Interested in pen spinning? Want to pick up a few moves? Pen spinning is the skilled movement of a writing instrument or pen with one's hands. It is used as a source of self entertainment (often for students), but there is a great deal of pen spinning culture (competitions, websites, etc.). Watch this pen spinning tutorial video and learn how to perform the "Continuous Middle Backaround 1.5" move.

This tutorial demonstrates how to quickly and easily create graphical navigation bars with DHTML menus for your website, using Xara Menu Maker.

A quick demo of how easy it is to create graphical website button bars with DHMTL menus using Xara Webstyle.

This website (www.someecards.com) is full of interesting e-cards that say what you really think instead of sugar coating it. Have fun with this one :-)

This walks you through how to create an animated GIF image file that can be used in websites, as avatar's, as icons, etc. You'll be using Microsoft Paint to create each frame of the animation, and an application called Unfreez (found here) to animate them together.

The extract tool in Photoshop is one of the most frequently used - and useful - tools you'll ever learn to use. Extracting allows you to remove a picture from its background or even filter away flyaway hair.

You can make almost any website your homepage but what if you have more than one favorite? How do you choose? With FireFox you don't have to because you can set multiple homepages.

This video explains how to organize your photos into folders on the Pictage Photo Lab website.

See how to add grungie borders to your images to give them a cool effect in Photoshop. If your borders are white and the background of the background of the website or page you are uploading them to is also the borders will blend in giving it an even cooler look. This is a great Photoshop picture effect!

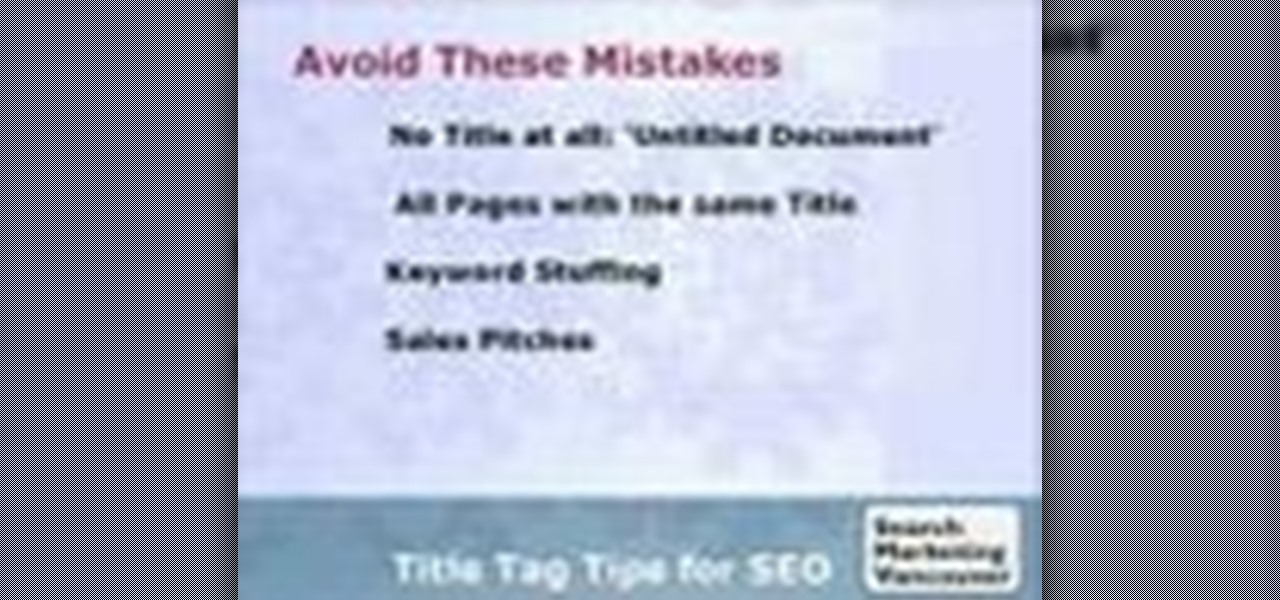
How to write Page Titles for your Title Tags from Search Marketing Vancouver. Learn how effective Title Tags can improve your SEO Results on Google and increase traffic to your website.

In this video, you'll discover how to upload files to your own website or blog using FTP.

This guitar lesson demonstrates how to play the recorder/keyboard intro to Stairway to Heaven as I have transcribed it on guitar. Tabs for this lesson are available on my guitar lesson website, on the "NEW STAIRWAY TO HEAVEN VIDEO" link:

This tutorial demonstrates how to create message boxes for a website using Adobe Dreamweaver.

Another NewDarkRoom.com Video tutorial. This tutorial will show you how to get more room out of your photo booth by hiding all the unwanted parts past your seamless paper. As usual you will be able to find a more detailed larger video at our website.

If you're putting your email address online on your own website, or sites like facebook or myspace, you may want to be a bit clever about it. Check out this tutorial and see how to protect your email address from spam.

Django is a Python web framework used for rapid application development in any environment. In under 10 minutes, you can go from a bare Linux (Ubuntu) installation to a fully functional Django server.

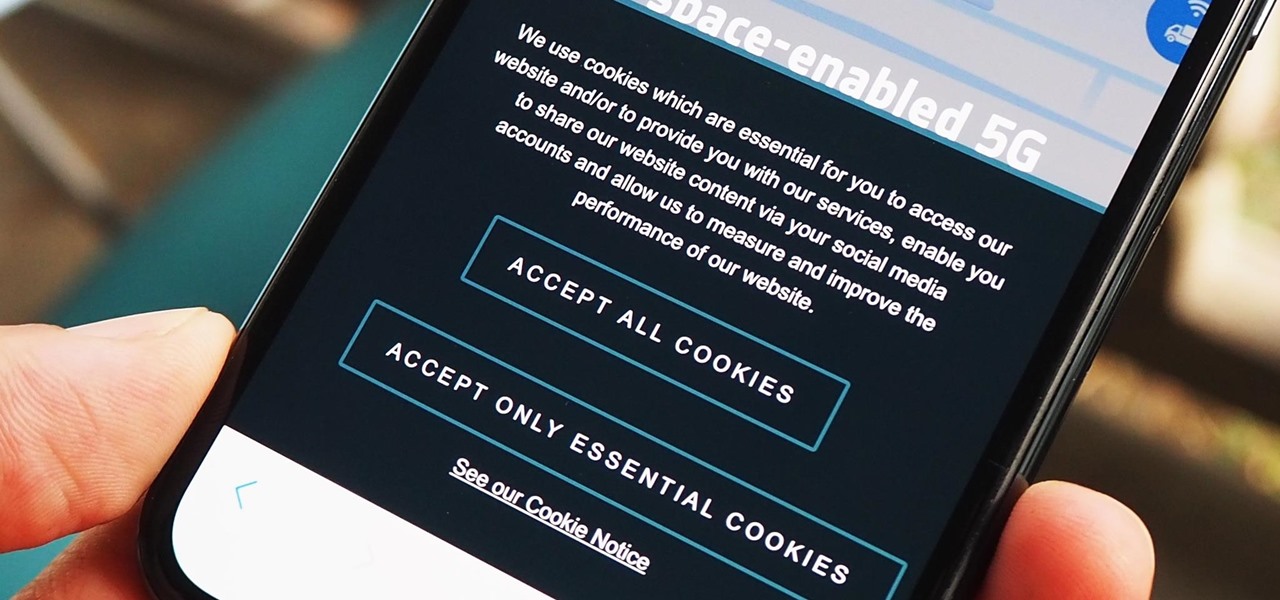
As a means to combat annoying and intrusive advertisements in Safari, Apple added native support for content blockers on the iPhone. Instead of being bombarded by notifications, banners, and pop-ups, content blockers prevent them from opening, which can also be said about those annoying cookie consent notices that many websites now have.

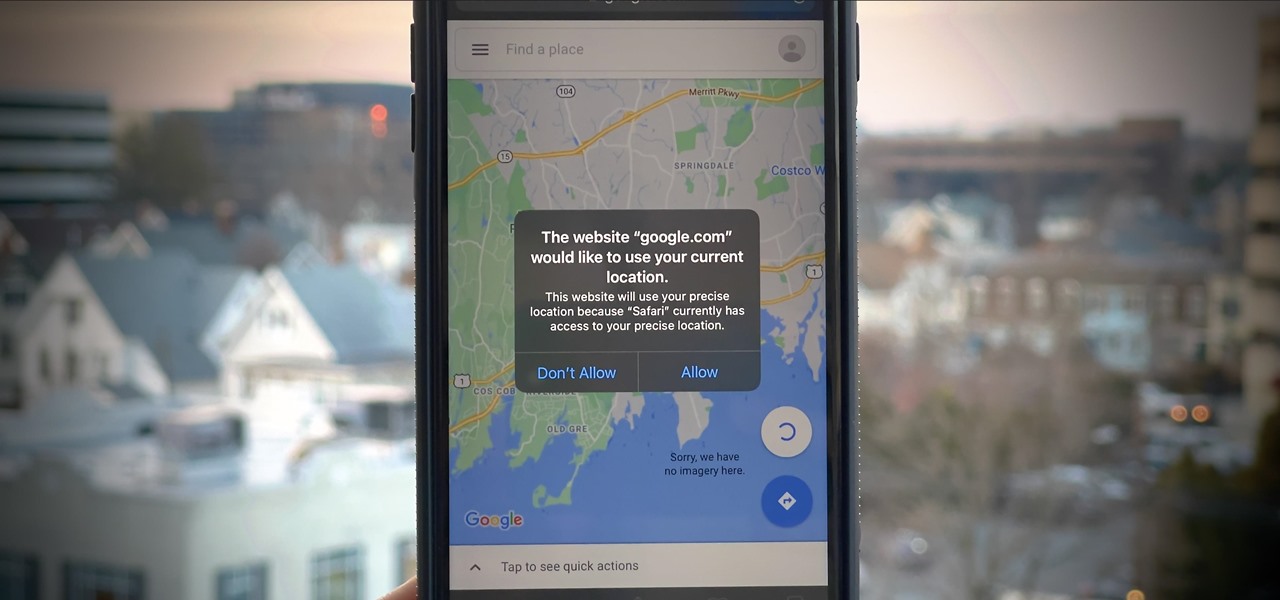
If you surf the web on your iPhone, you no doubt run into this problem all the time: a website wants your location. It can happen when performing a location-based task, such as using a store locator, or whenever a web app just wants to deliver better ads or local recommendations. If you're tired of allowing or denying permission each time, there's an easy way to stop the annoying security pop-ups.

It's pretty much a given at this point that Facebook has a lot of data on us. While you might be conscious of the data you share with Facebook when you post, upload photos, or chat with friends on Messenger, you might not be thinking about all the data it receives from websites and apps you use outside the social media giant. Now, you can actually do something about it.

Apple has seemingly always made it a priority to show how much it cares about user security and privacy — enough that it has a page dedicated to it, proclaiming that "privacy is a fundamental human right." It's true that there are few issues more important than user privacy when it comes to technology, and Apple only makes things better in iOS 13.

Business hours and addresses change, but they're not always updated on Yelp by business owners for the rest of us to see. Showing up when a business is closed or going to the incorrect address is a major annoyance, which is why the company allows us, the customers, to help update business information through the Yelp mobile app on iOS and Android. If owners won't do it, somebody has to.

Your social security number, credit card information, and medical history can fall into the wrong hands if you're not careful about how and where you share your data online. If you really care about your data, there are tools and techniques you can utilize to protect yourself from cyberstalkers, advertisers, and hackers in a time when digital lives are a high commodity.

During the keynote at WWDC earlier this year, Apple introduced the latest iteration of its mobile operating system, iOS 12. Despite a thorough demo on stage, Apple glossed over new eye tracking features that use ARKit 2. Developers can now use the TrueDepth camera on the iPhone X, XS, XS Max, and XR to determine where your eyes are looking, opening up incredible new possibilities for new apps.

Nmap is more powerful than you know. With a few scripts, we can extend its functionality beyond a simple port scanner and start to identify details about target servers sysadmins don't want us to know.

Reconnaissance is the phase of an attack where a red team or hacker designs a strategy based on the information they can learn about the target, as well as what the available attack surface looks like. These scans can take time to discover relationships, but Raccoon OSINT scanner coordinates multiple automated scans to produce invasively detailed reports on a target with a single command.

There are nearly 100,000 unique onion service addresses online with over two million people using Tor every single day. Join me as I explore a small fraction of what the Tor network has to offer.

A convincing domain name is critical to the success of any phishing attack. With a single Python script, it's possible to find hundreds of available phishing domains and even identify phishing websites deployed by other hackers for purposes such as stealing user credentials.

Identifying vulnerable devices and services on a target router can be difficult without leaving logs and other traces of an active attacker on the network. However, there is a way to covertly decrypt and view Wi-Fi activity without ever connecting to the wireless network.

The world of investment and finance can be labyrinthine in its very nature — and even more complicated in regards to augmented and mixed reality. While these new emergent technologies are teeming with explosive levels of unrealized potential, there's still a big layer of uncertainty in terms of return — but these investors aren't afraid to take the leap.

Welcome back, my greenhorn hackers! Throughout this series on Metasploit, and in most of my hacking tutorials here on Null Byte that use Metasploit (there are many; type "metasploit" into the search bar and you will find dozens), I have focused primarily on just two types of modules: exploits and payloads. Remember, Metasploit has six types of modules:

so i have just signed up to this, and i dont know much about this website but i wanted to show my recent upload

Custom Timelines (CTs) allow you to control exactly which Tweets appear in a column on Tweetdeck. So if a particular event catches your eye as newsworthy you can tailor your CT to show what you consider to be the most relevant Tweets. These CTs can then be customized, shared and embedded on your website. This is a great way of increasing interaction on Twitter and sharing current, interesting and breaking news stories from any niche or subject

How to Henna Your Hair Tutorial Pt.2 Please Dont forget to Watch Pt. 1

Video: . How to Henna Your Hair Tutorial #1

Very interesting interview with the editors of the New York Times Lens Blog, a website which is totally dedicated to photojournalism and videojournalism.

Welcome back, my novice hackers! Most of my tutorials up until this point have addressed how to exploit a target assuming that we already know some basic information about their system. These include their IP address, operating system, open ports, services running, and so on.

Learning how to use other text panels in the designs gallery. This website design tutorial will teach you how to add a note panel, numbered panel and one additional text panel.

This web design Tutorial will walk you through process of linking to files on your computer. You can link file types including but not limited to Microsoft Word, PowerPoint, PDF, Videos and so on for download on your website.

In this web design tutorial we will show you how to protect yourself from losing your work just in case the program malfunctions, computer crashes or you accidentally forget to save document and so on. I highly recommend you utilize this Web Design Tutorial especially if you are working on large websites for clients.

This Professional Website design Tutorial will show you how to place text on a curve using the line tool. However you can put text on the outline of shapes and other objects.