Microsoft's HoloLens comes with helpful features for capturing video and photos, but sharing whatever you record isn't as straightforward as you might expect. So here are the many ways to get your media off the device to share with the world.

Whether you simply can't stand it or consider it a separate food group (or not food at all), there's no denying that Spam is everywhere. America's favorite canned mystery meat got its humble beginning in Minnesota, but is now used in dishes and found in homes around the globe.

Greetings fellow students! I'm currently reading a book called "Violent Python: A Cookbook for Hackers, Forensic Analysts, Penetration Testers and Security Engineers"

Welcome back my, tenderfoot hackers! Many people come to Null Byte looking to hack Facebook without the requisite skills to do so. Facebook is far from unhackable, but to do so, you will need some skills, and skill development is what Null Byte is all about.

As Android's official app provider, the Google Play Store is packed with thousands of useful programs. But Google's terms of service is extremely restrictive, which means that countless apps simply don't qualify to be hosted on the Google Play Store.

Hello ladies and gentlemen, welcome back to the Part 2 of our UDP & Wireshark adventure as I promised. Last time we discussed about what DNS is and how it uses UDP as its transport protocol but we left some unexplained parts behind and I'm about to investigate those with you. I would advice you to go back to Part 1 so you can have a clear understanding in case you don't feel comfortable with the topic. So our computer made its request to the DNS server and asked "Hey, I want to find out what ...

If you use a wireless mouse or keyboard, you could be leaving yourself open to attacks from hackers. Researchers at Bastille had discovered in January 2016 that attackers could make use of a cheap $15 antenna to sneak into your computer through a wireless mouse or keyboard dongle (receiver).

Hello people again, I wrote my last post about crypto about 10 months ago, now I will introduce something not fresh for the science, but fresh for the people who wants to learn. In my http://null-byte.wonderhowto.com/forum/cryptography-0161538/ post of crypto concepts, there is just basics, today we will see something that targets wide concepts like Symmetric crypto, Public Key Cryptography, Hashing, Keys etc...

The Google Now on Tap feature puts the power of Google Search inside each and every application on your Marshmallow-powered device, allowing you to retrieve contextual results based on the content on your screen.

Hello fellow gray hat hackers, I wrote a program in python that helps me to fill up my proxychains.conf file, so I don't have to manually enter in the proxies. I figured I will give a little how-to of how I did it and maybe I could help some of you(hackers) out there to stay anonymous.

before I move on to more exciting areas in this series, I want to also point out some things to protect your information & how to not get DoXed.

Greetings all. Today I intend to append a new series to my mini-collection of posts. This series will consist of informative guides for the purpose of depicting certain aspects of the White Hat profession that I believe are of profound importance. Furthermore, I will keep this series simple for everyone to follow, regardless of your tech level. So without further ado, let's get right into it.

If you purchased something from iTunes, the iOS App Store, iBooks Store, Apple TV App Store, or the Mac App Store and it doesn't work, didn't download, is buggy, or wasn't what you thought it was, you can get a full refund from Apple—you just have to know how to ask.

Most of you probably heard about Rasberry Pi and if you haven't; what is wrong with you? But nothing less a Rasberry Pi is a computer a very small computer. Despite these size limitations, the Rasberry Pi is to not be underestimated. Not only can it do anything like a normal laptop or desktop, but, in my opinion on of the coolest features is that it boots off a Micro SD card. It can do anything that you want, but it's built to be played with. A hacker heaven.

Brand loyalty is one of the main factors behind our decision to choose a particular mobile device, but it doesn't have to be the entire equation. Educated consumers know that certain devices simply fit their budget and usage better than others, which means you can't always let a logo dictate what kind of phone or tablet you buy.

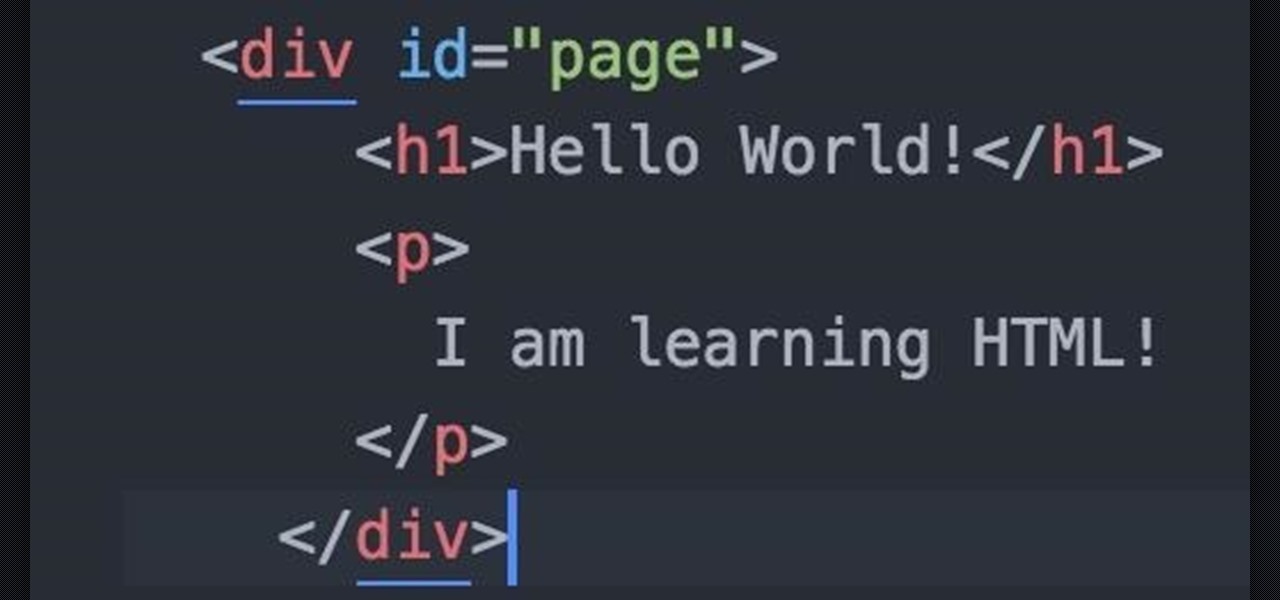
Welcome fellow Null-Byters! Sorry for the delay, this time of the year can be hectic for all of us. Hopefully this will not happen again. In this "tutorial" we will go over more styling and make our page look even better!

Switching your favorite facial cleanser isn't an easy choice. Since everyone's skin type can range from dry, to oily, to some complicated combination of both... well, let's just say that the conventional wisdom is to stick to what you know works.

The digital pen on the Surface Pro 4 and Surface Book is an indispensable tool for serious note-takers and artists alike.

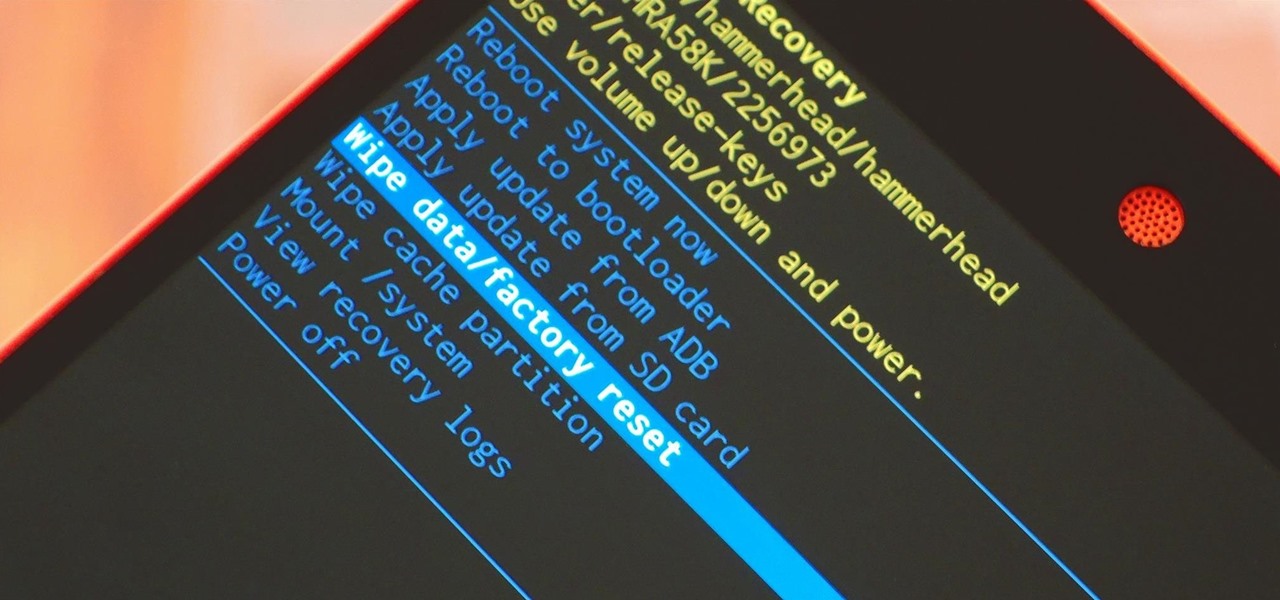
When it comes time to sell your smartphone or trade it in for your annual upgrade, you'll have to make sure that all of the sensitive data the device accumulated while you owned it is properly erased so that no one else can access it. This process is referred to as a "Factory Reset," and regardless of if you own an iPhone or Android device, like a Samsung Galaxy model, HTC One, or Nexus, I'll show you how to do it below.

You want to become anonymous, and dont want your IP to be logged on websites? Well read along here. Continuing This Series:

Welcome back, my novice hackers! More and more, the world is turning to and adopting the smartphone platform as the digital device of choice. People are not only using smartphones for voice communication, but also web services, email, SMS, chatting, social networking, photography, payment services, and so on.

Continuing this series, I am now moving on to the section, 'Anonymous'. Hope you are looking forward to read this.

I think it was 1986 when I first discovered my love for making computers say stupid things out loud. My older brother got a Commodore 64 for his birthday, which came bundled with software that would speak out any term you typed in—and boy, that computer sure made a fool of itself after my five-year-old imagination got a hold of the keyboard.

If you ever need to make calls and/or send texts to the U.S. or Canada from abroad, or even just receive them from those locations, there's an easy way to do so without breaking the bank. In fact, it's free, and all you need is a smartphone, computer, and some free tools.

If you haven't come up with a funny, innovative costume yet for Halloween, you're running out of time. While all your friends are busy perfecting their month-long DIY costume project, you're still being lazy about it and have just now started to search online for ideas.

People like to cite the iPhone as the device that started the smartphone craze, but the truth is, smartphones had existed for years by the time Apple got into the game. The real groundbreaking feature that this device brought to the table was a multi-touch screen to go along with its "smart" functionality, and this is still the main method we use to interact with our devices today.

Often, despite your favorite makeup mecca's rows and rows of endless colors, applicators, and brands, it's hard to find the perfect shade of lipstick—especially one at the price you want. Rather than resorting to what's available in stores, turn to your stovetop and a box of crayons.

One of the first orders of business after purchasing a new smartphone is to load up your shiny new toy with phone numbers, email addresses, and general contact information for all the important people in your life.

Windows 10 is officially here, and frankly, there's a ton of new features in Microsoft's latest operating system. From the return of the Start menu to the new Edge browser, Windows 10 can take some getting used to.

For many of you, this is common knowledge. But I still regularly see comments posted here and elsewhere asking, "This <AV bypass> doesn't work, because when I upload my payload to VirusTotal...."

If you remember last time, we successfully uploaded picture with a small hidden PHP command executer embedded in it onto a server. Now, our goal is to take this a step further and get an interactive shell. To do this, we need to upload another file that either binds a port for us, or connects back. For this tutorial, we will use a Python reverse Meterpreter shell.

These days, that pocket-sized computer we call a smartphone is home to your entire digital life. But with the onset of mobile payments and online banking, the line between your virtual world and the physical realm is becoming increasingly blurred.

Notes on iOS has never been a particularly great app due to a lack of overall features compared to other note-taking apps like Evernote or Microsoft OneNote.

Apple's latest update to Mac OS X, 10.11 El Capitan, is currently available in the Mac App Store for everyone to download and install at no cost. The new OS features Split View mode for better multitasking, a cleaner Mission Control, smarter Spotlight, a way to mute Safari tabs playing audio, enhanced Mail and Notes apps, and more.

Google made a huge splash this year in their annual Google I/O with an awesome announcement regarding their Photos app. Although I was primarily interested in the details surrounding Android M, my ears instantly perked up when Google announced that their Photos app will now offer free, unlimited, high-quality storage.

Before I start this tutorial, no, this is not that "Effective. Power." text that is going around. With that being said, let's talk about this attack.

Amazon makes it exceptionally easy to purchase anything you want in just a few minutes. From textbooks for school to live ladybugs, its more surprising when you can't have something delivered to your doorstep in a few day's time.

No one ever wants to experience pain, whether it's as small as a stubbed toe or as great as recovering from surgery. Yet so much of our lives causes pain, lasting or brief in its form. With a few mental tricks and unusual home remedies, you can relieve some of the most common aches and ailments that arise painlessly.

If you've ever wiped your computer without having a proper backup of your operating system, or just wanted to cause some havoc online, chances are you've had to rely on Linux to help you out, specifically the Ubuntu distro.

Willpower is a pretty significant word. It's the difference between sticking with a clean eating diet and diving face-first into a plate of brownies. It's what drags you out of bed on Monday mornings and into work rather than letting you stay snuggled under the covers asleep. And, most importantly, it's the kick in the butt we all require to both accomplish goals and make changes.