. While you might be conscious of the data you share with Facebook when you post, upload photos, or chat with friends on Messenger, you might not be thinking about all the data it receives from websites and apps you use outside the social media giant. Now, you can actually do something about it.

Apple has seemingly always made it a priority to show how much it cares about user security and privacy — enough that it has a page dedicated to it, proclaiming that "privacy is a fundamental human right." It's true that there are few issues more important than user privacy when it comes to technology, and Apple only makes things better in iOS 13.

Business hours and addresses change, but they're not always updated on Yelp by business owners for the rest of us to see. Showing up when a business is closed or going to the incorrect address is a major annoyance, which is why the company allows us, the customers, to help update business information through the Yelp mobile app on iOS and Android. If owners won't do it, somebody has to.

During the keynote at WWDC earlier this year, Apple introduced the latest iteration of its mobile operating system, iOS 12. Despite a thorough demo on stage, Apple glossed over new eye tracking features that use ARKit 2. Developers can now use the TrueDepth camera on the iPhone X, XS, XS Max, and XR to determine where your eyes are looking, opening up incredible new possibilities for new apps.

MacOS isn't known as an ideal operating system for hacking without customization, but it includes native tools that allow easy control of the Wi-Fi radio for packet sniffing. Changing channels, scanning for access points, and even capturing packets all can be done from the command line. We'll use aliasing to set some simple commands for easy native packet capture on a macOS system.

A router is the core of anyone's internet experience, but most people don't spend much time setting up this critical piece of hardware. Old firmware, default passwords, and other configuration issues continue to haunt many organizations. Exploiting the poor, neglected computer inside these routers has become so popular and easy that automated tools have been created to make the process a breeze.

The world of investment and finance can be labyrinthine in its very nature — and even more complicated in regards to augmented and mixed reality. While these new emergent technologies are teeming with explosive levels of unrealized potential, there's still a big layer of uncertainty in terms of return — but these investors aren't afraid to take the leap.

Welcome back, my greenhorn hackers! Throughout this series on Metasploit, and in most of my hacking tutorials here on Null Byte that use Metasploit (there are many; type "metasploit" into the search bar and you will find dozens), I have focused primarily on just two types of modules: exploits and payloads. Remember, Metasploit has six types of modules:

With the brand new SMS-based ordering service called Magic, anyone with a mobile phone can order whatever they want—really, anything—by sending causal text messages. Who says magic isn't real?

Keeping data private is vital in the days of smartphones and the free-floating information they carry. Justin wrote a guide on many of the deeply hidden and sometimes concerning privacy settings in iOS 7. Now we're back to cover some of the new (and old) privacy settings in iOS 8 that you need to address right now.

It used to be easy to hack tethering—root your device and install a third-party or modded tethering app. But snuck in amongst the changes in Android 4.3, a new data-monitoring service of sorts made its debut. There used to be a time when your data connection was yours. You paid for it, so you were free to use it for whatever you wanted. Unfortunately, those days are long gone.

Many of my aspiring hackers have written to me asking the same thing. "What skills do I need to be a good hacker?"

Welcome back, my novice hackers! Most of my tutorials up until this point have addressed how to exploit a target assuming that we already know some basic information about their system. These include their IP address, operating system, open ports, services running, and so on.

Make sure the bike is properly fit to the child. She should just be able to stand over the top bar of the frame without touching.

Watch this video tutorial to learn how to pick up a girl at a stoplight. Tired of the dating scene? Try meeting someone at a stoplight. If you don’t get arrested for stalking, you just might get a date.

Keep a high traffic floor evergreen using replaceable carpet tiles. All you need is a straight edge, measuring tape and a utility knife. Watch this how to video and grab your equipment to give your living room an entirely different feel.

Safety is of primary concern when driving a vehicle or riding a bicycle. Watch this video tutorial on how cyclists and motorists can safely share the road when the former wants to make a right turn and the latter is cycling straight.

Learn how to practice proper etiquette on a BlackBerry, smartphone or PDA. Make sure your love for your BlackBerry or other PDA device isn't making you obnoxious.

When it comes to household versatility, baking soda is king. Here are just some of the many cleaning uses for baking soda. Cleaning tips:

QR codes allow you to quickly and easily store and retrieve data within a single image. Much like barcodes at grocery stores, QR codes are images that can be scanned to discover data, such as an online website URL. Additionally, they can also be created by inputting text data into a QR code generator. Try scanning some of the QR codes in this video with an app on your phone or tablet to see how they work!

Blitzcrank is a steam golem champion with electrical abilities in League of Legends. His most unique ability is Rocket Grab, an ability that allows him to reach out and grab his enemies to bring them in close to a tower or for a kill. Learn how to abuse Blitzcrank's rocket grab and his other abilities to gank lanes and win games with this champion spotlight from Riot Games.

Found a video on YouTube that's perfect for your Keynote presentation? It's easy to embed YouTube clips on websites, but how can you successfully insert them into something like a Keynote project? It's actually quite easy! This video, just over a minute long, shows you the basic process behind downloading and re uploading your chosen video. Make sure that you append the .flv file extension to your downloaded fire, and also take care that you have the right to use what you're incorporating.

Gwyneth Paltrow is well known as an Oscar-winning actress and mother of two kids, Apple and Moses. But the film industry isn't the only one in which she excels. Paltrow started a healthy living and eating website called Goop a few years back, and she's a very talented chef.

If you're anything like the rest of the world, then you're glued to the computer. It's almost impossible to get away from using the computer at work, and once you get home how do you unwind? By checking your favorite blogs and websites on the computer.