With the sheer amount of photos, videos, and miscellaneous files we place on our computers, proper organization becomes necessary. Not only so that we can quickly get to a file when it's needed, but also to declutter folders and keep them from looking like random file dumps.
Welcome back for another How-To on the Xbox Community Ambassadors World! In this How-To, we are going to tell you how to help someone the right way so you can get a 9/9 rating when your finished assisting someone! Lets begin, shall we?

Welcome back, my nascent hackers!

This past year was a big one for WonderHowTo. Our biggest yet. In 2014 our writers, curators, and community members helped over 100 million people learn over 270 million new things. That's 40% more people than the total number of students enrolled in every single school from elementary through college across the entire United States. That's pretty awesome. I couldn't be more proud of our entire team, and of course you, the community members who've helped us grow to this point.

By now, nearly everyone with any type of media access is aware that Sony Pictures Entertainment was hacked on November 24th. Although there can be many interpretations and lessons drawn from this audacious act, there is one indisputable conclusion: it and its ripples across the globe underlines how important hacking has become in our all-digital 21st century. As I have emphasized so many times in this column, hacking is the discipline of the future. From cybercrime to cyber intelligence to cy...

The importance of body language is stressed from an early age: watch those around you, and you'll know what they're thinking. While you might be skilled at deciphering the messages of crossed arms, slouched sitting, eye movements, and hand gestures, the key to understanding those around you is a little less obvious.

Welcome back, my greenhorn hackers! Before we attempt to exploit any target, it is wise to do proper reconnaissance. Without doing reconnaissance, you will likely be wasting your time and energy as well as risking your freedom. In previous guides, I have demonstrated multiple ways to perform reconnaissance including passive recon with Netcraft, active recon with Nmap or hping3, recon by exploiting DNS or SNMP, and many others.

It wasn't too long ago that I showed you how to unlock the LG G3 bootloader and install TWRP, and while the process was extremely easy, the custom recovery can look a little intimidating to new users. Even long-time users who know how to navigate it find it boring to look at, as TWRP has had the same basic aesthetics since its creation.

While the adoption of Apple's newest mobile operating system, iOS 8, was smoother than its predecessor, there were still a lot of bugs and features that needed ironed out. There were lost cellular signals, missing Camera Rolls, a confusing iCloud Drive, and no functioning Apple Pay yet, among other things. Now it's just over a month later from its first release to the public and things are finally looking pretty good.

Apple has just released iOS 8 beta 5 to developers, which is speculated to be the second-to-last beta build before they launch the gold master (GM) edition at the end of this month.

Welcome back, my greenhorn hackers! Lately, much of the discussion here on Null Byte has revolved around evading detection and not getting caught hacking. Several of you have written me asking for a series on evading detection and forensics, and while I began a series 5 months ago on just that, we have changed hacking platforms from BackTrack to Kali, which has a much more highly developed forensic toolset.

Welcome back, my greenhorn hackers!

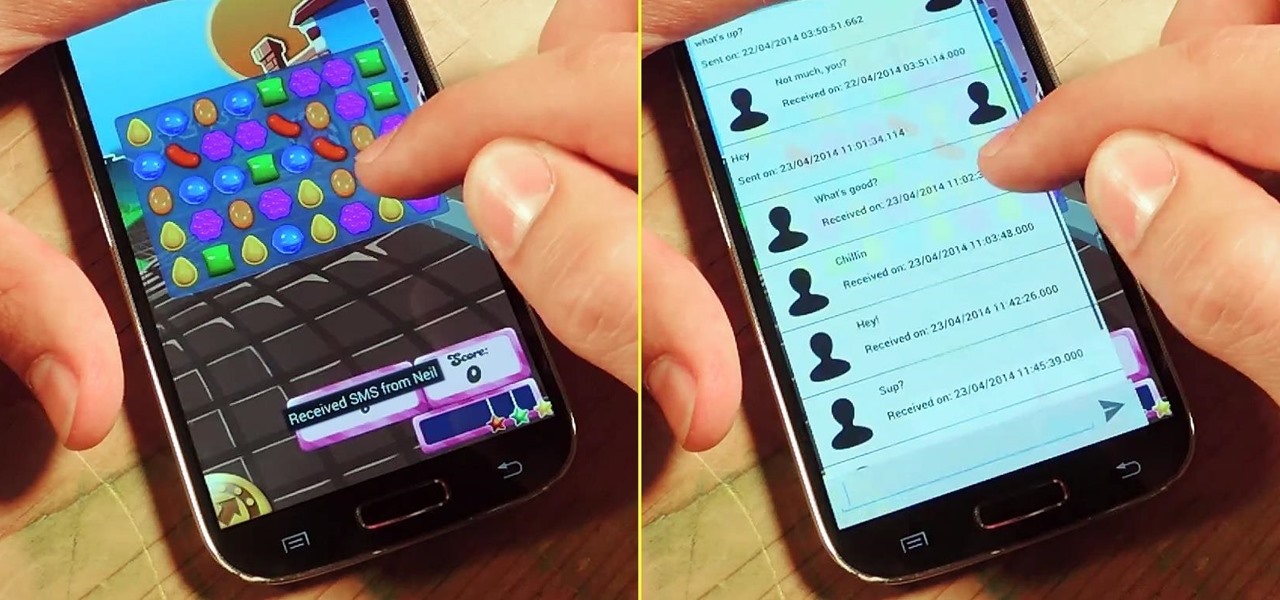
I'm a textaholic, as I've said many times before, but even textaholics forget to respond sometimes. When I'm watching a YouTube clip or devouring delicious snacks in Candy Crush Saga, I'll often ignore incoming texts and forget to respond later.

If you've ever used IFTTT, you know how well it can automate your online world. The premise is simple—If This, Then That—but the results are powerful. From automatically printing images based on hashtags to getting around Twitter bans, the service is quite useful with a wealth of possibilities.

With the emergence of rumors that Amazon, Google, and Samsung are all making their foray into the gaming console market, it's a possibility that our Android-powered mobile devices might become tools that play a central role.

Welcome back, my greenhorn hackers! Earlier in this series, I showed a you a couple of different ways of fingerprinting webservers. Probably the easiest way, is to use netcat and connect to port 80 and pull the webserver banner.

Changing your wallpaper and downloading icon packs is nothing new to the HTC One, but some people will go overboard with remapped keys, icon layouts on custom grids, and extensive wallpaper cropping—processes that could take hours to get just right.

Welcome back, my novice hackers! In a recent tutorial, I showed how the SNMP protocol can be a gold mine of information for reconnaissance on a potential target. If you haven't already, I strongly suggest that you read it before progressing here, as little of this will make much sense without that background.

Welcome back, my neophyte hackers! In today's hack, we're going to have a bit of Halloween fun. Have you ever had a boss who made you miserable with his micro-management and nagging? Maybe you thought he unfairly fired your friend/colleague? Well, now here's your chance to get a bit of revenge and keep him or her off your back!

Welcome back, my novice hackers! I've written a couple of articles on reconnaissance and its importance, and as I've said before, a good hacker will spend 3 to 4 more times doing reconnaissance than actually exploiting the system. If your recon isn't good, you'll likely fail, or worse—end up serving time and becoming Bubba's wife for a couple years. I can't say it enough—recon is critical.

Just because you wanted a stable, stock Android version on your HTC One doesn't mean you have to miss out on Sense because you bought or softModded to a Google Play Edition. As long as you have the Android SDK tools and you've unlocked your bootloader, you can turn your HTC One into the Developer Edition, a Sense version free of carrier bloat.

Welcome back, my hacker novitiates! Finding vulnerabilities in systems can be one of the most time-consuming tasks for a hacker. There will be times, though, when you'll find yourself in a position that you know that a particular port represents a vulnerable application or service.

Unlocking your Samsung Galaxy S4 so you can use a different SIM card isn't the easiest thing in the world. In the states, unlocking cell phones was actually illegal, despite the White House's disapproval, though, a recent bill has making its way to the House floor and has made it legal again.

Why can't I see who is stalking my Facebook profile?

Welcome back, my hacker apprentices! My recent posts here in Null Byte have been very technical in nature, so I thought that I'd have a little fun with this one.

Welcome back my fellow army of hackers! Today we'll be hacking a website. Hacking is technically not the right word used here. It should be defacing! So we are going to deface a website...

Welcome back, my newbie hackers! Hackers often are associated with clandestine and illegal activity, but that is not necessarily always the case. Hackers are increasingly being used and employed for law enforcement, national security, and other legitimate purposes. In this installment, we will look at how a single hacker could save the world from nuclear annihilation.

How to cut Drywall, Sheetrock, Plasterboard. THE EASY WAY! G'day Knuckleheads, Uncle Knackers here and welcome to Video Two of my ten part series titled 'My Top Ten DIY Tips' as nominated by you..

Welcome back, my hacker wannabees! Most of my recent posts have addressed using Metasploit’s Meterpreter and what we can do once we have embedded it on the victim’s system. This includes remotely installing a keylogger, enabling the webcam, enabling the microphone and recording, disabling the antivirus software, among many other things. The list is almost unlimited.

Welcome back, my tenderfoot hackers! In some of my past articles, I've shown numerous ways of embedding a listener/rootkit on a remote system, including buffer overflows of the operating system, getting the victim to click on a link to our malicious website, and sending a malicious Microsoft Office and Adobe Acrobat file.

Cross-dressing and gender-bending are nothing new, but the realm of Steampunk seems to be especially accepting of role-reversal in dress.

Welcome back my fellow hackers! In my last few articles, I've concentrated on what is called a listener, which is basically the same thing as backdoor and rootkit, only "listener" sounds much less malevolent than the other two terms.

I've tried my hand in the past at defining Steampunk, but as anyone else who has made a similar attempt will tell you, there's a significant backlash from the community against working to create a real definition of what Steampunk is. That may sound ridiculous to some, but it's a very serious matter to others. With the recent announcement that TeslaCon 4 will be called the Congress of Steam, I think it's appropriate to talk about why all of this stuff is worth it. In this article, I'm going t...

Getting two sticky-pistons to pull eachother, a piston-train, isn't anything new but the pistons and their timing in 1.3 are and there has been alot of QQ-ing on the Minecraft-forums about how bad they are and that Jeb should bring back the old pistons we all know. I, for one, not only welcome out new 1.3-pistons but have also made a small mini-game out of them. A two-player tug-o-war. The players stand on the diamond or emerald area and press a button to make the piston-train take one step t...

Hello and welcome to my post. I would like to share a few things I have picked up along the way - while feeding my two dwarf rabbits. In this tutorial I would like to answer the question - How to choose the best food for your rabbit?

Hi! All the cake lovers, welcome to my first post in the World of Dessert Recipes. I would like to contribute a recipe for the chocolate cake, called Taraba. The original recipe was made in Bosnia. It is one of my favorite cakes, very sweet, but does not contain fruit.

For anyone who lives in a space that may frown upon making holes in the walls, or for anyone who may not want to take on such a task, there's a simple alternative to hanging curtains or drapes. And the answer is brilliantly simple.

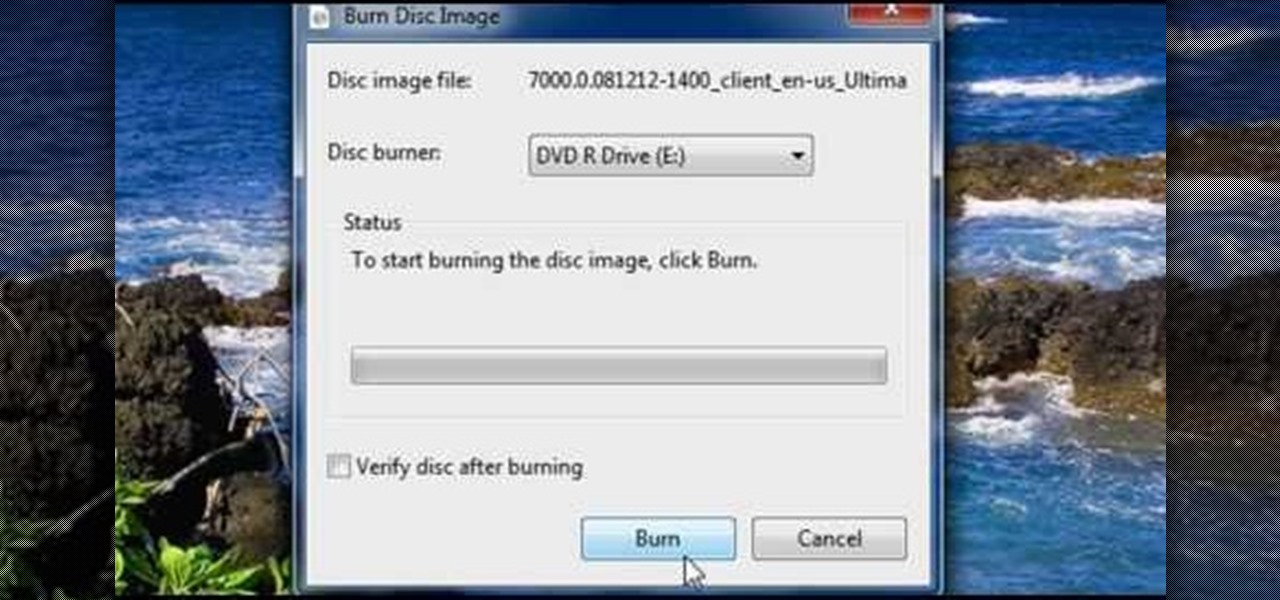
This how-to video is about how to download and install Windows 7 operating system in the computer. To download and install Windows 7 for free just follow these steps: