Joe McKenna died when he was 30 years old. A young married man with his future ahead of him, he was cleaning up the station where he worked as a fireman. Struck by a piece of equipment fallen from a shelf, Joe complained of a sore shoulder. Over the next week, Joe worsened and ended up in the hospital. Chilled, feverish, and delirious, his organs shut down from an infection we'd now call septic shock.

How do I get rid of these zits?! Whether its pimples, blackheads, or whiteheads, the name is the same, and the name is acne.

Even when no one is in your kitchen, it is crowded. The refrigerator, sink, and counters are all covered with microbes that are just hanging around. They are inadvertent remnants from the raw chicken you used in that recipe last night, brewing a bacterial cocktail in your Nespresso machine, or just growing their merry little colonies on your leftovers.

Each generation of smartphones ushers in a new set of top-of-the-line specs, with processing power, battery size, and display resolution growing by the year. These headlining features get the most press, but there's one unsung hero that has the potential to make the biggest difference when it comes to real-world performance: RAM, or random-access memory.

As a former repair tech, I've heard the same reasons over and over as to why people opt not to purchase phone insurance. Some cite the cost—why pay extra every month for insurance when you're careful with your phone? Deductibles are expensive, so why not just spend that money on a repair instead of getting a refurbished phone as a replacement?

Backdoors are convenient to leave behind once you've already found a way into a server, and they can come in handy for a variety of reasons. They're good for developers who want a quick way into machines they're working on, or for systems administrators who want similar access. Of course, backdoors are also a hacker's best friend, and can be added in a variety of ways. One good tool for doing this is Weevely, which uses a snippet of PHP code.

With all of the bare-bones setup out of the way in our Mac for Hackers series, your Apple machine should be ready to run a significant amount of pentesting tools. We can pull tools from GitHub and compile them, we can pull dependencies or tools from Homebrew, we have both Python and Ruby. Everything is ready to go and now it's time to start building a toolbox on our local host.

Right now is that magical time of year when the general public decides to embrace their inner fattie and get baking in the kitchen. Hello, pies and cakes and cookies and everything carbs. Goodbye, diets—see you in the next year, when you cripple us with unbridled guilt and longing.

Virtual reality holds the promise of electronically visiting distant places we'd otherwise struggle to reach, but that teleportation-esque ability isn't possible without the right content. YouVisit created a platform that makes it easy for almost anyone to create immersive 360-degree experiences so we can map our lives and see the world through the eyes of our fellow humans.

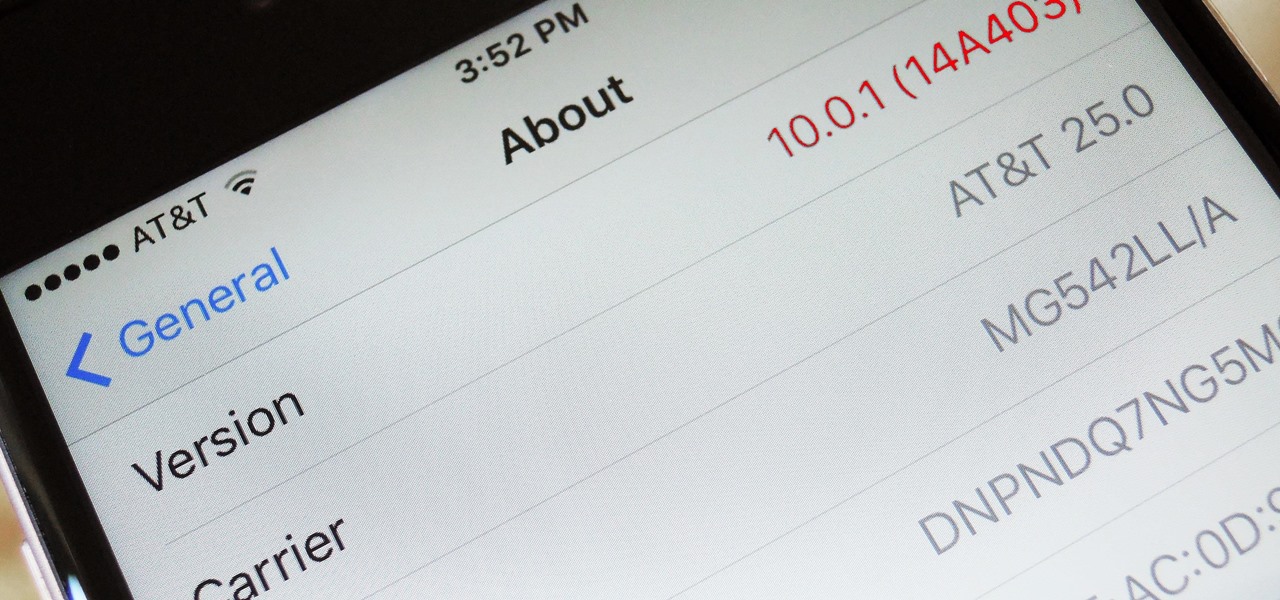
When a new version of iOS comes out, everybody gets caught up in the craze of finding features and playing around with new functionality. But this generally leads to a lack of coverage on the finer aspects of the update—things like bugs, minor tweaks, and pain points that users discover along the way.

While iOS 11 is ready to take over your iPad, iPhone, and iPod touch, let's take a step back and check out all of the new features that iOS 10 brought to the public when it was released to everyone in Sept. 2016.

Thanks to the Edge variants, Samsung's Galaxy S phones are just a few millimeters off in body size when compared to the Note series, and just 0.2 inches smaller when it comes to displays. Now that the two flagship models are almost identical in size—with matching curved displays—there's really only one thing that separates the Note7 from the Galaxy S7 Edge: The S Pen.

A carefully constructed frittata is one of the culinary world's perfect wonders. It's inexpensive to create, can be made with all sorts of leftovers, and is outstanding to eat for breakfast, lunch, or dinner. However, frittatas can go downhill fast and come out spongy, tasteless, dry, and over-done.

Our future technology has a lot of amazing possibilities, and few have more promise than augmented and mixed reality headsets. But these advancements come with several concerns over privacy, and if we don't understand them, we may lose control of our own data without even knowing.

When Microsoft release an update to the HoloLens Development Edition at the end of May, there were a bunch of cool new features added in. Among them: New voice controls that make working in the HoloLens operating system much easier.

Several technologies seek to change the way we perceive our reality, whether that involves entering a virtual world, augmenting an existing one in a realistic and interactive way, or somewhere in-between.

"It just ticked me off," he said. In March 2011, Neil Singh paid $50 to back the Hanfree iPad stand on Kickstarter. The project was funded at $35,000, but production stalled, and the delivery estimates kept getting pushed back.

Good day to everyone, today I will present some basic and advanced concepts that targets sophisticated attacks on the social basis, also I will write about some steps that can prevent this attacks from occuring, basically we will examine Social Engineering from the angle of attacker and victim, some people who are interested in security and work for middle-sized companys can learn and use something interesting from this post.

Instead of suffering through long, dull meetings with your supervisors and coworkers, you can turn those office table sessions into your very own psychological experiment.

The biggest problem with Netflix (which is hardly a real problem) is the overwhelming amount of content available for streaming. Browsing through profile-specific categories might help narrow down your search on something to watch, but some of those categories come and go without warning, and it's impossible to find them again—but not anymore.

Hey guys, in this tutorial, we are going to learn about the heap segment and how to use it for storing data in our programs. We will also go into the details of its use in conjunction with the char pointer and struct data types.

Smartphones are almost always connected to the internet, so it stands to reason that they can be hacked remotely. Or perhaps a jealous boyfriend or girlfriend got hold of your device physically, in which case they could've potentially installed a keystroke logger, a virus, or any other type of tracking app to spy on you.

Making sure you have the best gallery app available for your Android device used to be as easy as just installing QuickPic. But late last year, Android's top photo-viewing app was sold to a company who is notorious for permission spamming, so QuickPic quickly lost everyone's approval.

INTRODUCTION Hello dear null_byters here we go again with our third part of this serie.

When there's a crappy stock app you want to hide, the easiest thing to do is just bury it in the back of a miscellaneous folder. But what if there's an app you want to hide on your home screen that you actually use? For instance, what if you don't want everybody in eyeshot to see what banks you use, or don't want anyone to know about your "dating" apps or porn shortcuts?

Welcome, in this tutorial we shall we looking at creating a safe(r) way to back up your important files. The contents we will be covering are as follows;

In this day and age, maintaining your privacy is a perpetual battle, and doing so with an internet-connected device like your smartphone is even more of a struggle. Every website you visit, every app you install, every message you send, and every call you make is a potential vulnerability that could expose you to prying eyes.

When attempting to gain access to a server, there may come a point when you need to get around file upload restrictions to upload something. If we can find a way to get around the restrictions, then we can upload anything we want to the server, effectively compromising it. That is what we'll be doing here today, so let's get started!

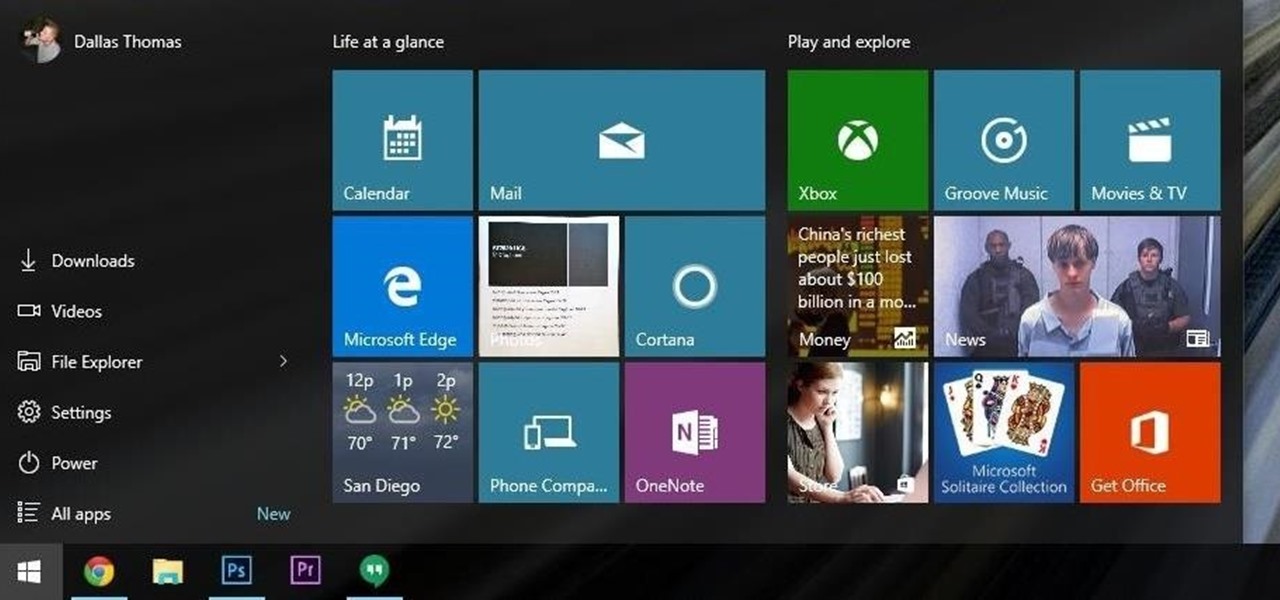
The desktop Start menu is finally back! After receiving a lot of negative user feedback, Microsoft ditched the touchscreen-first approach of Windows 8 and went with a more traditional setup for mouse-and-keyboard users in Windows 10.

I've been a diehard Chrome user since its inception, and even more so since Android was released. The ability to sync bookmarks, passwords, and web history across all of my devices made the switch a no-brainer, but what really made me fall in love was the amount of extensions available for it.

No, your Apple Watch isn't totally hacker-proof, despite what some have claimed.

Throwing a party means making sure everyone has fun, but that pursuit can quickly get out-of-hand. Before you know it, you're once laid back get-together has received so many RSVPs that it becomes obvious you're throwing the party of the century. With an over-abundance of beer and an inflated guest list, your newly-formed epic reputation must live up to the hype.

Whenever you buy a newer iPhone model, you get a set of Apple EarPods with remote and microphone built-in. Aside from their comfortable design and high-quality sound they provide, these headphones offer additional functionality beyond just pausing and playing music.

The drinking straw isn't just there to help you make annoying noises when you get to the bottom of your soda. That little tube of plastic is extremely versatile and can make your life a lot easier with a little know-how. Curious? Read on to find out more.

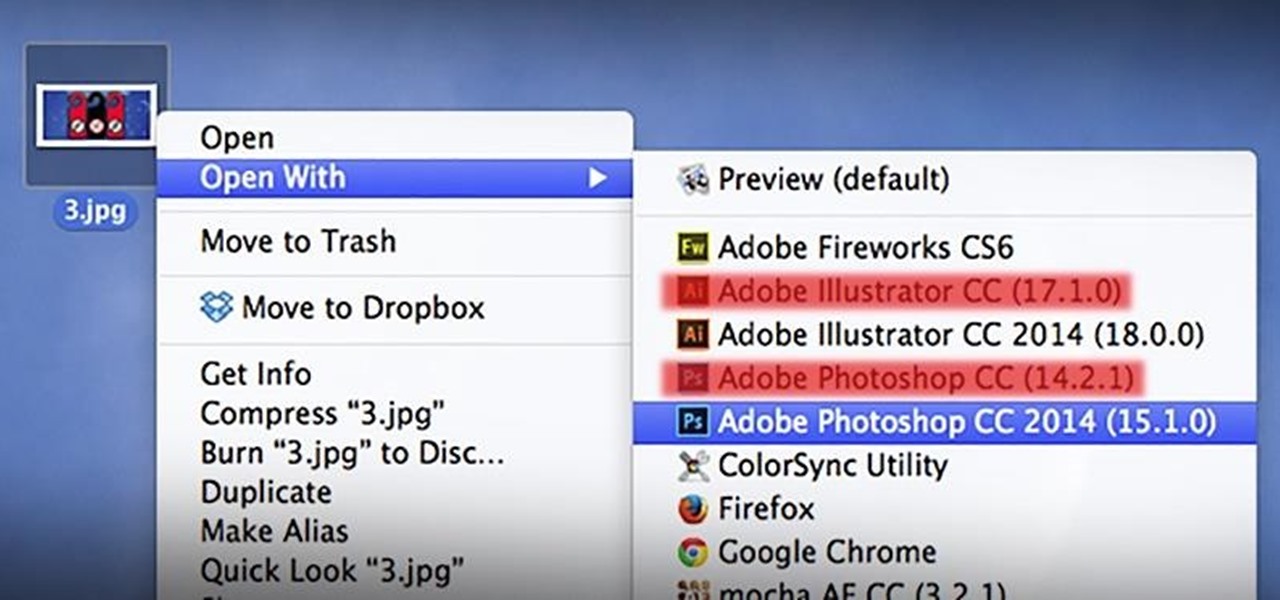
As a regular Mac OS X user, I have a love/hate relationship with the "Open With" contextual menu. Sometimes, it has just what I need. Other times, it's often packed with unnecessary or duplicate items, or missing the app I want to open the file up with the most.

Unless you're someone who's terrified of social situations, chances are you love to talk. But no matter how much you want to share you life story or take over the conversation, you shouldn't. Your socially awkward coworkers that keep their mouth shut might actually have a leg up on you at work, and here's why.

You send out a lot of emails, but probably get very few responses. How can you be sure those emails are even opened?

The long rumored and recently leaked Amazon phone has finally been unveiled, and in the interest of branding, continues down the Fire line—the Amazon Fire Phone. You can check out the full reveal here (warning: it's long), but I'll take you through all the features that sets this device apart from the rest. Before we get into that though, let's check out the specs:

Welcome back, my aspiring hackers and those who want to catch my aspiring hackers! As most of you know, this series on digital forensics is inspired by the motivation to keep all of you all out of custody. The more you know about the techniques used by law enforcement and forensic investigators, the better you can evade them.