Want to watch your favorite Internet clips in the woods? Or on a boat? This video tutorial offers step-by-step instructions on downloading streaming video from video sharing websites like YouTube and Dailymotion using the media-convert web application. For more, or to get started using Media Convert for yourself, watch this video how-to!

Interested in pen spinning? Want to pick up a few moves? Pen spinning is the skilled movement of a writing instrument or pen with one's hands. It is used as a source of self entertainment (often for students), but there is a great deal of pen spinning culture (competitions, websites, etc.). Watch this pen spinning tutorial video and learn how to perform the "Continuous Middle Backaround 1.5" move.

This walks you through how to create an animated GIF image file that can be used in websites, as avatar's, as icons, etc. You'll be using Microsoft Paint to create each frame of the animation, and an application called Unfreez (found here) to animate them together.

The extract tool in Photoshop is one of the most frequently used - and useful - tools you'll ever learn to use. Extracting allows you to remove a picture from its background or even filter away flyaway hair.

It's safe to say most of us know the dangers of online security. We know there are people trying to steal our most sensitive information, and we try our best to prevent that theft. But new research is showing what we're doing might not be enough, as the sensors in our phones may be telling hackers everything they want to know.

Step 1: What Exploit Development Is and Why Should I Be Interested on About This Topic
Welcome back Hackers\Newbies!

Choosing which programming language to learn next can seem like a nearly impossible task, regardless of whether you're a novice developer or a seasoned coding pro with years of experience creating apps and websites. But if you haven't already learned Python, look no further.

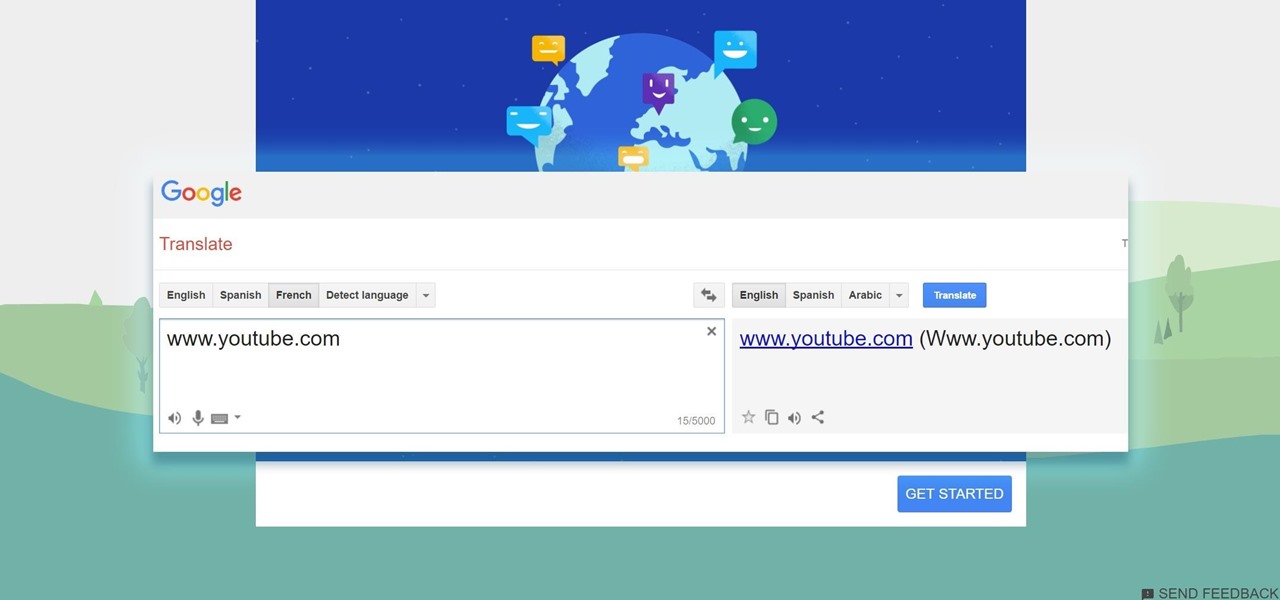
Have you ever gotten into a taxi in a foreign country and had trouble expressing where you want to go? Or tried to ask a waiter what's in the dish you're eyeing on the menu? Perhaps you just want to know what's happening in another country, and the news outlets don't offer a translated edition.

For anyone using open source information to conduct an investigation, a balance between powerful tools and privacy controls are a must. Buscador is a virtual machine packed full of useful OSINT tools and streamlined for online research. This program can easily be set up in VirtualBox, and once that's done, we'll walk you through some of the most useful tools included in it.

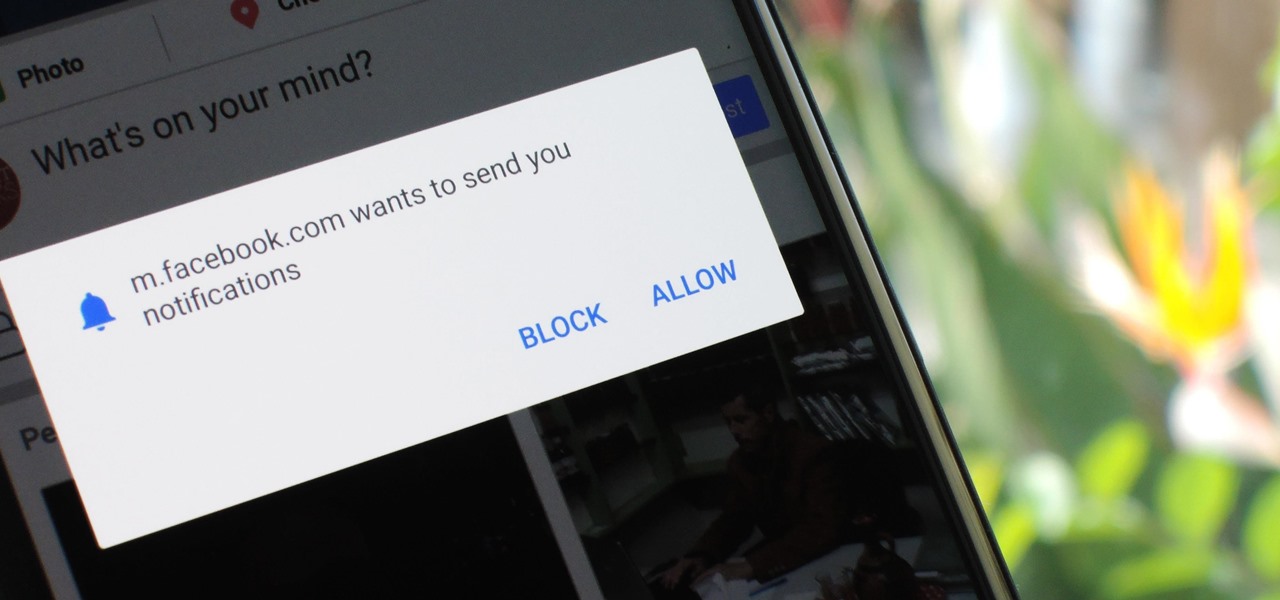
As the go-to browser for millions worldwide, Chrome makes web surfing a breeze with its simple interface and Google integration. But many websites are starting to ask if they can send you notifications, and this can interrupt your browsing. Thankfully, you can completely disable these prompts if you prefer.

Configuring onion services for the first time can be tricky. A surprising number of system administrators make seemingly trivial mistakes that ultimately lead to catastrophic cases of de-anonymizing supposedly anonymous sites on the dark web. OnionScan is a tool designed to identify common misconfigurations in onion services and aid us in understanding how to fix them.

Many websites are crowded with ads, pictures, and other irrelevant content that make it harder than necessary to read a simple article on your iPhone. In many cases, you have to zoom in just to get a better view of the text you're attempting to read—unless the webpage blocks zooming.

Welcome back, my greenhorn hackers, and happy New Year! Now that your heads have recovered from your New Year's Eve regaling, I'd like to grab your attention for just a moment to preview 2015 here at Null Byte. I hope you will add your comments as to what you would like to see, and I'll try to honor as many requests as I can.

Learn how to setup up a basic structure for a HTML web design document, define the HTML version, open and close HTML tags and learn how to apply the proper file extensions when saving document in notepad. This web design tutorial is by no means a complete structure for HTML coding and is only a brief introduction to HTML web design. This video will only go over a brief introduction to the structure of an HTML document and in a future tutorial we will go over additional components that are nee...

Online shopping is way more convenient than brick-and-mortar stores in a number of ways, not the least of which are the discounts. But with so many online stores and sites like Amazon which feature thousands of retailers, how can you know you're getting the best deal?

Need to break out of the restrictions your school or workplace have on internet browsing? Maybe you want to waste some time on YouTube, check out some gaming action on Twitch, or simply just browse Facebook or Twitter.

The WordPress revolution has completely altered the way that people build and distribute websites. Instead of having to memorize endless lines of HTML and Java, both novice and professional web developers are now able to create incredibly detailed and responsive sites using a series of intuitive templates and plugins. And each new version of WordPress comes with an improved batch of features that make web-building even easier.

Cases and stickers are always great, but they aren't the only way to customize an iPhone. The software on your device is full of customization options, from a better-looking home screen and cooler lock screen wallpapers to app icon changes and a system-wide dark mode. There's literally over 100 ways to make iOS on your iPhone genuinely unique, some of which are hiding in plain sight.

Social media accounts are a favorite target for hackers, and the most effective tactics for attacking accounts on websites like Facebook, Instagram, and Twitter are often based on phishing. These password-stealing attacks rely on tricking users into entering their passwords into a convincing fake webpage, and they have become increasingly easy to make thanks to tools like BlackEye.

Dark themes are all the rage these days, and both Android and iOS have system-wide versions. Many big-name apps and device manufacturers have already jumped on board the night train, and Google Chrome is no different. But the Chrome mobile browser offers various ways to enable its dark theme.

There's a lot of misinformation about VPN services, and it stems from the fact that not all of them are created equal. Some focus on privacy, others on security, and a few VPNs are seemingly even purpose-built for the polar opposite: data collection. We made this guide to help clear the air on some of these issues while objectively ranking the best of the best.

Privacy and security go hand in hand, especially for smartphones. When it comes to privacy, you decide what personal information about yourself is out there to discover. Security, on the other hand, is all about enforcing those privacy decisions.

The biggest corporation we know today is called Google, I bet you've heard of it yeah? How Google Tracks You:

welcome back my masters , teachers and classmates , in this second part of this 0-day series we will learn the basic of fuzzing, and i bought some gift for nullbyte(a 0 day vuln that will be released today exclusively on null-byte) .

Doxing is the act of finding one's personal information through research and discovery, with little to no information to start with. You may have seen doxing in the news, for instance when not so long ago, hacker team Anonymous doxed and reported thousands of twitter accounts related to ISIS. Doxing can be useful for finding the address of a coworker, or simply investigating people on the internet. The tutorial I will provide to you now will teach you the basics of doxing and how you can prot...

LastPass is a password manager that's been around for some time, and has finally made its way over to Android for use with apps, not just websites.

On the latest iOS software, your iPhone comes with significant privacy and security enhancements to protect your data even more than Apple did before. From safeguarding your iPhone to passcode-protecting files to making it easier to browse the web safely, there's a lot you need to know and start using.

URL tracking codes: you'll see them on almost every link you copy online to share with friends and followers. It could be tens or hundreds of extra characters appended to the end of a URL, which websites and marketers use to tell how you got to the link in the first place. These excess tracking tokens not only make the links you share look sloppy and spammy — they could even invade your privacy.

It only takes a few commands to manipulate a MacBook's secure HTTPS traffic and pluck login passwords out of the encrypted data. Let's take Facebook and Gmail hacking to the next level by intercepting Safari and Google Chrome web traffic in real time.

Coinhive, a JavaScript cryptocurrency miner, was reportedly discovered on the BlackBerry Mobile website. It was placed there by hackers who exploited a vulnerability in the site's e-commerce software that allowed them to anonymously mine cryptocurrency every time the website was viewed. There's no doubt Coinhive, an innovative mining method, is being abused and exploited by hackers in the wild.

This tutorial will explain how to make buttons and links to flip between pages in InDesign files. Create sleek looking, easy to use documents that can be used as websites or PDFs. This video will show you how to use InDesign to its full potential.

In this video tutorial, viewers learn how to clear their cookies in Mozilla Firefox. Begin by opening the web browser. Then click on Tools from the top menu and select Options. In the Options window, click on the Content tab and deselect "Block pop-up windows". Click OK. Now click on Tools and go to Options once again. Click on the Privacy tab and click on Clear Now under Private Data. Make sure that Cookies and Cache are checked and click OK when finished. This video will benefit those viewe...

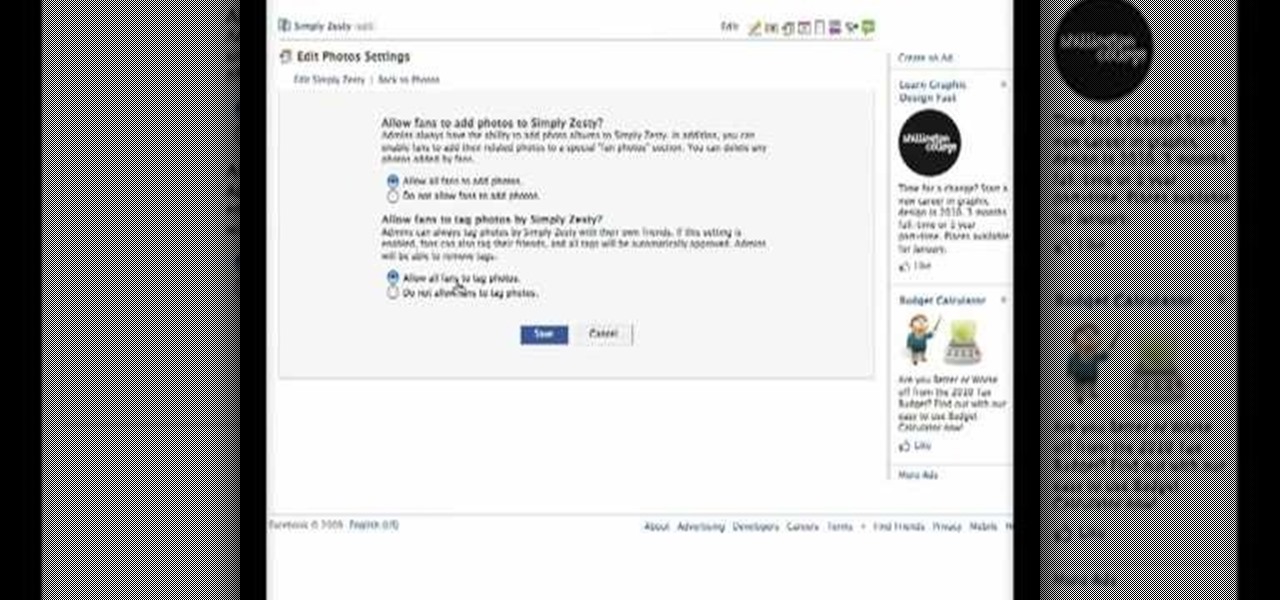
Facebook is the most popular social networking websites that can be used to stay in touch with friends and family. Using facebook you can look up your friends and even see the photos they have uploaded. You can also tag photos in the application. To do this go to your editor page and scroll down to photos. Now click edit settings inside it. At the bottom select 'Allow all fans to tag photos' option and save it. Now when you go to your home page and open the photos section you can tag them and...

In this video, we learn how to dress chic like a geek! Dressing like a geek is becoming one of the hottest ways to dress! Some of the modern geek fashions are shirts with binary on them, old school video game shirts, geek shirts and many others. You can visit websites including ThinkGeek, which has a section dedicated to geek clothing. They also have shirts that relate to computer geek information and talk. Zeestuff is an apparel site that has game wear apparel for gaming geeks. There are als...

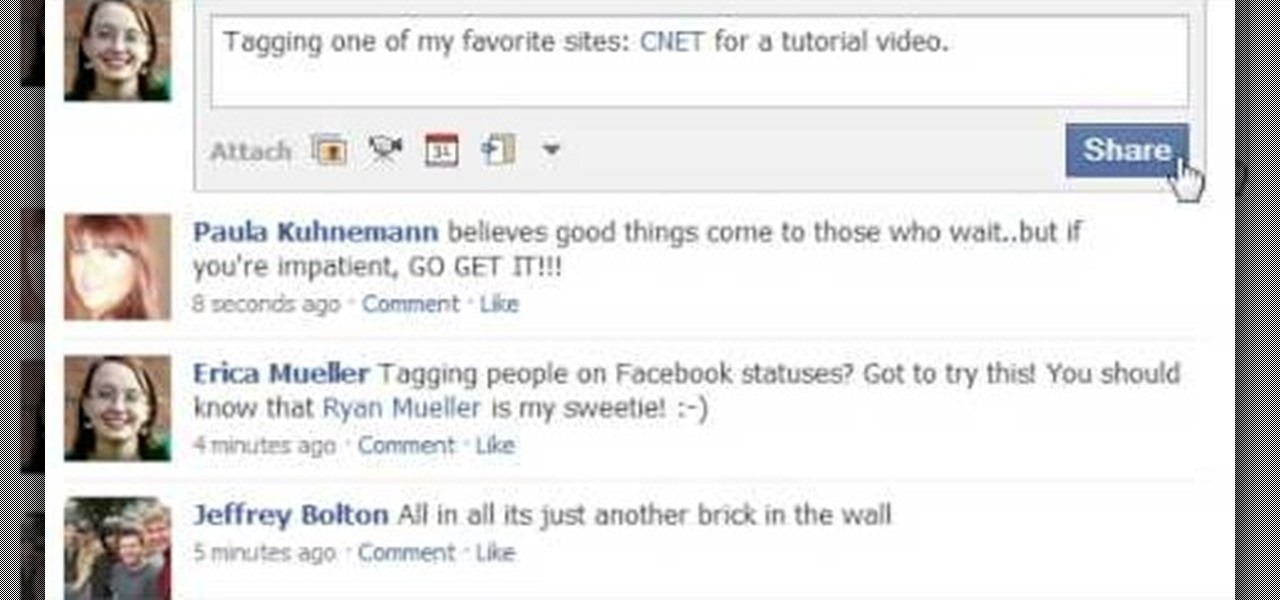
This short video demonstrates how to tag websites and groups in your Facebook status. In your status window start typing what you would like to tag. For example write "Tagging one of my favorite sites:" At this point type the @ symbol. Right after the @ type in the particular site you would like to tag. When you are finished typing press 'Share' and this will appear on your Facebook page with a clickable link to the site you tagged.

This video teaches the secrets of downloading and using uTorrent in your computer. First download the software from the link shown in the video and open it. Now to download any file search some popular torrent websites. Make sure you select a torrent file with more SEEDS but less LEECHERS and download it. Now open the downloaded torrent, select the required files if there are many and start downloading. After downloading stop the torrent and use the files.

CreativeIceDesigns shows you how to make a "Polaroid"-style image on Photoshop CS3. Open a new 400 x 500 pixel image, and create a new layer, and drag underneath the original background layer. On the original "Layer 0" (the top-most layer), take the marquee tool and cut out (delete) a square, so that what you have in front of you looks like a Polaroid picture. Drag the the picture you want in, transform it into the right shape (ctrl + T) and drag it underneath "Layer 0." You can add effects (...

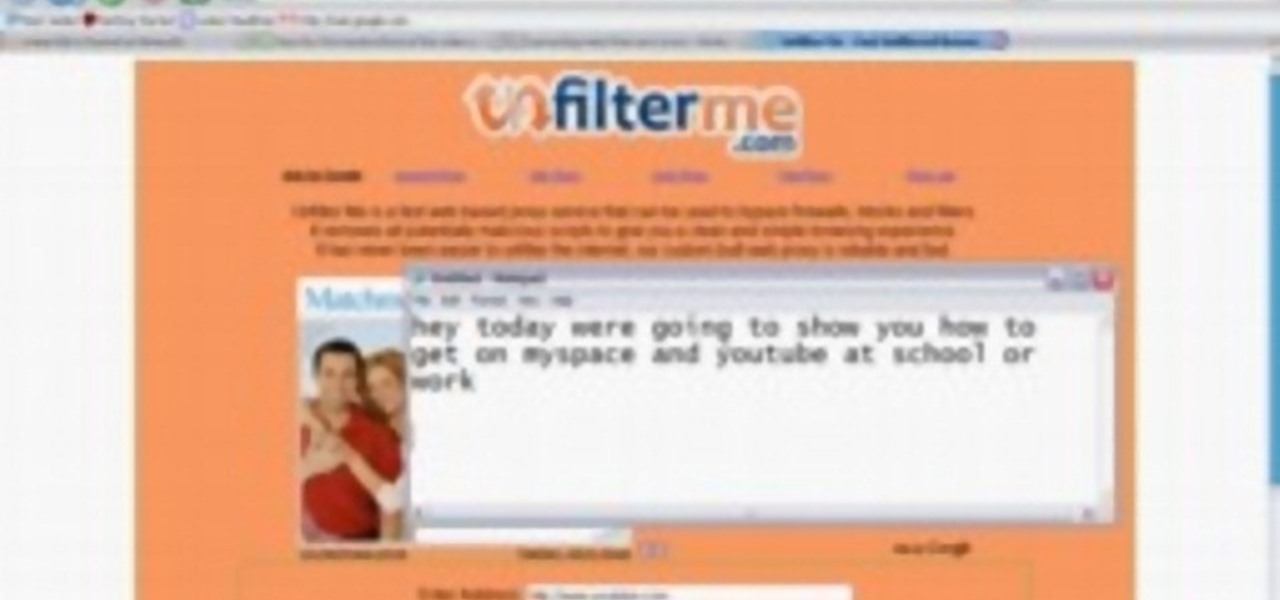
This video shows you how to easily access blocked website like MySpace or YouTube at school. The first thing you have to do is open the web browser and surf to Unfilter Me . Then, type your desired web site URL in the "Enter Address" field. Hit the "Start Browsing" button and wait for the site to load. Note that the URL in the address bar is different. This is the easiest way to access blocked websites at school. That's it! Good Luck!