
How To: Create comments box with Facebook Connect in 5 min
A quick tutorial by Facebook engineers on how to create a Comments Box social widget quickly and easily for iframe applications and websites.


A quick tutorial by Facebook engineers on how to create a Comments Box social widget quickly and easily for iframe applications and websites.
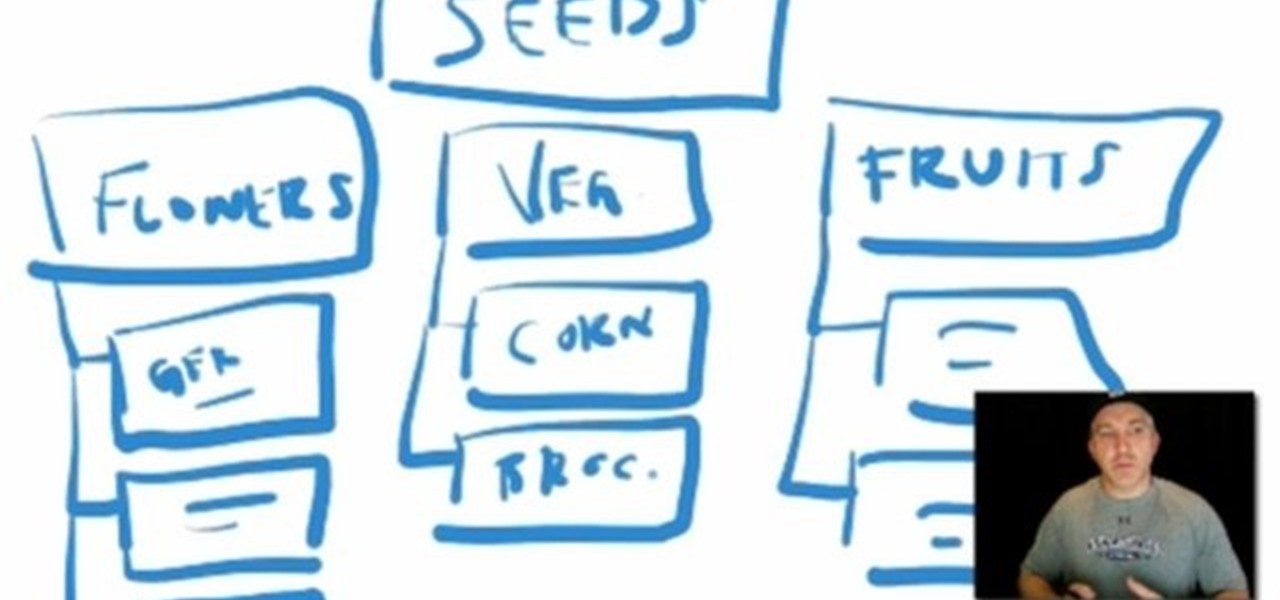
This video tutorial explains how to structure your web site the right way using content silos. But what's a content solo, you ask? Watch this video SEO tutorial to find out. Make structural improvements to your website such that Google has an easier time isolating your keywords with this how-to.
Whether it's a small business or a work group inside a large corporation, all members need access to the same materials in order to work effectively. Mac OS X server makes it easy for groups to collaborate and communicate through their own Wiki-powered Internet website. To learn how to use Wiki Server with Mac OS X Server, watch this video tutorial.
iWeb '08 introduces my albums templates. My album templates is a fast way to create and navigate web photo galleries. This tutorial shows you how to use the my albums templates and create a photo album page for your website in iWeb.
Are you a chat fanatic? Do you have a website with chat functionality built in? Have you seen other people with chat emoticons that you don't have? It's possible they designed their own emoticons and you can too! This Photoshop tutorial will show you how to design custom emoticons easily in Photoshop.

Learn how to design and create a stunning and unique logo for your business or website, using the gradient tool and texturizer features in Photoshop. Bert shows you everything you need to make a unique logo without Illustrator and just Photoshop.
If you're learning a foreign language, it's helpful to have a native speaker to whom you can talk. In this tutorial video, you'll learn how to use italki.com to find a foreign language partner to practice speaking a foreign language. Italki.com is a free language learning website where you can find language partners with whom to practice speaking a foreign language; ask questions about learning a language; share files about language learning, like free textbooks and handouts; and get recommen...
Here's a fast lesson in hosting video on your own Drupal website using the FileField and jQuery Media modules. The Filefield and jQuery Media modules are a one-two knock out combination for allowing users to upload media files to fields in your custom content types and then playing back the media files in their matching player or handler. It represents a positive direction for treating fields containing files and is a great starting point for researching your own implementation of this recipe.

This video shows you how to use Apple iMovie HD to edit and upload your video footage to Vimeo. If you're new to Apple's iMovie and your new to the Vimeo video website, then this is the best tutorial for you.
This video shows different ways to save music from websites onto your computer.
Learn how to export a web layout made in Photoshop and build an editable website layout in Dreamweaver, then convert the page to a template for future use and ease of editing.

Are you celebrating the independence day of your country? How about displaying a flag on your website? In this video tutorial you will learn how to make a flat flag wavy using a displacement map in Photoshop.

After dipping its toes into the AR cloud arena last year, Ubiquity6 is now jumping in with both feet this year.

You may not have thought of dorks as powerful, but with the right dorks, you can hack devices just by Googling the password to log in. Because Google is fantastic at indexing everything connected to the internet, it's possible to find files that are exposed accidentally and contain critical information for anyone to see.
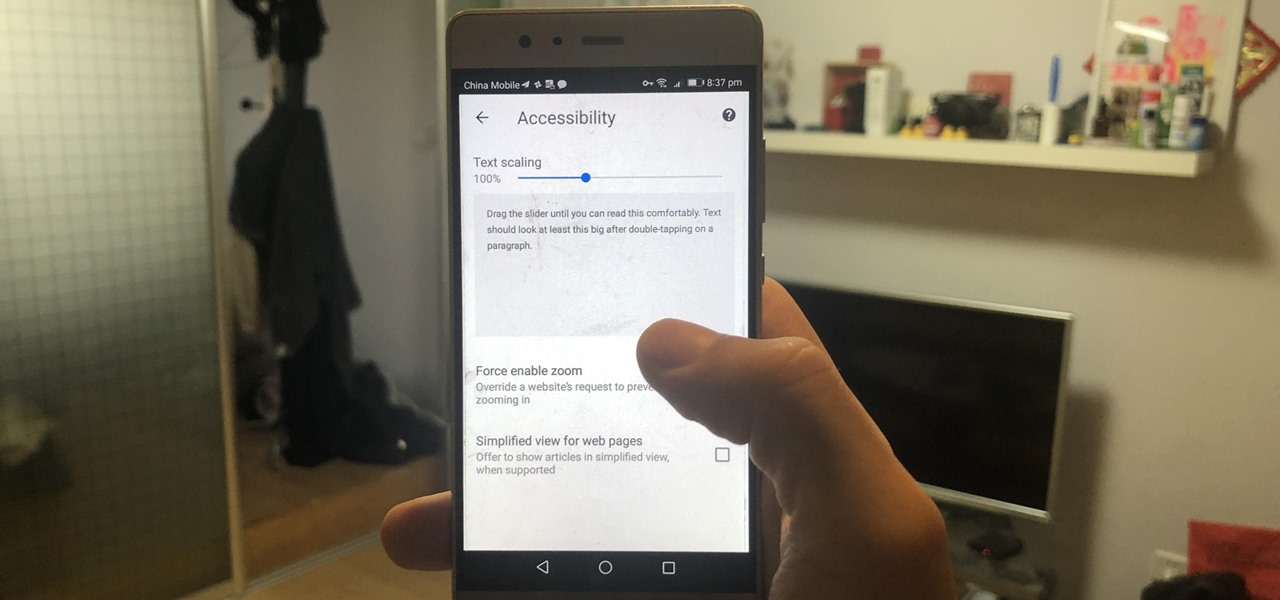
There are many reasons you might want to increase your text size in Google Chrome. The browser's accessibility options have a few tools to help the readability of text on websites. Changing the text scale, enabling zooming, and toggling the simplified view can customize Google Chrome to be perfect for you.

Over the years, TV has become more of a solo activity than ever before. It is exponentially more difficult to discuss the latest shows with friends since platforms like Netflix just release all episodes at once. Luckily, Snapchat makes it easy to keep your pals in the loop on what you're watching, so they can pick up the remote and do the same.

Stumbling upon a specifically tailored advertisement on your iPhone can be a bit disconcerting. But that's what happens when you let advertisers track your data. Some of you may appreciate more relevant ads in apps, but the rest of you might consider it a straight-up privacy invasion.
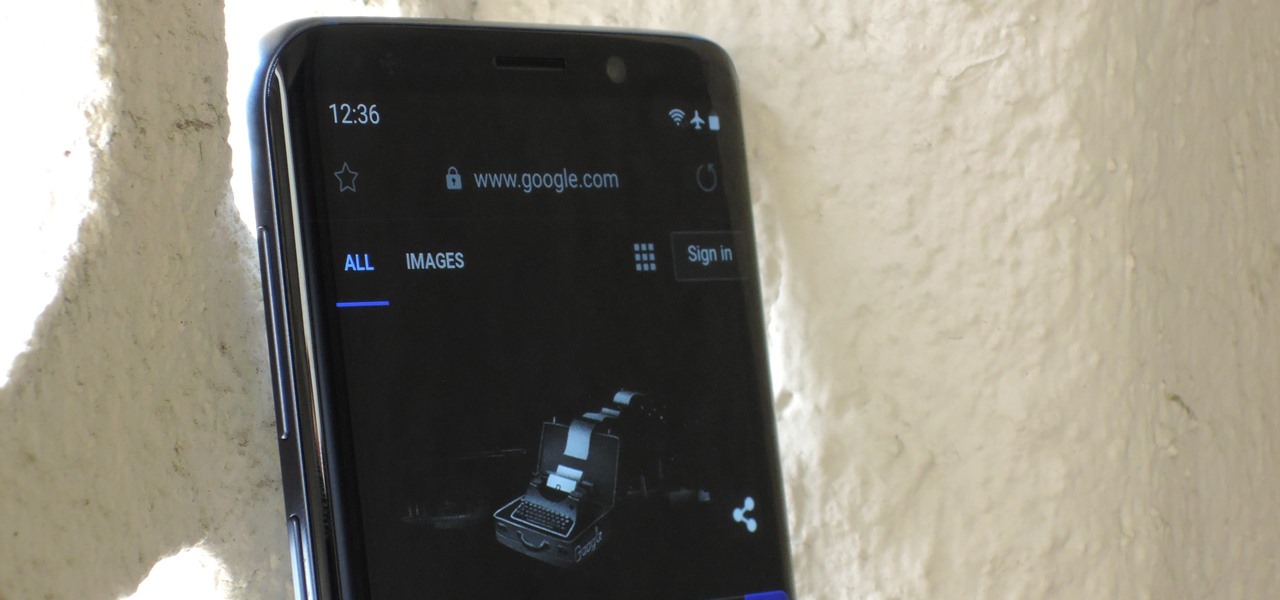
One of the headlining features in Samsung's One UI update is a new dark mode that turns stock apps and system menus black. But something you may have missed is what this theme does to the Samsung Internet app and all the websites you visit.

It only takes a few commands to manipulate a MacBook's secure HTTPS traffic and pluck login passwords out of the encrypted data. Let's take Facebook and Gmail hacking to the next level by intercepting Safari and Google Chrome web traffic in real time.

Web application vulnerabilities are one of the most crucial points of consideration in any penetration test or security evaluation. While some security areas require a home network or computer for testing, creating a test website to learn web app security requires a slightly different approach. For a safe environment to learn about web app hacking, the OWASP Juice Shop can help.

Leaked databases get passed around the internet and no one seems to notice. We've become desensitized to the data breaches that occur on a daily basis because it happens so frequently. Join me as I illustrate why reusing passwords across multiple websites is a truly awful practice — and compromise hundreds of social media accounts in the process.

Two-factor authentication (2FA) is a great way to add another layer of security to sensitive third-party apps and websites like Venmo. However, before iOS 12, to log into a particular 2FA-secured app or site on your iPhone, you'd have to memorize or copy the SMS code from Messages, then jump back in a timely manner to log in. Apple's latest iOS version streamlines this process.

Your homepage should be the site you most likely need to check whenever you start a new session with Samsung Internet. However, times change — perhaps the site you're currently browsing is just what you need to see multiple times a day. In that case, you'll want to know a quick and easy way to set it as your default homepage.

Using just a small sticky note, we can trigger a chain of events that ultimately results in complete access to someone's entire digital and personal life.

The internet is chock-full of fun and interesting content, but there's only so much time in the day for consuming it. That's when saving webpages for later comes in handy. If you don't want your bookmarks and favorites folders to clutter up fast, consider using the "Reading List" feature built right in Safari on your iPhone.

As of 2016, there are approximately 1.85 billion Android smartphones worldwide. This growing popularity has led to an increasing number hacks and cyber attacks against the OS. Unfortunately, Android users need more protection than what is offered by Google. The good thing is that there are a number of options available.

Networking is built largely on trust. Most devices do not verify that another device is what it identifies itself to be, so long as it functions as expected. In the case of a man-in-the-middle attack, we can abuse this trust by impersonating a wireless access point, allowing us to intercept and modify network data. This can be dangerous for private data, but also be fun for pranking your friends.

The creative possibilities are part of what makes Apple's ARKit so exciting. We've seen new camera effects, painting, and new ways to tell stories through ARKit. Now, the app developer studio "Orb" has created an app to let you create scenes with 3D objects of your choosing.

A fairly hidden feature in iOS 10 let you turn websites and documents into PDFs, but thanks to the new Markup function in iOS 11, this process has become a lot more streamlined.

Meta Company filed suit today against a former employee and his startup DreamWorld USA, Inc. for the misappropriation of trade secrets and confidential information.

Dirty, malformed, and outright mischievous text strings have long been the enemy of interactive website developers. Strings contain any combination of letters, numbers, spaces, and punctuation, and are entered into text boxes on websites by users. These strings in particular can do everything from highlighting XSS vulnerabilities to soliciting 404 error pages.

If you want to make some money from catching bugs and are sick of pentesting Facebook, Google, and Microsoft's products, Uber may be your new favorite playground.

Roughly four years ago, Adobe decided to abandon development of the mobile version of their popular Flash Player browser plugin. Their excuse at the time was that this move would enable them to focus more on HTML5 development for mobile devices and allow them to put more effort into maintaining the fluidity and security of their desktop Flash plugin.

Though you can use the Social Engineering Toolkit to clone websites, this way is much more customisable.
There are a bunch of new and interesting features packed inside of Windows 10, but one of the most exciting ones is the Microsoft Edge web browser, the long-awaited replacement of Internet Explorer.
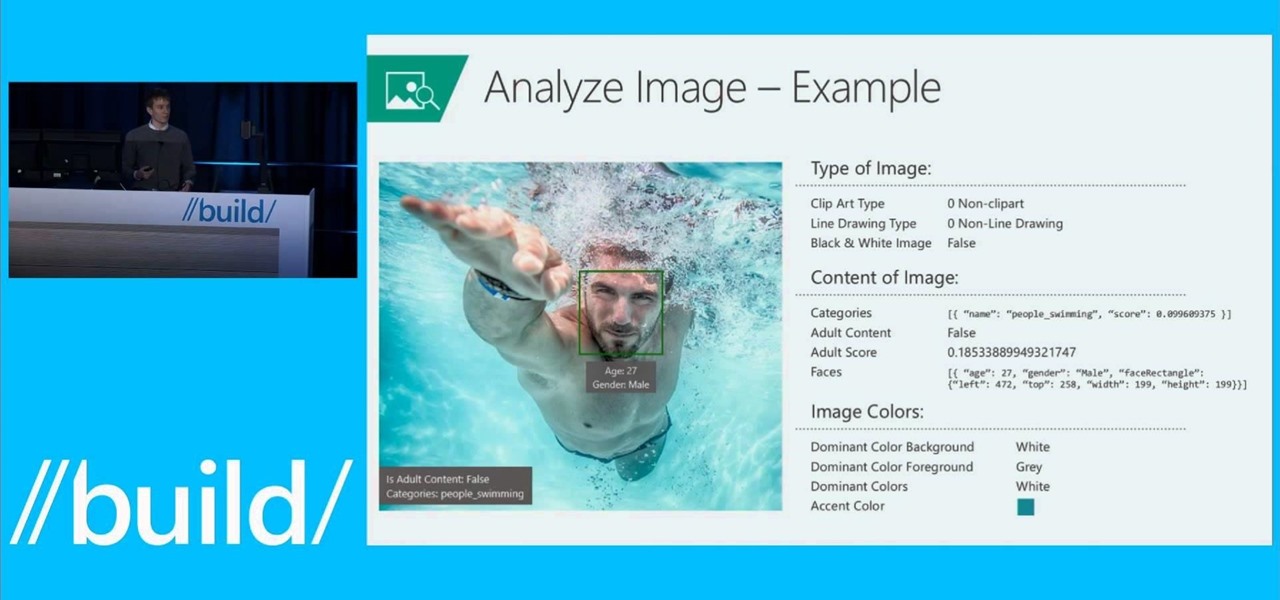
Microsoft is developing a new API project called poject "Oxford," and it includes face, speech, and more "smart" API technology. Despite being Microsoft, I actually found this to be very useful. ;)
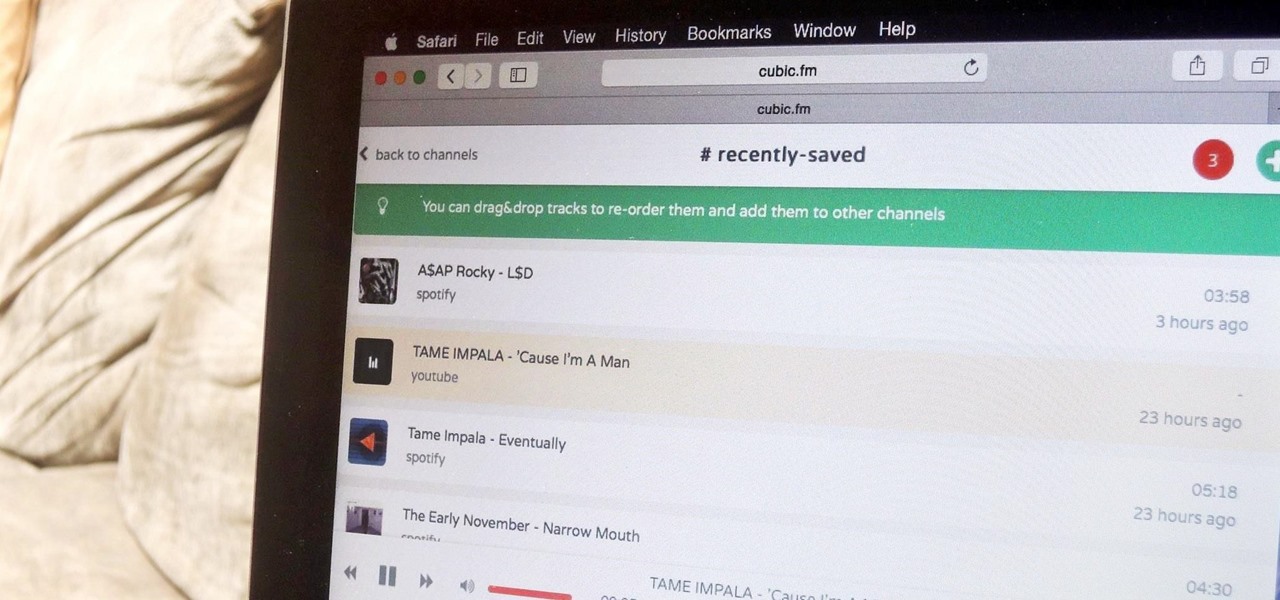
The options for finding random or specific music to listen to are vast. Spotify is excellent for streaming popular music and new releases, while SoundCloud provides a healthy dose of user-generated remixes and originals. And then there's YouTube for everything else.

Welcome back my fellow hackers. Today I'm going to teach you how to preform an Idle Scan. You may be asking what is an Idle Scan. Its a very stealthy scan because you don't use your own ip you use a zombie (in computer terms).

Welcome back, my novice hackers! In my series on cracking passwords, I began by showing off some basic password-cracking principles; developed an efficient password-cracking strategy; demonstrated how to use Hashcat, one of the most powerful password-cracking programs; and showed how to create a custom wordlist using Crunch. In this tutorial, I will show you how to create a custom wordlist based upon the industry or business of the targets using CeWL.
These days, phone calls aren't always the best way to communicate with others. Maybe you need to reach people out of the country, or you simply want to have a more visual conversation. Either way, there's a reason why video calling has become so popular.