
How To: Get a career in affiliate marketing
Big business is on the web these days and you don't have to build a shopping website or blog to get involved.


Big business is on the web these days and you don't have to build a shopping website or blog to get involved.

There is a lot of stigma around prenuptial agreements but they can be a good chance to work on difficult issues as a couple and make sure you're on the same page. Prenuptial agreements don't have to be a horrible experience and can give a soon to be married couple some peace of mind.

You've boxed up and shipped all your other possessions for the big move and all you're left with is the little issue of how your getting your car there. There are companies out there that will ship your car to you, just make sure your car is prepped for the journey.

To hack into Google images follow the following steps. You will first need to open a new internet browser window and go to Google, then load their images website. Next type into the search bar your image query and press search. Once you have gotten your search results paste the following code into your address bar:

The Peace Corps -- have you ever thought of it? It crosses everybody's mind at one point or another, but mostly college students. The Peace Corps offers many benefits, like life experience, student loan repayment, and travel. If you are ready for 27 months of hard but rewarding work, a job with the Peace Corps might be for you. These steps will help you on your way toward an unforgettable experience.
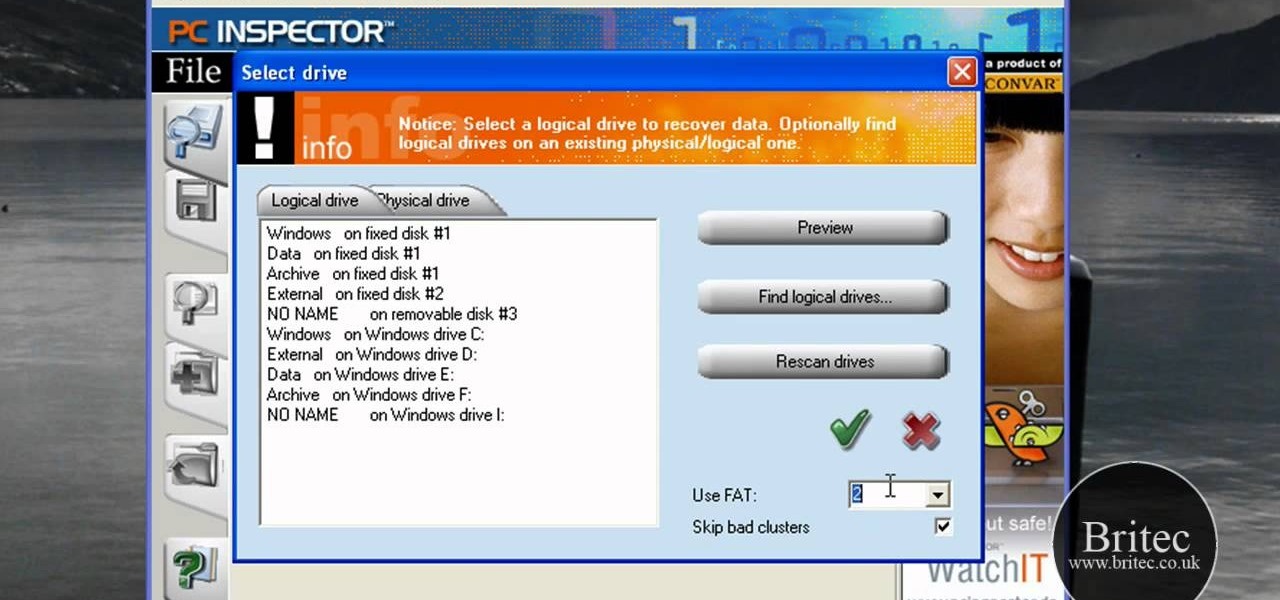
In this data recovery tutorial the instructor shows how to recover deleted files and lost data using a free software called PC Inspector. On your computer you may loose data sometimes due to a corrupted hard drive, or because you deleted it accidentally or some other reason. Now some times you will need to recover that important data and it will cost you hundreds of dollars to get it done outside by the professionals. Now you can avoid this and use a free software called PC inspector and reco...

This video explains how to send the Text message to any where specifically to mobile using Yahoo mail. To do that first type the "www.yahoo.com" or "www.yahoomail.com" in the browser. And then choose the Mail option from the front page of the yahoo website. From that click the sign in option, and give your Mail id and password in the yahoo sign in page now you will logged into your yahoo account. Into your account you will have the "New" menu option on left to corner. From that you have to ch...

Learn how to browse the Internet at work and get away with it. Load Excel (Any version will do). Click on the Data tab. Click 'Import External Data'. Click 'New Web Query'. Once the window has loaded, click through the prompts, selecting Yes. When the window has loaded completely, go to your favorite website in any browser you want. For this example, Twitter is used. Go to the RSS Feed and copy the link that appears at the top. Paste the link into Excel and click the Import button. Accept any...
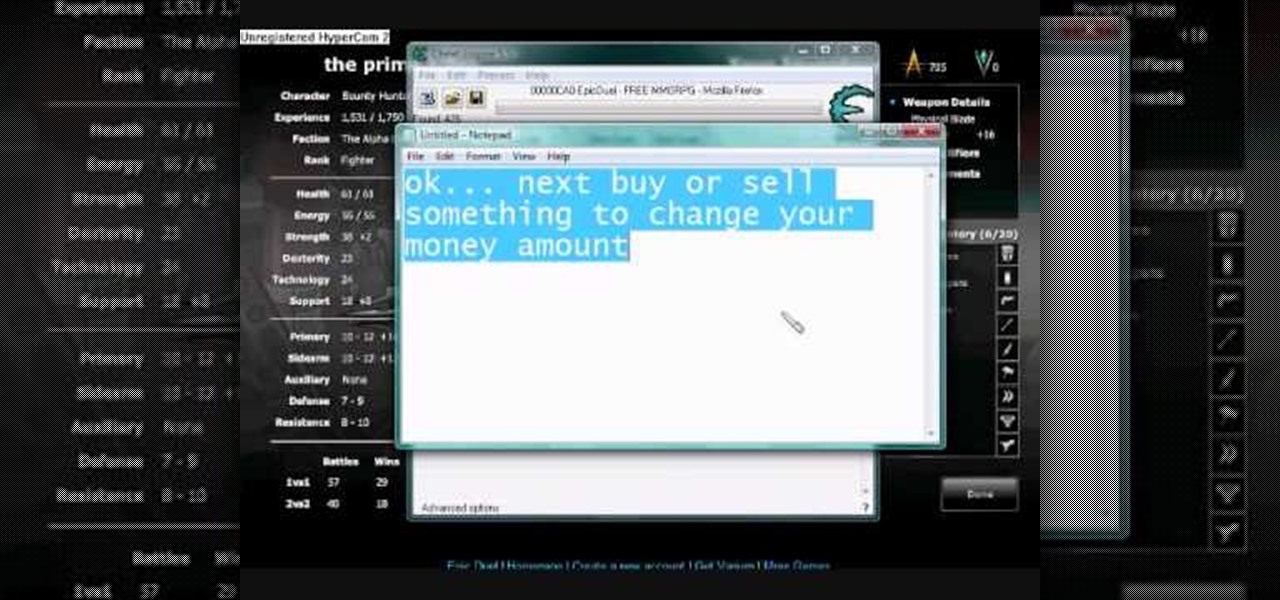
There's a great new web game called Epic Duel out on the internet, and everybody's playing it, but not everybody's hacking it, except you! Outshine them all with this EpicDuel cheat with Cheat Engine 5.5.

Internal linking is a valuable way to improve search engine optimization on your website or blog. This component of organic search engine optimization we going to focus on web copy threading.

Hacking seems like the only solution to today's flash-based games, like Club Penguin. If you can't do it yourself, let a cheating program do it for you. That's the new fad. Cheat Engine. That's all you need to hack online games.
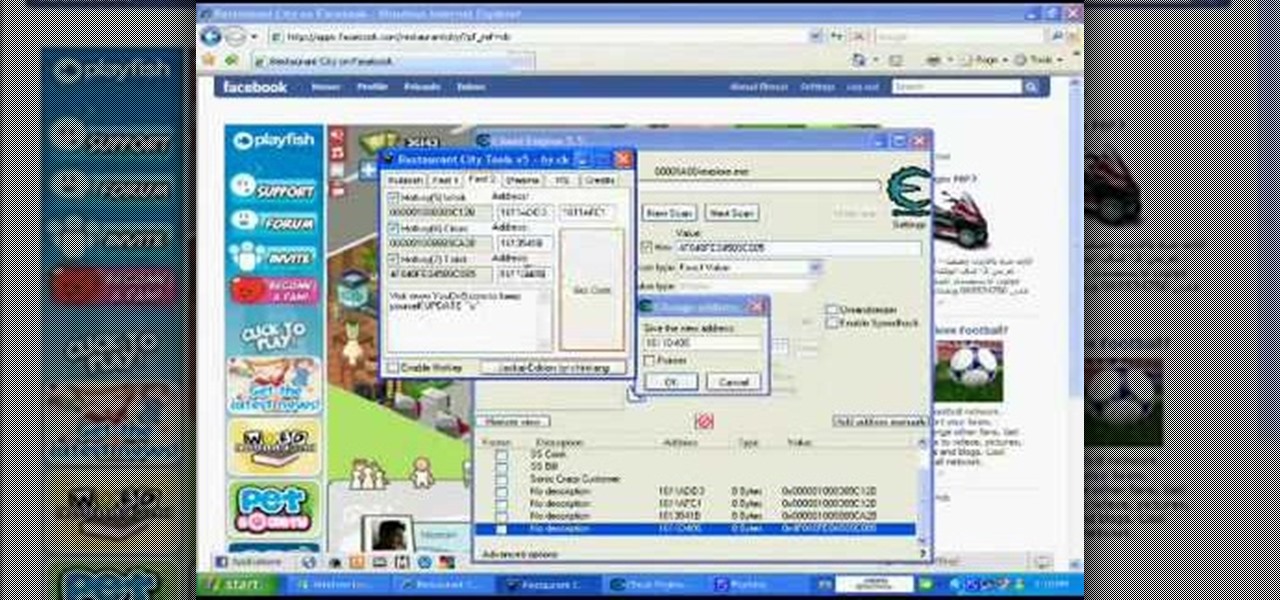
If you have any problems you can email me or visit my website at www.gapto.webs.com!!! This video shows you how to hack into Restaurant City using Cheat Engine and Restaurant Tools v5.
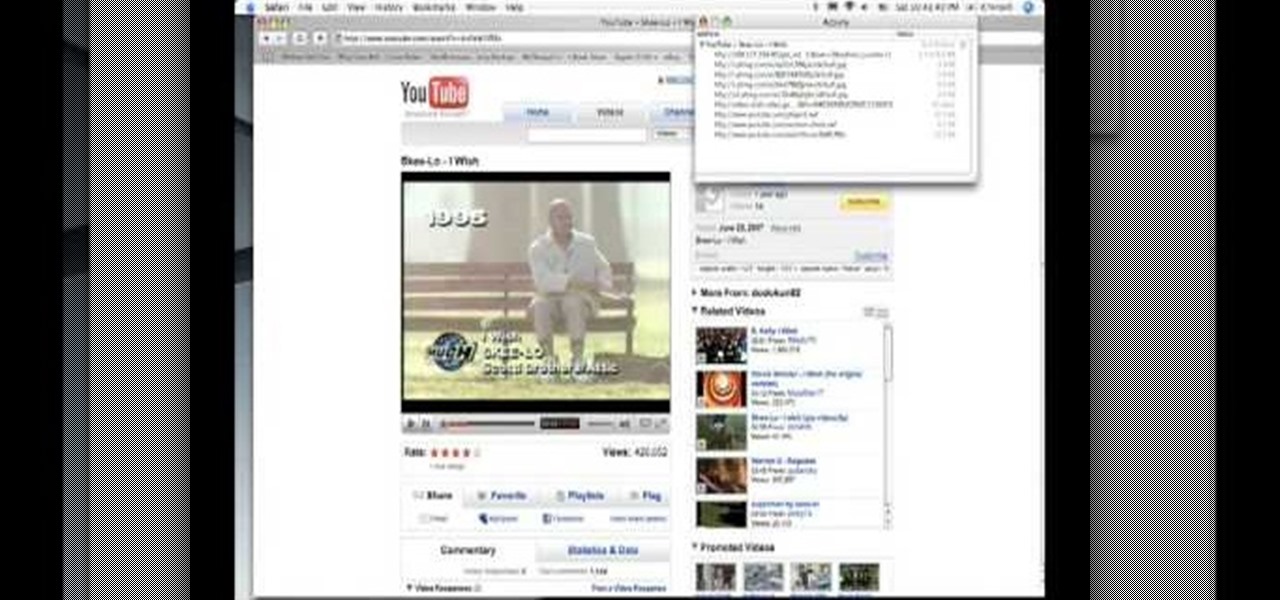
A quick video showing how to get free music online. May take a couple minutes per song. To prove quality I used the song i download in the video as background music. "I Wish" by Skee-Lo

Whenever you design elements for your garden, you should always keep in mind, that the more natural they are the better they seem to fit in. That's exactly what is done when you create this rustic bent wood trellis. But others have taken this idea a step further. In this how to video, Jim Long, author of the book Making Bentwood Arbors and Trellises, explains how to create these artistic garden ornaments.
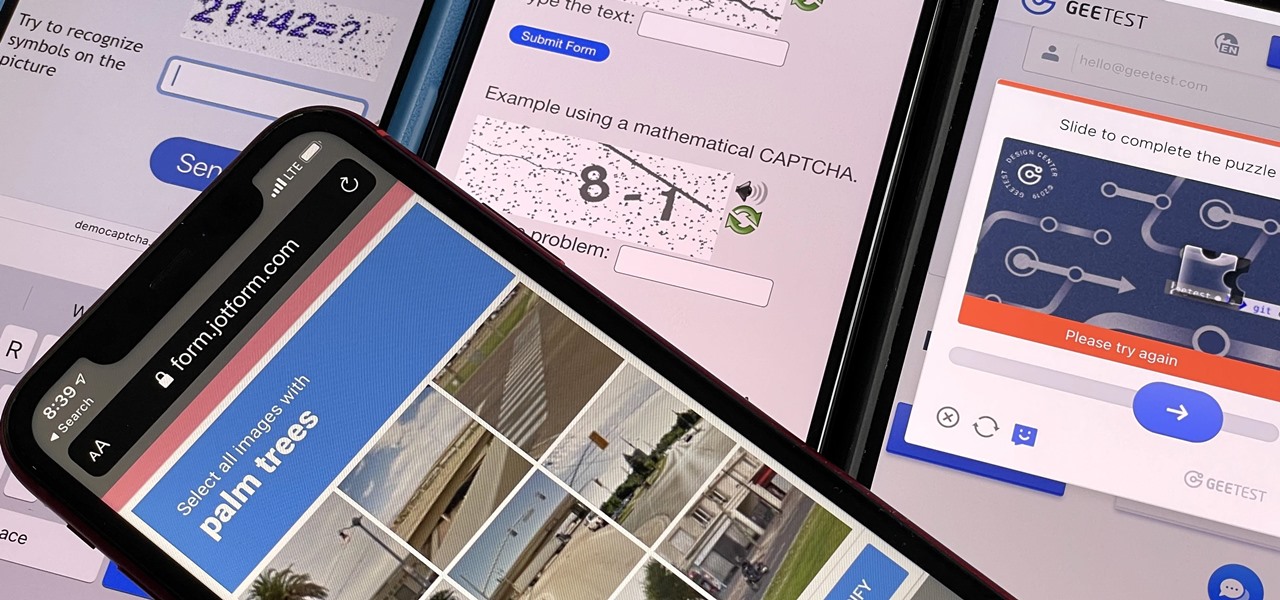
Some websites require you to perform a verification task so they know you're human and not a bot. It helps websites curb spam, abuse, unauthorized access, and cyberattacks but also adds an obstacle for anyone trying to visit their content. If you find it more of a nuisance than a necessary evil, there's an easy way to reduce the number of human verification prompts you receive on your iPhone, iPad, and/or Mac.

If you think you might be a likely target of a black-hat hacker, there's a new iOS security feature that offers extreme protection for your iPhone against spyware, phishing attempts, and other highly sophisticated cyberattacks.

Withstanding an attack from a motivated hacker is one of the most important responsibilities a system administrator must undertake. This is especially true for websites that may contain sensitive customer information and a high volume of users. So it's important for a sysadmin to take proactive measures to find and fix vulnerabilities in their websites.

SEO is the name of the game. If you want your business or brand to succeed, ranking on the front page of Google is a boon. Getting to the front page of search engines takes work, but it's not impossible when you master SEO best practices.

Let's face it: standing out in the digital world is challenging. Graphics platforms are either cumbersome to learn or produce generic stock art. A better solution is needed.

There's a lot of résumé writing happening right now. While it's a confusing and frustrating time, you don't have to wait to search for new opportunities. Maintaining a clear head and being proactive in your next career steps are two qualities that are necessary at this moment.

Whatever it is you're into, Facebook Groups are a great way to connect with others that share your interests. And beyond matching you up with like-minded people, Groups also give you access to deals on items, help you organize play dates with families in the same area, and so much more.

The cosmetics brands are among the earliest adopters of augmented reality, using virtual try-on tools to preview shades of makeup before buying.
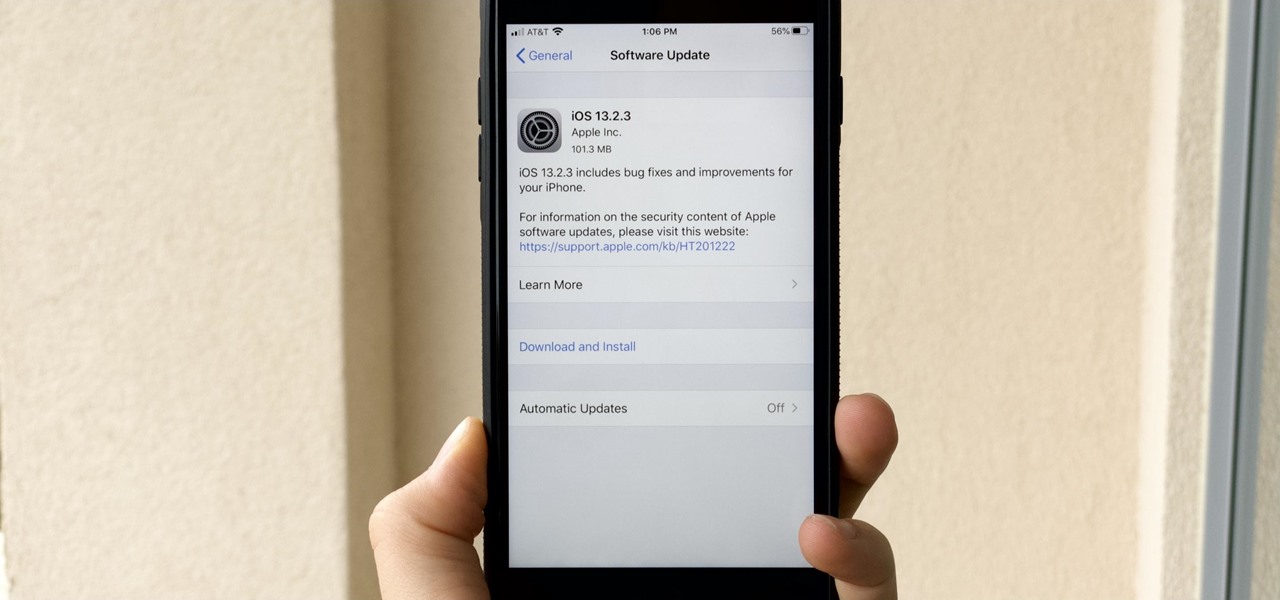
While we all refer to Apple's latest iPhone operating system as iOS 13, in truth, we're well beyond that number. The company has issued numerous updates to its big 2019 release since September, including major steps like iOS 13.1 and iOS 13.2. We've also seen minor updates, like iOS 13.2.2 eleven days ago. Today, Nov. 18, Apple releases another "minor" update, this time dubbed iOS 13.2.3.
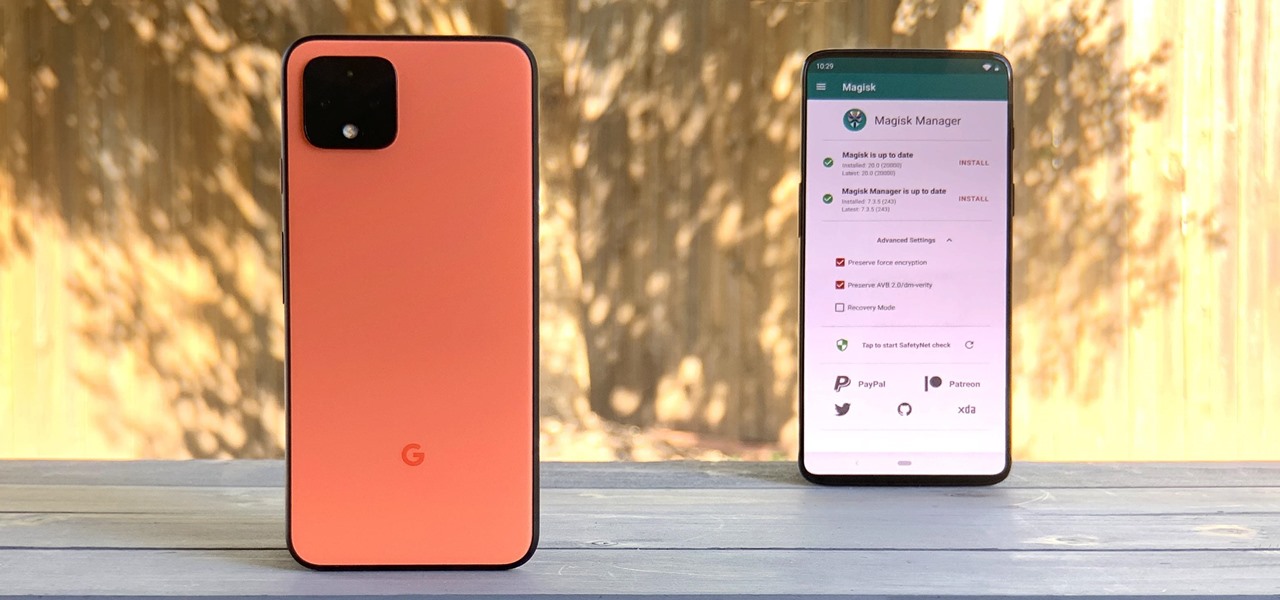
According to a study done by Kaspersky, 7.6% of Android users root their phones. That may not sound like a lot, but with over 2 billion Android devices out there, the math works out to over 150 million rooted phones — more than the total population of Russia, Mexico, or Japan — so root nation is an important demographic that deserves being catered to.
QR codes are supposed to make life easier, but having to install potentially shady third-party apps just to scan one is more trouble than it's worth. Thankfully, there's a QR code reader built into all Google Pixels, but you wouldn't know it unless you stumbled across the feature.

Apple might be a secretive company, but it's showing its hand these past few weeks. The release of iOS 13 was met with much excitement for its hundreds of new features but also frustration over the numerous bugs. Apple soon released iOS 13.1, then iOS 13.1.1, as a patch for some of those bugs, but clearly they weren't enough. How do we know? The company just released iOS 13.1.2 today, Monday, Sept. 30.

Metadata contained in images and other files can give away a lot more information than the average user might think. By tricking a target into sending a photo containing GPS coordinates and additional information, a hacker can learn where a mark lives or works simply by extracting the Exif data hidden inside the image file.

If you're noticing issues with Portrait Mode on your iPhone 8 Plus, you aren't alone. Apple confirmed the problem by introducing a new software update Monday, June 10, 17 days after the release iOS 12.3.1, and exactly four weeks after iOS 12.3. The update, iOS 12.3.2, is available only for the iPhone 8 Plus and not other iPhone models, so every other device will still be on iOS 12.3.1 for now.

The new film Brightburn, a horror take on the superhero genre produced by Guardians of the Galaxy director James Gunn, debuted in theaters on Friday, and it has some promotional backing from Snapchat to drive ticket sales.

The next libSSH or OpenSSH exploit may be just around the corner. Keep your SSH service out of Shodan's database before hackers find new ways to bypass the password protecting the server.

The long-awaited augmented reality game based on the Harry Potter franchise from Pokémon GO masterminds Niantic is closer to release, as the developer has begun public beta testing of the app.

London-based developer Andrew Hart has been working on AR navigation since Apple's original ARKit tool was still in beta preview. Now, he's ready to unleash his technology on the world.

Hollywood loves sequels so much that studios and their marketing teams are not too proud to release a sequel of an augmented reality promotion.

Giving up your Wi-Fi password can be giving up more control than you think. Because of the way Chromecast and other IoT devices communicate, anyone on the same Wi-Fi network as your device can often make it do whatever they want. With a script called "Cast All the Things," we can hijack a Chromecast to play nearly any kind of media with a single command in terminal.

Every year, fans of Irish culture, as well as those looking to celebrate their own culture, come together on St. Patrick's Day, March 17.
Canary tokens are customizable tracking links useful for learning about who is clicking on a link and where it's being shared. Thanks to the way many apps fetch a URL preview for links shared in private chats, canary tokens can even phone home when someone checks a private chat without clicking the link. Canary tokens come in several useful types and can be used even through URL shorteners.

The recent pitfalls and media fallout hitting Facebook hasn't stopped the social media giant from looking to the future.

While the betting lines on iPhones with depth-sensing, rear-facing cameras in 2019 have already been established, a new report adds some certainty to the notion that the iPhone will get new AR superpowers later this year.

In the last few weeks, the Magic Leap ecosystem has ramped up activity with a number of new releases debuting just before the close of the year.

Famed singer-songwriter David Bowie will return to the real world as part of an augmented reality app launching on Jan. 8, 2019, which would have been his 72nd birthday.