
How To: Use BeEF and JavaScript for Reconnaissance
Welcome back everyone. As many of you know, reconnaissance is extremely important in any successful hack. Without proper reconnaissance, we won't know what we're about to get into, literally.


Welcome back everyone. As many of you know, reconnaissance is extremely important in any successful hack. Without proper reconnaissance, we won't know what we're about to get into, literally.

The start of a new year is generally thought of as a chance to start over, a time to improve or "fix" things in your life. Yet most people who set stringent New Year's resolutions find themselves failing within weeks—or even days—of setting their lofty goals.
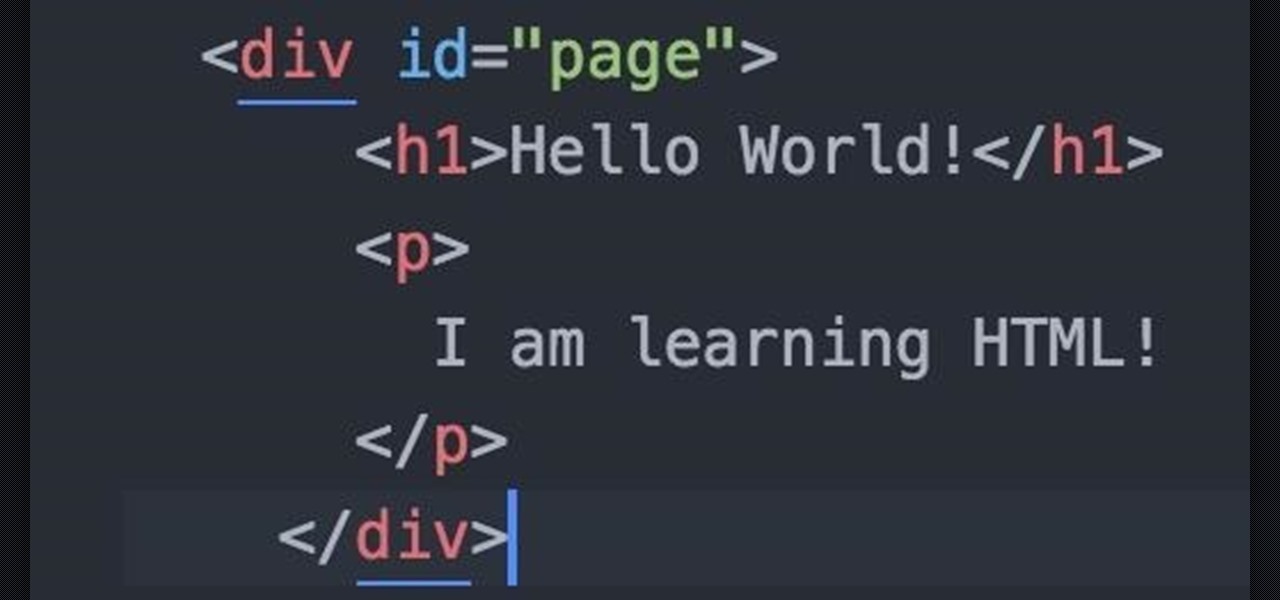
Welcome fellow Null-Byters! Sorry for the delay, this time of the year can be hectic for all of us. Hopefully this will not happen again. In this "tutorial" we will go over more styling and make our page look even better!

Welcome back to another tutorial on functions. Last time, we looked inside memory to see what functions looked like in the flesh and all that Assembly was pretty nasty. At least you have some exposure to it. This time, we will be examining how functions work with the stack.
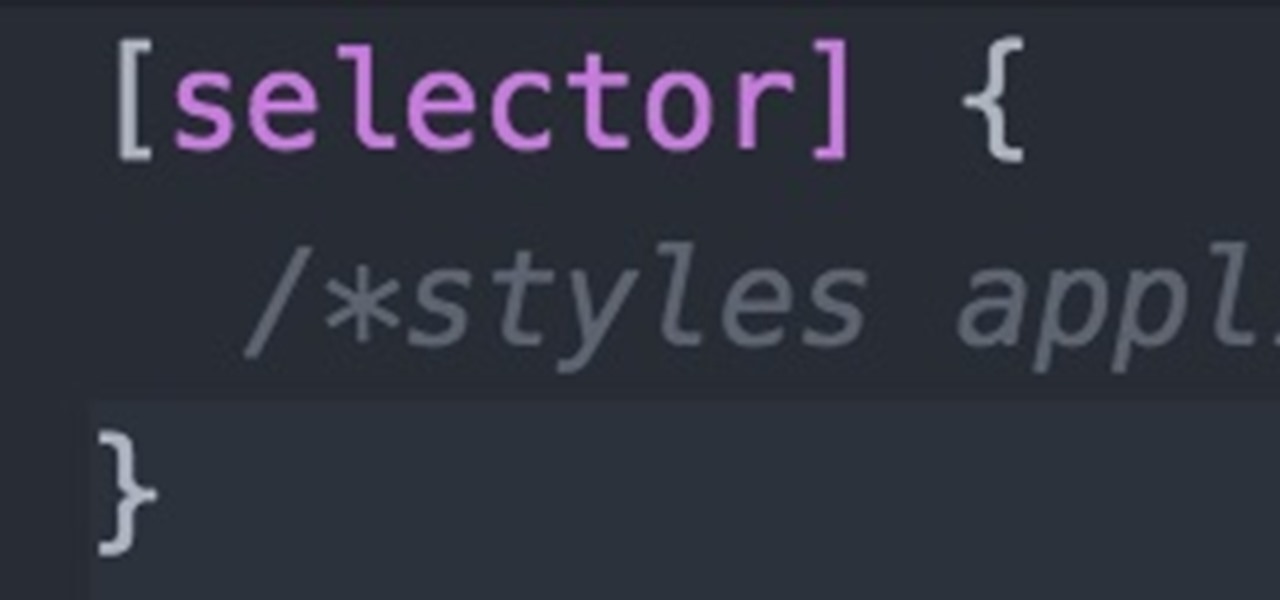
Welcome back Null-Byters! You finally have the pre-basics of CSS and we can begin with styling our web page. If you did not read our last adventure, I suggest you go and read it.

Welcome to another C tutorial. We will be looking at arrays, discussing what they are, when they are used and their special relationship with the char variable. Let's begin.

Welcome back! In the last training session, we covered logical and membership operators. We're going to switch gears and expand our knowledge of lists.

Welcome back, reader! In this tutorial, we will be covering our first program! So let's get to it. We all know the unspoken tradition of the first program when learning a language and of course, here we will respect and complete it. Fire up your favorite text editor (be it vim, emacs, gedit, it's all the same to me, no h8) and try to keep up.

Hello there, reader! If you've clicked on this How-to then it means you are interested in learning some C programming or just generally curious about what this page has to offer. And so I welcome you warmly to the first of many C tutorials!

Welcome back, my neophyte hackers! Digital forensics is one of the fields often overlooked by aspiring hackers. In a rush to exploit every and any system they can, they often ignore learning digital forensics—the field that may lead to them being traced.

Welcome back! In the last round of python training, we talked about tuples and dictionaries. We'll be diverging again and talking about logical operators as well as membership operators. These are used very similiar to booleans, so if you haven't read that, I suggest you do so first.

During my time living in dorm rooms and small apartments, I would find myself in need of many different appliances—a food processor for making hummus, a blender for vegetable smoothies, or even a mortar and pestle for muddling mojito-bound mint leaves. Luckily, there was one tiny, inconspicuous tool that solved all of these problems: the coffee grinder.

Welcome to the Part 2 of the series 'Cryptocurrency'. It has been late because of some errors, where all I typed was lost.

Welcome back, my novice hackers! More and more, the world is turning to and adopting the smartphone platform as the digital device of choice. People are not only using smartphones for voice communication, but also web services, email, SMS, chatting, social networking, photography, payment services, and so on.

Welcome back! In the last iteration of how to train your python, we talked about functions, and we even made our own! We're going to move on to more types of data arrays (much like lists) in today's discussion.

Welcome back, my tenderfoot hackers! As most of you know, I am strong advocate for using Linux as a hacking platform. In fact, I would say that without knowing Linux, you will never become a professional hacker/pentester.

Welcome back! In the last iteration of how to train your python, we covered error detection and handling. Today we'll be diverging from this and discussing functions. More specifically, we'll be creating our own functions. First we'll need to understand exactly what a function is, then we'll get on to making our own! So, let's get started!

Welcome back, my greenhorn hackers! Throughout this series on Metasploit, and in most of my hacking tutorials here on Null Byte that use Metasploit (there are many; type "metasploit" into the search bar and you will find dozens), I have focused primarily on just two types of modules: exploits and payloads. Remember, Metasploit has six types of modules:

Welcome back! In the last iteration of how to train your python, we covered loops, today we'll be covering something that I wish I had learned about much earlier in my scripting career, errors. We all run into them, and they can be frustrating, but there is also a silver lining to them. Today, we'll be discussing why some errors are unavoidable, and what we can do when we run into them. Also, this article will be more of a concept and less of writing actual code, but the information is equall...

Welcome back, my greenhorn hackers! Many new hackers come from a Windows background, but seldom, if ever, use its built-in command-line tools. As a hacker, you will often be forced to control the target system using just Windows commands and no GUI.

Welcome back, my hacker novitiates! There are many ways to hack databases, and most of these techniques require SQL injection (SQLi), which is a way of sending SQL commands back to the database from a web form or other input. In this tutorial, we will use SQL injection to get access to the underlying server. So instead of getting access to the database and its data, we will use the database as an intermediary to gain access to the underlying server.

Welcome back, my tenderfoot hackers! Recently, Microsoft released a new patch (September 8, 2015) to close another vulnerability in their Windows Vista, 7, 8, and 8.1 operating systems. The vulnerability in question (MS15-100) enabled an attacker to gain remote access to any of these systems using a well-crafted Media Center link (MCL) file.

Welcome back, my nascent hackers! Although my favorite TV show, Mr. Robot, had completed its first season already, I have not completed demonstrating the hacks that Elliot used in the show. (By the way, I can't wait for season 2!)

Welcome back, rookie hackers! We recently began an exploration of ways to hack using the Bluetooth protocol. As you know, Bluetooth is a protocol that connects near field devices such as headsets, speakers, and keyboards. Its minimum range is a 10-meter radius (~33 feet) and maximum is at 100 meters (~328 feet).

Welcome back, my fledgling hackers! In this series, I am trying to develop your knowledge of digital forensics, which is valuable whether you're choosing a career in it or just want to know how your hacker activity can be traced. Few professional digital forensic investigators have a hacking background, but the best ones do.

Whether you are sending your phone in for repairs or finally selling it to upgrade to a new flagship, you are going to need to make sure all of your personal data is removed from your device.

Welcome back, my rookie hackers! As most of you know, Mr. Robot is probably the best hacker TV show ever! This is a great show about a cyber security engineer who is being enticed to hack the very corporation he's being paid to protect. This show is so good, I began a series to demonstrate how to do the hacks he uses in the show.

Welcome back, my tenderfoot hackers! A number of you have written me telling me how much you enjoy the Mr. Robot series on USA Network. I am also a huge fan! If you haven't seen it yet, you should. It may be the best show on TV right now.
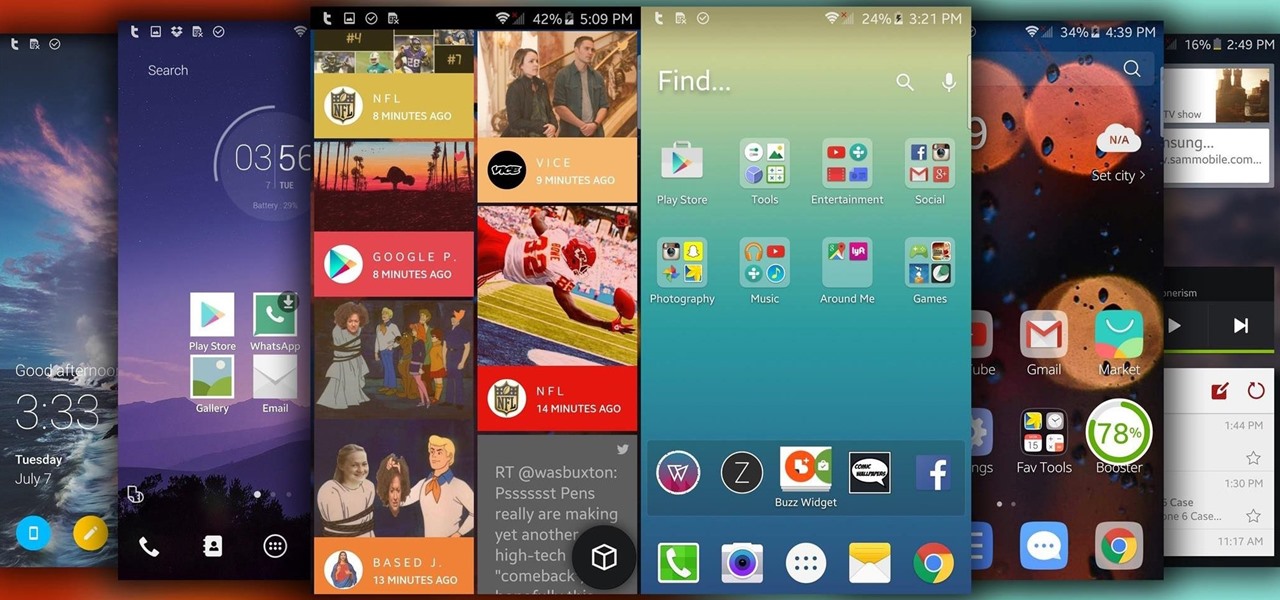
I'm often reluctant to use a home screen launcher other than the stock one on my Android. Once you're well acclimated with something, complacency sets in, welcoming change with much resistance. Well, my friends, I have seen the error of my ways...

Welcome back, my hacker novitiates! In the previous two posts in this series, we looked at the basics of buffer overflows. In this post, we will look at one technique for finding buffer overflows. We will try to send random, oversized, and invalid data at a variable to see whether we can make it crash or overflow. This process is known as fuzzing. It is often the first step to developing an exploit, as we need to find some variable that is susceptible to overflowing.

Welcome back, my tenderfoot hackers! One of the issues we often encounter with Metasploit is how to add new modules. Although Rapid7 (Metasploit's owner and developer) periodically updates Metasploit with new exploits, payloads, and other modules, at times, new modules appear that are not added to the Metasploit repository.

Hello there, 'Flashers'! Welcome to my 8th Post. This tutorial will explain how to flash Kali NetHunter on OnePlus (Tested) and Nexus Devices (Not Tested-Should work) as a secondary ROM, so that none of your personnel data/ROM gets affected.

Apple's latest update to Mac OS X, 10.11 El Capitan, is currently available in the Mac App Store for everyone to download and install at no cost. The new OS features Split View mode for better multitasking, a cleaner Mission Control, smarter Spotlight, a way to mute Safari tabs playing audio, enhanced Mail and Notes apps, and more.
Hello and Welcome back to another How-To on the Xbox Community Ambassadors World! In this How-To, I am going to tell you and kinda show you how to deal with or avoid angry Xbox Customers.

Welcome back, my tenderfoot hackers! Have you ever wondered where the physical location of an IP address is? Maybe you want to know if that proxy server you are using is actually out of your local legal jurisdiction. Or, maybe you have the IP address of someone you are corresponding with and want to make certain they are where they say they are. Or, maybe you are a forensic investigator tracking down a suspect who wrote a threatening email or hacked someone's company.

Welcome back, my rookie hackers! In my ongoing attempts to familiarize aspiring hackers with Linux (nearly all hacking is done with Linux, and here's why every hacker should know and use it), I want to address a rather obscure, but powerful process. There is one super process that is called inetd or xinetd or rlinetd. I know, I know... that's confusing, but bear with me.

Hi there, Elites Welcome to my 6th post, This tutorial will explain how to hack windows, using a program (No-IP)

Everyone has the same five spirits in their bar: vodka, rum, whiskey, tequila, and gin. They're all great, but every so often the mood strikes to try a cocktail with a little something different. We'd like you to meet three spirits from South America that would make a welcome addition to your next cocktail party.

Welcome back, my tenderfoot hackers! Now that we have begun this trip down web app hacking lane, we need to first address target reconnaissance. Like any hack, reconnaissance is critical. (Are you tired of me saying that yet?)

OR rather How to make the Backdoor Persistent: Hello, my Cold and Merciless Hackers,