Nmap is more powerful than you know. With a few scripts, we can extend its functionality beyond a simple port scanner and start to identify details about target servers sysadmins don't want us to know.

Reconnaissance is the phase of an attack where a red team or hacker designs a strategy based on the information they can learn about the target, as well as what the available attack surface looks like. These scans can take time to discover relationships, but Raccoon OSINT scanner coordinates multiple automated scans to produce invasively detailed reports on a target with a single command.

There are nearly 100,000 unique onion service addresses online with over two million people using Tor every single day. Join me as I explore a small fraction of what the Tor network has to offer.

Hackers rely on good data to be able to pull off an attack, and reconnaissance is the stage of the hack in which they must learn as much as they can to devise a plan of action. Technical details are a critical component of this picture, and with OSINT tools like Maltego, a single domain name is everything you need to fingerprint the tech details of an organization from IP address to AS number.

Coinhive, a JavaScript cryptocurrency miner, was reportedly discovered on the BlackBerry Mobile website. It was placed there by hackers who exploited a vulnerability in the site's e-commerce software that allowed them to anonymously mine cryptocurrency every time the website was viewed. There's no doubt Coinhive, an innovative mining method, is being abused and exploited by hackers in the wild.
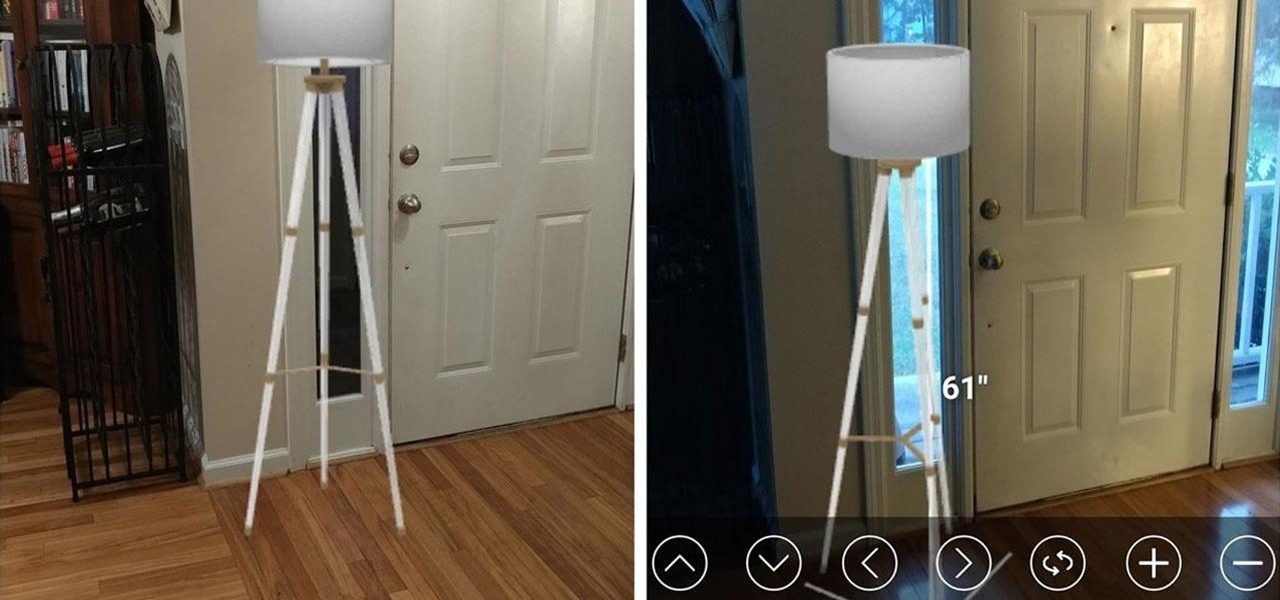
While some companies like IKEA and Lowe's zig towards ARKit to entice shoppers, Target has opted to zag to broader appeal with an augmented reality see-before-you-buy tool for its mobile website.

After laying off 40% of its staff this month to cut costs, SoundCloud appears to be struggling to stay afloat. While blog posts from the company have assured fans that the music platform is not in danger of shutting down, some people aren't so sure this is the truth. Internet Archive — a non-profit dedicated to preserving websites and services — announced today that they will be conducting a partial backup of SoundCloud to safeguard the site's content in case of closure.

The world of investment and finance can be labyrinthine in its very nature — and even more complicated in regards to augmented and mixed reality. While these new emergent technologies are teeming with explosive levels of unrealized potential, there's still a big layer of uncertainty in terms of return — but these investors aren't afraid to take the leap.

If you're tired of Google tracking you, but love how Chrome works, CyanogenMod has you covered. Their browser is called Gello, which is based off Chromium, Chrome's open-source counterpart. It's basically a souped-up version of Chrome—without all of the intrusive Google stuff. So if you're uncomfortable with Google displaying personalized ads based on your browsing history, or using your location to bring the "Physical Web" to your phone, you won't have to worry about any of that with Gello.

Star Wars season is definitely upon us. No matter where you turn, you can't go a day without being bombarded by merchandising and co-branding advertisements that attempt to draw a parallel between some character from a galaxy far, far away and a galactic cruiser like the Dodge Viper, or a midichlorian-laden power source like Duracell. Yep, it's kind of annoying, but at least we can get some fun out of it here and there.

Welcome back, my greenhorn hackers! Throughout this series on Metasploit, and in most of my hacking tutorials here on Null Byte that use Metasploit (there are many; type "metasploit" into the search bar and you will find dozens), I have focused primarily on just two types of modules: exploits and payloads. Remember, Metasploit has six types of modules:

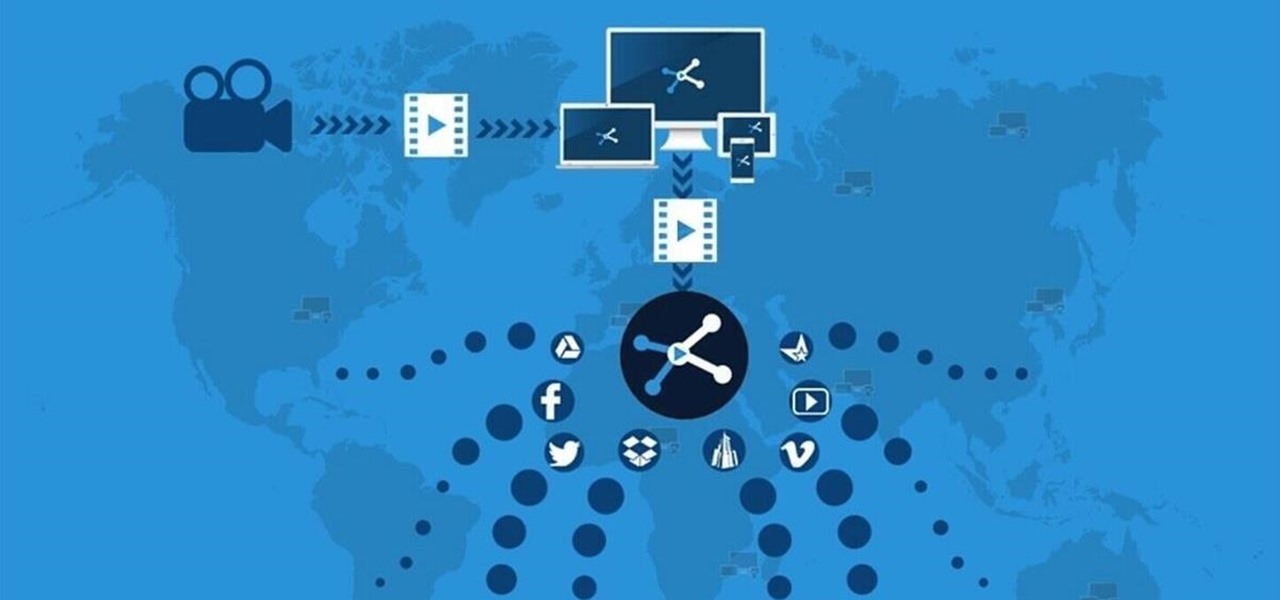
Are you tired of uploading videos to different sites separately? It's really time consuming and difficult. Finally, there is a way to upload and distribute your videos to YouTube, Facebook, Dailymotion, and many more video-hosting websites in one go. No need to upload to every site separately and one by one.

Do you remember the last time we used BeEF? Well, now we get to use it again, but this time with MITMf! We are going to auto-inject the hooking script into every webpage the victim visits!

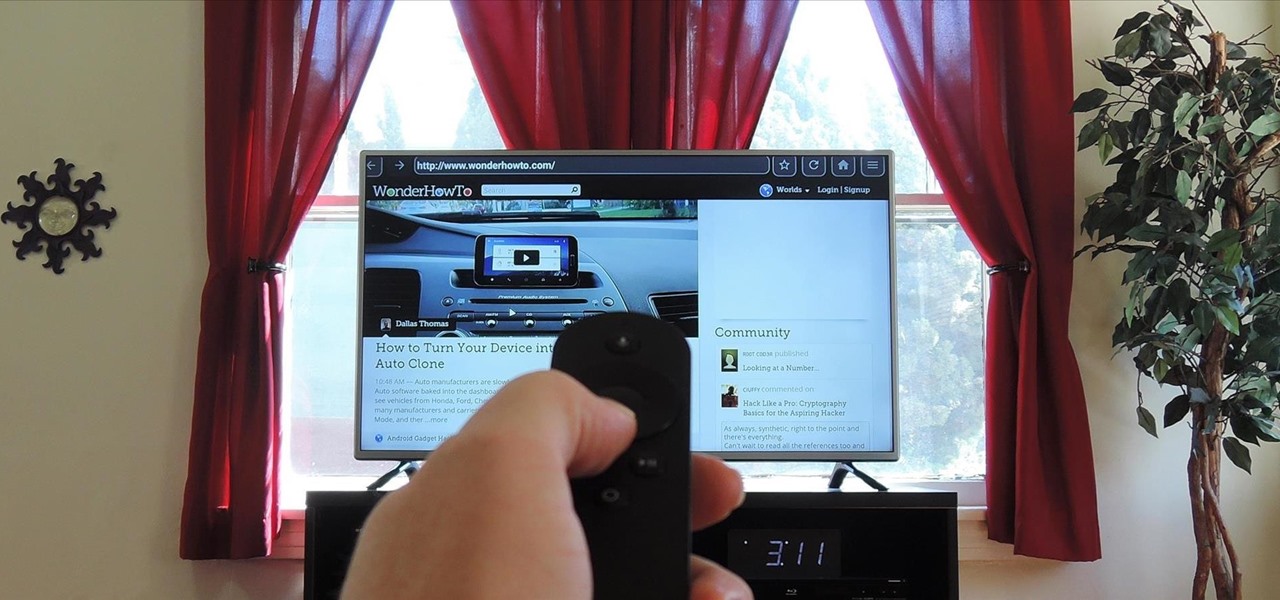
Since the Nexus Player is an Android device at heart, there are already several internet browsers that can be used on the streaming set-top box. Chrome, Firefox, and a few others will run perfectly fine, but the trouble with these is that you need a mouse to use them.

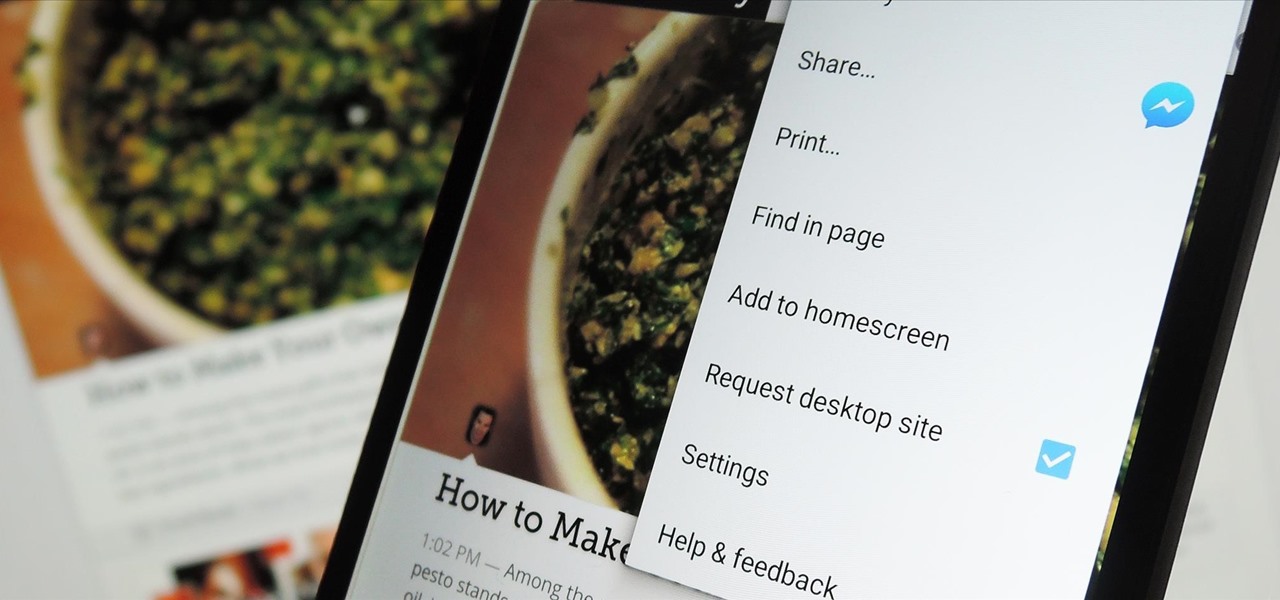
The majority of Android web browsers carry a "desktop mode" feature that makes mobile websites look like normal computer versions. Mobile versions are designed to work faster and more efficiently on smartphones, but sometimes the desktop version looks better on large displays or has additional features not included in the mobile one.

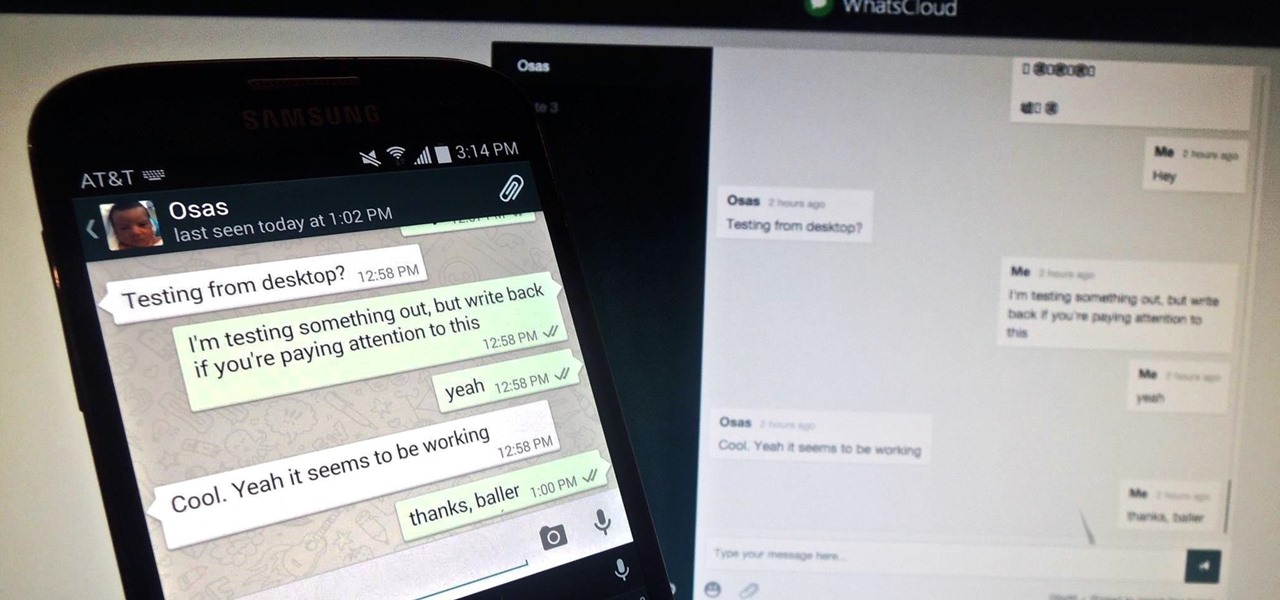
Pretty much my only gripe with computer-side messaging clients like Mighty Text is that they don't allow you to send and receive messages shared through WhatsApp, the popular third-party messaging application, which was purchased earlier this year for $19 billion by Facebook.

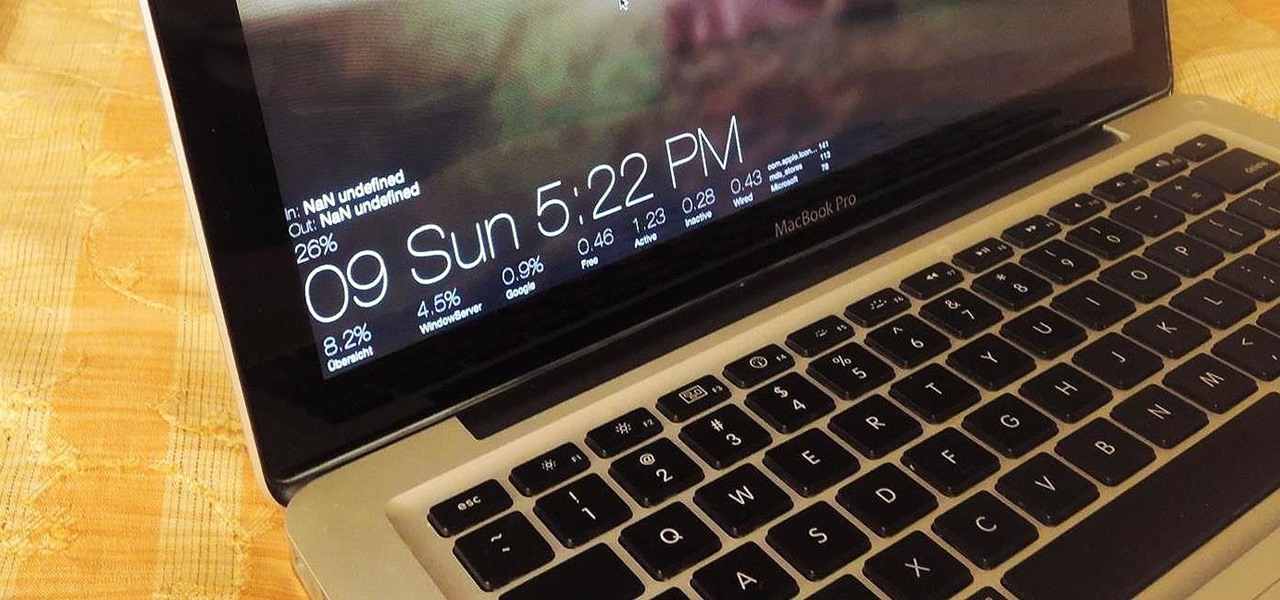
Apple hasn't been the most avid supporter of widgets over the years. Yes, they added them to the Notification Center in Yosemite, but that requires a drawer to be opened and closed whenever you want to check them. In my search for a better solution, I came across Ubersicht by developer Felix Hageloh.

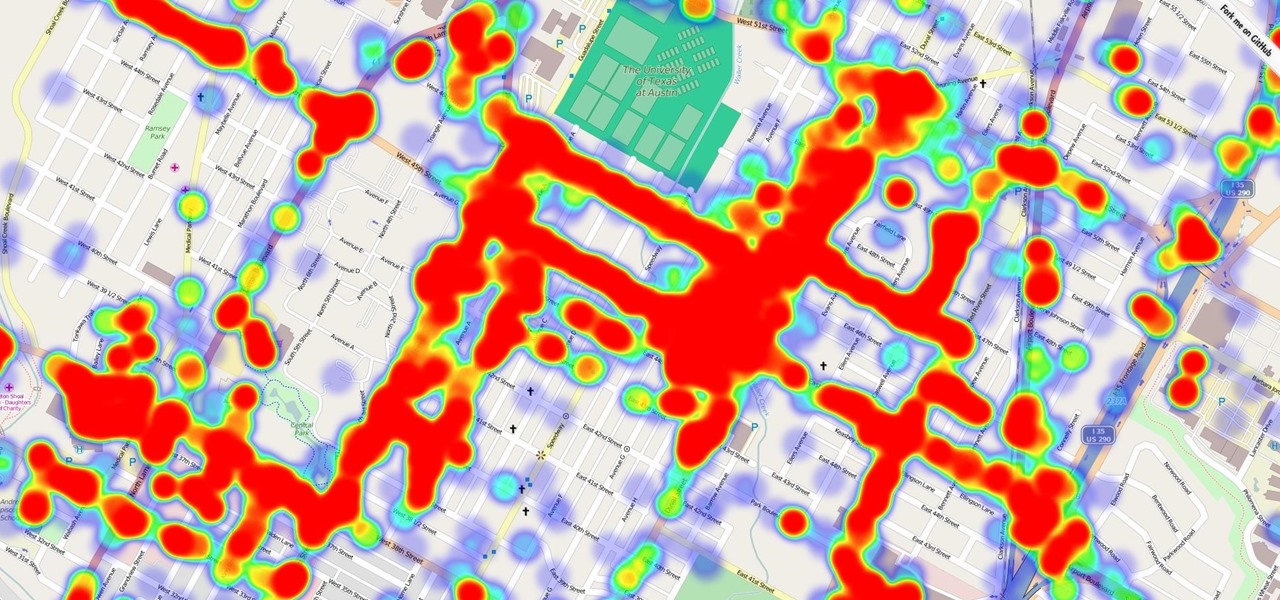
With an Android device left at its default settings, your location history is automatically recorded. You can view and manage this data, but the simple interface of points plotted on a map leaves a lot to be desired.

You may not always be connected to the internet, but if you're anything like me, your thirst for web content is insatiable. Whether you're on an airplane or stuck in an area with no reception, having some offline content stored on your Nexus can definitely save the day.

Welcome back, my novice hackers! Most of my tutorials up until this point have addressed how to exploit a target assuming that we already know some basic information about their system. These include their IP address, operating system, open ports, services running, and so on.

So many times, you turn on your computer, you open your front door, or you sit down on the couch to watch some well-earned TV, when you think -- Gosh! If only I could do this or this, life could be so much easier! And then, if you were a boring person, you would slouch even further down on the couch and continue to watch those reruns of The Sopranos.

Do you want to sell your car? It's important to make sure that you have everything in place before you hand off your car. Do your research, and everything will fall in place. Watch this video to learn how to cancel your license tags when you sell your car.

Check out this video tutorial on Blender. You'll see how to successfully create a modeled skull in Blender.

QR codes allow you to quickly and easily store and retrieve data within a single image. Much like barcodes at grocery stores, QR codes are images that can be scanned to discover data, such as an online website URL. Additionally, they can also be created by inputting text data into a QR code generator. Try scanning some of the QR codes in this video with an app on your phone or tablet to see how they work!

Blitzcrank is a steam golem champion with electrical abilities in League of Legends. His most unique ability is Rocket Grab, an ability that allows him to reach out and grab his enemies to bring them in close to a tower or for a kill. Learn how to abuse Blitzcrank's rocket grab and his other abilities to gank lanes and win games with this champion spotlight from Riot Games.

Found a video on YouTube that's perfect for your Keynote presentation? It's easy to embed YouTube clips on websites, but how can you successfully insert them into something like a Keynote project? It's actually quite easy! This video, just over a minute long, shows you the basic process behind downloading and re uploading your chosen video. Make sure that you append the .flv file extension to your downloaded fire, and also take care that you have the right to use what you're incorporating.

Gwyneth Paltrow is well known as an Oscar-winning actress and mother of two kids, Apple and Moses. But the film industry isn't the only one in which she excels. Paltrow started a healthy living and eating website called Goop a few years back, and she's a very talented chef.

If you're anything like the rest of the world, then you're glued to the computer. It's almost impossible to get away from using the computer at work, and once you get home how do you unwind? By checking your favorite blogs and websites on the computer.

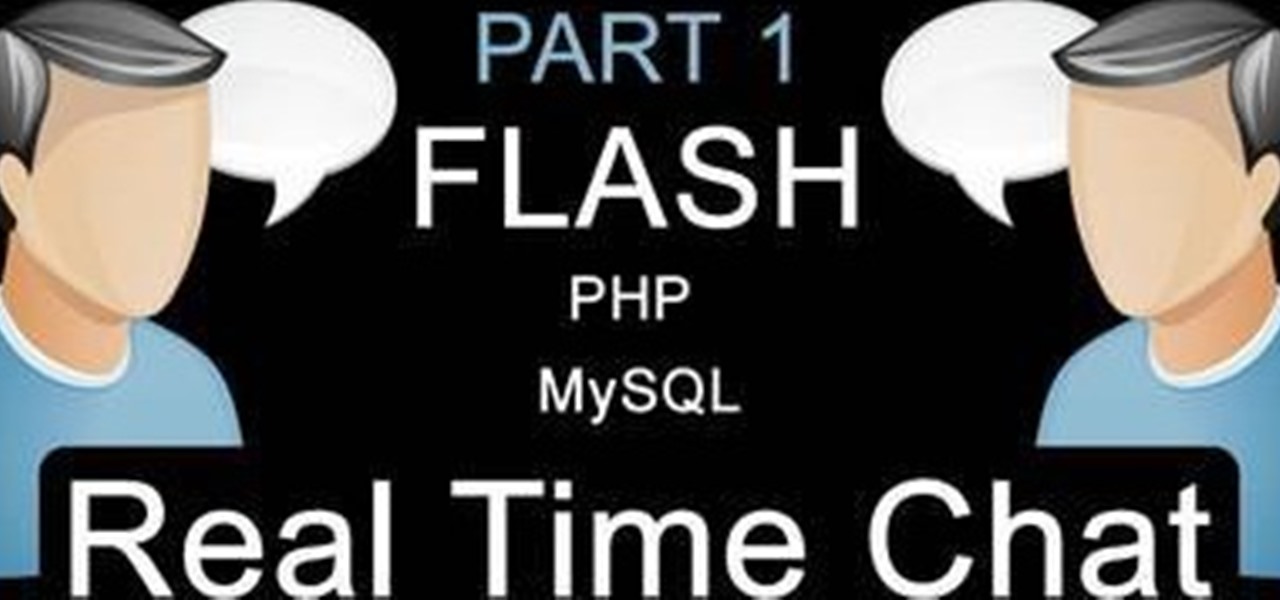
Add a chat program to your website and allow the logged in users to talk to each other! You can write this program using Adobe Flash CS3, PHP and MySQL. This tutorial shows you how to write your own Flash chat program incorporating all three systems.

We've all seen this warning message at one time or another while playing around on the internet in the Mozilla Firefox web browser:

Urban Decay has a nasty habit of releasing highly anticipated makeup palettes in very limited quantities so they sell like hotcakes. Their most recent palette, NAKED, sold out in seconds on their website, but if you were one of the lucky ones to snatch one of these up, then this tutorial will teach you how to create a smokin' hot look using the palette.

If you're getting bored of the same old same old in your e-mail messages, or if you're looking for an easier way to show off each of your social networking, as well as personal websites, then you will be happy to hear that Gmail has finally introduced rich text signature lines that'll allow you to hyper-link your images in your signature via HTML. All this can be found in the Labs section of your settings in Gmail. In this video you will learn how to set up the signature with the images and h...

In this clip, learn how to create lightbox galleries for images posted to your WordPress blog. Every version of WordPress brings with it new features, new functions and new ways of doing things. Fortunately, the very same technology that allows an open-source blog publishing application like WordPress to exist in the first place also makes it easy for its users to share information about the abovesaid things through videos like this one. Take a look.

If you have an Android-based cell phone and want to tether it to your MacBook, MacBook Pro, or other computer running Mac OS X software, the secret lies in a little application called PdaNet.

Urban Decay's new makeup palette, Naked, sold out within minutes of debuting on Sephora and on Urban Decay's website. Why? Well, with eight universally flattering neutrals and four gunmetal gray shades, you can either do a very neutral, daytime look for work or amp up the glam factor with the smokey gray colors for night.

In this tutorial, we learn how to set up a group on Facebook. First, log into your Facebook, then click on "groups", then click "create a new group". Now, give your group a name, description, news, email address, and contact information. When finished, click on "create group". Now you will be able to customized your group by adding images. Once you do this, you can add a website and change your different options. Allow only instructors to upload photos, because students may decide to upload i...

In this tutorial, we learn how to download mathematical applets using Wolfram Alpha. First, go to the website Wolfram Demonstrations. Once on this site, use the search bar to type in whatever topic you are interested in, and press enter. After this, you can scroll through and see several different applets. Next, you can click "watch web preview" to get a brief idea of what the applet does. When you find one you like, download the Mathematica Player, which you will only have to download once. ...

In this video tutorial, viewers learn how to use Flickr photos in their screen-saver. This task can only be done on the Windows computer. Users will need to download the program from the website provided in the video. Once downloaded and installed, there is an option in the Screen Saver Settings. Users are able to take photos from specific users or groups, or can search through tags and contacts. Further options include selecting the size of the photo and delay between switching the photos. U...

In this tutorial, we learn how to use salty hashes to keep passwords secure. A hash is stored in a database that is hashed with an algorithm, so not everyone can see exactly what your password is. When you type your password into a website, it doesn't actually register as words, it registers as a hash. This keeps your passwords secure so not everyone can see them. Salting is when you use random pits and attaching them to your regular hashes so not every password is the same. The salt is what ...

In this video, we learn how to find your Windows product key. Start off by going to Magical Jellybean Keyfinder. This website has a download that will find your product key for your Windows program. This is a great and necessary tool if you happened to loose the product key that came with your computer. This is also great for computers that already had Windows installed, and you never had the product key in the first place. Once you install this on your computer, you just open it up on your d...