A-BnC Parties and More, Inc. demonstrates how to construct a do-it-yourself music guitar cut out for your musical theme party centerpieces. The guitar is accented with guitar strings made from black yard, heavy black card stock and clear push pins. Judy shows how to take a plain white polystyrene guitar cut out, paint and add these lovely accents. She puts it on another budget Just Add Sand centerpiece base and accents with two pieces of onion grass. Add balloons, a table name and table place...

Judy of A-BnC Parties and More, Inc. shows you how to make an economical do it yourself music note centerpiece. Three music notes are attached to wooden dowels which are added to a budget Just Add Sand centerpiece base. The centerpiece is accented with two pieces of onion grass. Add balloons, a table name and table place cards for an economical musical themed music note centerpiece for your Bat Mitzvah, Bar Mitzvah, wedding, special event or party!

This two part video tutorial teaches you how to make metallic paper poofs which can be used to camouflage the Styrofoam® base of your centerpiece. The poofs, or flowers, also add color and excitement to your finished product. Metallic paper reflects light and comes in deeper tones that tissue paper. Use these flowers for all kinds of centerpieces: bar or bat mitzvah, wedding and engagement, birthday, sports theme, retirement, anniversaries, corporate events, etc.

If you cover a particular area in tech long enough, you develop certain pet peeves, and one of mine happens to be devices that attempt to keep us wed to the Google Glass style of augmented reality. And while I remain mostly uninterested in such devices, one of these products recently earned my admiration and might work for you, too, under the right circumstances. It's called the Golden-i Infinity.
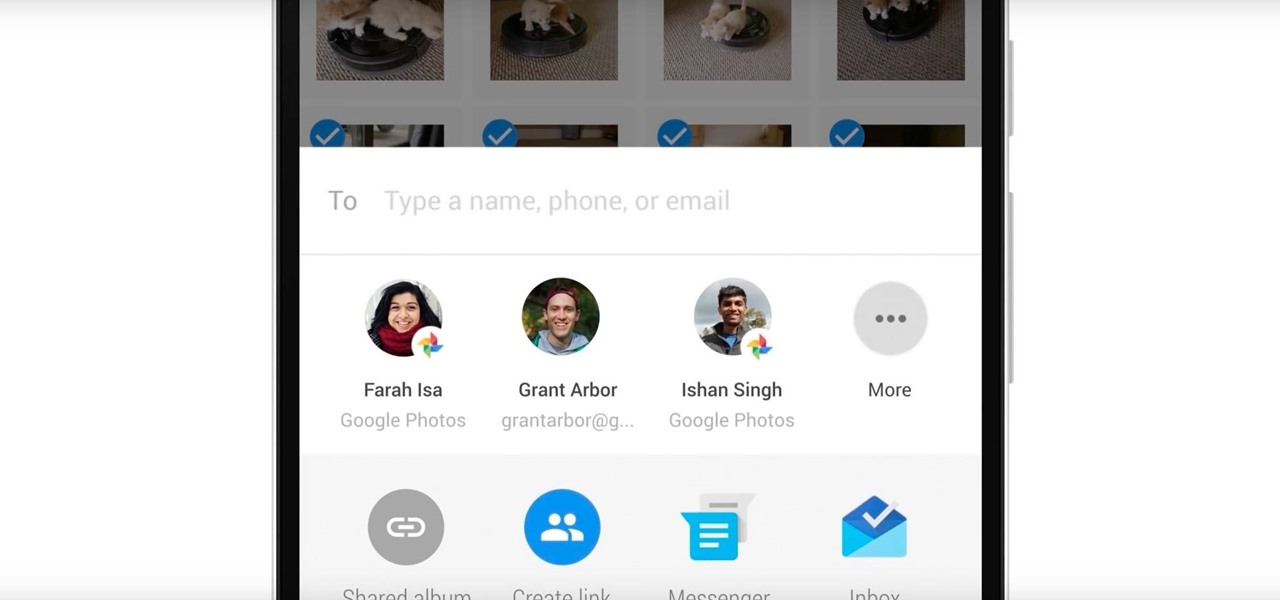
In case Google Photos didn't recognize your face enough, they're now rolling out a new AI feature who uses facial recognition for easy photo sharing.

At Facebook's first Communities Summit, admins from top Facebook groups assembled to discuss tools to better manage and optimize their members. Here, Facebook CEO Mark Zuckerberg announced that these changes fuel the company's shifting focus from connecting the world to uniting it.

If you find this update from Pinterest more than a little creepy, I agree. If you don't, then keep reading about how Pinterest's updated "Lens" feature is your next must-have tool!

One lump or two? That was the age-old question with sugar cubes, which used to be a staple of any tea salon or dignified household this side of Downton Abbey. These days sugar isn't really used in cubes much except in bars and restaurants, and that's a shame. Cubes are a lot less messy than granulated sugar, and you can measure the exact amount you put in your drink no matter what.

Most people keep their ungodly sexual desires deep inside, only to be indulged in private on their computers. It makes you wonder... what secrets do your neighbors have? What kind of porn are they watching? And how much and for how long? Thanks to some public (and anonymous) data, you can now find out.

Have you ever admired those individuals that get so much accomplished in a day and wonder how the heck they do it? Now's your chance to learn their secrets. The Productivity & Motivation Master Class Bundle brings you everything you need to life-hack your way into leading a more productive lifestyle at home and work.

Amazon Web Services (AWS) offers over 200 services, including networking, computing, storage, analytics, blockchain, mobile, and developer tools. Not surprisingly, numerous companies rely on AWS's massive infrastructure. Instead of building their own server farms, they rent space and computing power from AWS's secure and robust system.

Invented by Motorola engineer Bill Smith in 1986, Six Sigma's methodology defines a series of steps with specific value targets. These targets can be used, for example, to eliminate costs and process cycle time while increasing profits and customer satisfaction.

Most of us have never put much thought into this, but the question needs to be asked — what exactly happens to all of our online accounts when we die? No, the internet won't just know and delete accounts for you, so you need to plan for life's one guarantee. Because without a plan, things become a lot harder to sort out.

The iPhone X, iPhone 8, and iPhone 8 Plus may be some of the fastest phones of 2o17. However, the equally new iOS 11 isn't quite as impressive. That being said, Apple is continuing updates to the developer beta for iOS 11.1, as it releases the 5th version of the beta today.

A man-in-the-middle attack places you between your target and the internet, pretending to be a Wi-Fi network while secretly inspecting every packet that flows through the connection. The WiFi-Pumpkin is a rogue AP framework to easily create these fake networks, all while forwarding legitimate traffic to and from the unsuspecting target.

Take a close look at the image above. These bugs spread a deadly parasite that infects thousands of people each year. They also live in the US, and it's important to know where they are and whether you need to worry that they're carrying a dangerous infection.

Android has several features built into the platform that improve user experience but require extra attention to prevent a security breach. By modifying these settings, you can drastically reduce the possibility of someone exploiting your device or intercepting information.

Marijuana is legal to use for medical purposes in 28 states and the District of Columbia, but the quick development of this new industry could have left some regulation issues in the lurch.

This tutorial was written with Windows 7 in mind, but the principle applies to all versions starting from 7.

Well hello dear readers of Null byte, let me start off stating english is not my first language and they will be some grammar mistakes. This also is my first tutorial so don't hesitate to give me feedback :)

Apple just showed off iOS 9 and its new features at WWDC 2015, including multitasking support for iPads (finally!), a new Low Power Mode to save battery, local area search and transit directions in Maps, a highly improved "Proactive" Siri, a better Spotlight search, new apps, and so much more.

It's been a while when the major web browsers first introduced HTTP Strict Transport Security, which made it more difficult to carry Man In The Middle (MITM) attacks (except IE, as always, which will support HSTS since Windows 10, surprised?).

Nintendo fans rejoice! Not only can you play classic NES games on your iPad or iPhone without jailbreaking, you can play Game Boy Advance and Game Boy Color games. And that's not it. Now, thanks to @angelXwind, we can add Nintendo DS to our list of non-jailbreak emulators for iOS 7.

A few days ago, Russian hacker Alexy Borodin found a way to get free in-app purchases on an iPhone or iPad. In-app purchases include things like items and power-ups for iOS games, as well as subscriptions and "premium" memberships for certain apps.

Create your own floral centerpiece design with silk wedding flowers. Learn how to make a silk bridal bouquet in this free flower arranging video series.

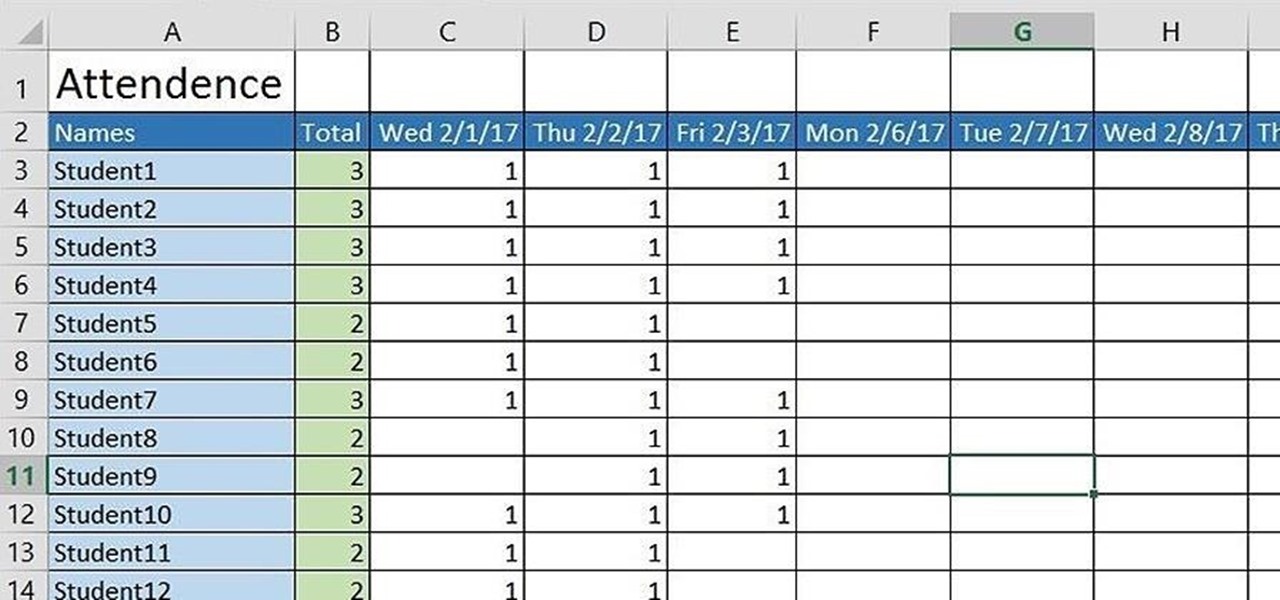
If you're a teacher in any type of school, whether it's high school, college, or middle school, it's imperative that you keep an attendance sheet. The paper and pen route can get pretty messy, and very disorganized, and that's where Microsoft Excel comes in. With this software, you can create a simple yet functional attendance sheet to keep track of your students.

Photo books are a great way to consolidate your favorite moments into one place, and there's no need to buy those clunky photograph books anymore, especially when the whole world of photography has turned digital. That's where Lulu comes in.

This pop up greeting card project is to celebrate a wedding or give someone best wishes. Brenda is an expert on this simple art project.

In this video series, watch as professional homemaker Vickie Pavone teaches how to iron clothes and other household items. Learn how to iron fitted sheets, how to iron flat sheets and pillow cases, how to iron a blouse, how to iron a skirt, how to iron pleats, how to iron a men's button down shirt, how to iron a men's polo shirt, how to iron slacks, how to iron denim, how to iron a law enforcement uniform, how to iron clothes using starch, how to iron, delicate silk fabrics, how to iron synth...

While you may not notice them at first, iOS 11 included some pretty significant improvements to the Photos app on your iPhone. These upgrades will help you make your Live Photos livelier, surprise you with photos you totally forgot about, keep your photos and videos organized, and more.

When most people say, "Damn, look at that rock," regarding an engagement ring, they're usually not referencing an actual rock—let alone a space rock.

My Cuisinart ice cream maker was a wedding gift; it wasn't something on my list, but I jumped up and down with delight when I unwrapped it. I never would've purchased this appliance on my own because it didn't seem practical, yet I loved the idea of making homemade ice cream.

You might be familiar with the use of zucchini blossoms in cooking and maybe even know how to make herbal simple syrups. But if you really want to show off as someone who knows how to use flowering plants in food, try adding some flower water to your cooking/baking repertoire.

We are visual animals. So when it comes to food, presentation is everything. In deciding what to eat, certain colors and textures instantly turn us off or on. Think of runny sautéed spinach versus a salad of fresh vibrant spinach. Which one would you reach for first?

KitKats? Toast? Sorry if that headline made you hungry, but no I'm not talking about Nestlé's chocolatey wafer treat, nor the crunchy slices of bread you have with your eggs in the morning.

Yes, boys. It’s true. It’s here. IT’S FOR REAL!! I am here to provide a list of things that boys should do (meaning they don’t do these things very often, probably why us girls think it’s adorable when they do) when they are pursuing one of us lovely ladies. There is a lot more to making her fall for you than you think, and yes, it’s the little things. The opened doors, the little touches, the tiny encouragements. Those are the things that matter. So here we go...

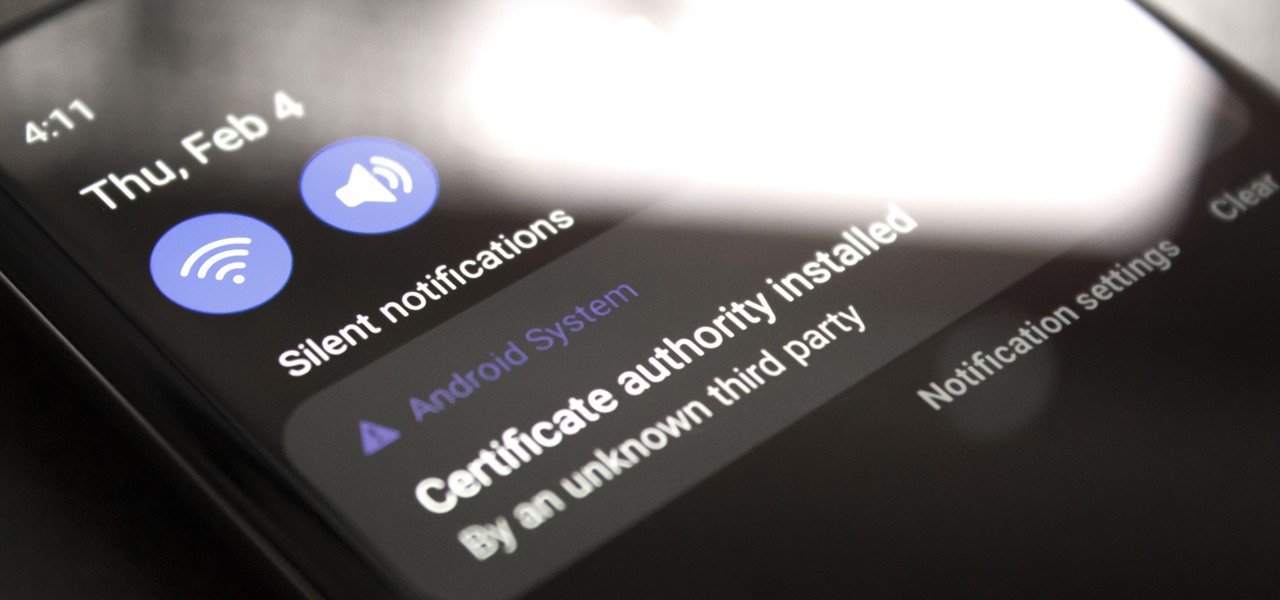
If you're using a VPN-based ad blocker with full HTTPS functionality on a Samsung phone, you'll get a notification informing you there's a third-party security certificate in use. No big deal, except it shows up every time you restart the phone. Samsung isn't alone in this type of annoyance, either.

Directory traversal, or path traversal, is an HTTP attack which allows attackers to access restricted directories by using the ../ characters to backtrack into files or directories outside the root folder. If a web app is vulnerable to this, an attacker can potentially access restricted files that contain info about all registered users on the system, their permissions, and encrypted passwords.
Have you ever used an open wifi, which after you connect displays a website to enter your credentials to get internet? That website is called captive portal and widely used in airports, hotels, universities etc. Have you ever wondered what would happen if someone would set up an open wifi with the same name displaying a very similar web page asking for credentials? Usually if there are multiple wifi networks with the same name and encryption, devices only display the one with the highest sign...

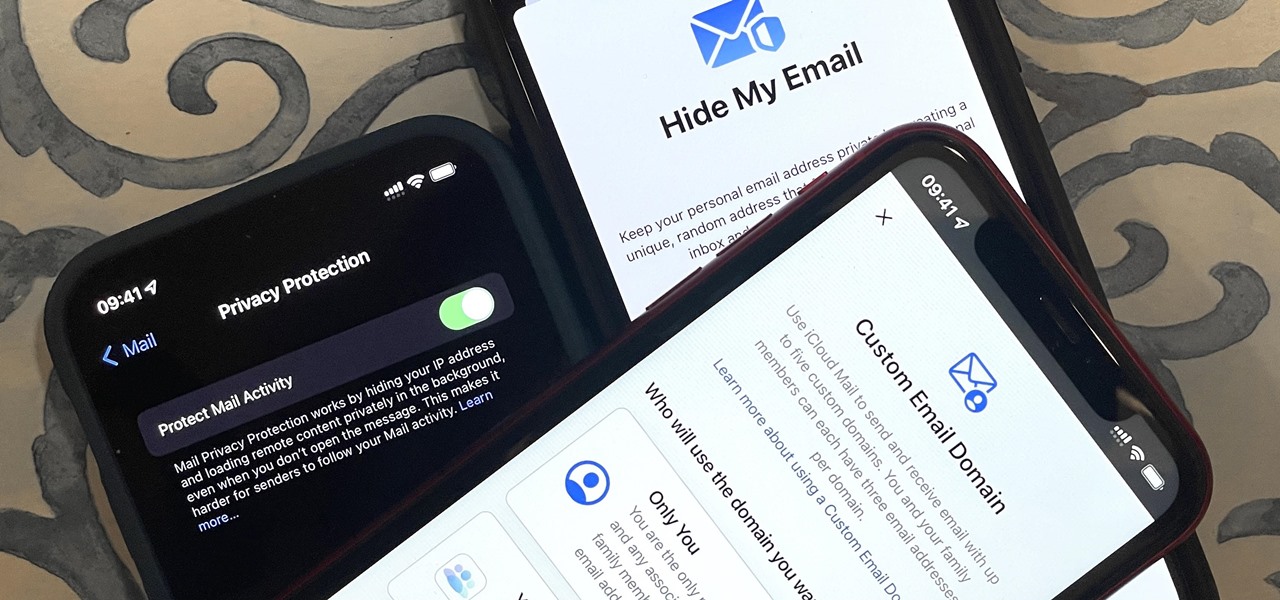
Privacy is a growing concern in the tech industry, but Apple has fallen behind many of its peers when it comes to email security. Fortunately, iOS 15 changes that. Your email address is the key to a vast amount of personal information, not to mention a stepping stone into your other online accounts, so it's great to see new features for iPhones that protect email accounts and their contents.