Learn how to create a drop shadow that runs along your site, and, if your site expands, expands with it! Start in Photoshop to create a nice little drop shadow graphic and then head to Dreamweaver for some fun with CSS and divs. Looking for an easy way to create 3D shapes? Have Photoshop CS3 or later? Whether you're new to Adobe's popular image editing software or simply looking to pick up a few new tips and tricks, you're sure to benefit from this free video tutorial from TutVids.
For the proud fantasy weapon enthusiasts among you who does have the privelege of access to blacksmithing equipment, making a cardboard-and-clay replica sword is a fun and safe alternative project. This video demonstrates how to make a replica of the sword Perseus uses in the iconic and recently-remade film Clash of the Titans. Any practicing hobbyist should have all the necessary tools. The video makers website has very detailed step-by-step instructions to accompany the video here.

Stuffed bell peppers can be prepared in an infinite number of delicious ways. Whole peppers, half peppers, red or green peppers, meat or vegetables or both? The debate will rage as long as chefs like to talk, and that's not going to change any time soon. This particular recipe calls for beef sausage and rice as the principal elements of the stuffing, and halved green peppers for the shell. As always, the dish is easy to prepare, takes quite some time to cook, but yields a delicious, hearty re...

Learn from Betty Crocker Kitchens, how to easily and quickly make a dinosaur birthday cake. You do not need a special cake pan for this recipe. She uses two 9" round cakes, to cut all the shapes you need to make the dinosaur. It is only required to cut out 3 shapes, and you can print the templates from their website. After the shapes are cut, you use the frosting to "glue" the cake to the platter you are working on and then spread a thin layer of the frosting all over the cake to seal in the ...

In this Home & Garden video tutorial you will learn how to step down or end your patio wall. This video is from www.allanblock.com. Get the installation details and the location of the nearest dealer from the website. The instructions are on How-to sheet #160. The easiest way to create step down is to create corner blocks. Simply place corner blocks at the end of each course overlapping the block as the wall steps down. Finish the wall with wall caps. Once the wall caps are in place, you can ...
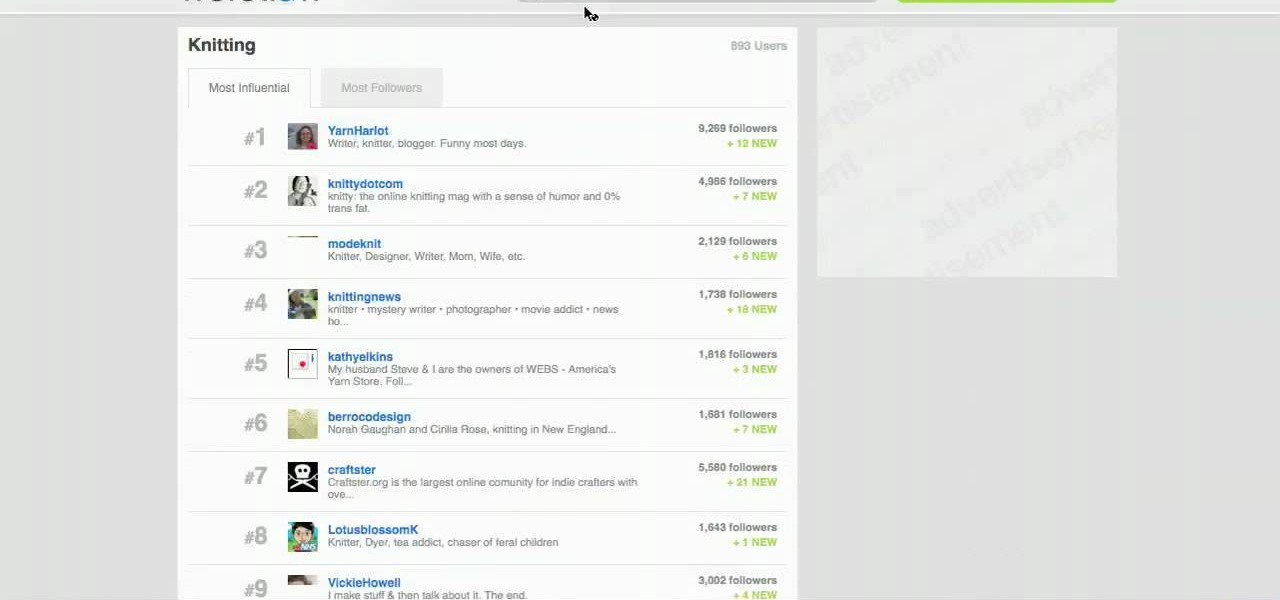
In this how-to video, you will learn how to use the website Wefollow for twitter. This will allow you find more people to follow you on twitter. You can list yourself under a category so people can find and add you. If you are an antique dealer, you can label yourself as one. This allows you to be searched for and added. You will get higher on the search list as you get more influence and more people following you. If you are looking for people to follow in your niche, you can type in the nic...

This video from the website What to Cook When shows us how to crack open the crab legs and get the meat out of them. Firstly starting with the cluster of legs, simply grab one of the legs and break it off of the cluster. Now simply grab the leg and starting with the joint, break it into half and pull it apart. Then take the middle section which you just broke and put your fingers right in the middle of that section, crack that one leg and then flip it over and crack it the other way. And once...

Facebook is a social networking website where you can stay in touch with your friends and even make new friends. Using Facebook you can suggest your friend to some one else on Facebook. To do this first open the profile of the person you want to suggest. Scroll down and to the left you will find a link which says suggest friends to others. Click on it and this brings up a list of people who are in your friends list. Now select all the people you want to suggest this person. You can select mul...

Whether you are protecting your children or hiding personal information, there are ways to block unwanted websites from your computer. Follow this tutorial and learn how to accomplish this on a Windows PC easily.

This video shows you how to install OSX on a Windows Netbook. They create a "Mini Mac" and show you what the steps are. This is a good thing to do for someone who is used to a Mac but wants the portability of a Netbook, which weighs only 2 pounds. They start with a Dell Netbook that has Windows XP on it, which they covert. One thing that you need to do is to increase the memory in order to install the new operating system. There is an informative website called MyDellMini that has helpful inf...

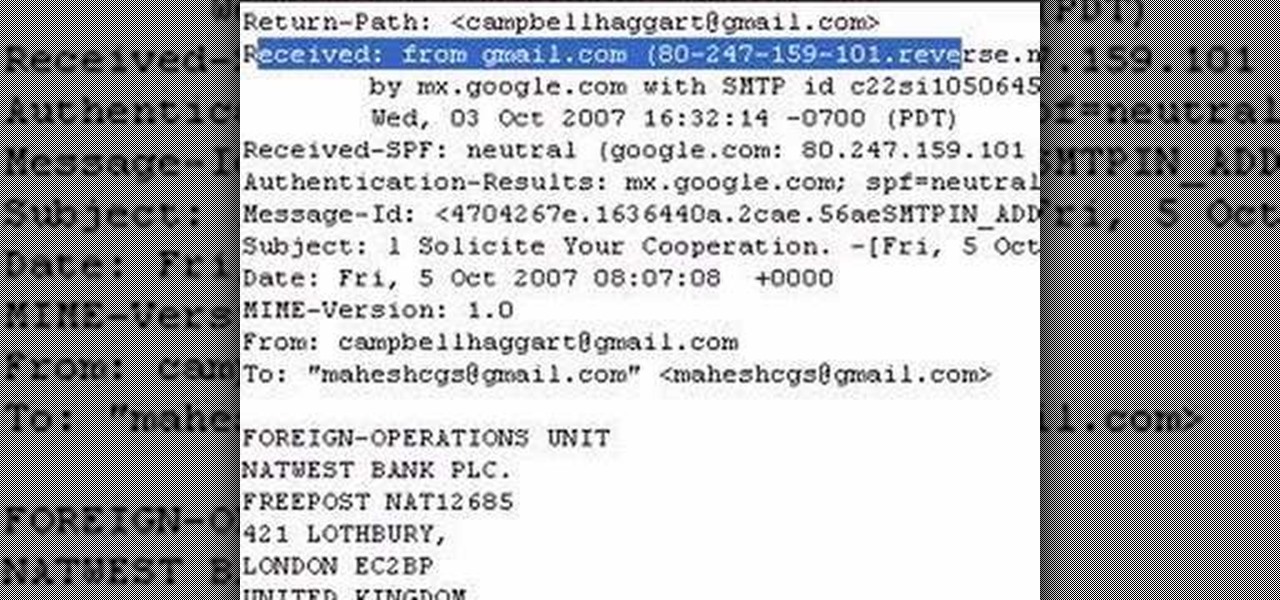
The author shows how to identify the IP address of a email. He shows how to check the 'Show Original' options in Gmail and in that content how to identify where the email came from and exactly its IP address. Now we can take that IP address and go to any of the many IP lookup websites and trace the original geographical location of that IP address. By following the steps in this tutorial you can easily trace out the origination IP address of an email from which you can extract a lot of useful...

Customizing your user account online for Ford's new SYNC system is a cinch. Simply go to the website and customize news and sports, vehicle health reports, and your personal favorites. You can even start out by adding your favorite destinations for turn-by-turn directions later. Learn how to customize your Ford SYNC online user account.

Club Penguin is a flash-based website with an a virtual world of online games for kids to play. Learn how to hack Club Penguin with tricks and cheats. Watch this video tutorial to learn how to find hidden items in the Club Penguin catalog (09/29/09).

Kids... it's dance time! Check out this dance video tutorial on how to do a ball change step in hip hop dance for kids.

Kids... it's dance time! Check out this dance video tutorial on how to do a body roll step in hip hop dance for kids.

Welcome to a tennis lesson from FuzzyYellowBalls, the the best place to learn how to play tennis online. Our free video tennis lessons teach you how to play the game in a new way that combines technical analysis, visual learning, and step-by-step progressions.

How to Use Your Mac as a Server: Turn your Mac Mini into a server! Yes, that's right, with a little know-how and a little spunk, you can turn an inexpensive Mac Mini computer into a server to provide services over you network. You won't even need the Mac OS X Server, just the Mac OS X Client, so there is no extra software to buy, just the Mac Mini and it's operating system.

How to Use Your Mac as a Server: Turn your Mac Mini into a server! Yes, that's right, with a little know-how and a little spunk, you can turn an inexpensive Mac Mini computer into a server to provide services over you network. You won't even need the Mac OS X Server, just the Mac OS X Client, so there is no extra software to buy, just the Mac Mini and it's operating system.

This software tutorial takes a look at how to design an icon set in both Photoshop and Illustrator. An icon set is a set of icons that you can integrate into a number of different projects, like a website or a company letterhead, logo and identity set up. Having an icon set readily available for all your project needs will make your workflow faster and simpler. So watch and see how to make an icon set first in Photoshop and then in Illustrator.

I'm always looking for solutions to problems people are having with their smartphones. This means I spend a lot of time browsing forums and release sites looking for new apps. In doing so, I find a lot of apps that don't quite solve a major problem, but are nonetheless pretty cool. I came across four of those this week.

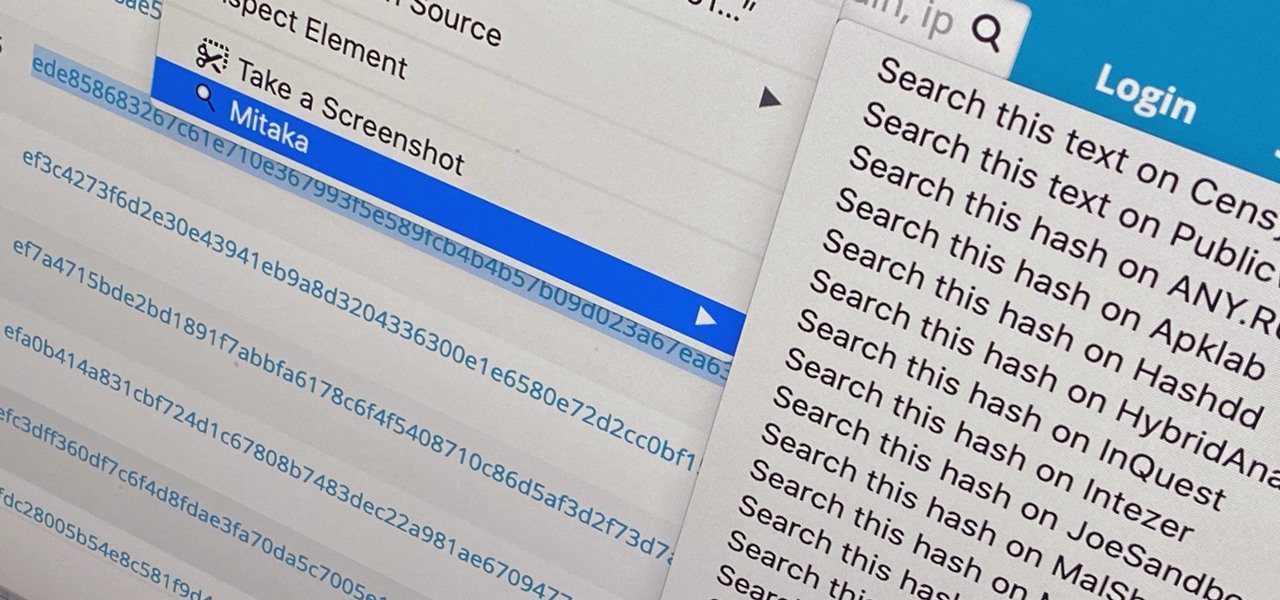
Web browser extensions are one of the simplest ways to get starting using open-source intelligence tools because they're cross-platform. So anyone using Chrome on Linux, macOS, and Windows can use them all the same. The same goes for Firefox. One desktop browser add-on, in particular, makes OSINT as easy as right-clicking to search for hashes, email addresses, and URLs.

Since it first launched in 2003, WordPress has dominated the internet. The free, open-source content management system (CMS) is used by over 60 million websites. Wordpress is undeniably one of the most popular CMS solutions in the world.

While much of the world is currently in some form of quarantine due to the COVID-19 pandemic, augmented reality (AR) gives us all the opportunity to see virtual content while stuck in our homes.

As long as you have the meeting ID, you can join and interrupt virtually any video call on Zoom. And that's how we get terms such as "Zoom-bombing," where someone jumps into a chat to say or visually show vulgar and inappropriate things to the other participants. However, hosts can put an end to it.

The COVID-19 pandemic has created a frenzy for news and information that is nearly unprecedented in the smartphone era, with a major side effect of misinformation. Now, major tech companies are making it easier to ask for advice about novel coronavirus from their respective digital assistants. Results may vary, but Apple and Google are the most useful at the moment.

Google has always experimented with Chrome's UI, but when they make more drastic changes, they start by hiding them in the feature flags menu. One of the latest designs makes Chrome more accessible in a world of big and tall phones.

On Twitter, you can pin one of your tweets or replies to your profile, so it's the first post people see when they visit your page. However, Twitter prevents you from pinning someone else's tweet. You can't even pin something you retweet. There is a clever workaround, though, and it also works for posting empty tweets.

We already know that major players like Magic Leap have been planting the seeds of augmented reality for mainstream consumers through wireless partnerships with AT&T, NTT Docomo, SK Telecom.

When researching a person using open source intelligence, the goal is to find clues that tie information about a target into a bigger picture. Screen names are perfect for this because they are unique and link data together, as people often reuse them in accounts across the internet. With Sherlock, we can instantly hunt down social media accounts created with a unique screen name on many online platforms simultaneously.

While browsing the web on a computer, most of us are familiar with using Ctrl + F (or Command + F) to search for a specific word on a page — but what if you want to do that on mobile? If you're using Google Chrome, there's a simple way to search for specific words on iPhone or Android.

If you don't want the large and permission-hungry Facebook app on your phone, the perfect solution is to create an app icon for the Facebook mobile site on your home screen. The website version of Facebook doesn't run background tasks, has no distracting notifications by default, you won't be giving Facebook as much data, and your phone's battery life will be improved.

With an inconspicuous Android phone and USB flash drive, an attacker can compromise a Windows 10 computer in less than 15 seconds. Once a root shell has been established, long-term persistence to the backdoor can be configured with just two simple commands — all while bypassing antivirus software and Windows Defender.

Giving up your Wi-Fi password can be giving up more control than you think. Because of the way Chromecast and other IoT devices communicate, anyone on the same Wi-Fi network as your device can often make it do whatever they want. With a script called "Cast All the Things," we can hijack a Chromecast to play nearly any kind of media with a single command in terminal.

Directory traversal, or path traversal, is an HTTP attack which allows attackers to access restricted directories by using the ../ characters to backtrack into files or directories outside the root folder. If a web app is vulnerable to this, an attacker can potentially access restricted files that contain info about all registered users on the system, their permissions, and encrypted passwords.

ARP spoofing is an attack against an Ethernet or Wi-Fi network to get between the router and the target user. In an ARP-spoofing attack, messages meant for the target are sent to the attacker instead, allowing the attacker to spy on, deny service to, or man-in-the-middle a target. One of the most popular tools for performing this attack is Ettercap, which comes preinstalled on Kali Linux.

Amazon Web Services is calling up an age-old tactic of the tech industry — the hackathon — to drum up excitement and encourage the development of apps built on the Amazon Sumerian AR/VR platform.

For anyone using open source information to conduct an investigation, a balance between powerful tools and privacy controls are a must. Buscador is a virtual machine packed full of useful OSINT tools and streamlined for online research. This program can easily be set up in VirtualBox, and once that's done, we'll walk you through some of the most useful tools included in it.

Hackers rely on good data to be able to pull off an attack, and reconnaissance is the stage of the hack in which they must learn as much as they can to devise a plan of action. Technical details are a critical component of this picture, and with OSINT tools like Maltego, a single domain name is everything you need to fingerprint the tech details of an organization from IP address to AS number.

The easiest way around a security policy is to find users who don't follow it. The Have I Been Pwned database identifies accounts with information breached by major third parties like Yahoo and LinkedIn. With Maltego, hackers can locate breached accounts created using company email addresses, potentially giving attackers access to a company account if the employee reuses a compromised password.

While hackers adore the command line, working with the GUI (graphical user interface) of an operating system has some advantages. This is especially true when it comes to post-exploitation. When we can control the mouse and keyboard of a remote computer, we can truly say we have complete control over the device. Today, I'm going to introduce to you the PyAutoGUI module, which does just that, and just how much fun you can have with it!