This guitar lesson demonstrates how to play the recorder/keyboard intro to Stairway to Heaven as I have transcribed it on guitar. Tabs for this lesson are available on my guitar lesson website, on the "NEW STAIRWAY TO HEAVEN VIDEO" link:

This tutorial demonstrates how to create message boxes for a website using Adobe Dreamweaver.
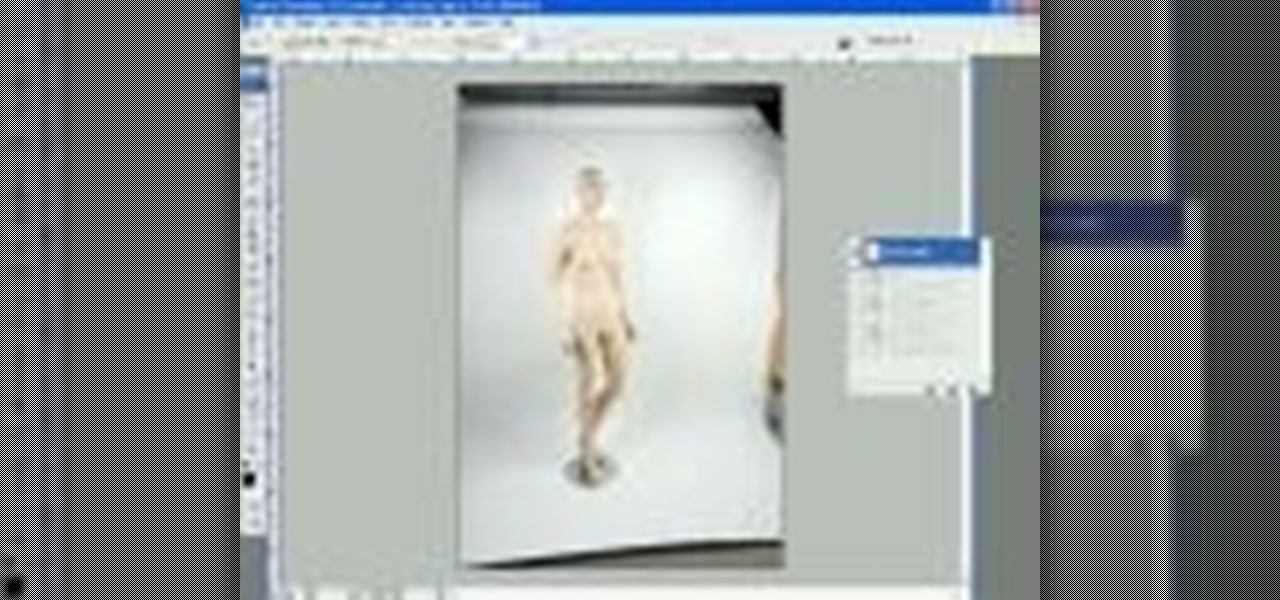
Another NewDarkRoom.com Video tutorial. This tutorial will show you how to get more room out of your photo booth by hiding all the unwanted parts past your seamless paper. As usual you will be able to find a more detailed larger video at our website.

If you're putting your email address online on your own website, or sites like facebook or myspace, you may want to be a bit clever about it. Check out this tutorial and see how to protect your email address from spam.

Django is a Python web framework used for rapid application development in any environment. In under 10 minutes, you can go from a bare Linux (Ubuntu) installation to a fully functional Django server.
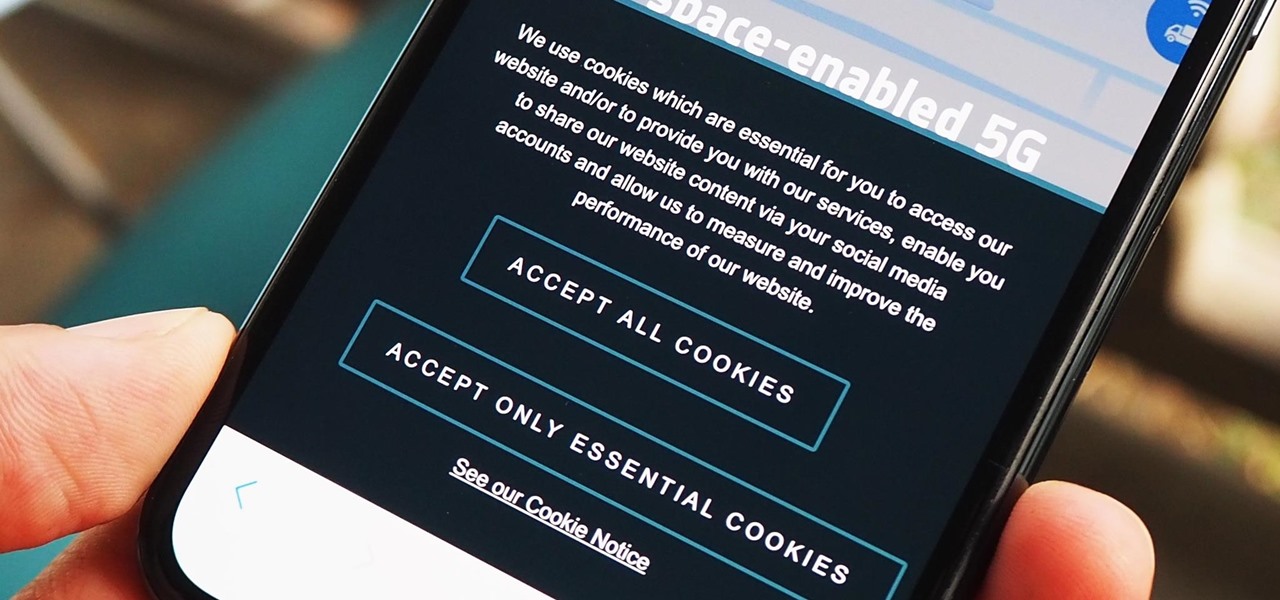
As a means to combat annoying and intrusive advertisements in Safari, Apple added native support for content blockers on the iPhone. Instead of being bombarded by notifications, banners, and pop-ups, content blockers prevent them from opening, which can also be said about those annoying cookie consent notices that many websites now have.

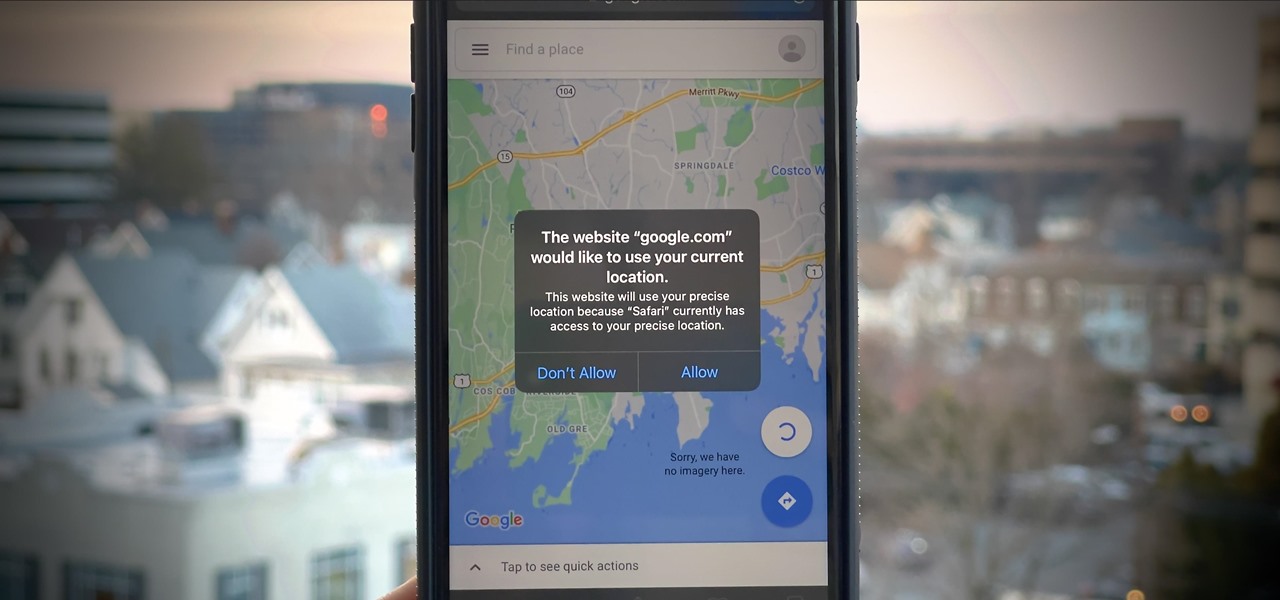
If you surf the web on your iPhone, you no doubt run into this problem all the time: a website wants your location. It can happen when performing a location-based task, such as using a store locator, or whenever a web app just wants to deliver better ads or local recommendations. If you're tired of allowing or denying permission each time, there's an easy way to stop the annoying security pop-ups.

Whether you want to build your own website for your business, start your new lucrative career in web development, or gain a wealth of projects to add to your portfolio, this course will help you do it. And right now, "The Complete Web Developer Course" is on sale for just $14.99 — a staggering 92% discount off the regular price of $199.

No website, service, or platform is immune to being abused or exploited by hackers, and Google Analytics is no exception. To better understand how Google Analytics can help deliver payloads and bypass security protocols, one might want to learn how to use Google Analytics from a user's perspective first.

On March 13, President Trump announced during a briefing in the Rose Garden that Google was building a COVID-19 screening website to help Americans understand if they might have the new coronavirus. If likely infected, the site would also include the location of a local drive-through testing site to visit. So how can you access the screening website?

It's pretty much a given at this point that Facebook has a lot of data on us. While you might be conscious of the data you share with Facebook when you post, upload photos, or chat with friends on Messenger, you might not be thinking about all the data it receives from websites and apps you use outside the social media giant. Now, you can actually do something about it.

Your social security number, credit card information, and medical history can fall into the wrong hands if you're not careful about how and where you share your data online. If you really care about your data, there are tools and techniques you can utilize to protect yourself from cyberstalkers, advertisers, and hackers in a time when digital lives are a high commodity.

Nmap is more powerful than you know. With a few scripts, we can extend its functionality beyond a simple port scanner and start to identify details about target servers sysadmins don't want us to know.

Reconnaissance is the phase of an attack where a red team or hacker designs a strategy based on the information they can learn about the target, as well as what the available attack surface looks like. These scans can take time to discover relationships, but Raccoon OSINT scanner coordinates multiple automated scans to produce invasively detailed reports on a target with a single command.

A convincing domain name is critical to the success of any phishing attack. With a single Python script, it's possible to find hundreds of available phishing domains and even identify phishing websites deployed by other hackers for purposes such as stealing user credentials.

Identifying vulnerable devices and services on a target router can be difficult without leaving logs and other traces of an active attacker on the network. However, there is a way to covertly decrypt and view Wi-Fi activity without ever connecting to the wireless network.

Tossing an old Android smartphone with a decent battery into your hacking kit can let you quickly map hundreds of vulnerable networks in your area just by walking or driving by them. The practice of wardriving uses a Wi-Fi network card and GPS receiver to stealthily discover and record the location and settings of any nearby routers, and your phone allows you to easily discover those with security issues.

The biggest corporation we know today is called Google, I bet you've heard of it yeah? How Google Tracks You:
Have you ever used an open wifi, which after you connect displays a website to enter your credentials to get internet? That website is called captive portal and widely used in airports, hotels, universities etc. Have you ever wondered what would happen if someone would set up an open wifi with the same name displaying a very similar web page asking for credentials? Usually if there are multiple wifi networks with the same name and encryption, devices only display the one with the highest sign...

Welcome back, my fledgling hackers! Over the years, we have examined multiple ways to own, exploit, or compromise a system. On the other hand, we have not spent a lot of time on denial-of-service (DoS) attacks.

NOTICE: Ciuffy will be answering questions related to my articles on my behalf as I am very busy. Hope You Have Fun !!!

People who know that I am a professional hacker often ask me what they can do to make their computers and personal information safe from people like me. The answer, of course, is that nothing will make you completely safe, but there are a number of measures any computer user can take to reduce the chances of being a victim of a hacker.

so i have just signed up to this, and i dont know much about this website but i wanted to show my recent upload

Custom Timelines (CTs) allow you to control exactly which Tweets appear in a column on Tweetdeck. So if a particular event catches your eye as newsworthy you can tailor your CT to show what you consider to be the most relevant Tweets. These CTs can then be customized, shared and embedded on your website. This is a great way of increasing interaction on Twitter and sharing current, interesting and breaking news stories from any niche or subject

Apple's new iOS 8 has a ton of new features, and so does their revamped Safari app, only some of the features aren't quite as obvious as others. In this guide, I'll show you my 5 favorite Safari secrets in iOS 8 for your iPad, iPhone, or iPod touch.

Welcome back, my greenhorn hackers! My preference for Linux as a hacking platform is well documented, and I have even created a series of tutorials to train new hackers. Without being proficient in Linux, you can't really call yourself a hacker.

I rarely receive spam mail, but every now and then I’ll get an email from Cat Fancy Magazine. I’ve never read an issue of Cat Fancy Magazine or been to their website. Actually, I’m allergic to cats. So how did they manage to get my information?

How to Henna Your Hair Tutorial Pt.2 Please Dont forget to Watch Pt. 1

Video: . How to Henna Your Hair Tutorial #1

Need to clear you cache? This guide details how on any web browser (Chrome, Internet Explorer, Firefox, Opera, Safari, Internet, and Dolphin) for any platform (Windows, Mac OS X, iOS, and Android). What Is the Cache Exactly?

Very interesting interview with the editors of the New York Times Lens Blog, a website which is totally dedicated to photojournalism and videojournalism.

Learning how to use other text panels in the designs gallery. This website design tutorial will teach you how to add a note panel, numbered panel and one additional text panel.

This web design Tutorial will walk you through process of linking to files on your computer. You can link file types including but not limited to Microsoft Word, PowerPoint, PDF, Videos and so on for download on your website.

In this web design tutorial we will show you how to protect yourself from losing your work just in case the program malfunctions, computer crashes or you accidentally forget to save document and so on. I highly recommend you utilize this Web Design Tutorial especially if you are working on large websites for clients.

This Professional Website design Tutorial will show you how to place text on a curve using the line tool. However you can put text on the outline of shapes and other objects.

In this web design tutorial learn how to repel text around objects. This Professional website design tutorial will also explain why it is important to have the objects in proper order for the repel function to work properly.

In this Web Design Tutorial you learn how to convert the mouseover state into a navigation menu. Once the navigation menu is created you will be able to use the navigation bar properties to make additional modifications to your website menu.

In this web design tutorial you will learn how to manage web design layers efficiently by using solo mode, hiding layers and locking layers. This Xara Web Designer tutorial will show you the importance of using these features to manage your website design.

In this video we're making a weather predicting light! Good luck! Video: .

Every year, Black Friday gets a little more insane. People get up at ungodly hours, wait in lines forever, and get into some of the most ridiculous fights you've ever seen. All in the name of saving some cash. Everyone loves saving money, but without a game plan, you could end up missing all the good deals and going home with nothing. Luckily, the Internet is here to take some of the stress out of holiday shopping. With these sites and apps, you can find out about all the best deals before yo...