In this web design tutorial learn how to use the straight line tool. Although the straight line tool might seem like a useless tool I can tell you from experience it is very useful. Especially if you have ever attempted to draw a straight line with a tool other than the straight line tool. There are many ways you could use the straight line tool such as dividing content, design graphics, separating navigation menu headers and much more. My recommendation would be that you take a look at some ...

The creation of private browsing was brought upon by the backlash against ad tracking and other ways that sites and agencies take away users' privacy online. People were tired of getting spammed with ads for Vitamin C pills simply because they visited WebMD. Private browsing is now built into all of the major browsers and is used frequently. While private browsing is more infamously known as the "Porn Portal," and does prove to be a great way of keeping racy content out of the sight of others...

We've all seen the breathtaking, colorful photos of the Eagle, Egg and Cat's Eye Nebulae. You may not recognize them by name, but you've seen them, whether in astronomy textbooks, magazines, websites, album covers, or tee shirts. They are some of the most striking photographs ever taken from the Hubble Space Telescope (HST).

At first, it seemed like a clever art installation housed on the web, but now we're not so sure... the Newstweek hack may indeed be legit.
Safari's massive upgrade in Apple's latest iPhone software update includes new features you won't find in any other web browsers on iOS, from better ways to stay organized to enhanced security and further privacy protections.
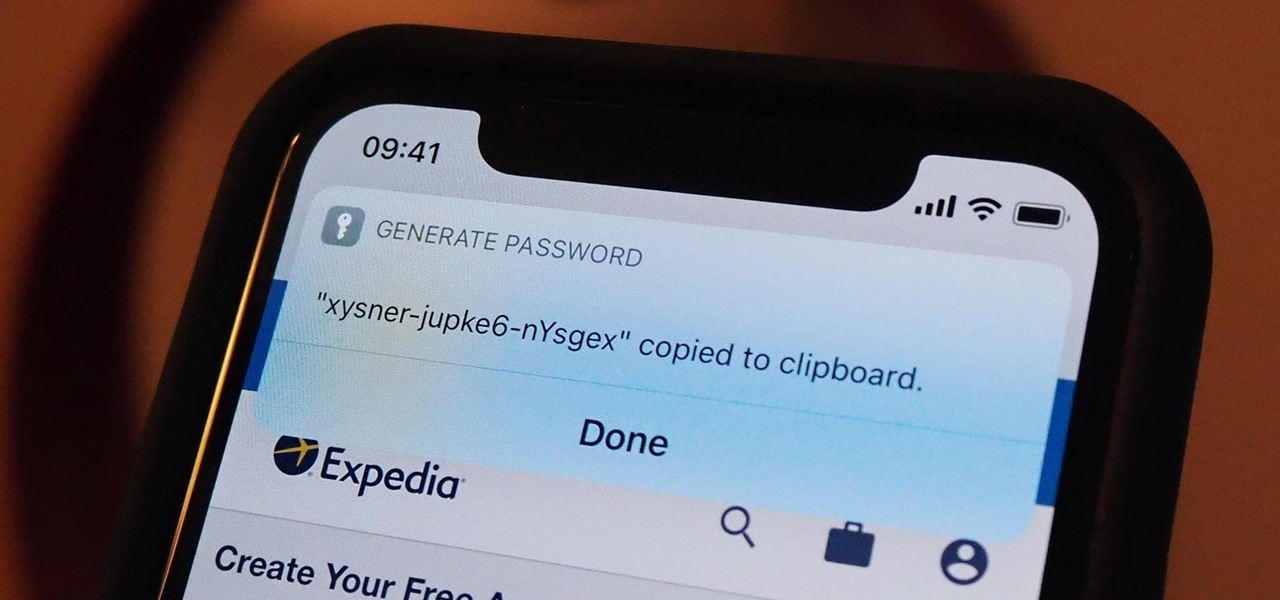
Apple's password manager, iCloud Keychain, lets you securely save important login credentials for apps, websites, and services that sync up across all of your Apple devices — iPhone, iPad, iPod touch, and Mac. One of its biggest highlights is that it can create strong passwords for you. Unfortunately, it doesn't always work, and in those cases, there are other ways to generate random, strong passwords.

Wordpress is one of the world's most-loved content management systems (CMS). The user-friendly interface and ease of use have made this open-source system a no-brainer for millions of people. Over one-quarter of the top 10 million websites on the planet use Wordpress.

One of the first steps when pentesting a website should be scanning for hidden directories. It is essential for finding valuable information or potential attack vectors that might otherwise be unseen on the public-facing site. There are many tools out there that will perform the brute-forcing process, but not all are created equally.

Reconnaissance is one of the most important and often the most time consuming, part of planning an attack against a target.

Phishing is the easiest way to get your password stolen, as it only takes one mistake to log in to the wrong website. A convincing phishing site is key to a successful attempt, and tools to create them have become intuitive and more sophisticated. SocialFish allows a hacker to create a persuasive phishing page for nearly any website, offering a web interface with an Android app for remote control.

When researching a person using open source intelligence, the goal is to find clues that tie information about a target into a bigger picture. Screen names are perfect for this because they are unique and link data together, as people often reuse them in accounts across the internet. With Sherlock, we can instantly hunt down social media accounts created with a unique screen name on many online platforms simultaneously.

Gathering information on an online target can be a time-consuming activity, especially if you only need specific pieces of information about a target with a lot of subdomains. We can use a web crawler designed for OSINT called Photon to do the heavy lifting, sifting through URLs on our behalf to retrieve information of value to a hacker.

If there's one strength of Apple's that iOS and Android fans can agree on, it's the company's dedication to user privacy. With each new iteration of iOS, Apple builds upon these foundations, enhancing and increasing each iPhone's ability to protect its user's data. In iOS 12, Apple has added many new features to Safari, most of which have their own unique way of keeping you safe online.

A convincing domain name is critical to the success of any phishing attack. With a single Python script, it's possible to find hundreds of available phishing domains and even identify phishing websites deployed by other hackers for purposes such as stealing user credentials.

Unlike many browsers, Firefox gives a lot of control to the user. By default, Firefox does a great job of balancing security and performance. However, within the app's settings, you can modify options to shift this balance in one direction or another. For those looking to shift it toward security, here are few suggestions.

As the third-largest smartphone manufacturer in the world, Apple devices are a constant target for hackers everywhere. While iOS has seen fewer common vulnerabilities and exploits (CVEs) in recent years, iPhones still aren't hack-proof. Fortunately, you can strengthen your security with the help of a few apps.

WordPress did not become what is arguably the most popular blogging and CMS platform on the planet because it was difficult to use. Rather, its user-friendly and rich feature set led to it finding a home on somewhere north of 70 million websites—and that's just counting blogs hosted on WordPress.com.

Hello NullByte! This will be my first How To series.

hello hackers,newbies and followers of this great community, after some research here in our community, I noticed that there is not even one tutorial that teach Web Development. We have a lot of tutorials on how to hack web site but many do not know exactly how a web site is composed, then I decided, meeting the community's needs, begin to teach people how to develop web sites.

Smartphones are almost always connected to the internet, so it stands to reason that they can be hacked remotely. Or perhaps a jealous boyfriend or girlfriend got hold of your device physically, in which case they could've potentially installed a keystroke logger, a virus, or any other type of tracking app to spy on you.

INTRODUCTION Hello dear null_byters here we go again with our third part of this serie.

Today I am going to teach the various ways that you can use social engineering to hack a system. For those of you that have followed my past tutorials, you know that social engineering can unlock a world of possibilities. This is because no matter how many firewalls, no matter how many patches there are on a server, the password is kept in the minds of people...and people, are not as smart as computers.

While most of us don't think twice about dragging a pattern or using Touch ID to open our phones, or entering a password in for our email and bank accounts, these features are there to protect some of our most private information. Only problem is, they don't do a good job of it.

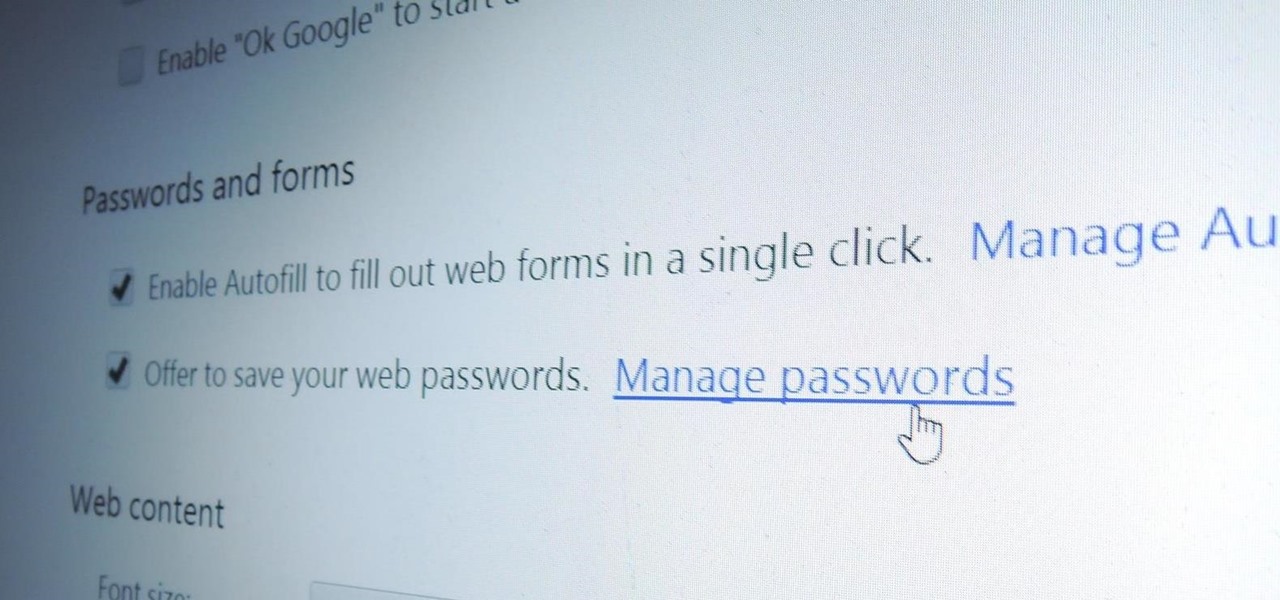
Chrome, Firefox, and Safari all provide built-in features that allow you to save your username and password for your favorite sites, making the process for entering your credentials a breeze when you revisit them.

There are few apps on my iPhone that I visit on a daily basis, and one of them is Drippler, the discovery and news app that tells you everything you need to know about your device.

For over 20 years, a tiny but mighty tool has been used by hackers for a wide range of activities. Although well known in hacking circles, Netcat is virtually unknown outside. It's so simple, powerful, and useful that many people within the IT community refer to it as the "Swiss Army knife of hacking tools." We'll look at the capabilities of Netcat and how the aspiring hacker can use it.

There is never a dull moment when it comes to the internet. You can find practically anything you want, whenever you want it. To make that process even smoother and more direct, companies have created a bunch of apps designed to help you find what you're looking for, or enlighten you on a subject you may not have even thought of yourself.

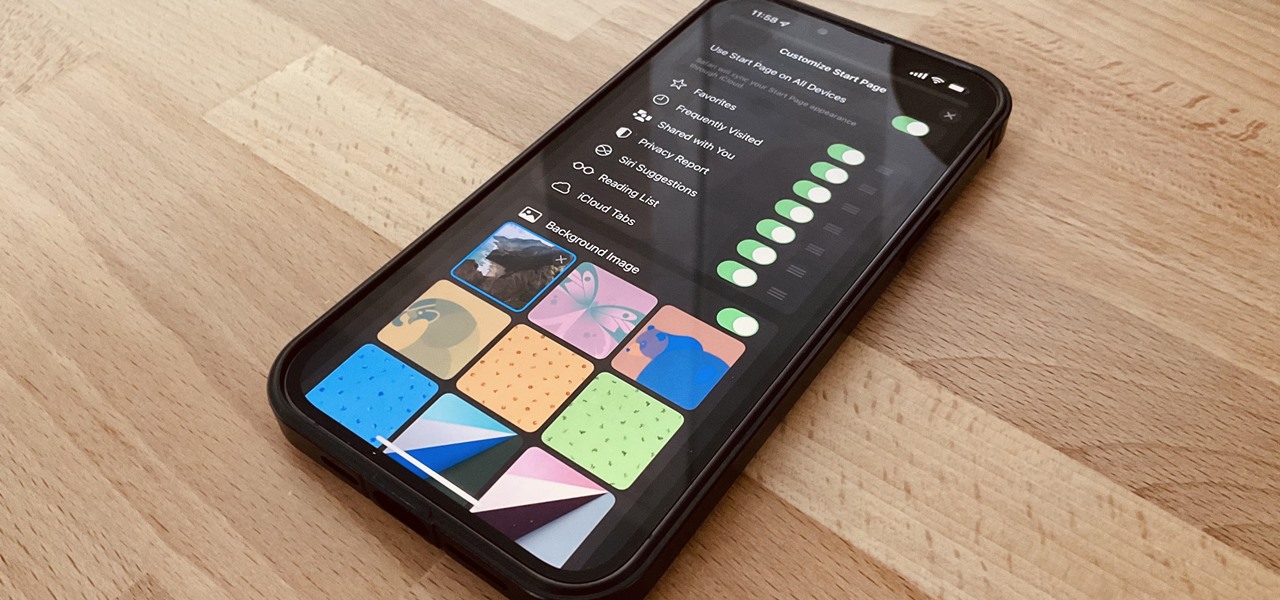
One of the biggest grievances with Safari on iPhone was always its lack of customization, and iOS 15's browser upgrades tackle that problem head-on. Apple added many great features, including Safari extensions, Tab Bar, and Tab Groups, but the most prominent feature caters to those obsessed with finding the perfect Home and Lock Screen look.

You've probably already used a few Safari Extensions on your Mac, but if you haven't explored Safari's web extensions on your iPhone yet, you're missing out on some fantastic possibilities to increase productivity, make tasks easier, filter out noise, and bring more fun to your browsing experience.

Using a strong password is critical to the security of your online accounts. However, according to Dashlane, US users hold an average of 130 different accounts. Memorizing strong passwords for that many accounts is impractical. Fortunately, password managers solve the problem.

Okay, so you've decided to take the plunge, and participate in our Love. Earn program with a how-to article. But, for whatever reason, your article keeps getting rejected by WonderHowTo, and you're wondering, well, where's the love?

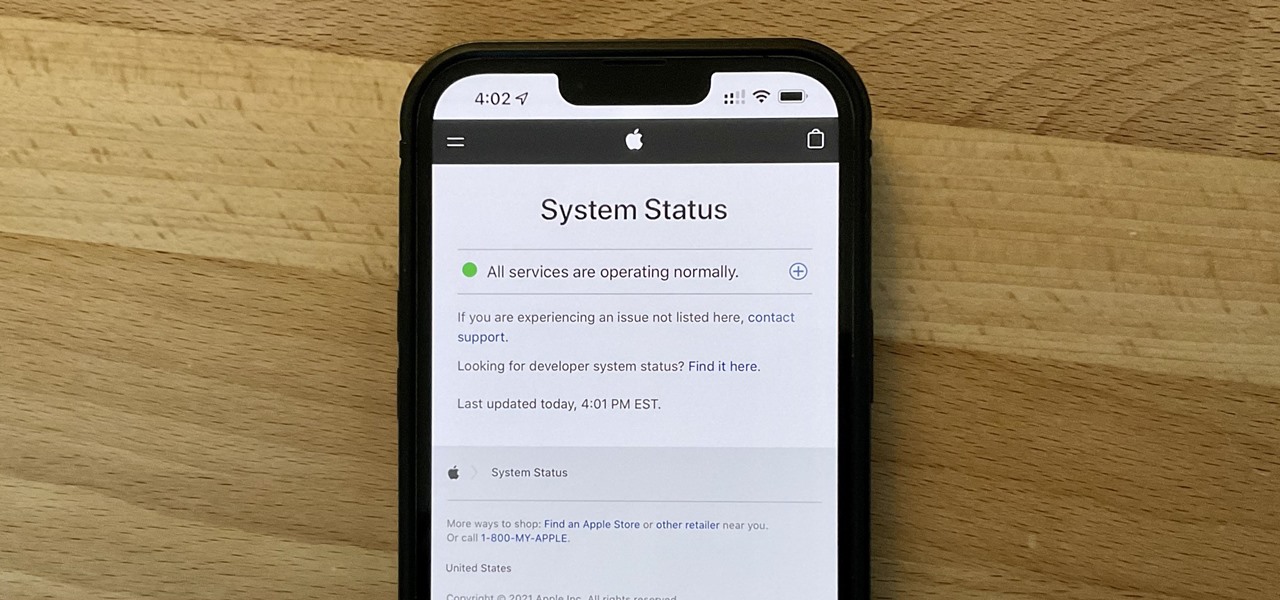
It can be very frustrating: You open your Messages app, send an iMessage, and then see that dreaded red exclamation point or horrible green SMS bubble. At this point, you may be curious whether it's just your iPhone or whether iMessage is broken for everyone, but how do you find out?

It's no secret that the vast majority of Null Byte readers range from beginner to seasoned coding pros and developers. Regardless of whether you're interested primarily in building websites or creating best-selling apps and games, working with a wide variety of programming languages remains one of the best ways to make serious money in an increasingly app-driven world.

There's a lot of résumé writing happening right now. While it's a confusing and frustrating time, you don't have to wait to search for new opportunities. Maintaining a clear head and being proactive in your next career steps are two qualities that are necessary at this moment.

Whatever it is you're into, Facebook Groups are a great way to connect with others that share your interests. And beyond matching you up with like-minded people, Groups also give you access to deals on items, help you organize play dates with families in the same area, and so much more.

So you want to know what that person who is always on their phone is up to? If you're on the same Wi-Fi network, it's as simple as opening Wireshark and configuring a few settings. We'll use the tool to decrypt WPA2 network traffic so we can spy on which applications a phone is running in real time.

Chrome has just introduced some new UI elements for web exploration. The new URL bar is not intuitive. But once you get to grips with it, you will be so much more efficient in your address bar editing, pasting, and navigation.

Complex shell scripts can be implanted into photo metadata and later used to exploit a MacBook. In addition to obfuscating the true nature of an attack, this technique can be used to evade network firewalls as well as vigilant sysadmins.

Hacker's are always looking for new ways to exploit systems and exfiltrate passwords, even in hashed form. Sophisticated brute-force attacks powered by high-end GPUs can perform millions of password attempts per second. But Ubuntu and Debian users aren't completely helpless. There are ways to harden the hashed password to better defend against Hashcat attacks.