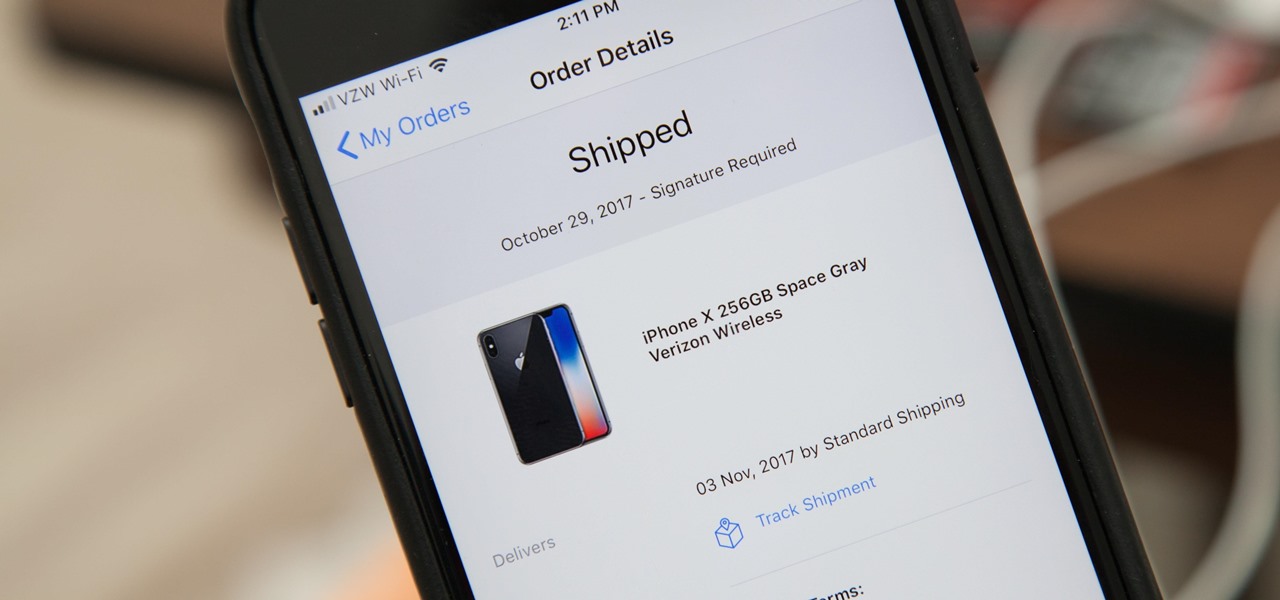
News: Your iPhone X May Have Shipped (Even if You're Not Expecting It To)
Current shipping estimates for the iPhone X are 5–6 weeks, but is there a chance you'll get yours tomorrow?


Current shipping estimates for the iPhone X are 5–6 weeks, but is there a chance you'll get yours tomorrow?
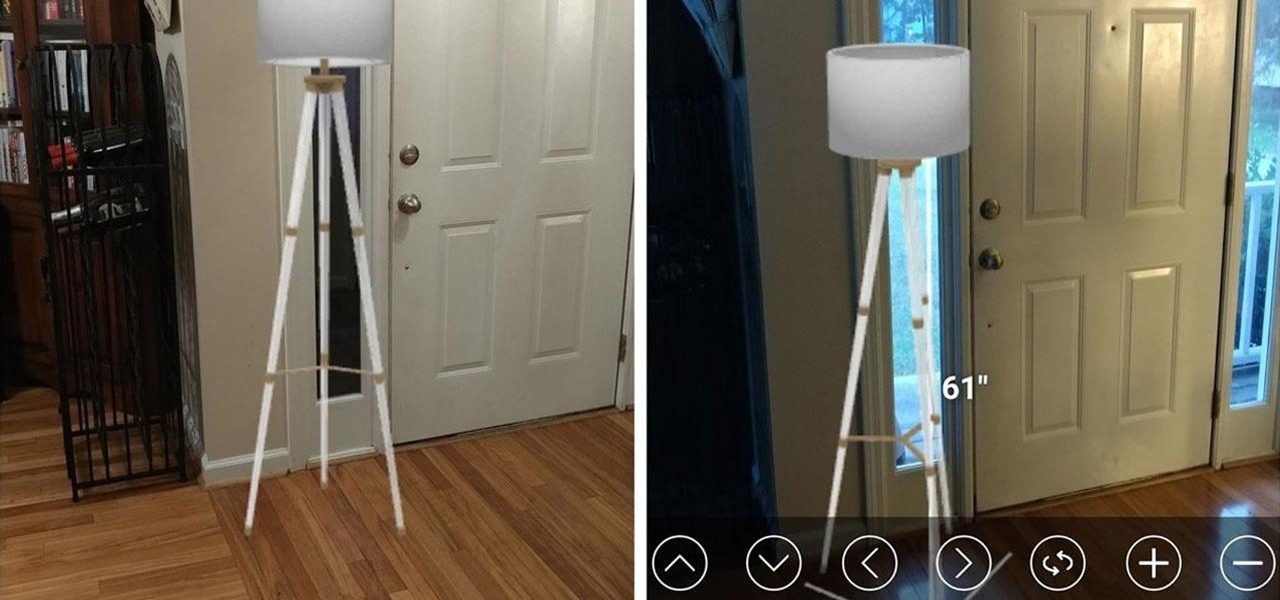
While some companies like IKEA and Lowe's zig towards ARKit to entice shoppers, Target has opted to zag to broader appeal with an augmented reality see-before-you-buy tool for its mobile website.

Imagine for a moment that a VPN is like putting on a disguise for your computer. This disguise works to change your IP address, secure your traffic with encryption, and mask your location to bypass regional restrictions. This makes it a helpful tool for both whistleblowers and journalists. VPNs are also built into the well-known Tor Browser.

Spotty cellular reception is a fact of life that we all have to deal with, especially when you're traveling. For those of us who rely on our smartphones for navigation, driving through areas with bad mobile data service can be a cause for major headaches.

Buyers can't wait for their Tesla Model 3 to be delivered. But with no clear arrival date in sight, buyers are starting to get a little antsy waiting to see what the Tesla Model 3 will look like up close. Luckily, Tesla accessories seller EVANNEX partnered with technology firm Kinetic Vision to try and satisfy buyers for a while by creating an app that lets you view an augmented reality Tesla Model 3 that's nearly life sized.

After laying off 40% of its staff this month to cut costs, SoundCloud appears to be struggling to stay afloat. While blog posts from the company have assured fans that the music platform is not in danger of shutting down, some people aren't so sure this is the truth. Internet Archive — a non-profit dedicated to preserving websites and services — announced today that they will be conducting a partial backup of SoundCloud to safeguard the site's content in case of closure.

Two salsa dancers who also happen to be programmers are soon releasing an app called Dance Reality, made with Apple's ARKit. Through this app, you will be able to practice your dancing with augmented reality as your teacher right from your iPhone.

Making a custom location on Instagram is one of the best ways to generate traffic to your account. It gives you that extra uniqueness when it comes to standing out amongst other companies. It also allows people to check in at the same location, further promoting your account across other platforms.

The producers of FX's animated series Archer have devised a plan to introduce augmented reality hijinks into its eighth and penultimate season with a new app for iOS and Android devices.

Last week it was announced that Waymo, the former Google Self-Driving Car project, had graduated from Alphabet's X innovation center. This graduation had been in the cards for many months with senior members of the project team and X hinting that it would be soon.
If you're tired of Google tracking you, but love how Chrome works, CyanogenMod has you covered. Their browser is called Gello, which is based off Chromium, Chrome's open-source counterpart. It's basically a souped-up version of Chrome—without all of the intrusive Google stuff. So if you're uncomfortable with Google displaying personalized ads based on your browsing history, or using your location to bring the "Physical Web" to your phone, you won't have to worry about any of that with Gello.

One of Android's biggest strengths is its ability to interact with other operating systems. When you plug your phone into your Windows PC, you instantly see all of the files it holds—and all it takes is a simple syncing app to do the same with Mac. To top that off, apps like Pushbullet and Join bridge the gap even further by allowing you to share links, files, and messages between all of your devices.

Welcome back, my novice hackers! As many of you know, recon is crucial to a successful hack/pentest. In most cases, hackers spend more time doing good reconnaissance than actually hacking. Without proper recon, you are simply guessing at what type of approach or exploit is going to work and, as a result, your time is wasted without any useful outcomes.

Welcome back, my tenderfoot hackers! Web apps are often the best vector to an organization's server/database, an entry point to their entire internal network. By definition, the web app is designed to take an input from the user and send that input back to the server or database. In this way, the attacker can send their malicious input back to the servers and network if the web app is not properly secured.

Although they're often times the primary source of income for websites, on-site advertisements can annoy even the most tolerable reader. That's why ad blockers have been some of the most popular downloads on Firefox and Chrome for some time now, demonstrating that when it comes down to it, most people just want nothing to do with ads shoved in their face.

Last month, it was revealed that Juniper Networks' routers/firewalls were hacked. It was reported that a backdoor was implanted in the operating system of their routers/firewalls and that attackers could listen in on all encrypted communication. There are now fears that all confidential communications by U.S. government agencies and officials could have been compromised over the last three years.

Star Wars season is definitely upon us. No matter where you turn, you can't go a day without being bombarded by merchandising and co-branding advertisements that attempt to draw a parallel between some character from a galaxy far, far away and a galactic cruiser like the Dodge Viper, or a midichlorian-laden power source like Duracell. Yep, it's kind of annoying, but at least we can get some fun out of it here and there.

Many websites are crowded with ads, pictures, and other irrelevant content that make it harder than necessary to read a simple article on your iPhone. In many cases, you have to zoom in just to get a better view of the text you're attempting to read—unless the webpage blocks zooming.
Are you tired of uploading videos to different sites separately? It's really time consuming and difficult. Finally, there is a way to upload and distribute your videos to YouTube, Facebook, Dailymotion, and many more video-hosting websites in one go. No need to upload to every site separately and one by one.

Do you remember the last time we used BeEF? Well, now we get to use it again, but this time with MITMf! We are going to auto-inject the hooking script into every webpage the victim visits!

In an attempt to remain a mobile-exclusive app, Instagram doesn't let users upload photos or videos from their computer. On the Instagram web app, you can pretty much only like and comment on items in your feed, but what about all of those photos on your computer that scream #tbt?

In a study attempting to observe virality in real time, two Microsoft engineers, Corom Thompson and Santosh Balasubramanian, used Microsoft's recently released Face detection API to create How-Old.net and track its usage in real time.
Since the Nexus Player is an Android device at heart, there are already several internet browsers that can be used on the streaming set-top box. Chrome, Firefox, and a few others will run perfectly fine, but the trouble with these is that you need a mouse to use them.

Welcome back, my budding hackers! With this article, I am initiating a new series that so many of you have been asking for: Hacking Web Applications.

Welcome back, my novice hackers! As we saw in my first tutorial on Facebook hacking, it is not a simple task. However, with the right skills and tools, as well as persistence and ingenuity, nothing is beyond our capabilities.

Hello Hackers! Welcome to my 2nd Post: This is a tutorial explaining how to hack android phones with Kali.

Welcome back, my budding hackers! This is the initial post of a new series on how to hack Facebook. It's important to note here that each hack I'll be covering is very specific. I have said it before, but I feel I need to repeat it again: there is NO SILVER BULLET that works under all circumstances. Obviously, the good folks at Facebook have taken precautions to make certain that their app is not hacked, but if we are creative, persistent, and ingenious, we can still get in.
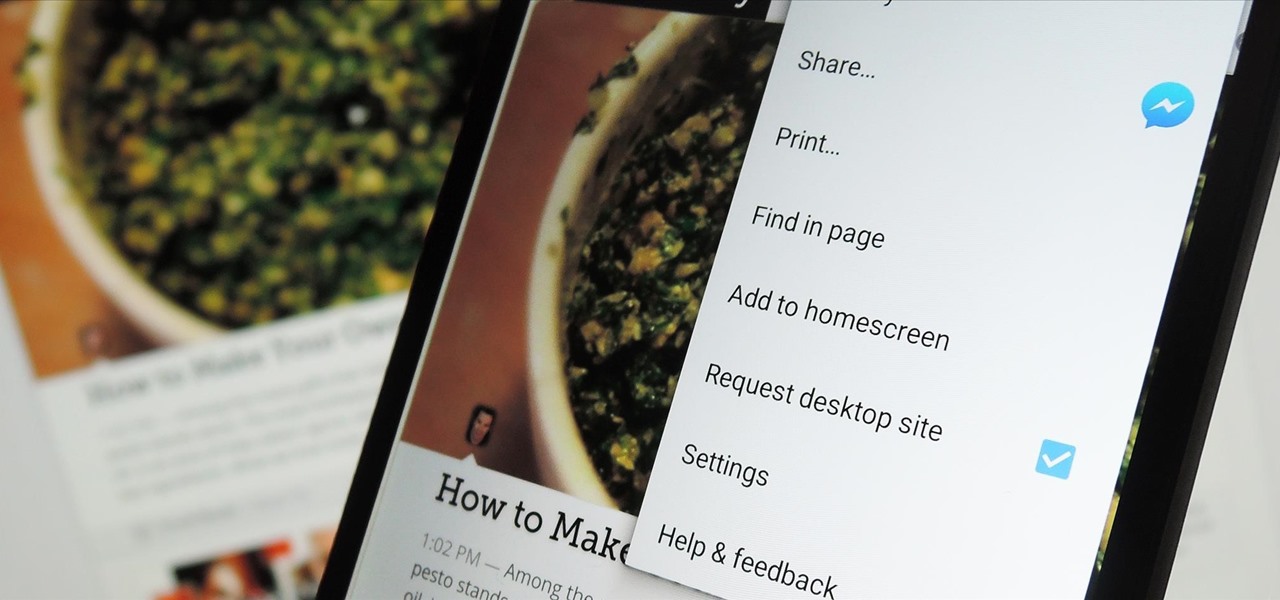
The majority of Android web browsers carry a "desktop mode" feature that makes mobile websites look like normal computer versions. Mobile versions are designed to work faster and more efficiently on smartphones, but sometimes the desktop version looks better on large displays or has additional features not included in the mobile one.

Welcome back, my nascent hackers! In previous tutorials for my Wi-Fi Hacking series, I have shown you how to crack WEP and WPA2 passwords, break a WPS PIN, and create Evil Twin and Rogue access points. In this continuation of the series, let's look at slightly different approach to attacking wireless.

Video: . This Video will Show you how to Stretch your Natural hair with no Heat. I love doing this Method it is just as good as blowing your hair out. It gives your hair length without putting heat to it.
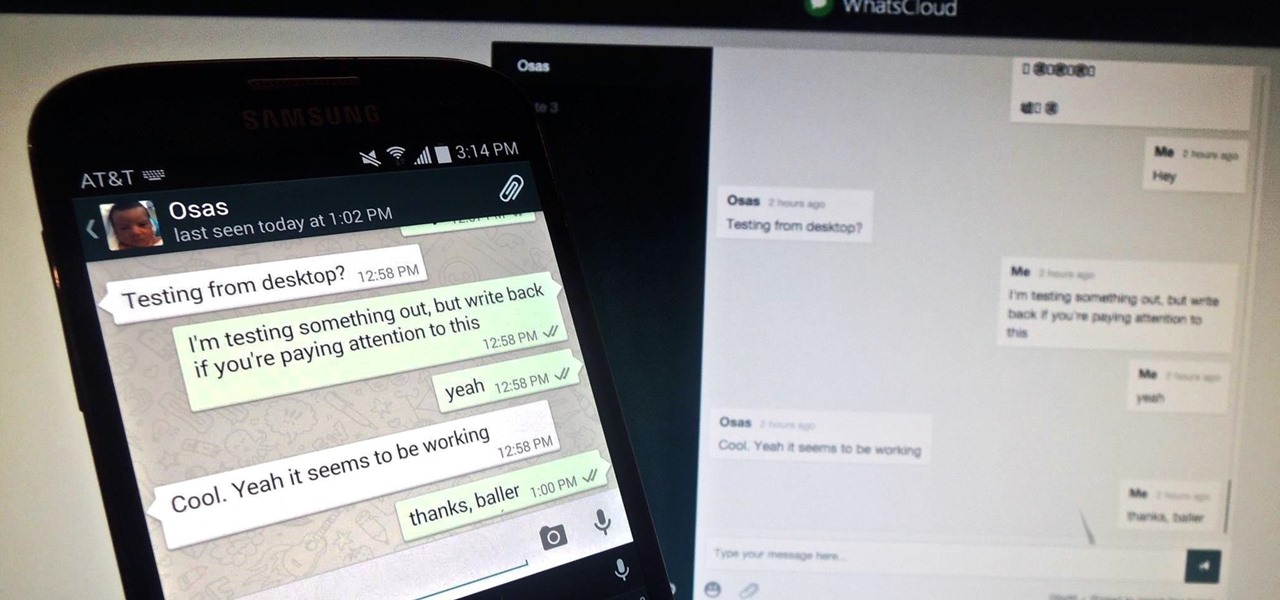
Pretty much my only gripe with computer-side messaging clients like Mighty Text is that they don't allow you to send and receive messages shared through WhatsApp, the popular third-party messaging application, which was purchased earlier this year for $19 billion by Facebook.
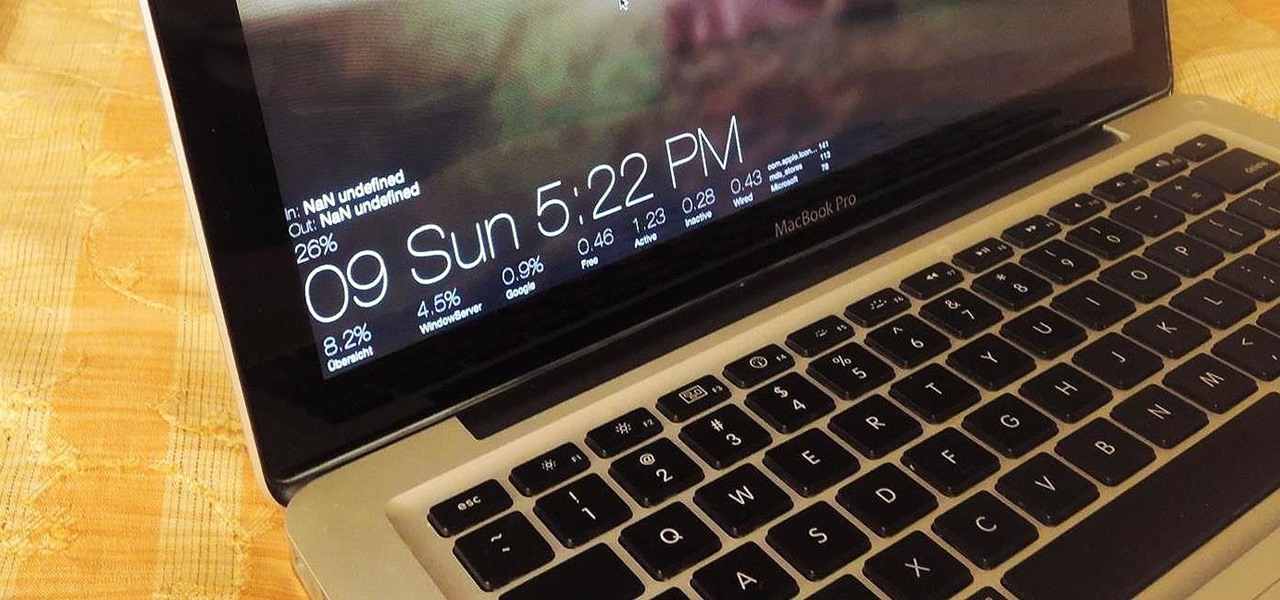
Apple hasn't been the most avid supporter of widgets over the years. Yes, they added them to the Notification Center in Yosemite, but that requires a drawer to be opened and closed whenever you want to check them. In my search for a better solution, I came across Ubersicht by developer Felix Hageloh.
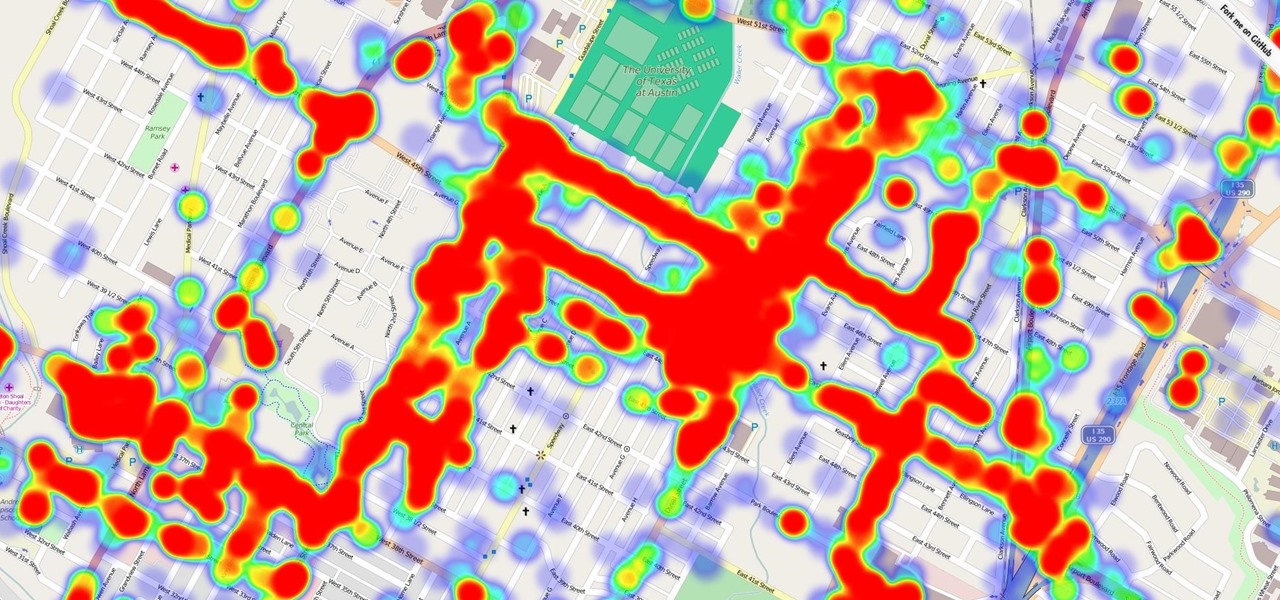
With an Android device left at its default settings, your location history is automatically recorded. You can view and manage this data, but the simple interface of points plotted on a map leaves a lot to be desired.

While some mobile sites have built-in text-resizing tools, many do not. A lot of those that don't won't even let you pinch-to-zoom. That makes it difficult for people with low vision to read small fonts on their iPhones. In some cases, like with photo captions, even those with perfect eyesight suffer.

As this generation continues to evolve, we become more involved with social media. For example, you may have a Facebook, Twitter, and a Google+ account, and be heavily involved in using all three, but the constant switching between sites, logins, and conversations can get very tedious.

Welcome back, my neophyte hackers! Many newbie hackers seem to be confused regarding the process or methodology to employ a successful hack. Most want to simply go straight to the exploit without doing the due diligence to make certain that the hack will work and you won't get caught.
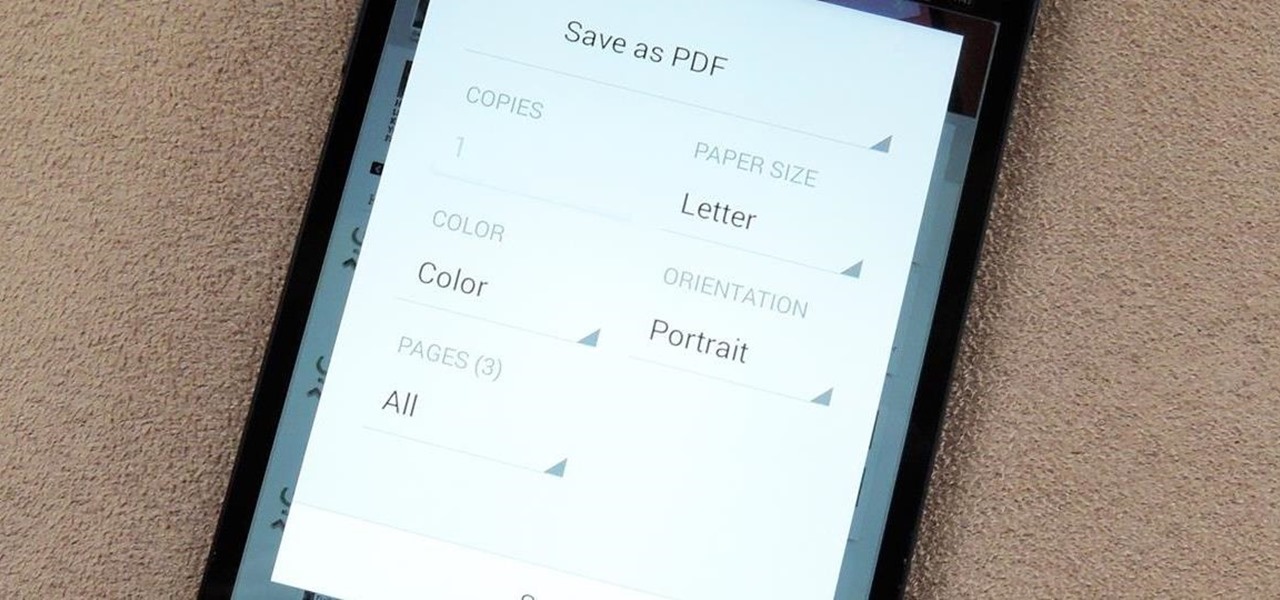
You may not always be connected to the internet, but if you're anything like me, your thirst for web content is insatiable. Whether you're on an airplane or stuck in an area with no reception, having some offline content stored on your Nexus can definitely save the day.
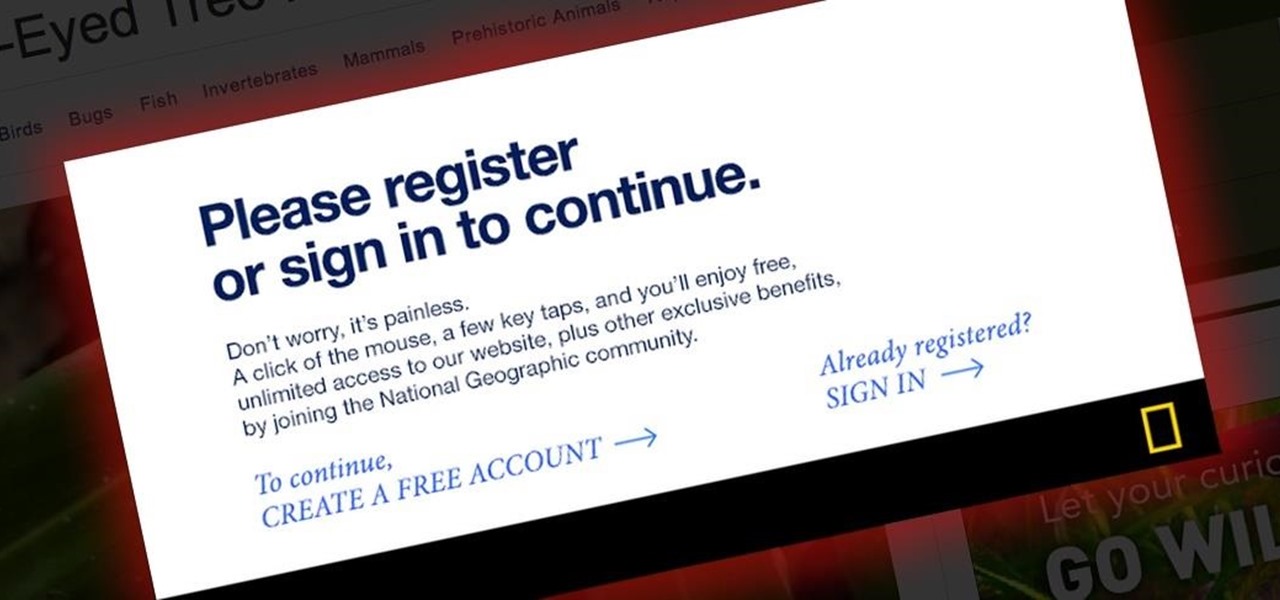
Last night, I was reading a riveting National Geographic article on the green-eyed tree frog, until I was quickly interrupted by an annoying popup asking me to "create a free account" or "sign in." Really, I'd like to do neither. I just want to read about tree frogs.

Welcome back, my fledgling hackers! A short while ago, I did a tutorial on conducting passive OS fingerprinting with p0f. As you remember, p0f is different from other operating system fingerprinting tools as it does not send any packets to the target, instead it simply takes packets off the wire and examines them to determine the operating system that sent them.

Do you have a passion that you would like to share with the world, but not sure how to do it. If so, that was my story too. I knew the niche I wanted to share, but I had no computer, video editing, website, or any other digital experience.