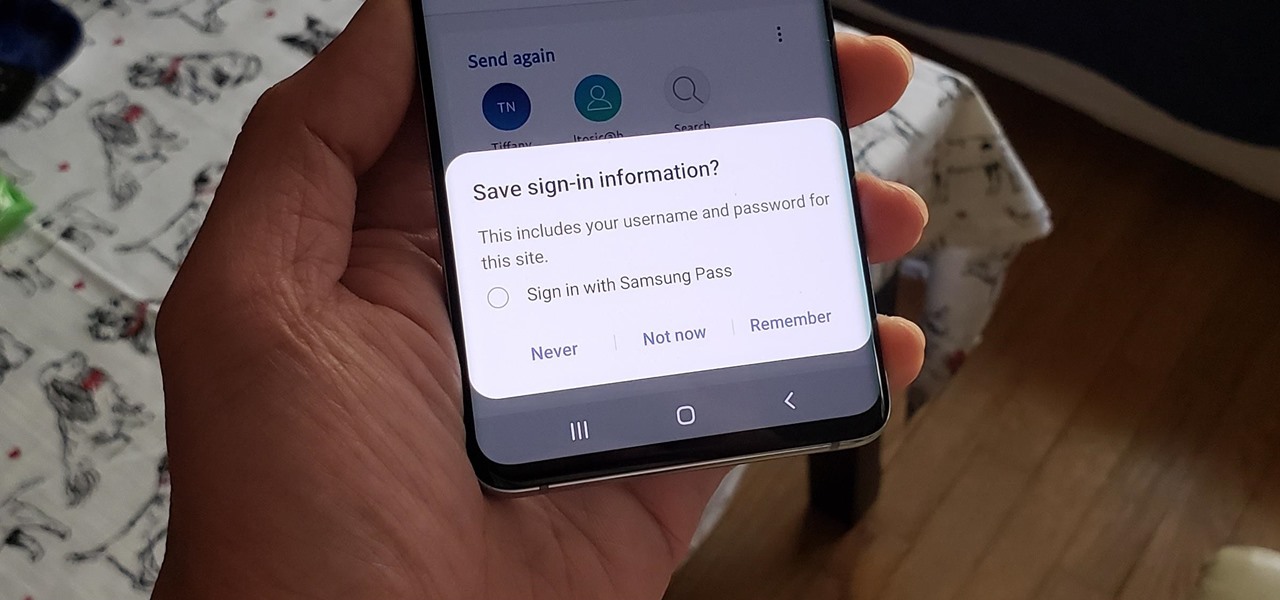
If you use Google Chrome on your computer, you've undoubtedly saved a ton of passwords since the browser always prompts you to. But Samsung uses their own password service on their phones by default, so you'll have to change a setting if you want to use your Chrome passwords to log into apps and sites on your Galaxy.
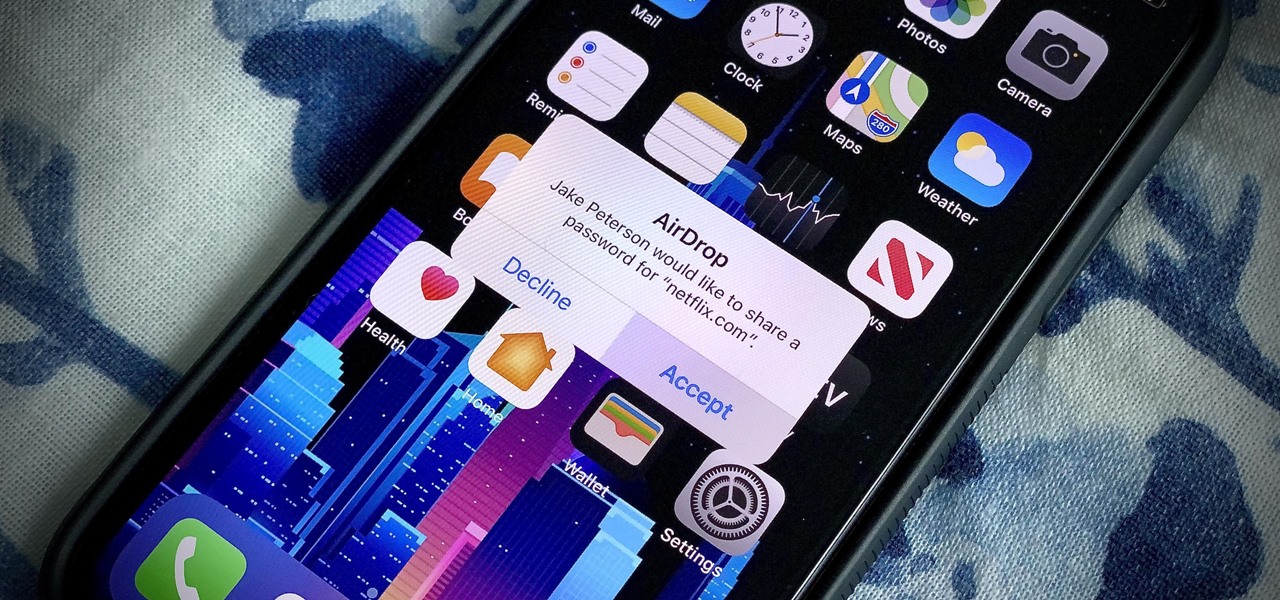
In iOS 11, Apple made it easier for you to share passwords with friends. Back then, it was just Wi-Fi passwords, which made sense. "What's the Wi-Fi?" gets old after a while. But now, whether you're running iOS 12 or 13, you can share any password you want with any iPhone around, all with one of iOS' best features: AirDrop.

Correctly identifying the underlying technologies that run on a website gives pentesters a considerable advantage when preparing an attack. Whether you're testing out the defenses of a large corporation or playing the latest CTF, figuring out what technologies a site uses is a crucial pen-tester skill.
Chrome has just introduced some new UI elements for web exploration. The new URL bar is not intuitive. But once you get to grips with it, you will be so much more efficient in your address bar editing, pasting, and navigation.

We know that Microsoft's HoloLens 2 is due to start shipping later this year, but despite the trickle of news about the device, we still don't know when.

One of the best ways to dig into a website and look for vulnerabilities is by using a proxy. By routing traffic through a proxy like Burp Suite, you can discover hidden flaws quickly, but sometimes it's a pain to turn it on and off manually. Luckily, there is a browser add-on called FoxyProxy that automates this process with a single click of a button.

Gathering information on an online target can be a time-consuming activity, especially if you only need specific pieces of information about a target with a lot of subdomains. We can use a web crawler designed for OSINT called Photon to do the heavy lifting, sifting through URLs on our behalf to retrieve information of value to a hacker.

ARP spoofing is an attack against an Ethernet or Wi-Fi network to get between the router and the target user. In an ARP-spoofing attack, messages meant for the target are sent to the attacker instead, allowing the attacker to spy on, deny service to, or man-in-the-middle a target. One of the most popular tools for performing this attack is Ettercap, which comes preinstalled on Kali Linux.

Outside of a few headlining features, Apple focused on polishing things up in iOS 12. Instead of revamping functionality left and right and running the risk of releasing a buggy mess like iOS 11, this year's feature additions are smaller. Case in point, you can now show favicons in Safari — nothing groundbreaking, but a nice touch.

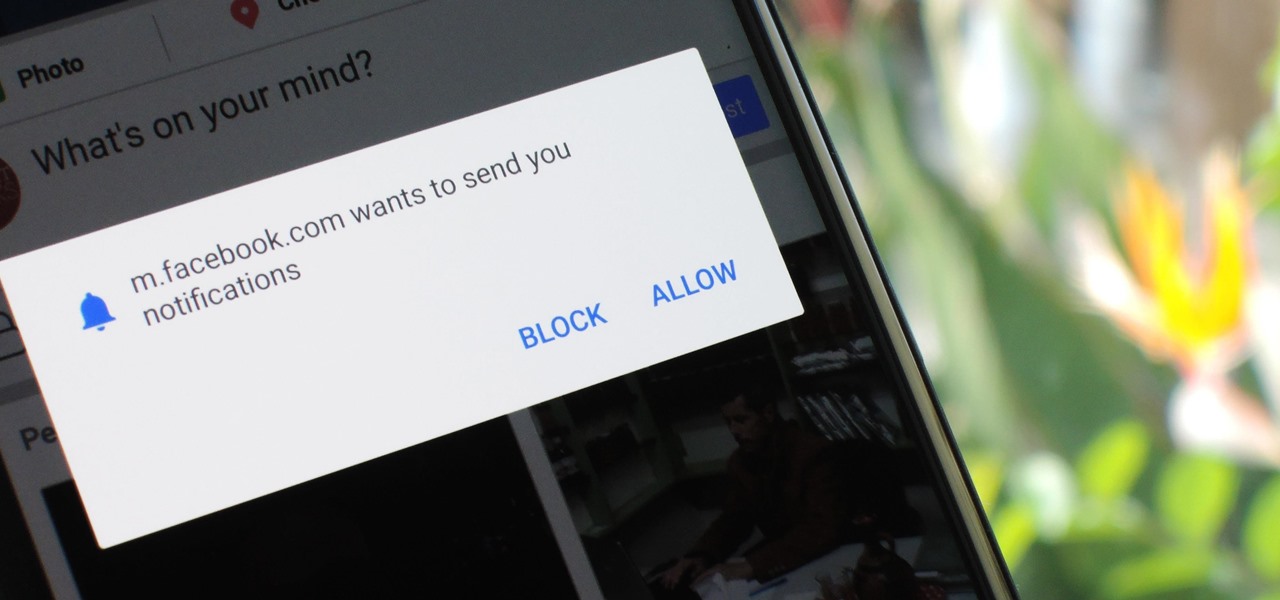
As the go-to browser for millions worldwide, Chrome makes web surfing a breeze with its simple interface and Google integration. But many websites are starting to ask if they can send you notifications, and this can interrupt your browsing. Thankfully, you can completely disable these prompts if you prefer.

Conducting phishing campaigns and hosting Metasploit sessions from a trusted VPS is important to any professional security researcher, pentester, or white hat hacker. However, the options are quite limited since most providers have zero-tolerance policies for any kind of hacking, good or bad. After researching dozens of products, we came out with 5 potentials that are ideal for Null Byte readers.

Earlier this week, Snapchat announced a partnership with NBCUniversal regarding the 2018 Winter Olympic Games in South Korea. Starting on February 10, Snapchat will be streaming a feed of NBC's live broadcast of the Olympics in Pyeongchang.

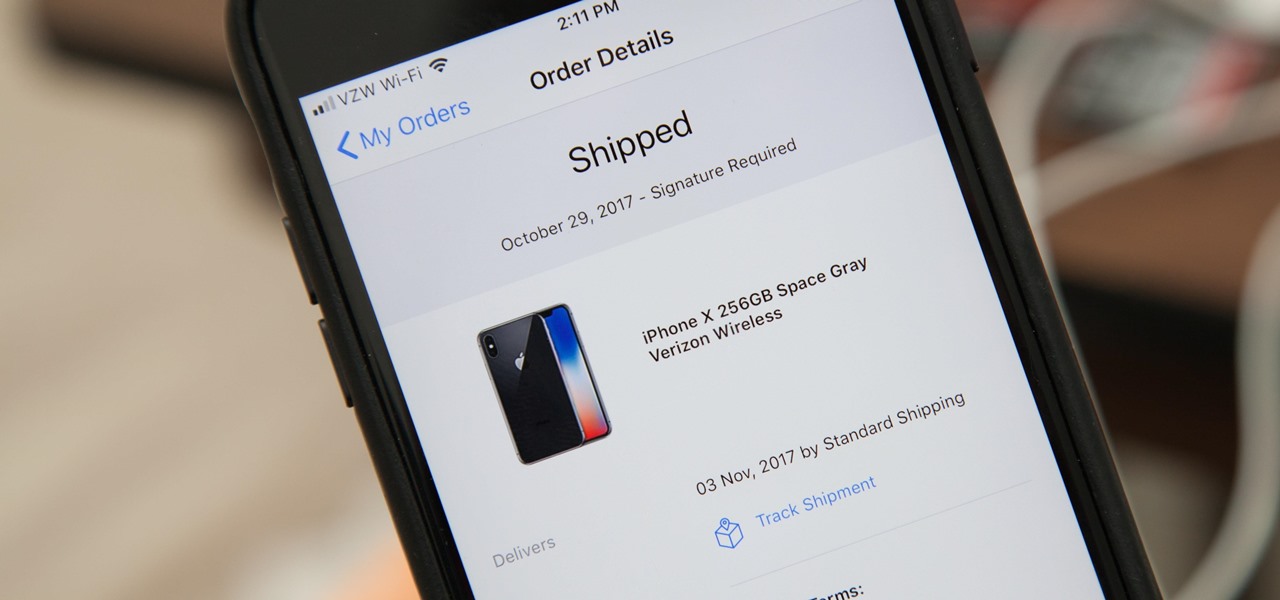
Current shipping estimates for the iPhone X are 5–6 weeks, but is there a chance you'll get yours tomorrow?

Buyers can't wait for their Tesla Model 3 to be delivered. But with no clear arrival date in sight, buyers are starting to get a little antsy waiting to see what the Tesla Model 3 will look like up close. Luckily, Tesla accessories seller EVANNEX partnered with technology firm Kinetic Vision to try and satisfy buyers for a while by creating an app that lets you view an augmented reality Tesla Model 3 that's nearly life sized.

Two salsa dancers who also happen to be programmers are soon releasing an app called Dance Reality, made with Apple's ARKit. Through this app, you will be able to practice your dancing with augmented reality as your teacher right from your iPhone.

Throughout this NR50 series, we have talked about the incredible growth the augmented and mixed reality space has seen in the last year. More devices, software, developers, and use-cases seem to arrive daily. For this growth to have occurred, it took the work of many people, from many different backgrounds and skill sets — and Next Reality wants to recognize them for all that they have done and are doing.

The producers of FX's animated series Archer have devised a plan to introduce augmented reality hijinks into its eighth and penultimate season with a new app for iOS and Android devices.

One of Android's biggest strengths is its ability to interact with other operating systems. When you plug your phone into your Windows PC, you instantly see all of the files it holds—and all it takes is a simple syncing app to do the same with Mac. To top that off, apps like Pushbullet and Join bridge the gap even further by allowing you to share links, files, and messages between all of your devices.

Welcome back, my novice hackers! As many of you know, recon is crucial to a successful hack/pentest. In most cases, hackers spend more time doing good reconnaissance than actually hacking. Without proper recon, you are simply guessing at what type of approach or exploit is going to work and, as a result, your time is wasted without any useful outcomes.

This Is for the Script Kiddies: This tutorial is about a script written for the How to Conduct a Simple Man-in-the-Middle Attack written by the one and only OTW.

Welcome back, my tenderfoot hackers! Web apps are often the best vector to an organization's server/database, an entry point to their entire internal network. By definition, the web app is designed to take an input from the user and send that input back to the server or database. In this way, the attacker can send their malicious input back to the servers and network if the web app is not properly secured.

Although they're often times the primary source of income for websites, on-site advertisements can annoy even the most tolerable reader. That's why ad blockers have been some of the most popular downloads on Firefox and Chrome for some time now, demonstrating that when it comes down to it, most people just want nothing to do with ads shoved in their face.

Many websites are crowded with ads, pictures, and other irrelevant content that make it harder than necessary to read a simple article on your iPhone. In many cases, you have to zoom in just to get a better view of the text you're attempting to read—unless the webpage blocks zooming.

In an attempt to remain a mobile-exclusive app, Instagram doesn't let users upload photos or videos from their computer. On the Instagram web app, you can pretty much only like and comment on items in your feed, but what about all of those photos on your computer that scream #tbt?

In a study attempting to observe virality in real time, two Microsoft engineers, Corom Thompson and Santosh Balasubramanian, used Microsoft's recently released Face detection API to create How-Old.net and track its usage in real time.

Hello Hackers! Welcome to my 2nd Post: This is a tutorial explaining how to hack android phones with Kali.

Welcome back, my budding hackers! This is the initial post of a new series on how to hack Facebook. It's important to note here that each hack I'll be covering is very specific. I have said it before, but I feel I need to repeat it again: there is NO SILVER BULLET that works under all circumstances. Obviously, the good folks at Facebook have taken precautions to make certain that their app is not hacked, but if we are creative, persistent, and ingenious, we can still get in.

Video: . This Video will Show you how to Stretch your Natural hair with no Heat. I love doing this Method it is just as good as blowing your hair out. It gives your hair length without putting heat to it.

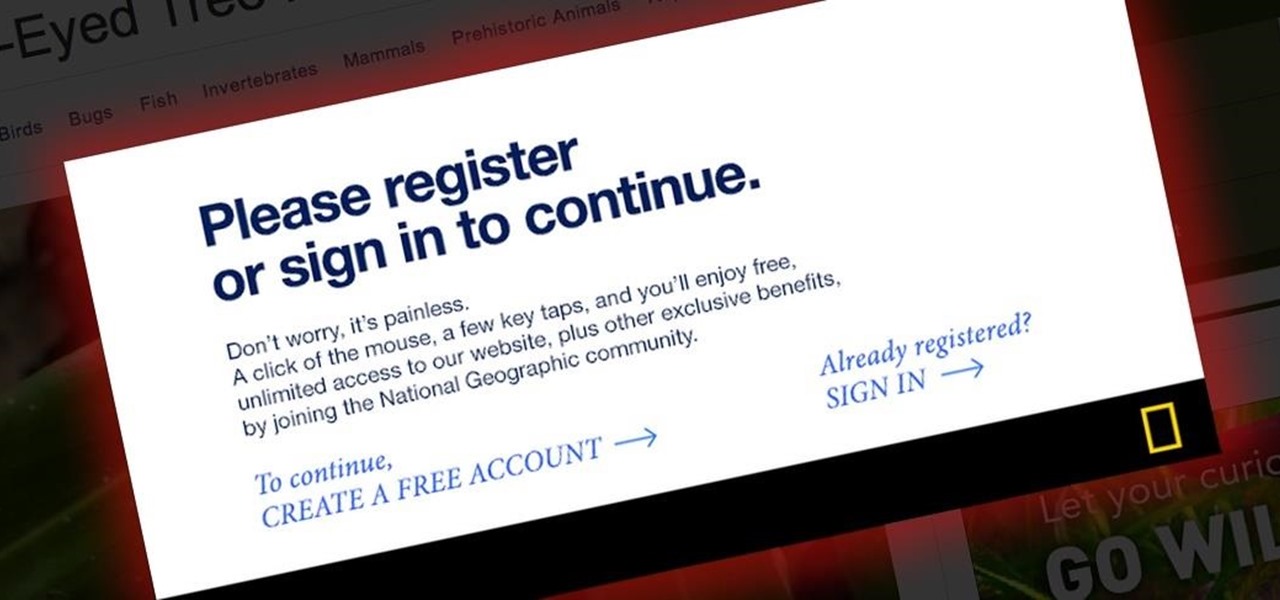
Last night, I was reading a riveting National Geographic article on the green-eyed tree frog, until I was quickly interrupted by an annoying popup asking me to "create a free account" or "sign in." Really, I'd like to do neither. I just want to read about tree frogs.

This time it's serious. Really. The largest web security vulnerability of all time went public on Monday, April 7th, 2014, resulting in widespread panic throughout the Internet as system administrators scrambled to secure their websites from the OpenSSL bug known as Heartbleed.

Do you have a passion that you would like to share with the world, but not sure how to do it. If so, that was my story too. I knew the niche I wanted to share, but I had no computer, video editing, website, or any other digital experience.

Welcome back, my greenhorn hackers! In a previous tutorial on hacking databases, I showed you how to find online databases and then how to enumerate the databases, tables, and columns. In this guide, we'll now exfiltrate, extract, remove—whatever term you prefer—the data from an online database.

You saw our post on the 18 coolest new features of iOS 7, but now that you've had a chance to play around with your updated iPhone, it's time to lock it down.

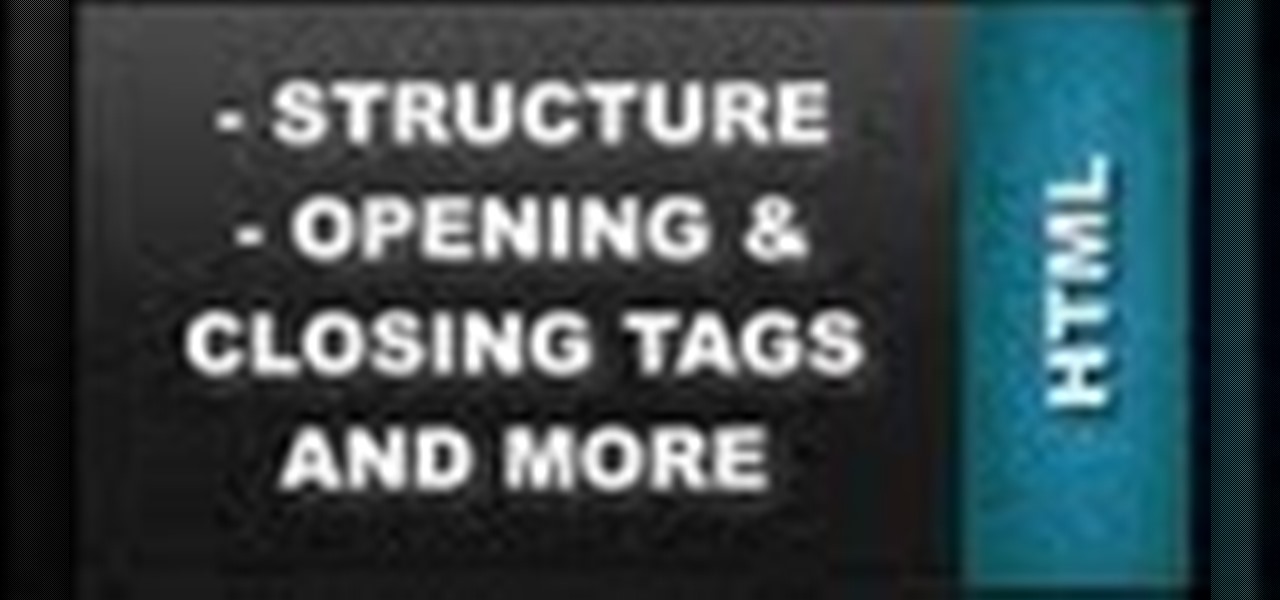
Learn how to setup up a basic structure for a HTML web design document, define the HTML version, open and close HTML tags and learn how to apply the proper file extensions when saving document in notepad. This web design tutorial is by no means a complete structure for HTML coding and is only a brief introduction to HTML web design. This video will only go over a brief introduction to the structure of an HTML document and in a future tutorial we will go over additional components that are nee...

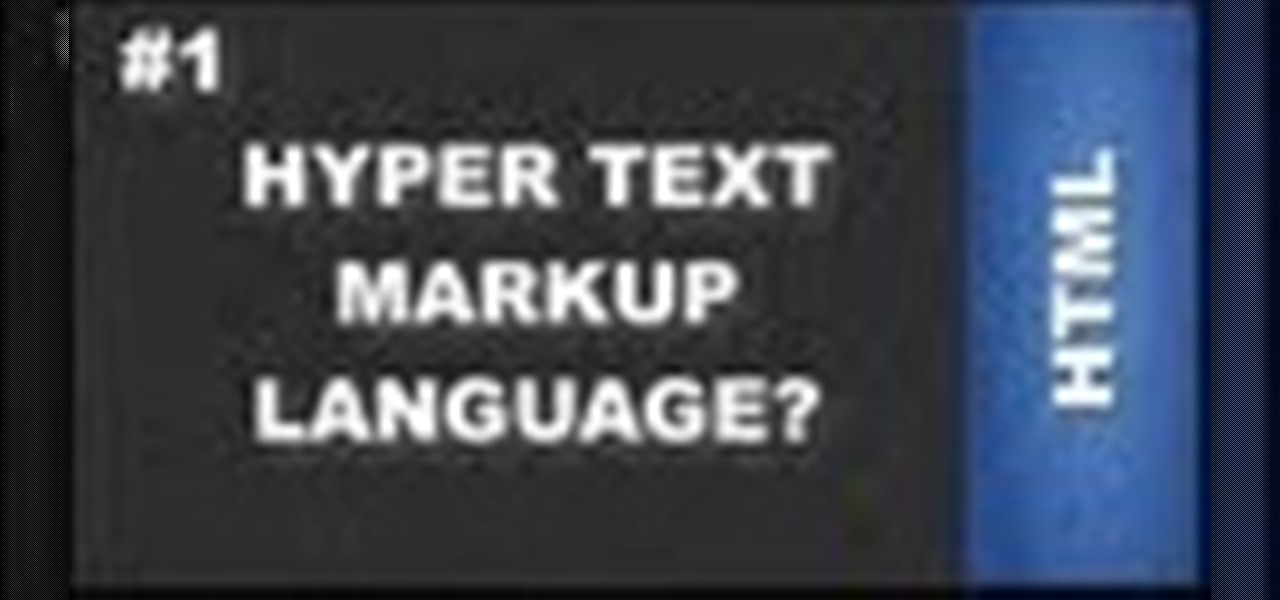
This HTML web design tutorial will explain what HTML is and how it can benefit you rather you are looking to build a website from the ground up or you are planning on using a combination of automated software and HTML Design and need the flexibility to still make fine tune edits to your website. From a simplistic view the primary purpose of HTML design is to interpret and display text based content in a given web browser. For example when you read articles online from places like wall-street ...

Newsletters, subscriptions, and receipts are all necessary evils that come along with online services and shopping, and they take up a significant amount of space in a lot of people's inboxes. If you've ever signed up for an account on a website, chances are you've gotten an email from them.

Every Windows system includes command prompt; and while a lot of people on Null Byte and WonderHowTo in general know how to use it, some people don't know anything about it, even how to access it.

Checking notifications from all of your social media accounts is half the fun of the Internet, but can become quite tedious—hopping from site to site can take up hours of your time, especially when you're running away from something (in my case, it was always homework/studying).

The lovely Kato of Steampunk Couture has gone hardcore. For those who prefer to exercise their imaginations a bit more, Voila! Veronique Chevalier in Gearhearts Steampunk Glamour Revue- click here should do... A recent kerfuffle unfolded on facebook's Steampunk Revolution group when a discussion was started by Steampunk R &D''s very own Austin Serkin on the subject of Kato's new foray into steampunk porn, which was, ahem, examined in detail. (Well, figuratively, not literally, since her websi...

In 2006, everything that revolved around my world shattered into tiny pieces as I learned that scientists had decided to rescind Pluto's planetary status. Given the ol' Jeff Probst treatment, Pluto was officially voted off our solar system in the blink of an eye, leaving us with only eight planets and a whole load of useless textbooks. The primary reason that Pluto was demoted down to a "dwarf planet" was due to Pluto's largest moon, Charon, being about half the size of Pluto; all the other p...